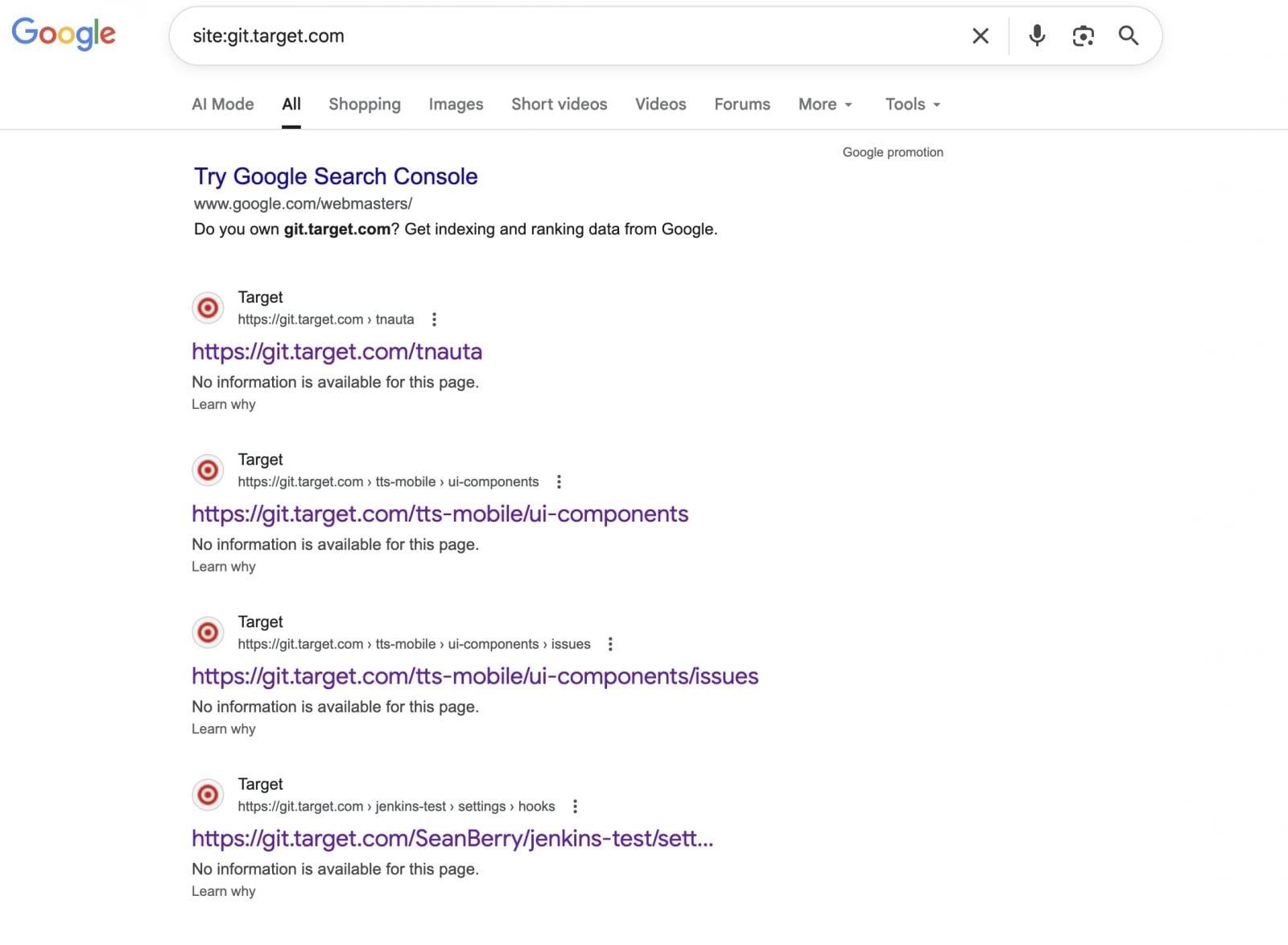
The digital infrastructure supporting one of the nation’s largest retailers, Target Corporation, experienced immediate and drastic remediation following the emergence of claims that an unknown threat actor had successfully exfiltrated a substantial volume of proprietary source code. This incident, which unfolded rapidly across public and underground digital ecosystems, culminated in the swift inaccessibility of Target’s dedicated internal Git repository server, git.target.com, signaling a high-priority internal security response.
The initial indicators of compromise materialized last week when intelligence sources flagged activity within clandestine online forums frequented by threat actors. The actor purportedly possessed access to Target’s internal software development environment and began publicly advertising this access. As proof of concept—a common tactic used by data vendors to entice potential buyers—the threat actor established several repositories on Gitea, a popular self-hosted Git platform analogous to industry mainstays like GitHub or GitLab. These public-facing Gitea containers were positioned as mere samples, previewing a significantly larger cache of proprietary data purportedly slated for auction to the highest bidder via private channels.

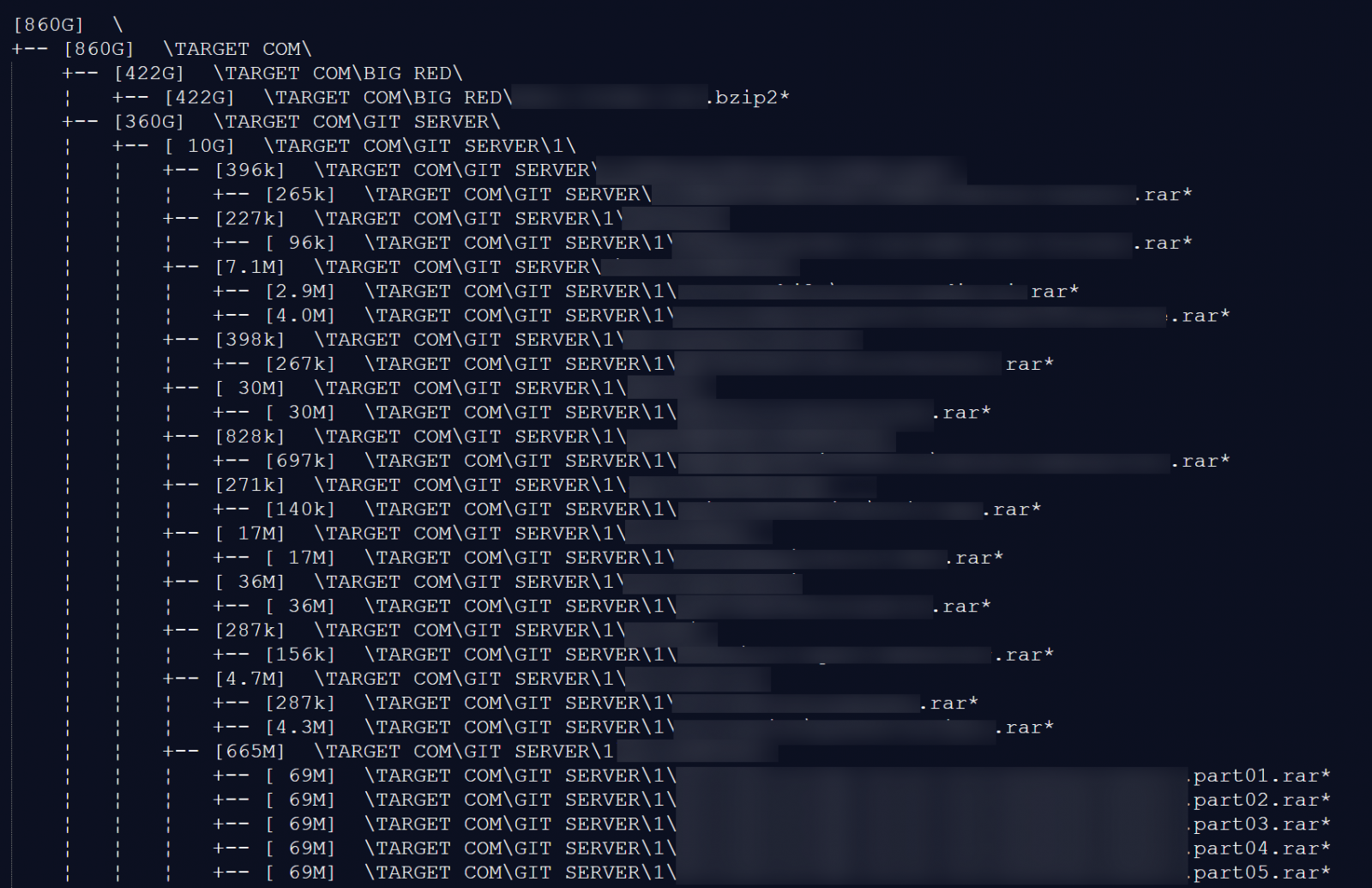
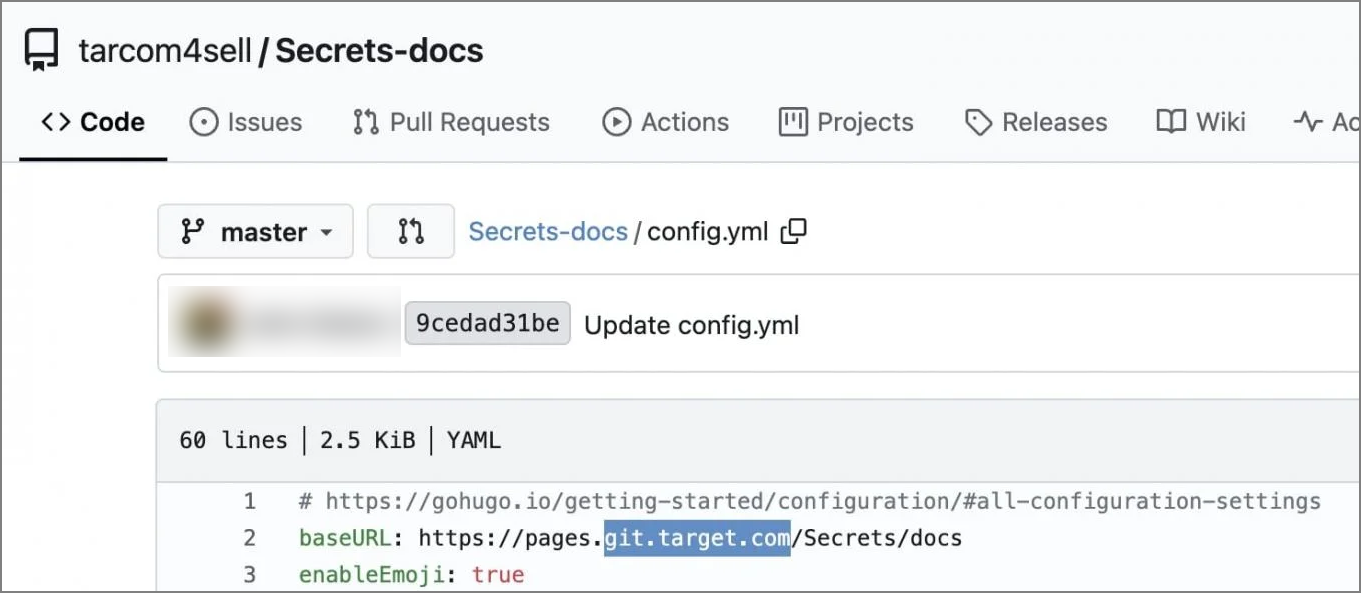
The evidence presented in these sample repositories was highly suggestive of an internal origin. Each contained a file labeled SALE.MD, which detailed an extensive index of files and directory structures supposedly constituting the full dataset. This index reportedly spanned over 57,000 lines, mapping to an estimated total archive size approaching 860 gigabytes of data. Crucially, metadata embedded within the code commits and accompanying documentation made reference to specific internal Target development servers, internal API endpoints (such as references to confluence.target.com), and, most alarmingly, cited the names of current senior and lead engineering personnel within the corporation.
The repository names themselves hinted at core corporate functions, featuring identifiers that strongly suggested interaction with systems related to inventory management, customer loyalty programs, and potentially core point-of-sale or enterprise resource planning (ERP) components. While the full scope of the 860 GB archive remains unverified externally, the granularity and specificity of the sample data presented a compelling, albeit unconfirmed, case for a significant intellectual property (IP) theft. This material did not correlate with Target’s established open-source contributions hosted on public platforms like GitHub, reinforcing the assertion that the data originated from secure, private development repositories.
Upon receiving initial indicators and specific links to the Gitea repositories on Thursday, this publication formally contacted Target Corporation for comment regarding the alleged security incident. The immediate aftermath saw a rapid escalation of defensive measures. By Friday and into Saturday, the Gitea repositories publicized by the threat actor began resolving to ‘404 Not Found’ errors, indicative of a coordinated removal or takedown request being successfully executed.

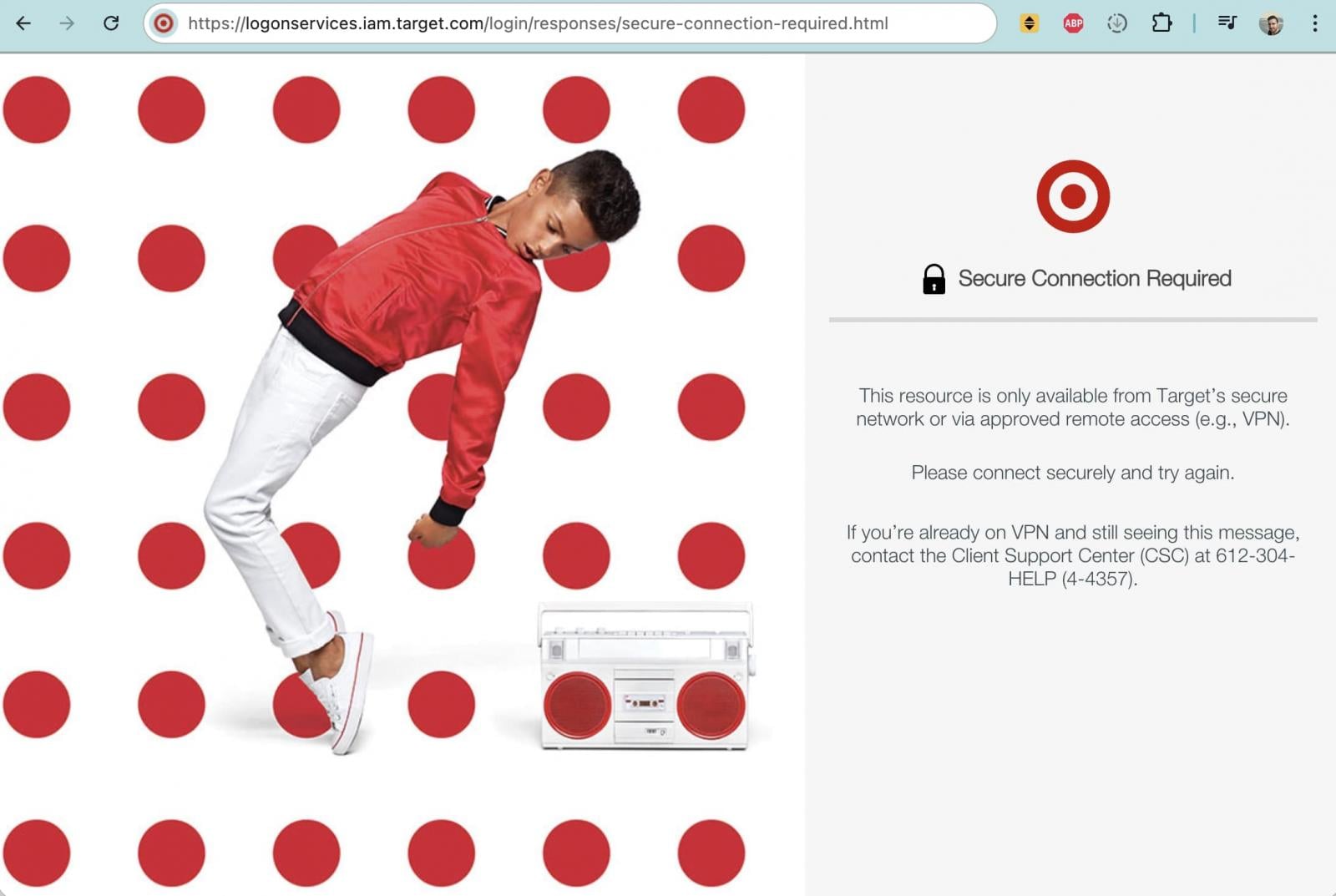
Concurrently, the corporation enacted a drastic quarantine measure concerning its own development infrastructure. The subdomain dedicated to version control, git.target.com, which previously resolved to a login gateway requiring connection via a secure corporate network or VPN, became completely unresponsive to external internet requests by Saturday. This move strongly suggests an immediate internal assessment, isolation, and potential rebuilding or forensic imaging of the compromised source code management systems. The sudden silence of the Git server speaks volumes regarding the severity with which Target is treating the potential exposure of its proprietary engineering assets.
Contextualizing the Threat: Source Code as High-Value Target
The alleged theft of source code represents a fundamentally different class of cyber threat compared to the widely publicized data breaches targeting customer payment information, such as the infamous 2013 incident that severely impacted Target’s reputation. While the 2013 breach involved the mass exfiltration of Personally Identifiable Information (PII) and payment card details—a direct threat to consumer finance—the compromise of source code strikes at the heart of a company’s technological competitive edge and long-term security posture.
Source code is the blueprint for all of a company’s digital operations. For a retailer of Target’s scale, this includes proprietary algorithms for logistics optimization, inventory forecasting, dynamic pricing engines, personalized marketing logic, and, critically, the underlying code for their e-commerce platforms and in-store transaction systems.
From an attacker’s perspective, owning the source code is extraordinarily valuable. It allows for deep reconnaissance, revealing architectural weaknesses, hardcoded credentials, insecure coding practices, and the logic governing sensitive business processes. This intelligence can be weaponized in several ways:
- Supply Chain Attacks: Understanding the dependencies and integration points allows attackers to craft highly precise follow-on attacks against vendors or integrated third-party systems that rely on Target’s software frameworks.
- Zero-Day Discovery: Attackers can methodically audit the code to discover logic flaws or buffer overflows that might not be immediately apparent through dynamic testing, enabling the creation of sophisticated zero-day exploits targeting Target’s live systems.
- Competitive Espionage: Competitors, or nation-state actors interested in understanding the operational capabilities of major U.S. retailers, gain insight into efficiency models and proprietary business logic.
The fact that the adversary immediately moved to monetize this information, rather than using it for a quiet, persistent infiltration, suggests the primary motive might be financial gain through the sale to a specialized buyer, though the residual risk remains high.
Industry Implications and Expert Analysis
The incident serves as a stark reminder of the evolving landscape of enterprise risk, particularly concerning the security of Software Development Kits (SDKs) and Version Control Systems (VCS). Modern application security (AppSec) strategies must now treat the source code repository—whether hosted internally on platforms like Git or externally via SaaS offerings—as one of the most critical Crown Jewels of the organization.
Industry analysts point to the critical failure point that allowed this potential exposure: the security perimeter around the development environment. In many large organizations, development environments, while logically segmented from production, often retain overly permissive access controls or rely too heavily on network segmentation rather than robust, identity-centric security models. The presence of internal server names and employee identifiers in commit logs suggests either a configuration error allowing exposure of internal metadata or, more concerningly, the compromise of credentials belonging to high-privilege developers who had access to both the Git server and potentially the code itself.
"When source code repositories become the vector for a data leak, it signifies a breakdown in the ‘least privilege’ principle within the CI/CD pipeline," notes Dr. Evelyn Reed, a specialist in enterprise architecture security. "If an attacker can map out internal system architecture and identify specific engineers through commit history, it implies that the attacker either gained access via a developer’s compromised workstation or successfully bypassed authentication to the Git server itself. The subsequent quarantine of git.target.com suggests Target understood the potential for downstream exploitation and prioritized containment over immediate transparency."
The rapid removal of the Gitea samples following contact further suggests that Target’s incident response team moved swiftly to mitigate public visibility, potentially initiating legal action or engaging with the hosting provider to effect a takedown. However, the genie is out of the bottle; once data is posted on underground forums, complete eradication is nearly impossible.
Future Impact and Security Trends
This event is likely to accelerate several key trends already underway in corporate security departments:
1. Hardening of Secrets Management: The presence of internal references heightens the scrutiny on how secrets (API keys, internal URLs, connection strings) are stored within codebases. Expect heightened adoption of dedicated secrets management solutions integrated directly into the development workflow, ensuring that even if code is leaked, embedded credentials are automatically rotated or rendered useless.
2. Shift-Left Security Mandates: Retailers and enterprises globally will likely intensify efforts to "shift left"—integrating security scanning earlier and more rigorously in the Software Development Life Cycle (SDLC). This includes mandatory Static Application Security Testing (SAST) and Software Composition Analysis (SCA) scans before code can even be committed to central repositories, specifically looking for accidentally committed credentials or overly detailed internal system mapping.
3. Rethinking Developer Access: The potential exposure of employee names within commit histories will drive stricter controls over developer identity and access management (IAM). Multi-Factor Authentication (MFA) enforcement on all development tooling, including Git servers, will become non-negotiable, potentially coupled with session monitoring for high-risk activities like bulk code cloning. Furthermore, organizations may begin employing techniques like code pseudonymization or mandatory use of generic service accounts for commits to obscure individual developer footprints in public logs, should a leak occur.
4. Increased Scrutiny on Self-Hosted Infrastructure: While self-hosting services like Gitea offers control, it also introduces maintenance overhead and the risk of misconfiguration. If the compromise originated from a vulnerability in the Gitea instance itself, or an improper firewall rule allowing unauthorized access, it underscores the inherent risk of managing proprietary code on infrastructure that may not receive the same rigorous patching cadence as a managed SaaS solution.
For Target, the immediate focus will be forensic analysis to determine the initial point of entry—was it a successful phishing attack against a developer, a vulnerability in the Git server software, or an insider threat? The 860 GB figure suggests a successful, prolonged period of data exfiltration, indicating a sophisticated threat actor or a significant lapse in perimeter or identity security around the development environment. While the corporation has not issued a formal statement confirming the breach details, the synchronized shutdown of the sample repositories and the internal Git server provides a strong, albeit indirect, confirmation of a serious security event demanding immediate, comprehensive remediation. The long-term implications hinge on whether the leaked code contains exploitable business logic or critical system vulnerabilities that can be leveraged in future, more destructive attacks.