The pervasive reliance on phishing click-through rates as the primary benchmark for email security effectiveness represents a significant strategic miscalculation within many security operations centers (SOCs) and executive boardrooms. This metric, easily quantifiable and readily digestible for quarterly reports, offers a dangerously superficial view of an organization’s true exposure. Treating click rates as the bellwether of security posture is akin to monitoring only the surface ripple while ignoring the underlying current. While a low click rate might satisfy immediate compliance checks, it provides negligible predictive value regarding the actual financial and operational fallout of a successful breach.
The fundamental flaw in this measurement philosophy stems from a misplaced emphasis on the initial point of intrusion—the phishing email itself—rather than the subsequent exploitation pathway. Phishing, whether successful via a malicious link, an infected attachment, or social engineering, is merely the access vector. The true security crisis unfolds after the attacker has successfully navigated the perimeter and established a foothold within the cloud workspace environment.
The Evolution of the Threat Landscape: Beyond the Inbox Filter
To appreciate why click rates fail, we must contextualize the modern threat landscape. Traditional perimeter defenses, heavily reliant on advanced threat protection (ATP) filtering for inbound email, have become increasingly porous against sophisticated, multi-stage attacks. Attackers are adapting rapidly to bypass static signature analysis and even rudimentary AI filters.
Furthermore, the narrative that email security solely concerns stopping unsolicited malicious messages is outdated. A growing segment of high-impact compromises originates not from a user clicking a dodgy link, but from credential theft, session hijacking, or the exploitation of legitimate, often over-privileged, third-party application integrations within the cloud office suite (e.g., Microsoft 365 or Google Workspace). These "inbox breaches without any phishing attack at all" bypass the very systems designed to measure click success or failure entirely.
When security professionals ask, "How effective are we?" and the answer is based on a 2% click rate, they are fundamentally asking the wrong question. The meaningful, CISO-level query must be: "If an attacker establishes a session within a production mailbox, what is the potential blast radius, and how rapidly can we neutralize their lateral movement and data exfiltration capabilities?" This shifts the metric from prevention efficacy to intrinsic resilience.
The Inadequacy of Current Maturity Models
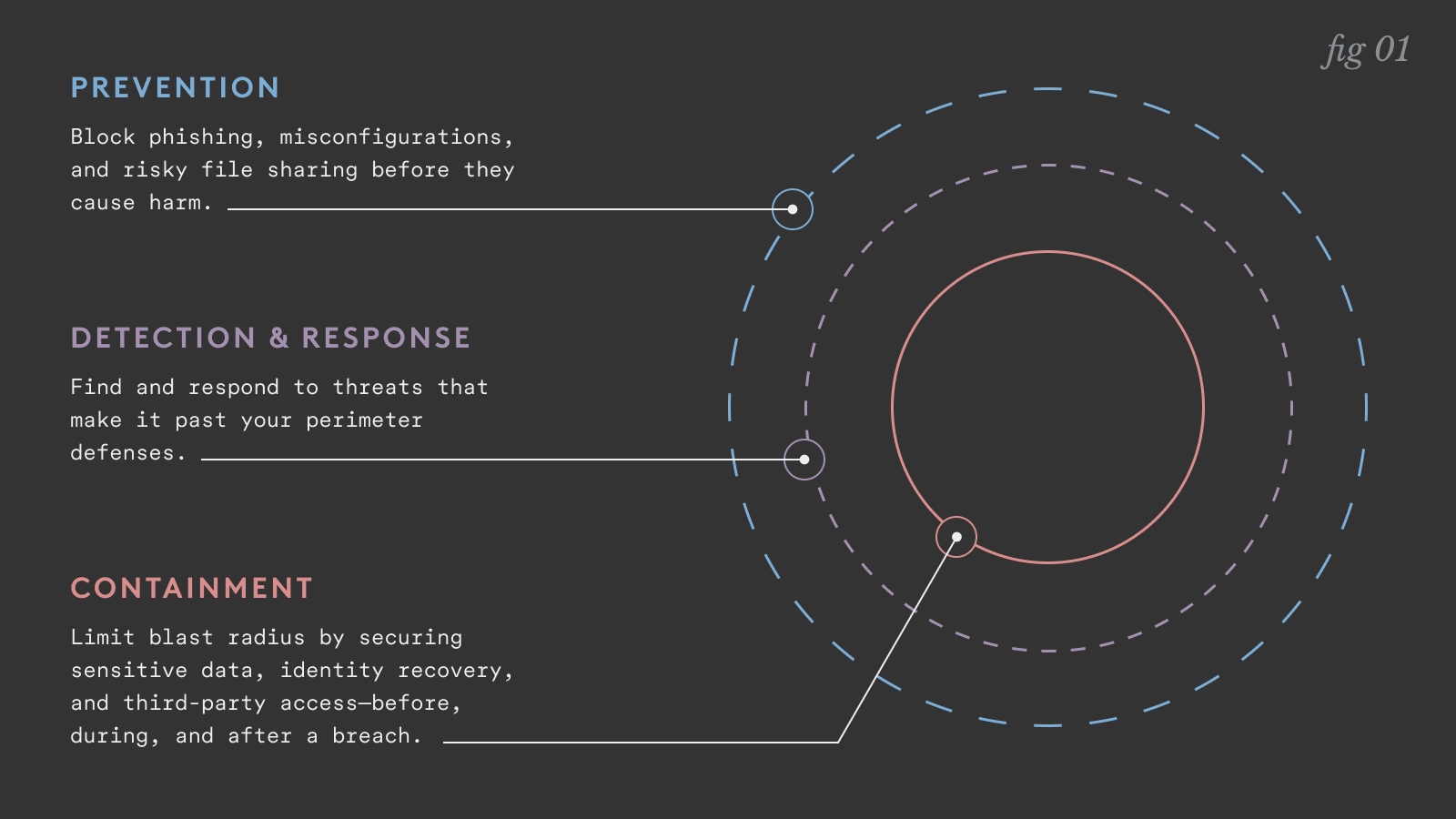
Current cybersecurity maturity models often exhibit a heavy bias toward preventative measures. Organizations typically invest heavily in first-generation defenses: spam filters, URL sandboxing, and endpoint detection and response (EDR). These efforts constitute the "Prevention" layer in a robust security architecture. While essential, over-reliance on this layer creates dangerous blind spots.

The standard framework for security analysis involves three core capabilities: Prevention, Detection/Response, and Containment.
- Prevention: Stopping the initial attack from succeeding. (Where click-rate monitoring lives.)
- Detection and Response (D&R): Identifying that a breach has occurred (e.g., anomalous login locations, unusual file access patterns) and initiating a human-led investigation or automated alert.
- Containment: The immediate, automated actions taken to sever the attacker’s ability to cause further damage once a compromise is confirmed or strongly suspected.
Most organizations achieve moderate success in Prevention, often due to high vendor saturation. D&R capabilities are improving but frequently suffer from alert fatigue and slow manual triage, meaning the window between detection and effective response is often too wide. Critically, the capability for effective, rapid Containment remains the Achilles’ heel for the vast majority of enterprises.
Multi-Factor Authentication (MFA), often touted as the ultimate defense, is not a panacea. Advanced techniques like MFA prompt bombing, session cookie theft, and the use of compromised application tokens can grant attackers persistent access to cloud environments that bypass traditional MFA checks entirely. When compromise is treated as inevitable—a fundamental axiom in zero-trust philosophy—the focus must pivot to minimizing the dwell time and impact of that inevitable breach.
Containment: The Unsung Hero of Cybersecurity Resilience
Containment is the technological equivalent of deploying airbags and reinforced chassis into a vehicle, regardless of how good the driver’s record is. It is the set of proactive, pragmatic controls designed to neutralize the attacker’s post-compromise objectives before they can materialize into a business disaster.
If Prevention stops the initial breach, and D&R confirms the attacker’s presence, Containment executes the critical surgery. This involves real-time manipulation of the compromised environment to limit data access, revoke privileges, and halt exfiltration channels.
What does effective containment look like in the context of an email/cloud compromise? It means immediate, automated action against the attacker’s primary goals:
- Revoking Malicious Access: Immediately terminating active attacker sessions, invalidating compromised session tokens, and isolating the affected user account from sensitive resources without waiting for manual security team sign-off.
- Data Lockdown: Automatically identifying and revoking permissions on documents or mailboxes that the attacker has begun accessing or exporting, even if the initial phishing email only targeted a low-level employee.
- Third-Party App Control: Instantly disabling or revoking credentials for any third-party applications that the compromised account recently authorized, which often serve as persistent backdoors into the environment.
- Internal Reconnaissance Disruption: Automatically deleting or quarantining suspicious internal emails sent by the compromised account (e.g., internal spear-phishing attempts directed at finance or executive assistants), thereby stopping the spread of the attack laterally within the organization.
These actions require deep integration and contextual awareness within the cloud workspace itself—something traditional inbound email gateways cannot provide. They require a shift from endpoint/gateway security to identity and workload security within the collaboration platforms.
The Operational Burden: Why Manual Containment Fails
The main obstacle preventing organizations from adopting mature containment strategies is operational bandwidth. In a large enterprise, a single successful phishing or credential theft incident can generate hundreds of alerts related to file access, sharing changes, and unusual API calls. Manually triaging every one of these events is impossible. Security teams are drowning in data, leading to analysis paralysis and delayed remediation.
This is where intelligent automation becomes non-negotiable. Effective containment must move beyond simple alerts to automated remediation workflows. Systems must be capable of ingesting signals from across the cloud ecosystem (email activity, file access logs, application authorization status) and applying predefined, context-aware playbooks instantly.
For example, if a user account suddenly attempts to download 50 sensitive documents from SharePoint and simultaneously initiates an external share via a cloud-synced drive, an automated system should execute a three-pronged containment response within seconds: suspend the user’s external sharing capability, alert the incident response team, and flag the documents for immediate review—all without a Tier 1 analyst needing to confirm the obvious. This transition moves the human analyst from being a low-level triaging bot to a high-level strategic decision-maker.
Metrics That Actually Quantify Risk
If the click rate is merely the tide, security leaders need metrics that reflect the actual depth and velocity of the water threatening to swamp the vessel. The focus must shift entirely to post-compromise risk quantification:
- Time to Containment (TTC): This is the paramount metric. It measures the duration from the moment a compromise indicator is logged within the cloud environment to the moment the attacker’s ability to cause further damage is neutralized. A TTC measured in hours or days is unacceptable; mature security mandates TTC measured in minutes or seconds for critical assets.
- Blast Radius Index (BRI): This metric quantifies the number of high-value assets (e.g., executive mailboxes, source code repositories, PII databases) that an attacker could access or manipulate during their dwell time before containment. A low BRI indicates effective segmentation and tight permission controls, even if the initial compromise was successful.
- Privilege Escalation Velocity: Tracking how quickly a compromised standard user account is able to pivot to administrative roles or gain access to sensitive data stores. High velocity indicates overly permissive roles or weak internal access governance.
- Remediation Automation Rate: The percentage of identified post-compromise threats that are automatically contained versus those requiring manual intervention. A high automation rate directly correlates with a low TTC.
The Future Imperative: Security by Design for Cloud Workloads
The trajectory of cyber threats indicates that the battleground is permanently shifting inward—from the network edge to the collaboration suite itself. Attackers understand that email clients and cloud storage platforms are the primary repositories of corporate intelligence, strategic communications, and financial data.
Future security frameworks will demand "security by design" principles embedded directly into the cloud workload management layer. This means abandoning siloed tools that only look at the email transport layer and embracing platforms that treat the entire cloud office suite—email, file storage, calendar, and third-party application integrations—as a single, interconnected security surface requiring continuous, automated governance.
Obsessing over the ability of a user to resist a well-crafted lure is a reactive, low-yield activity. The modern enterprise must adopt the mindset that an attacker will eventually gain access. Therefore, the industry must stop measuring the minor inconvenience of a click and start rigorously measuring the speed and efficacy of the digital seatbelts and airbags that prevent that single point of failure from becoming an existential organizational catastrophe. The next decade of security success will be defined not by how many phishing emails are stopped, but by how quickly we can render a successful intrusion inert.

