The pervasive threat landscape surrounding browser extensions has once again been illuminated by the ongoing activities of the GhostPoster campaign. Security researchers have uncovered a fresh wave of 17 malicious add-ons, distributed across the Google Chrome, Mozilla Firefox, and Microsoft Edge ecosystems, collectively amassing an alarming total of 840,000 user installations. This development underscores a persistent failure in the vetting processes for browser marketplaces, allowing sophisticated, long-term disinformation and financial exploitation campaigns to thrive under the guise of legitimate utility software.
The initial exposé of the GhostPoster operation, which surfaced in December through the diligent work of researchers at Koi Security, revealed a cunning methodology: the concealment of malicious JavaScript payloads directly within the image assets, specifically the logos, of various browser extensions. These seemingly innocuous visuals served as Trojan horses, delivering code designed to surreptitiously monitor user navigation, compromise digital transactions, and generate illicit revenue.
The core functionality of the initial threat involved retrieving a heavily obfuscated secondary payload from remote servers. Once executed, this payload initiated a multi-pronged attack: comprehensive tracking of the victim’s browsing history, the hijacking and redirection of affiliate links on high-traffic e-commerce sites—thereby siphoning commissions—and the injection of near-invisible iframes designed to facilitate large-scale ad fraud and click fraud schemes.

The resilience and ongoing nature of this campaign are now confirmed by a recent, in-depth analysis from LayerX, a platform specializing in browser security. Their findings indicate that despite public awareness following the initial December report, the GhostPoster operators have successfully redeployed and updated their arsenal. The 17 newly identified extensions represent an active, evolving threat vector, demonstrating the attackers’ commitment to maintaining operational continuity across different browser environments.
A Campaign of Longevity and Cross-Platform Expansion
A crucial finding from the LayerX investigation centers on the timeline of these malicious deployments. While the campaign appears to have originated with a focus on the Microsoft Edge Add-ons store, it rapidly metastasized to infect the Firefox Add-ons repository and the Chrome Web Store. More troublingly, the analysis of deployment dates revealed that several of these fraudulent extensions have been lurking in browser repositories since as far back as 2020. This four-year lifespan for some components speaks volumes about the sophistication of their obfuscation techniques and the limitations of automated store scanning during that period. It signals a long-term, highly successful cybercriminal enterprise operating within the trusted digital periphery of billions of user sessions.
The timeline visualization provided by LayerX starkly illustrates the sustained effort by the threat actors to introduce new variants while maintaining older, successful infrastructure. For the average user, the trust placed in these marketplaces—where extensions are often vetted for basic security compliance—is fundamentally betrayed by such persistent evasion.
Evolving Evasion: The Advanced Staging of GhostPoster
While the fundamental evasion and post-activation behaviors observed in the new batch align closely with those documented earlier by Koi Security, LayerX pinpointed a significant technological leap in a specific variant: the "Instagram Downloader" extension. This evolution represents a notable advancement in malware staging and resilience.

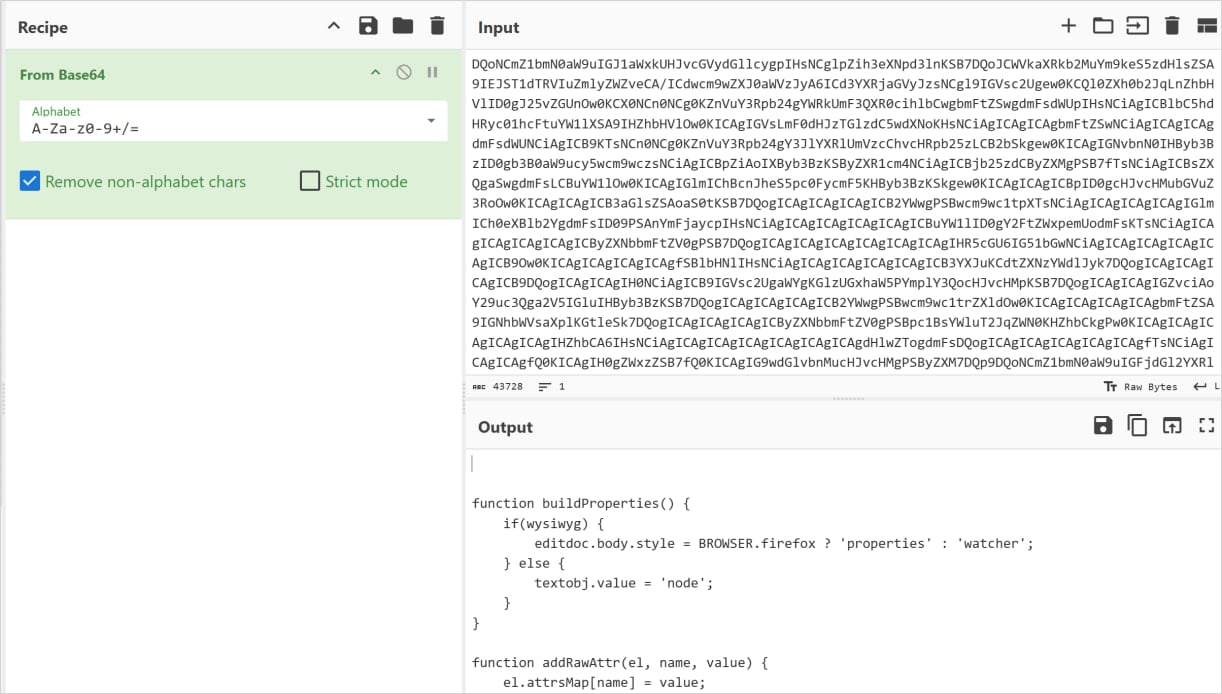
Previously, the malicious code was more directly embedded or linked via the visual asset. In this updated iteration, the threat actors have migrated the critical malicious staging logic away from the primary icon file and deeper into the extension’s background script. Furthermore, the payload container itself has been refined. Instead of relying solely on the extension icon, the malware now utilizes a bundled image file within the extension package as a covert, secondary container for the actual malicious code.
This move introduces layers of indirection that severely complicate static analysis and traditional behavioral monitoring tools. The execution sequence is now a multi-stage process designed for maximum dormancy and resilience:
- Initialization: Upon loading, the extension’s background script initializes.
- Data Extraction: The script actively scans the raw binary data of the bundled image file.
- Delimiter Search: It searches for a specific, proprietary delimiter sequence (identified as
>>>>) embedded within the image data. - Payload Isolation: Upon finding the delimiter, the script extracts the subsequent data block—the hidden payload—from the image file’s raw bytes.
- Storage: This extracted data is then securely stored within the extension’s local storage mechanism.
- Execution: Only after a period of dormancy or upon a specific trigger does the script retrieve the data, perform a Base64 decoding operation, and finally execute the resulting JavaScript code within the user’s browser context.
LayerX’s assessment of this refined process is critical: "This staged execution flow demonstrates a clear evolution toward longer dormancy, modularity, and resilience against both static and behavioral detection mechanisms." This architecture means that simple scans checking for remote communication or immediate obfuscated code execution upon installation are likely to fail, as the true malicious intent is unlocked hours, days, or even weeks later, only after the necessary data has been locally assembled.
Industry Implications and the Burden on Platform Owners
The discovery of these deep-rooted, long-lived threats carries significant implications for the entire software distribution industry, particularly for the browser makers who operate these vital add-on marketplaces. The 840,000 installs figure is not merely a statistic; it represents a massive potential pool for financial exploitation, identity harvesting, and the propagation of low-level, persistent adware across a significant user base.

For platform owners like Google, Mozilla, and Microsoft, this incident highlights systemic vulnerabilities in their vetting pipelines. If extensions dating back to 2020 could harbor such complex, evolving malware, it suggests that historical security checks, which may have been adequate at the time of initial approval, are insufficient to catch subsequent malicious updates or persistent backdoors. The current arms race in cybersecurity demands continuous, adaptive scrutiny, not just point-in-time approval.
The shift from simple icon-based steganography to bundled image file payloads within the extension structure itself suggests that the attackers are actively reverse-engineering the platform security tools. They are leveraging the allowed file types and storage mechanisms of the extensions—which are designed for legitimate configuration—as sophisticated, multi-layered bunkers for their command-and-control infrastructure.
User Risk and Remediation Challenges
While researchers have confirmed that the newly identified extensions have been purged from the Mozilla and Microsoft repositories, and Google has subsequently confirmed the removal of the Chrome variants, the immediate danger to users who previously installed these tools persists.
The primary risk lies in the persistence of the malware. Even after removal from the store, the malicious code remains active on the machines of those who installed it. Unless the user manually navigates to their extension management panel and explicitly uninstalls the add-on, the threat actors retain the capability to continue monitoring activity, hijacking affiliate links, and potentially leveraging any stored session cookies or browser data until the extension code is neutralized.
This reality places a heavy burden on end-users, who are often unaware of the extent of their installed software footprint. Furthermore, the sophisticated nature of the payload means that even if the extension appears dormant, a remote trigger could reactivate the full suite of malicious capabilities at any moment. Security hygiene mandates that users who may have installed any software associated with this campaign—even if they haven’t noticed any immediate adverse effects—should perform immediate, thorough removal and potentially review their recent online purchase histories for fraudulent activity linked to affiliate link redirection.
The Future of Browser Security: Beyond Simple Signatures
The GhostPoster campaign, particularly its advanced iteration involving image-file staging, serves as a critical case study signaling the future trajectory of browser-based malware. Attackers are moving away from overt, easily detectable JavaScript payloads toward file-based steganography and multi-stage execution designed to defeat sandboxing and behavioral analysis.
Expert analysis suggests several necessary shifts in defensive posture:
- Deep Content Analysis: Browser store vetting processes must move beyond metadata and manifest checks to incorporate deep, context-aware analysis of all bundled assets, including images and data files, looking for known obfuscation patterns or structured data that resembles encoded executables.
- Runtime Integrity Monitoring: Browser vendors need to deploy more aggressive runtime integrity checks that monitor for attempts by extensions to dynamically decode and execute code stored in non-standard locations (like local storage populated from image files).
- Dormancy Detection: Security models must evolve to prioritize extensions that exhibit long periods of low activity followed by bursts of high-privilege activity, especially those interacting with high-value targets like e-commerce domains.
- Supply Chain Verification: Given the longevity of these campaigns, a form of "software supply chain integrity" for extensions, perhaps involving regular re-verification of the code base against the initially approved version, is becoming essential.
In conclusion, the GhostPoster discovery is not an isolated incident but a marker of increasing sophistication in the commoditization of browser compromise. With hundreds of thousands of users exposed to financially motivated surveillance and fraud, this episode reinforces the urgent need for browser platform providers to radically overhaul their security paradigms to address threats that hide in plain sight, embedded within the very fabric of trusted application icons. The battleground has clearly shifted from detecting bad code to detecting malicious intent hidden within benign containers.

