The digital security landscape is experiencing a notable escalation in the sophistication of social engineering tactics, particularly concerning high-value targets like Facebook accounts. Over the preceding six months, threat actors have demonstrably shifted allegiance toward leveraging the Browser-in-the-Browser (BitB) technique, a method engineered to dismantle the user’s fundamental trust in their web environment. This technique, initially conceptualized and demonstrated by security researcher "mr.d0x" in 2022, has transitioned rapidly from a proof-of-concept exploit into a core component of real-world, large-scale phishing operations targeting platforms including Meta’s Facebook ecosystem and gaming platforms like Steam.
The continued focus on Facebook is unsurprising given its monumental scale, boasting over three billion active users globally. This vast user base represents an irresistible surface area for malicious actors aiming to harvest personally identifiable information (PII), propagate widespread scams, or engage in complex identity fraud schemes. Security telemetry gathered by firms like Trellix underscores this persistent threat, detailing the observed rise in these highly deceptive campaigns.
Deconstructing the Browser-in-the-Browser Mechanism
The core innovation of the BitB attack lies in its ability to simulate the operating system’s native browser interface—or at least, a near-perfect facsimile thereof—entirely within the context of the compromised webpage. In a standard phishing attempt, a user navigates to a malicious site and is presented with an embedded form or redirected to a convincing clone. However, the BitB method introduces a layer of visual deception that exploits deep-seated cognitive habits.

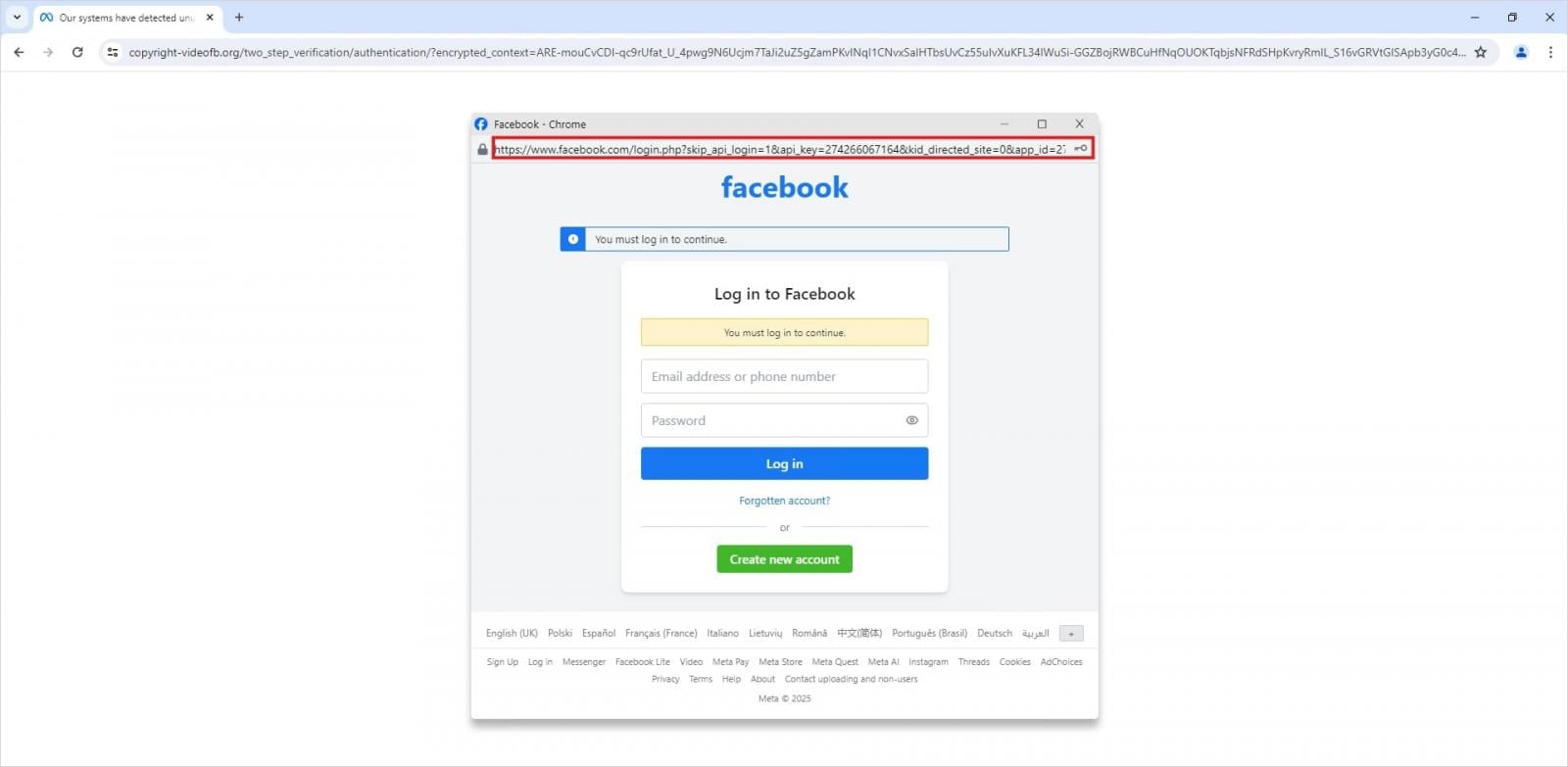
When a user lands on an attacker-controlled webpage, the payload triggers the creation of a meticulously crafted, seemingly independent pop-up window. This window is not a genuine browser instance managed by the operating system; rather, it is an elaborate rendering achieved through an HTML <iframe>. This iframe is specifically styled and configured to mimic the visual attributes of a legitimate authentication dialogue. Crucially, attackers can manipulate properties such as the window title bar, the address bar display (often showing a legitimate-looking URL, or even a stylized, yet ultimately fake, address bar), and the window’s border elements to create the illusion of a separate, trusted application context.
This visual fidelity is the key differentiator. Users are trained to look for tell-tale signs of a malicious redirect—a strange URL in the main browser window, a poorly rendered page, or an unexpected application launch. The BitB technique preempts these checks by placing the credential entry point inside a visual container that looks identical to the trusted authentication modal that users encounter daily when interacting with services like Facebook, Google, or Microsoft.
Evolving Lures: Scenarios Exploiting User Panic and Compliance
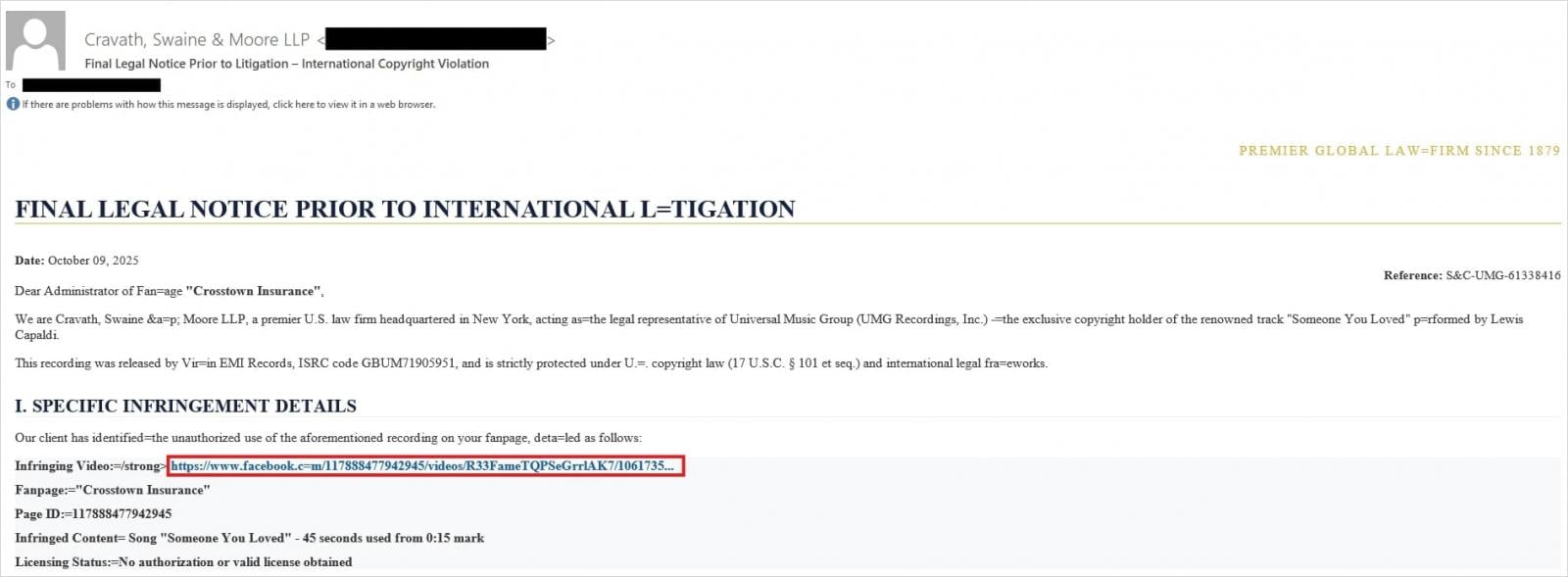
The effectiveness of the BitB technique is amplified by the narrative context provided in the accompanying lure—typically a phishing email. Trellix analysis highlights that recent campaigns targeting Facebook users employ highly specific, high-pressure scenarios designed to bypass critical thinking. These include:
- Copyright Infringement Allegations: Scenarios involving law firms demanding immediate action regarding alleged intellectual property violations, threatening swift and permanent account suspension if compliance is not met.
- Security Breach Notifications: Fake alerts from Meta Security, claiming unauthorized login attempts or suspicious activity, urging the user to "verify" their identity immediately via a provided link.
- Policy Violation Threats: Notifications asserting breaches of community standards, often implying that the account is flagged and requires prompt re-authentication to avoid disabling.
To enhance the perceived legitimacy and evade automated security scanning, attackers are integrating further obfuscation layers. This often involves the use of URL shorteners, which conceal the final malicious destination, and the inclusion of mock security challenges, such as fake CAPTCHA pages, intended to increase the user’s investment in the process before the final credential capture.

The Infrastructure Play: Abuse of Trusted Cloud Services
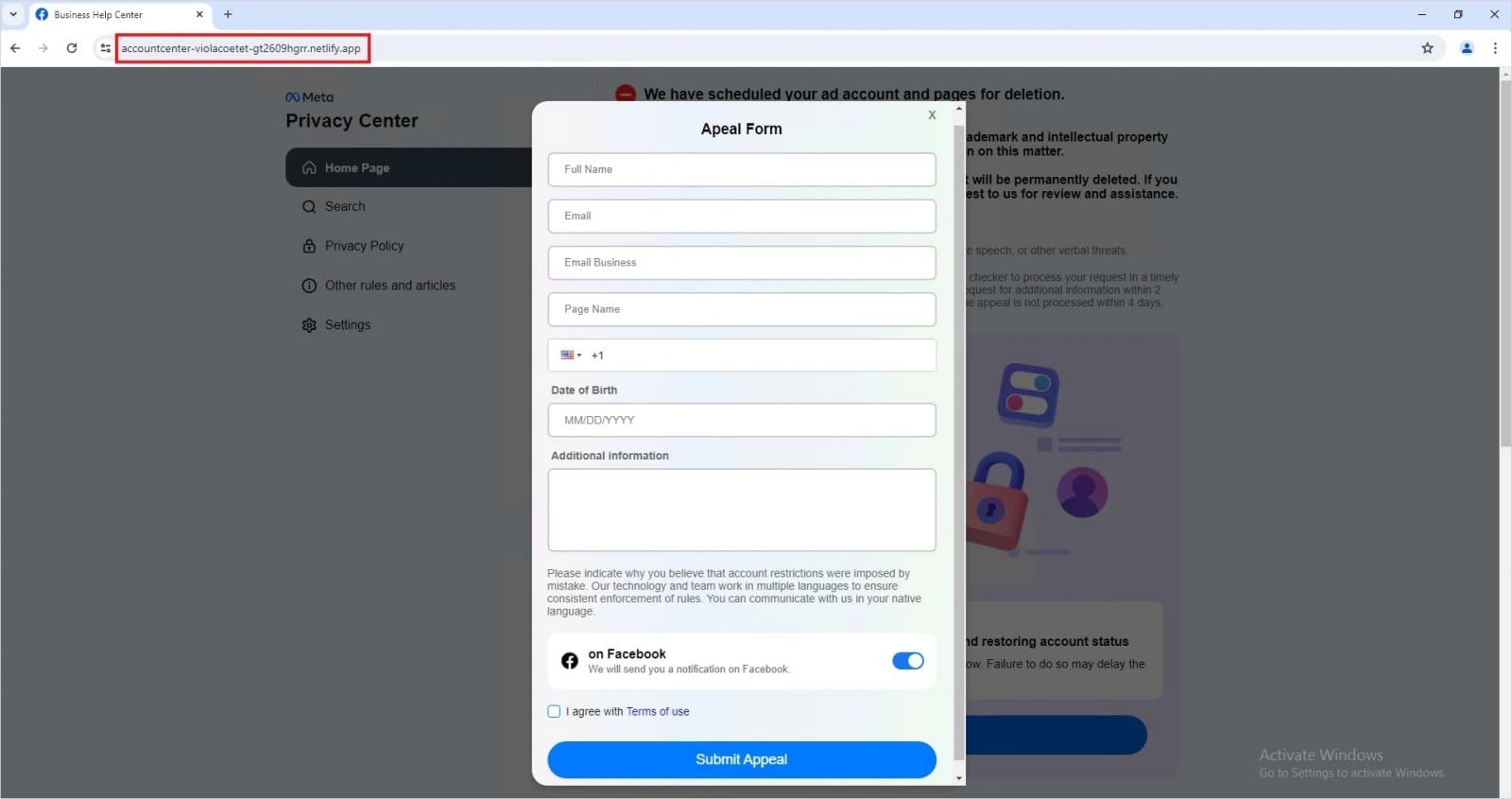
A significant strategic evolution observed in these campaigns, beyond the visual deception of BitB, is the wholesale abuse of established, trusted cloud infrastructure. Instead of relying on newly registered, easily blacklisted domains, threat actors are heavily utilizing legitimate, high-reputation services such as Netlify and Vercel to host their phishing landing pages.
This practice introduces a substantial hurdle for traditional domain reputation filtering. When a security system encounters a link pointing to a Netlify subdomain, it often registers the destination as "safe" because the underlying infrastructure provider is trusted by default. Furthermore, these compromised cloud environments are frequently used to host convincing replicas of legitimate portals, such as Meta’s Privacy Center, subsequently redirecting users into forms disguised as account appeal mechanisms. This collection of PII through fraudulent appeal processes represents a more insidious form of data exfiltration than simple credential theft alone.
As articulated in threat intelligence reports, this infrastructure abuse is critical: "The key shift lies in the abuse of trusted infrastructure, utilizing legitimate cloud hosting services like Netlify and Vercel, and URL shorteners to bypass traditional security filters and lend a false sense of security to phishing pages." The BitB technique, in this context, becomes the final, devastating mechanism deployed after the initial trust barrier (the legitimate hosting platform) has been successfully navigated.
Industry Implications and Expert Analysis
The widespread adoption of the BitB technique signifies a maturation of the cybercriminal ecosystem. It moves phishing from a low-skill, high-volume activity to a more tailored, high-impact operation. The reliance on sophisticated front-end rendering techniques suggests that the toolkits facilitating these attacks are becoming democratized and more user-friendly, lowering the technical barrier to entry for complex social engineering.
From an industry standpoint, this development forces a critical re-evaluation of endpoint security assumptions. Historically, security measures have focused heavily on URL inspection, SSL certificate validation, and examining the overall browser window’s properties. BitB attacks bypass these checks by operating entirely within the rendering engine of the legitimate browser instance. The malicious iframe inherits the security context and visual legitimacy of its parent window.
Security experts emphasize that the visual check is the only reliable defense left for the end-user in these scenarios. The defining characteristic of an iframe-based element, regardless of how well it is styled, is its binding to the parent window. A true, OS-level browser window can be resized, moved independently across the screen, and potentially display different native chrome elements (like context menus). A BitB pop-up, being an element within the webpage DOM, cannot be dragged outside the boundaries of the initial, compromised browser tab. This physical limitation serves as the most immediate, albeit subtle, indicator of compromise.
The parallel increase in sophisticated data collection, evidenced by the fake Privacy Center appeal forms hosted on reputable CDNs, suggests that attackers are not just seeking immediate account access but are building comprehensive profiles on victims, potentially for use in synthetic identity fraud or highly targeted spear-phishing later on.
Future Trajectories and Mitigation Strategies
The arms race between attackers and defenders will inevitably lead to further innovation on both sides. We can anticipate that threat actors will refine their BitB implementations to incorporate more dynamic elements, perhaps simulating loading bars or even attempting to replicate minor, erratic behaviors of native browser windows to defeat more complex behavioral analysis tools. Furthermore, the integration of generative AI into the creation of these phishing kits could lead to hyper-realistic, context-aware social engineering scripts that adapt dynamically based on user interaction data scraped from the initial landing page.
For organizations and individual users, adaptation requires a paradigm shift in authentication verification protocols:
1. Embrace Out-of-Band Verification: The most robust defense remains avoiding embedded links entirely. If a notification regarding an account status, security alert, or infringement claim is received via email, the user must manually open a new browser tab, navigate directly to the service provider’s official homepage (e.g., facebook.com), and check for alerts within their authenticated session. This ensures the user is operating within a verified environment, independent of any malicious redirects.
2. Scrutinize Window Mobility: As highlighted by researchers, users must actively test the boundaries of any login prompt. Attempting to click and drag the suspicious pop-up outside the main browser window is a crucial diagnostic step. If the window remains rigidly confined to the parent page, it is almost certainly an embedded iframe and should be treated as compromised.
3. Mandatory Multi-Factor Authentication (MFA): While MFA is not a panacea against credential theft via phishing, it acts as a critical backstop. Even if the attacker successfully captures a username and password via a BitB attack, a strong MFA implementation—especially hardware-based keys or authenticator apps over SMS—will prevent immediate account takeover, buying the victim time to detect and remediate the breach. Organizations should mandate the use of phishing-resistant MFA solutions where available.
4. Endpoint Security Evolution: Security vendors must enhance endpoint detection and response (EDR) capabilities to specifically monitor for the creation of DOM elements that mimic native window APIs or attempt to override standard browser chrome functionality within the rendering pipeline. Detecting the specific JavaScript techniques used to forge these iframes, rather than just the destination URL, will become increasingly vital.
In summary, the integration of the Browser-in-the-Browser technique with the strategic use of legitimate cloud infrastructure represents a significant and alarming inflection point in large-scale social engineering campaigns targeting billions of users. Defending against this threat demands heightened user vigilance, a commitment to out-of-band verification practices, and an ongoing evolution in security tooling capable of peering beyond superficial visual cues to analyze the underlying structure of web interactions.

