The digital identity and credential management landscape is experiencing a significant evolution, driven by escalating sophistication in cyber threats. In a notable development, 1Password, a leading subscription-based vault and password management solution deeply embedded within numerous high-profile enterprise environments, has deployed a new layer of defense specifically engineered to mitigate the risks associated with phishing attacks. This enhancement introduces contextual, on-screen warnings designed to halt users before they inadvertently surrender sensitive credentials to fraudulent websites.
This proactive feature recognizes a critical vulnerability inherent in even the most robust security tools: human error and social engineering efficacy. While password managers like 1Password traditionally offer a fundamental layer of protection by refusing to auto-fill login details on URLs that do not precisely match the stored, authorized address, this mechanism alone has proven insufficient against modern, highly deceptive phishing campaigns. Attackers are increasingly leveraging techniques like typosquatting—registering domain names that are subtle misspellings or visual approximations of legitimate sites—to trick users into believing they are on the correct platform.
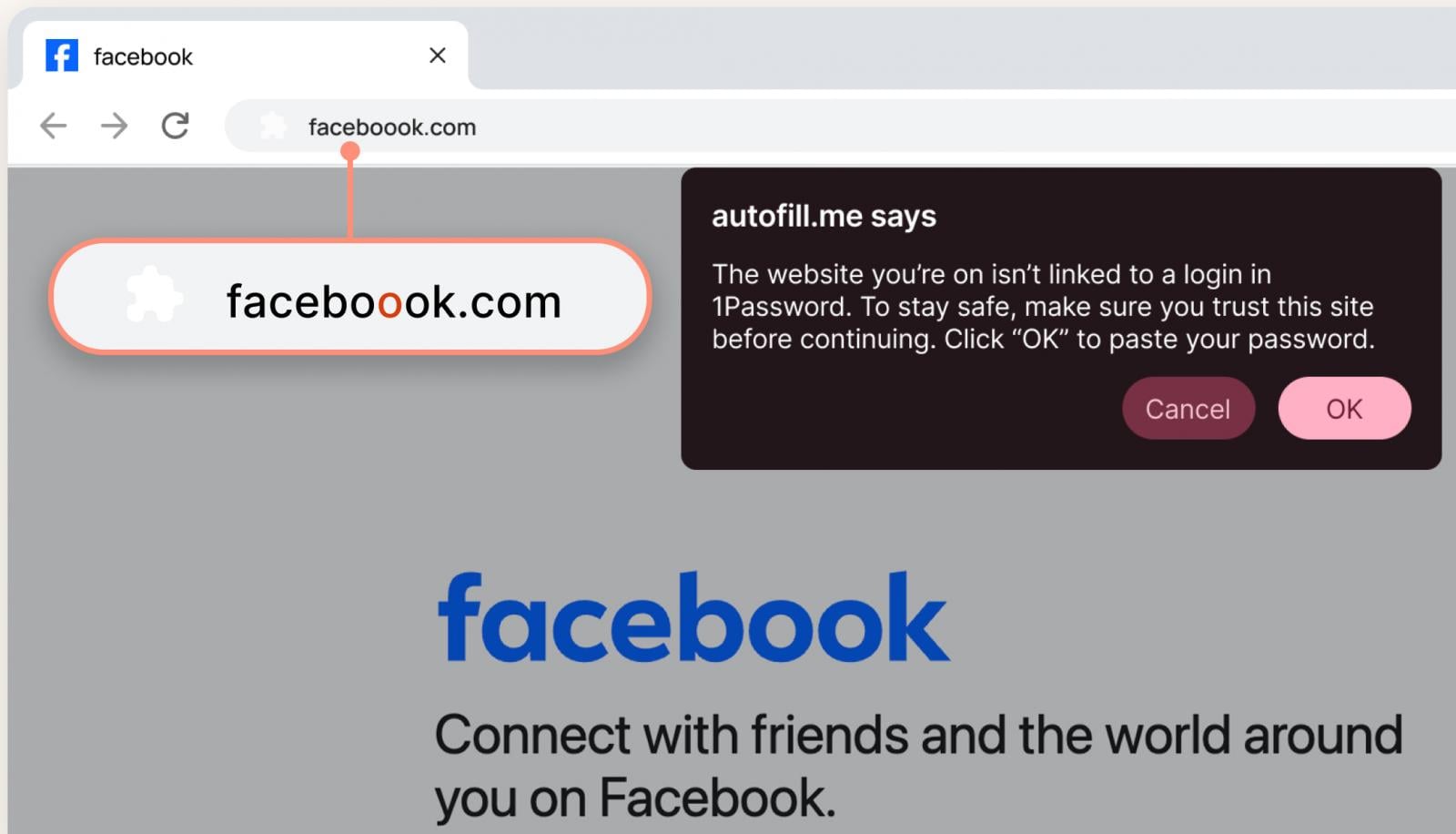
The core security philosophy underpinning password managers dictates that if the URL doesn’t match the stored entry, the automation stops. However, as 1Password itself has acknowledged, users encountering a convincing but slightly misspelled domain may override this default behavior. They might assume a momentary software glitch, a temporary vault lock, or simply overlook the minor discrepancy in the address bar, leading them to manually input their username and password into the malicious form. This manual override is the precise pivot point the new feature aims to disrupt.
The newly integrated defense mechanism manifests as an explicit, unavoidable pop-up alert. This interruption serves not as a hard block, but as a mandatory cognitive speed bump. By presenting a clear warning about potential phishing risk, the system forces the user to pause, re-examine the URL, and consciously confirm their intentions. The vendor cites examples, such as subtle alterations to major platform domains, where a single extra or missing character can easily escape casual notice, especially when the visual design of the fraudulent page is meticulously replicated. The intention behind this alert is clear: to prompt the user to "slow down and look more closely before proceeding," transforming a moment of potential automated trust into one of deliberate security verification.

Deployment Strategy and Accessibility
The rollout of this enhanced phishing detection is segmented across user tiers, reflecting the platform’s diverse customer base. For individual and family plan subscribers, the feature is activated by default, ensuring immediate security uplift for consumers. In the critical enterprise sector, where the ramifications of a single compromised account can lead to extensive lateral movement across internal networks, the deployment is managed by administrators. IT and security teams retain granular control, capable of enabling this crucial warning system for all employees via the Authentication Policies section within the 1Password administrative console, thereby standardizing user vigilance across the organization.
The introduction of this feature is framed within a broader context of an accelerating threat landscape, particularly noting the impact of generative Artificial Intelligence (AI). AI tools are lowering the barrier to entry for threat actors, allowing them to produce highly convincing, grammatically perfect, and voluminous phishing lures at an unprecedented scale. This democratization of sophisticated social engineering necessitates an equivalent leap in defensive countermeasures.
The Human Factor: Data Driving the Change
The decision to implement this level of user intervention is heavily informed by proprietary research concerning user behavior. A survey conducted by 1Password across 2,000 U.S. participants revealed alarming statistics that underscore the necessity of moving beyond passive security measures. Sixty-one percent of respondents admitted to having been successfully phished at some point, and a staggering 75% reported that they rarely, if ever, scrutinize the URLs embedded in links before clicking.
In the corporate sphere, the data is even more concerning regarding organizational risk. 1Password found that one-third of employees engage in password reuse between their professional accounts and personal services. When coupled with the fact that nearly half of these same employees have previously succumbed to phishing attacks, the potential for catastrophic organizational breach through credential stuffing or session hijacking becomes starkly apparent. Furthermore, the survey highlighted a significant psychological barrier: almost 50% of employees view phishing defense as solely the responsibility of the IT department, not an individual obligation. This mindset contributed to 72% admitting they had clicked suspicious links, and more than half stating they found it more convenient to simply delete suspicious messages rather than take the time to report them through established channels. These statistics confirm that security solutions must actively intervene in the user’s workflow to be effective.
Industry Implications: The Shift to Proactive Defense
This development marks a significant step in the evolution of password management tools, pushing them beyond simple credential storage and retrieval into the realm of active threat intelligence and user education. Historically, security solutions operated on a perimeter defense model or relied on post-compromise detection. Modern solutions, however, are embracing in-the-moment intervention.

For the identity and access management (IAM) industry, 1Password’s move sets a new benchmark for what consumers and enterprises should expect from their credential vaults. It acknowledges that the "last mile" of security is often the most vulnerable—the user’s final decision point. Other established password managers and security vendors will likely face pressure to integrate similar, context-aware alerting systems, particularly as deepfake technology and advanced AI models make visual spoofing more convincing.
The integration also dovetails neatly with 1Password’s recent move to support native passkey management within Windows. Passkeys, which rely on cryptographic key pairs rather than static passwords, are inherently resistant to phishing because the cryptographic verification process is tied to the originating domain. However, until passkeys achieve universal adoption, the vast majority of online interactions still rely on traditional username/password combinations, making the transitional defense layer provided by these pop-up warnings indispensable.
Expert Analysis: The Cognitive Load Trade-Off
From a security architecture perspective, the introduction of friction—even beneficial friction—requires careful balancing. Security professionals constantly grapple with the "usability vs. security" trade-off. Excessive security prompts lead to "alert fatigue," where users habitually dismiss warnings without reading them, effectively neutralizing the protection.
1Password’s approach appears calibrated to avoid this fatigue by limiting the intervention to only the most critical scenarios: potential credential submission to unverified sites. By leveraging their internal mapping of known, authorized URLs, the system generates a high-fidelity signal for when a user is about to enter sensitive data in an unapproved context. This specificity increases the likelihood that when the alert fires, the user will take it seriously, as it directly pertains to an action (logging in) that requires high cognitive attention.
Furthermore, this system acts as a subtle, persistent security awareness training tool. Each time a user is stopped by the alert, they are subtly reinforced on the necessity of checking domain names—a behavior that 1Password’s survey indicated is sorely lacking. Over time, this mechanism might help cultivate better digital hygiene, reducing the reliance on the tool to act as a perpetual safety net.
Future Impact and Trend Forecasting
Looking ahead, the trajectory of this technology points toward even deeper contextual awareness. Future iterations of these protective layers could integrate broader signals:
- Reputation Scoring: Beyond simple URL matching, the system could incorporate real-time reputation scoring for newly registered or previously flagged domains, even if they are not exact matches for known typosquats.
- Behavioral Anomaly Detection: If a user frequently accesses a service from a specific geographical location or device, an attempt to log in from a completely different context might trigger a higher-severity alert, even if the URL appears correct, suggesting a session hijack or credential stuffing attempt.
- Integration with Endpoint Detection and Response (EDR): Tighter integration between the password manager and EDR solutions could allow the warning system to cross-reference the destination site against known malware distribution lists or command-and-control servers, providing a multi-layered verification before login data is exposed.
The battle against phishing is increasingly a battle of context versus automation. As generative AI makes the phishing content itself nearly flawless, security solutions must become exponentially better at understanding the context of the user’s action. 1Password’s new pop-up warning represents a significant investment in this contextual defense strategy, recognizing that in the zero-trust paradigm, the user’s immediate environment and decision-making process are the final, and often weakest, security perimeter. This move solidifies the role of password managers as essential security gatekeepers, not just organizational databases, in the modern threat environment. The industry is now watching to see how quickly competitors adopt similar real-time cognitive interruption techniques to combat the rising tide of AI-supercharged scams.