A significant escalation in the operational sophistication of a prominent Chinese state-sponsored hacking group has been documented, following the deployment of a new iteration of the notorious ToneShell backdoor. This latest iteration is being delivered via a highly advanced, kernel-mode loader, a tactic that grants the malware unprecedented depth of access and stealth within targeted systems. The campaign, primarily focused on government entities across Southeast Asia, signals a determined push by the threat actor to achieve near-total operational invisibility against conventional defenses.
The group linked to this campaign is widely tracked under the moniker Mustang Panda, also known interchangeably as HoneyMyte or Bronze President. This entity has a long and documented history of engaging in cyberespionage operations aimed at geopolitical intelligence gathering, consistently targeting high-value vectors such as governmental agencies, non-governmental organizations (NGOs), and influential think tanks across the globe. The persistent targeting profile underscores the strategic nature of their objectives, moving beyond opportunistic crime toward sustained, state-level intelligence acquisition.
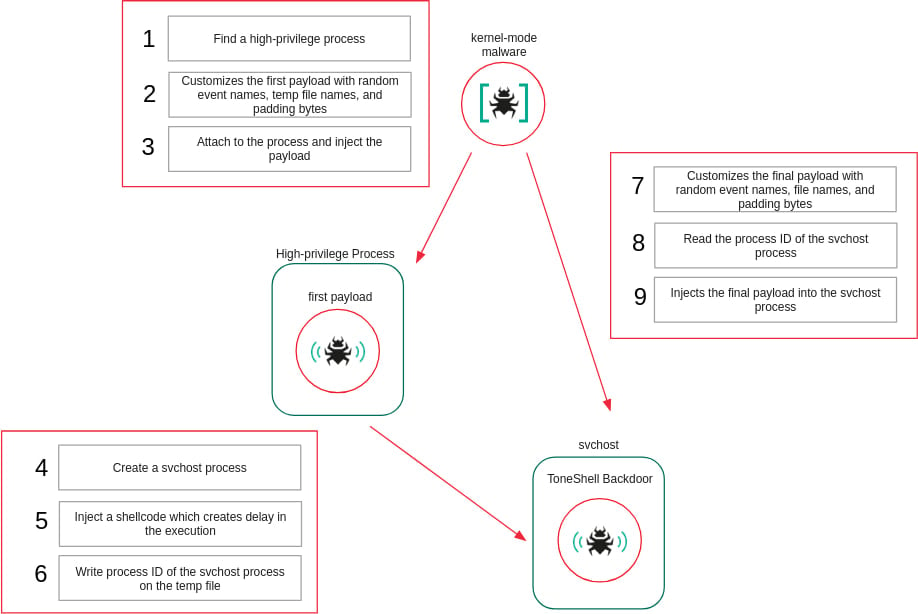
Initial forensic analysis, spearheaded by researchers at Kaspersky, uncovered the malicious components embedded within system drivers on compromised machines located in various Asian jurisdictions, including Myanmar and Thailand. Crucially, the investigation revealed that these recent incursions were not isolated events. The evidence strongly suggests a pattern of sustained compromise, where victims already harbored previous versions of the ToneShell malware, or were previously infected with legacy tools attributed to the same cluster, such as the PlugX remote access Trojan or the ToneDisk USB-borne worm. This indicates that the deployment of the kernel-mode loader represents an evolution of an existing, persistent relationship with the victim environment, rather than a fresh initial access vector.
The Architecture of Stealth: Kernel-Mode Rootkit Implementation
The core innovation in this latest campaign lies in the deployment mechanism: a custom-built mini-filter driver identified as ProjectConfiguration.sys. This driver functions as a sophisticated, albeit malicious, rootkit operating at the deepest privilege levels of the Windows operating system.
Mini-filter drivers are legitimate components designed to interface directly with the Windows file-system Input/Output (I/O) stack. They possess the capability to scrutinize, manipulate, or outright halt file operations—a functionality commonly leveraged by security software, disk encryption utilities, and enterprise backup solutions. By masquerading as such a utility, ProjectConfiguration.sys gains the necessary kernel-mode elevation to execute its objectives covertly.
A critical aspect of the driver’s legitimacy facade is its digital signature. The driver is signed using a certificate that, while ostensibly valid for legitimate purposes, has been either stolen or compromised from Guangzhou Kingteller Technology Co., Ltd. Furthermore, the certificate’s validity window (cited as 2012 to 2015) suggests the attackers are recycling older, potentially less scrutinized signing material to bypass modern certificate transparency checks or to exploit blind spots in legacy trust chains.
The driver’s design employs multiple layers of obfuscation aimed squarely at defeating static analysis tools. Instead of relying on hardcoded imports of necessary kernel APIs—a common red flag for automated scanning—the driver resolves these dependencies dynamically at runtime. This is achieved by iterating through all currently loaded kernel modules and employing function hashing techniques to locate and call the required system functions. This ‘lazy loading’ or on-the-fly resolution significantly complicates static reverse engineering efforts, as the malware’s true dependencies are not immediately apparent in the binary structure.

Once loaded, ProjectConfiguration.sys actively weaponizes its mini-filter status. It registers itself to intercept file system operations specifically related to file deletion and file renaming. When an operation targets the driver file itself—an attempted cleanup or quarantine by an endpoint detection and response (EDR) solution—the driver immediately blocks the request by artificially forcing the I/O operation to return a failure status, effectively rendering itself immutable while the system is running.
Further hardening its presence, the rootkit establishes persistence and protection over its associated service configuration entries within the Windows Registry. It achieves this by registering a dedicated registry callback mechanism. This callback function is programmed to explicitly deny any subsequent attempts by other processes—including security products—to create, open, or modify the registry keys that maintain the malware’s operational settings.
To guarantee precedence over legitimate security countermeasures, the malware carefully selects its mini-filter altitude. In the Windows driver stack, altitude dictates the order of execution; a lower altitude means the driver processes I/O operations first. The attackers configure ProjectConfiguration.sys to register at an altitude deliberately positioned above the reserved range typically utilized by antivirus and EDR solutions. This ensures that the malicious driver inspects and potentially modifies file operations before any security software has a chance to intervene.
Perhaps the most aggressive defense mechanism involves the direct subversion of Microsoft’s native security tools. The driver actively interferes with the operation of Microsoft Defender by targeting the configuration of the legitimate WdFilter driver. It manipulates the settings to prevent WdFilter from being loaded into the crucial I/O stack path, effectively creating a blind spot in the operating system’s primary, built-in defense layer.
Finally, the driver provides crucial protective scaffolding for the user-mode components of the ToneShell payload it injects. It maintains an internal list of Process IDs (PIDs) that are deemed "protected." During the execution of the injected shellcode, the driver actively denies handle access to these protected processes. This prevents user-mode debugging tools, process explorers, or memory scanners from attaching to the running malware process. Once the payload’s critical operations are complete, the protection is meticulously removed, attempting to restore the system state to minimize forensic traces.
Kaspersky analysts highlighted the significance of this architectural shift: "This is the first time we’ve seen ToneShell delivered through a kernel-mode loader, giving it protection from user-mode monitoring and benefiting from the rootkit capabilities of the driver that hides its activity from security tools." This transition from user-mode deployment to kernel-mode bootstrapping represents a paradigm shift in Mustang Panda’s operational tradecraft, prioritizing deep system compromise and evasion over speed or simplicity.
ToneShell’s Evolution: Refinement for Persistence
Beyond the sophisticated loader, the ToneShell backdoor itself has undergone a notable update, incorporating several enhancements aimed at increasing its longevity and reducing its signature footprint across the network.
One key change involves the host identification mechanism. Previous iterations relied on a 16-byte Globally Unique Identifier (GUID) to fingerprint the compromised machine for command-and-control (C2) communication. The new variant has simplified this to a more compact 4-byte host ID marker. While this might seem like a reduction in complexity, it often correlates with efforts to reduce network chatter or align with newly provisioned C2 infrastructure that may utilize shorter identifiers for batch processing.

More critically for evasion, the network communications layer has been significantly overhauled. The malware now implements robust traffic obfuscation techniques, most notably by wrapping its actual command-and-control data within what appear to be legitimate, albeit fake, Transport Layer Security (TLS) headers. This allows the encrypted C2 traffic to blend seamlessly with vast amounts of genuine encrypted web traffic observed across enterprise networks, effectively bypassing basic network intrusion detection systems (NIDS) that rely on TLS handshake analysis for anomaly detection.
The command set supported by the latest ToneShell variant also reflects an expansion of its mission profile. While the precise list of all commands is extensive, the observable additions indicate a focus on expanded reconnaissance and persistence management. Supported remote operations now include granular file system enumeration, advanced process manipulation (including the ability to terminate specific processes), secure data exfiltration pathways, and potentially mechanisms for establishing secondary, redundant communication channels should the primary C2 be disrupted. The inclusion of commands for system configuration modification suggests a goal beyond simple data theft, leaning toward persistent infrastructure control within the target environment.
Industry Implications and Expert Analysis
The adoption of kernel-mode rootkits by groups like Mustang Panda sends clear reverberations throughout the cybersecurity industry, particularly concerning defensive postures against state-sponsored espionage.
Erosion of Trust in System Integrity: The primary implication is the fundamental undermining of operating system integrity. When malware can load a driver that operates at a higher privilege level than most commercial security products, the trust hierarchy inherent in the OS security model is broken. Traditional EDRs that rely on monitoring user-mode process activity or standard kernel callbacks become increasingly vulnerable to being blinded or manipulated by a driver operating with elevated authority.
The Necessity of Hypervisor-Level Visibility: This development strongly reinforces the industry-wide pivot toward security solutions capable of operating at or below the kernel level—specifically, those leveraging hardware virtualization or hypervisor introspection technologies. Memory forensics, as explicitly recommended by Kaspersky, becomes not just a valuable secondary step, but a mandatory primary investigative technique. If a driver is successfully hiding its files and processes from the running OS, the only reliable way to observe its true state is by taking a snapshot of the system memory while it is active, circumventing the malware’s real-time manipulation capabilities.
The Lifecycle of Compromise: The evidence of prior infections (PlugX, ToneDisk) connected to this new deployment suggests a highly mature, multi-stage infiltration strategy. This points to threat actors who are patient, likely utilizing initial, lower-profile access methods to establish a foothold, followed by a measured, strategic escalation to deep-kernel persistence only when necessary for high-value objectives or to secure long-term access against expected clean-up attempts. This methodical approach is the hallmark of highly resourced, state-backed operations.
Impact on Geopolitical Security: Given Mustang Panda’s targeting focus on government and policy organizations in Asia, the use of this technology raises significant diplomatic and national security concerns. The ability to maintain undetectable, long-term surveillance within critical government networks allows for the systematic collection of sensitive political, military, and economic intelligence, providing a distinct advantage to the sponsoring nation-state.
Future Trajectories in Advanced Evasion
This deployment of a kernel-mode loader for ToneShell is not an isolated event; it is indicative of a broader, accelerating trend among advanced persistent threat (APT) actors globally: the race to the bottom of the operating system stack for ultimate evasion.
We can anticipate several subsequent developments based on this trajectory:
-
Wider Adoption of Signed Drivers: Attackers will continue to aggressively pursue valid, albeit compromised, code-signing certificates. The utility of a legitimate-looking signature to bypass driver verification checks and gain initial kernel trust is too high to ignore. Furthermore, expect increased scrutiny on the provenance of all drivers present in enterprise environments, necessitating rigorous certificate whitelisting.
-
Focus on Boot Integrity: As operating systems like Windows introduce more stringent security measures for driver loading (e.g., Secure Boot requirements), threat actors will inevitably shift focus toward compromising the boot process itself. Techniques that allow malware to inject code before the OS security mechanisms fully initialize, or to manipulate the UEFI firmware, will become increasingly common.
-
Counter-Forensics in Memory: Since memory forensics is now the primary detection avenue, threat actors will likely develop counter-forensic measures specifically designed to tamper with or corrupt memory images captured by security tools. This involves detecting the presence of memory acquisition tools and proactively wiping or altering critical data structures before the snapshot is finalized.
-
Exploitation of Supply Chains Beyond Software: While the current attack utilized a compromised third-party driver certificate, future iterations might see direct exploitation of the software supply chain for legitimate hardware or peripheral drivers, embedding malicious code directly into firmware or deeply integrated system software updates, making detection even more challenging as the malware is delivered through an ostensibly trusted vendor channel.
In conclusion, the deployment of the kernel-mode loader for the ToneShell backdoor by Mustang Panda represents a maturation of Chinese cyberespionage capabilities. It forces security practitioners to abandon assumptions about user-mode visibility and instead invest heavily in deep-system integrity monitoring and memory analysis to successfully counter these highly resilient, state-sponsored intrusions.

