PcComponentes, a towering figure in the Spanish and European technology retail landscape, has publicly and emphatically refuted widespread claims suggesting a catastrophic data breach affecting potentially 16 million customers. While the company, which commands an estimated 75 million unique annual marketplace visitors through its extensive catalog of computers, peripherals, and high-end hardware, maintains that its core databases remain impervious to unauthorized intrusion, it has concurrently confirmed the successful exploitation of customer credentials via a credential stuffing campaign. This dual announcement clarifies a significant cybersecurity incident, distinguishing between a deep system compromise and a widespread account takeover attempt fueled by external data leakage.
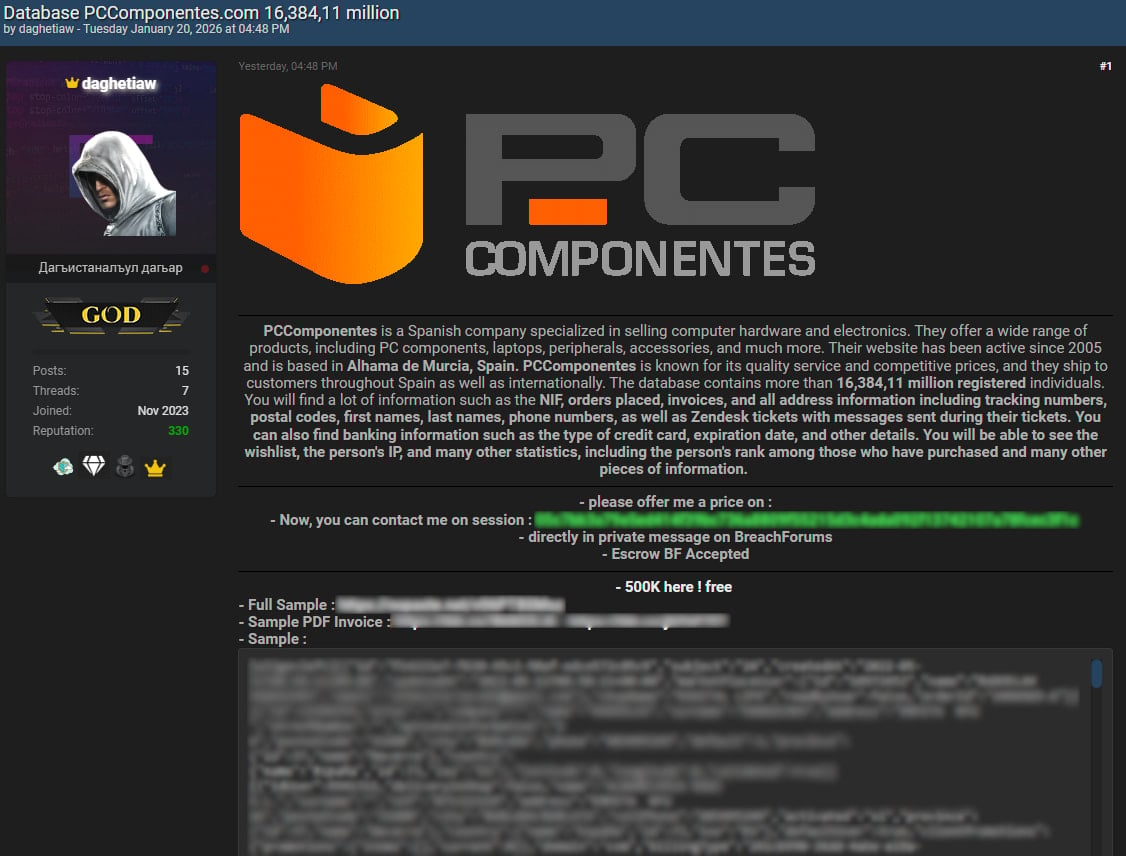
The controversy ignited when a threat actor, identifying themselves under the moniker ‘daghetiaw,’ surfaced online marketplaces disseminating what they purported to be an extensive database extracted from PcComponentes’ infrastructure. The claim asserted the theft of a staggering 16.3 million customer records. To substantiate this, the malicious actor selectively leaked approximately 500,000 records into the public domain while advertising the remainder for sale to the highest bidder. Forensic analysis of the exposed data samples revealed highly sensitive, albeit non-financial, information, including full customer names, physical delivery addresses, contact telephone numbers, historical IP logs, detailed records of product wish lists, and transcripts of customer support interactions routed through the Zendesk platform.
In response to the escalating alarm and the provocative data leak, PcComponentes swiftly initiated an internal security audit. The outcome, presented in a formal corporate statement, categorically denied any evidence of a root-level breach. "There has been no illegitimate access to our databases or internal systems," the firm asserted, directly addressing the scale of the alleged theft. They emphasized that the figure of 16 million potentially affected accounts is statistically unsound, given that the actual base of active PcComponentes accounts is substantially smaller. Crucially, the retailer confirmed a foundational security measure remains intact: no sensitive payment data or customer passwords are ever stored on their primary servers, mitigating the most financially devastating risk scenario.
However, the investigation did confirm the vector of compromise: a sophisticated credential stuffing attack targeting the platform’s authentication layer. This type of attack operates on the principle of credential reuse. Cybercriminals leverage massive caches of usernames and passwords previously compromised in unrelated breaches across the internet. Automated tools then systematically test these stolen pairs against the login portals of high-value targets like PcComponentes, exploiting the common user tendency to employ the same login credentials across multiple services.

Threat intelligence specialists, notably the firm Hudson Rock, provided crucial context, tracing the origin of the credentials used in the stuffing attempt. Their analysis strongly suggests that the login data was not acquired through a direct assault on PcComponentes’ network but rather harvested by sophisticated info-stealing malware residing on end-user devices. As Hudson Rock detailed in their analysis, "Every single email we checked from the threat actor’s sample was found in existing infostealer logs." This indicates that the initial compromise happened at the endpoint—the customer’s personal computer or mobile device—where malware silently exfiltrated stored credentials, sometimes dating back as far as 2020. A verification snapshot published by Hudson Rock illustrated this finding starkly, showing that all tested email addresses in the attacker’s sample were already cataloged as compromised via prior infostealer infections.
PcComponentes’ official disclosure outlined the specific categories of information exposed for the limited subset of accounts successfully compromised via this credential stuffing method. While the full list remains subject to ongoing internal review, the confirmed exposed data elements for these specific accounts included names, physical addresses, contact numbers, and historical support query data. The fact that this information was exposed, even in limited numbers, underscores the danger of relying solely on passwords when security hygiene is weak across the broader digital ecosystem.
The retailer’s immediate and decisive remediation strategy is indicative of modern cybersecurity best practices following an authentication attack. To staunch any further unauthorized access, PcComponentes has deployed several layered defenses. They have immediately enforced the use of CAPTCHA mechanisms on all login interfaces to disrupt automated bot activity. More significantly, they have instituted a mandatory, non-negotiable activation of Two-Factor Authentication (2FA) across their entire user base. Furthermore, the company performed a global invalidation of all active user sessions. This means every user, regardless of their prior login status, has been forcibly logged out and must re-authenticate, which, in turn, triggers the requirement to enable 2FA before access is reinstated.
Beyond these technical countermeasures, PcComponentes issued a clear advisory to its customer base, reinforcing fundamental digital hygiene. They stressed the importance of using strong, unique passwords for every online service—a direct countermeasure to the credential stuffing threat—and strongly recommended the adoption of reputable password management solutions. Vigilance against subsequent phishing attempts, often launched by threat actors capitalizing on recently confirmed user data, was also highlighted as paramount.
Industry Implications: The Pervasiveness of Credential Stuffing
This incident serves as a critical, real-world illustration of a growing trend in cybercrime: the shift from large-scale, direct database breaches to targeted, automated account takeovers (ATOs) fueled by readily available, compromised credential sets. For e-commerce platforms handling high volumes of transactions and customer data, credential stuffing represents a persistent, low-cost threat vector.

The incident highlights a fundamental vulnerability in the digital economy: the dependency on end-user security practices. Major retailers like PcComponentes can implement state-of-the-art perimeter defenses, but these safeguards become insufficient when user credentials, obtained from less secure forums or infected personal machines, are used to mimic legitimate access. The findings from Hudson Rock, linking the attack directly to infostealer logs, cement the concept that customer devices are often the weakest link in a large organization’s security chain. This necessitates a greater focus on client-side security awareness and the industry-wide push toward ubiquitous MFA adoption, which PcComponentes has now rightly prioritized.
Expert Analysis: The Nuance Between Breach and Attack
From a cybersecurity risk management perspective, the distinction PcComponentes has drawn between a "data breach" (unauthorized access to internal servers) and a "credential stuffing attack" (leveraging external credentials for account access) is vital for regulatory compliance and public perception. A true data breach implies a failure in the organization’s internal security architecture, potentially exposing proprietary systems or vast troves of unencrypted data. In contrast, a credential stuffing attack primarily signals a failure in authentication protocols or user behavior, though the outcome—unauthorized access to user accounts—is often functionally similar for the affected customer.
The data exposed—order history, addresses, support tickets—while sensitive, is less catastrophic than a breach of payment card industry (PCI) data or hashed passwords. However, the exposure of support tickets via Zendesk is noteworthy. These logs can often contain personally identifiable information (PII) discussed during troubleshooting, or even, in poorly managed environments, incidental disclosure of partial account details, providing fodder for social engineering attacks later on.
The decision to immediately roll out mandatory 2FA is a high-impact, necessary response. While it causes short-term user friction—the mass log-out and re-authentication process—it is the most effective technical control against credential stuffing. By requiring a second factor, the stolen username/password pair becomes functionally useless to the attacker unless they also control the user’s second factor (usually a smartphone).
Future Impact and Security Trends
This episode underscores several emerging security imperatives for large-scale retailers:
-
Proactive Credential Monitoring: Retailers must invest more heavily in continuous monitoring of dark web and underground forums, not just for mentions of their brand, but for credential dumps that match their user base patterns. Identifying these external leaks allows for proactive alerts to users before a stuffing attempt occurs.
-
Frictionless MFA Implementation: While mandatory 2FA deployment can be disruptive, the industry trend is moving toward less intrusive, more seamless second-factor methods, such as FIDO2 hardware keys or biometrics integrated directly into mobile applications, reducing user resistance to adoption.
-
Device Trust and Behavioral Biometrics: Given the link to infostealer malware, organizations are increasingly looking at device fingerprinting and behavioral biometrics to identify when a legitimate user account is suddenly being accessed from a device exhibiting anomalous characteristics (e.g., a known compromised IP range or a device profile that has never logged in before).
-
Data Minimization: PcComponentes’ assertion that they do not store passwords or financial details is a best practice, but the scope of the exposed PII—addresses, wish lists, support logs—reinforces the need for data minimization strategies. If the data is not collected or retained long-term, it cannot be stolen.
The incident at PcComponentes, therefore, is less a story of a catastrophic internal system collapse and more a cautionary tale about the interconnectedness of digital security. It highlights that even highly secure enterprise platforms are vulnerable to the weak security habits endemic across the wider internet, forcing companies to not only secure their own walls but also to actively manage the security posture of their user base. The comprehensive response, balancing transparency regarding the credential stuffing with aggressive protective measures like mandatory 2FA, sets a benchmark for how major retailers should manage these increasingly common, externally driven account compromise events.

