Identity and access management (IAM) infrastructure, particularly Single Sign-On (SSO) solutions like those provided by Okta, has become the central nervous system for modern enterprise operations. This centralization, while offering unparalleled convenience and efficiency, simultaneously presents a high-value target for sophisticated threat actors. Recent intelligence highlights a significant escalation in social engineering tactics, moving beyond static web pages to highly interactive, real-time vishing (voice phishing) campaigns powered by specialized, commercialized phishing kits. These toolsets are transforming the psychological landscape of digital deception, directly targeting the weakest link in the security chain: human trust facilitated by real-time voice interaction.
Okta’s recent security disclosures confirm that these bespoke phishing frameworks are actively deployed in operations aimed at compromising credentials for major identity providers, including Okta, Google, and Microsoft, as well as critical cryptocurrency platforms. The operational model for these kits is alarming: they are sold and distributed as a managed service, lowering the barrier to entry for diverse criminal syndicates intent on large-scale data exfiltration.
The Mechanics of Real-Time Deception
The fundamental shift in this attack vector lies in the architecture of the phishing infrastructure. Traditional phishing relies on replicating a login page and hoping the victim enters their credentials before realizing the discrepancy. These new kits, however, function as sophisticated Adversary-in-the-Middle (AiTM) platforms explicitly engineered for synchronous engagement during a live phone call.
The process begins with meticulous reconnaissance. Attackers dedicate resources to profiling target employees, mapping out their roles, the specific cloud applications they access via SSO, and critically, gathering internal contact information, such as the phone numbers associated with the organization’s legitimate IT helpdesk or support departments. This preparatory work allows the threat actors to cultivate authenticity.

The assault is initiated when the attacker contacts the target employee, typically spoofing the phone number of the internal helpdesk or IT security team. The narrative often revolves around urgent security matters, such as mandated MFA upgrades, security patch deployment, or, increasingly, the setup of newer, perceived-as-safer authentication methods like passkeys.
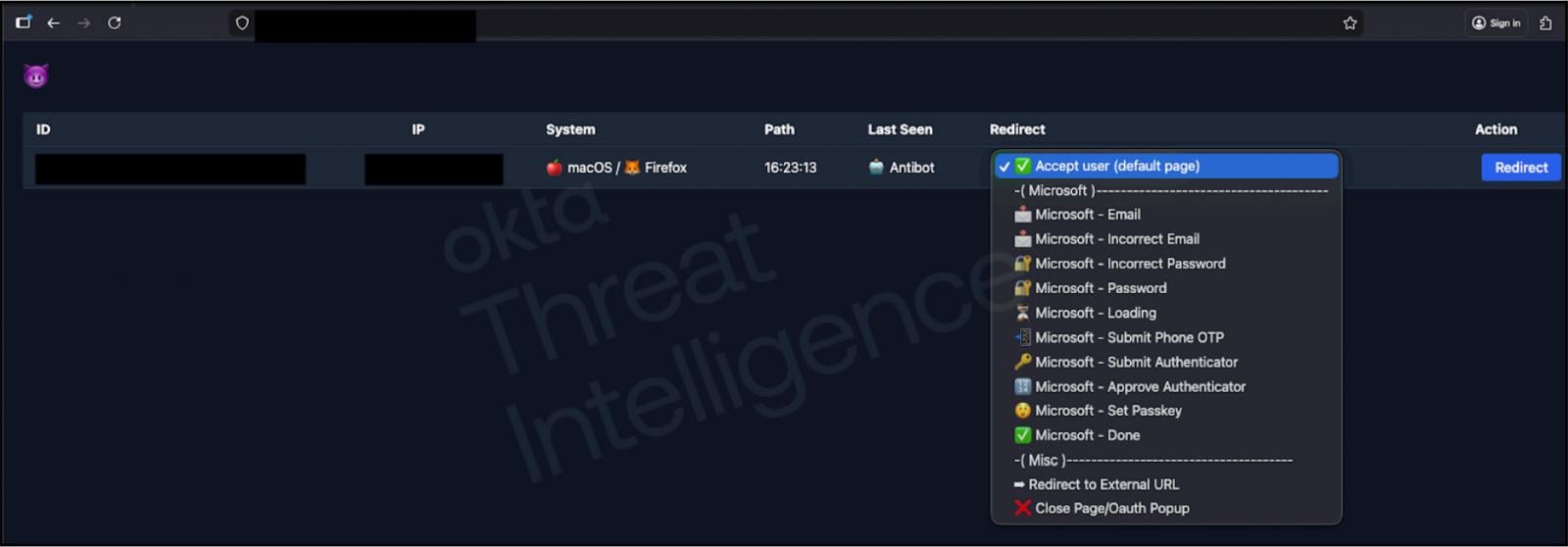
During this conversation, the victim is directed to a bespoke phishing site. These sites are often cleverly branded to mirror the target organization’s internal portal, sometimes incorporating company names alongside terms like "internal" or "my," creating immediate, localized credibility. As the victim inputs their username and password into this seemingly legitimate interface, the credentials are instantaneously relayed to the attacker’s command-and-control (C2) backend, often utilizing instant messaging platforms like Telegram for rapid notification.
The true innovation, and the danger, lies in the subsequent steps. Once the attacker possesses the initial credentials, they immediately attempt to log into the genuine service. This real-time action forces the legitimate service (e.g., Okta) to issue a Multi-Factor Authentication (MFA) challenge to the actual user.
At this critical juncture, the AiTM platform takes over the visual experience of the victim. The attacker, monitoring the live authentication response from the target service, dynamically updates the content displayed on the victim’s browser. If the system issues a push notification prompt, the phishing site immediately displays a corresponding push notification request, often instructing the user to select a specific number or approve the prompt. This perfect visual synchronization—where the user’s screen perfectly mirrors the expected legitimate flow—crushes cognitive dissonance, making the fraudulent request appear entirely valid.
Bypassing Advanced MFA Safeguards
Perhaps the most significant technical finding from Okta’s analysis is the capability of these kits to neutralize modern, context-aware MFA methods. Technologies like MFA push notifications incorporating number matching are specifically designed to prevent credential stuffing and session hijacking by requiring the user to verify a code displayed both on their phone and their desktop screen.

In the vishing scenario, the attacker circumvents this safeguard not by cracking the MFA, but by socially engineering the user’s input. When the victim is prompted to enter the verification number displayed on their phone, the attacker, who has already seen the challenge response on their own screen or through the C2 panel, simply instructs the victim verbally: "Please enter the number 42 on the screen now." Because the attacker controls the displayed prompts on the victim’s browser via the C2 interface, the visual elements align perfectly, and the user approves the request, granting the attacker session access.
This level of interaction demands that the attacker maintain a highly controlled, low-latency communication channel with the victim, sustained entirely through the phone call, making the human element the pivot point for sophisticated technical circumvention.
Industry Implications: The Centralization Risk
The targeting of identity providers like Okta underscores a critical risk inherent in enterprise cloud adoption: the single point of failure created by centralized access management. Okta SSO serves as the universal gateway to an enterprise’s entire digital ecosystem—including productivity suites (Microsoft 365, Google Workspace), customer relationship management (Salesforce), communication tools (Slack, Zoom), and development environments (Jira, Confluence).
Compromising a single set of SSO credentials grants an attacker immediate, broad-spectrum access to sensitive operational data, intellectual property, and customer records across disparate platforms. As evidenced by observed post-compromise activities, threat actors rapidly pivot from the initial SSO breach to data exfiltration targets. Reports emerging from affected organizations indicate a particular focus on CRM systems like Salesforce, cited by threat actors for their relatively straightforward data extraction capabilities.
The implications for sectors with high regulatory burdens and significant proprietary data—such as Fintech, wealth management, and financial advisory services—are severe. These industries rely heavily on cloud-native workflows and robust identity security, yet they remain prime targets due to the high intrinsic value of the data they manage. A breach originating from a vishing attack on an SSO credential can trigger immediate compliance failures, severe financial penalties, and irreparable reputational damage.
The Commoditization of Cybercrime
The "as a service" model underpinning these phishing kits is a significant trend in the current threat landscape. It signifies the industrialization of cybercrime, where complex technical infrastructure (the AiTM phishing platform, C2 servers, and real-time manipulation scripts) is abstracted away from the end-user attacker. This democratization allows lower-skilled actors to execute highly complex, multi-stage attacks that previously required significant coding and infrastructure expertise.
The observed coordination with known extortion groups, such as ShinyHunters—a group previously associated with major data theft operations, including large-scale Salesforce breaches—suggests a well-funded and professionalized supply chain for data theft and subsequent ransomware or extortion campaigns. The threat actors are not merely interested in credential harvesting for resale; they are executing direct data theft and leveraging that access for immediate financial gain via extortion demands.
Mitigation: Moving Beyond Password Reliance
Okta’s official guidance correctly points toward the necessity of migrating away from legacy authentication methods that are susceptible to real-time interception. The core vulnerability here is the reliance on something the user knows (password) or something the user has (a code generated by a device, which can be coerced).
The industry must accelerate the adoption of phishing-resistant Multi-Factor Authentication (MFA).
- FIDO2 Security Keys and Passkeys: These cryptographic methods rely on public-key cryptography tied to a specific domain origin. Critically, they cannot be phished because the user’s hardware or integrated device verifies the legitimacy of the site’s origin certificate before allowing authentication. The physical presence of the key or the biometric confirmation of a passkey provides a strong anchor against remote manipulation.
- Phishing-Resistant MFA Solutions: Utilizing Okta FastPass or similar native solutions that integrate cryptographic proofs directly into the authentication flow reduces reliance on easily intercepted knowledge factors or simple TOTP codes.
From an organizational defense perspective, the threat necessitates a dramatic increase in security awareness training that specifically addresses voice-based deception. Training must evolve past generic phishing awareness to include recognition of subtle social engineering cues: unexpected IT calls, requests for immediate action on credentials, and the importance of independently verifying unsolicited contact through known, pre-established channels (e.g., calling the official helpdesk number back, not relying on the caller-ID).

Future Trajectories and Security Evolution
The convergence of sophisticated AiTM technology with highly persuasive social engineering techniques sets a new benchmark for digital deception. As attackers integrate more advanced technologies, such as generative AI to create flawless, context-aware voice impersonations (voice cloning), the effectiveness of vishing will only increase.
We can anticipate several future trends stemming from this development:
- AI-Driven Reconnaissance: Threat actors will leverage AI to automate the collection and synthesis of employee data from public and semi-public sources, making the initial reconnaissance phase faster and more comprehensive.
- Ephemeral Phishing Infrastructure: The use of disposable hosting services, like the previously observed Render instances, indicates a strategy of rapid deployment and abandonment of phishing infrastructure to evade takedown efforts. Defenders will need to focus on behavioral detection at the network layer rather than solely relying on domain reputation blacklists.
- Targeting the Identity Perimeter: Security tooling must adapt to monitor the behavior across the identity perimeter in real time. Anomalous authentication sequences—such as a login attempt from a new geographic location immediately followed by a high-value MFA request—must trigger automated session termination or step-up verification, regardless of the successful MFA entry.
The ongoing campaign targeting Okta SSO users is a stark reminder that identity security is no longer purely a technological challenge; it is a continuous battle against human psychology, weaponized by readily available, highly effective commercialized attack tools. The security posture of any organization relying on a centralized IAM system is now directly proportional to the vigilance of its least-informed employee when fielding an unexpected phone call. Investment in phishing-resistant authentication is rapidly transitioning from a best practice recommendation to an operational imperative for survival in the modern threat landscape.

