The landscape of cyber espionage continues its rapid transformation, with a notable North Korean threat actor, tracked as Konni (also known by aliases Opal Sleet or TA406), demonstrating a sophisticated pivot toward leveraging generative artificial intelligence in the creation of their offensive tooling. This group, historically linked to established clusters such as APT37 and Kimsuky, has maintained a persistent operational tempo since approximately 2014, historically focusing espionage efforts on targets across South Korea, Russia, Ukraine, and various strategic entities within Europe. However, recent forensic analysis reveals a sharp strategic realignment: Konni is now specifically engineering malware campaigns to infiltrate the highly sensitive and lucrative ecosystem of blockchain development and engineering.
This evolution is significant not merely for the change in target sector but for the methodology employed. Security researchers examining the latest deployment observed strong indicators suggesting the use of Large Language Models (LLMs) during the malware development lifecycle, specifically yielding a highly obfuscated PowerShell backdoor. This shift suggests that state-sponsored actors are integrating commercially accessible, or custom-trained, generative AI tools to accelerate development, enhance evasion techniques, and potentially reduce the operational security risks associated with human coding errors.
The latest observed wave of activity, according to investigations by cybersecurity firm Check Point, shows a pronounced focus on the Asia-Pacific (APAC) region, with submission telemetry pointing towards compromised systems in Japan, Australia, and India. Given the nature of the targeted sector—blockchain engineers—the objective is clearly high-value data exfiltration and potential financial disruption, targeting the very core components that secure decentralized finance (DeFi) and Web3 projects.

The Infection Vector: Deceptive Simplicity and Layered Execution
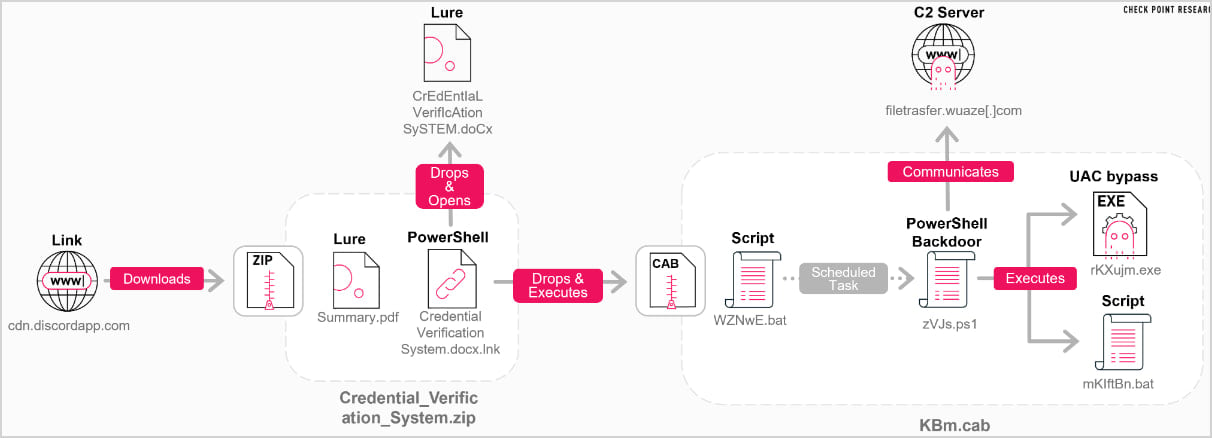
The initial access mechanism employed by Konni remains rooted in tried-and-true social engineering, albeit delivered through modern platforms. The campaign initiates when a targeted developer receives a link, typically distributed via the communication platform Discord. This link serves as the gateway to a compressed ZIP archive.
Within this archive, the initial payload is deceptively crafted to mimic legitimate documentation. It contains a PDF lure document, intended to engage the victim immediately, alongside a malicious LNK (shortcut) file. The reliance on a shortcut file is a classic technique designed to bypass certain security controls that scrutinize direct execution of executables, instead relying on the system’s built-in interpretation of shell commands.
Upon interaction with the LNK file, a chain reaction is triggered. The shortcut executes an embedded PowerShell loader. This loader’s primary function is to decompress and stage several components from a contained CAB archive. This archive is a carefully curated toolkit, containing not only the core PowerShell backdoor but also two distinct batch files and a Portable Executable (PE) file designed for User Account Control (UAC) bypass—a critical step for escalating privileges post-initial compromise.
Crucially, the initial execution simultaneously opens the decoy DOCX document. This dual action—displaying a seemingly benign document while covertly running malicious background scripts—is a common tactic to distract the user while the malware establishes persistence. The opening of the DOCX is synchronized with the execution of the first of the two batch files extracted from the CAB archive.

Targeting the Crown Jewels: Development Environments
The content of the lure document itself provides analysts with insight into the threat actor’s strategic intent. The documents are designed to look like technical specifications or project documentation relevant to software engineering, specifically targeting those involved in cryptographic or distributed ledger technology (DLT) development. By compromising these environments, Konni seeks access to what security professionals term the "crown jewels" of any crypto organization: source code repositories, private keys, API credentials necessary for interacting with mainnets, and, ultimately, the ability to manipulate or drain cryptocurrency holdings. The threat is less about traditional network infiltration and more about direct, high-impact asset theft.
The first batch file executes immediately, setting up a staging directory to house the persistent components of the attack. The second batch file performs the critical step of establishing persistence. It schedules a recurring task, set to execute hourly, deliberately masquerading its identity as a standard operating system component—specifically, a OneDrive startup task. This camouflage is designed to blend in with routine system activity, making detection via standard system monitoring tools significantly more challenging.
This scheduled task performs a crucial, albeit advanced, maneuver: it retrieves an XOR-encrypted PowerShell script stored on disk. This script is then decrypted directly into memory for execution. The practice of decrypting and executing code in memory (often referred to as fileless malware execution) severely limits the ability of endpoint detection and response (EDR) systems relying on disk-based scanning to intercept the payload. Once executed, the task performs self-deletion to further obfuscate the initial method of infection.
The Signature of AI: Analyzing the PowerShell Backdoor
The core of the infection is the PowerShell backdoor, which exhibits characteristics that researchers argue are hallmarks of Large Language Model (LLM) augmentation. The code is sophisticatedly obfuscated, utilizing techniques such as arithmetic-based string encoding and dynamic runtime string reconstruction. The final stage of execution relies heavily on the dangerous Invoke-Expression cmdlet, a common practice in malware to execute dynamically built strings as code.
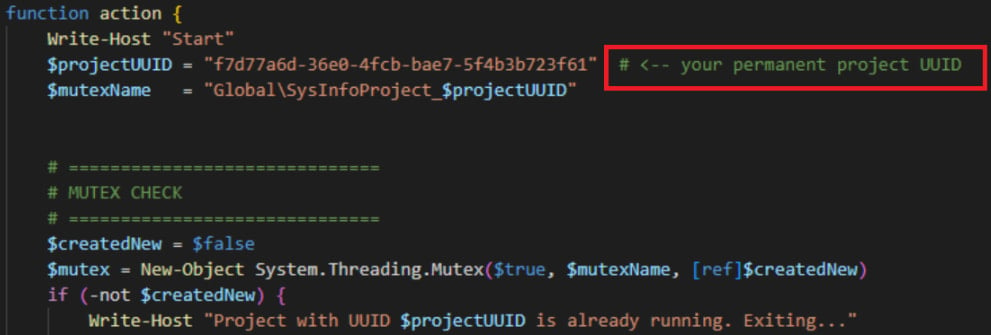
What differentiates this payload from typical hand-coded malware is its structural integrity and documentation. Traditional, hastily written malware often presents as a messy string of obfuscated commands. Conversely, this Konni script displayed clear, highly structured documentation blocks at its genesis. More tellingly, researchers identified a specific comment placeholder: "# <— your permanent project UUID".
As Check Point researchers noted, this phrasing is exceptionally characteristic of code generated by LLMs. When users prompt an AI to generate modular code, the AI often includes placeholders explicitly instructing the human operator on how to insert necessary configuration variables, treating the script like a template. Such explicit, instructional comments are rarely found in bespoke malware authored purely by human operators focused on stealth. This provides compelling, though not absolute, evidence that the actors are leveraging AI to rapidly prototype and refine their malicious codebases, increasing development speed and potentially improving obfuscation efficiency.
Evasion and Privilege Escalation
Before fully activating its command-and-control (C2) functions, the malware executes a series of rigorous checks designed to thwart automated analysis and sandbox environments. It probes the host system for specific hardware identifiers, software configurations, and signs of user activity. If the environment appears to be a controlled analysis system (e.g., a virtual machine or automated sandbox), the execution halts immediately.
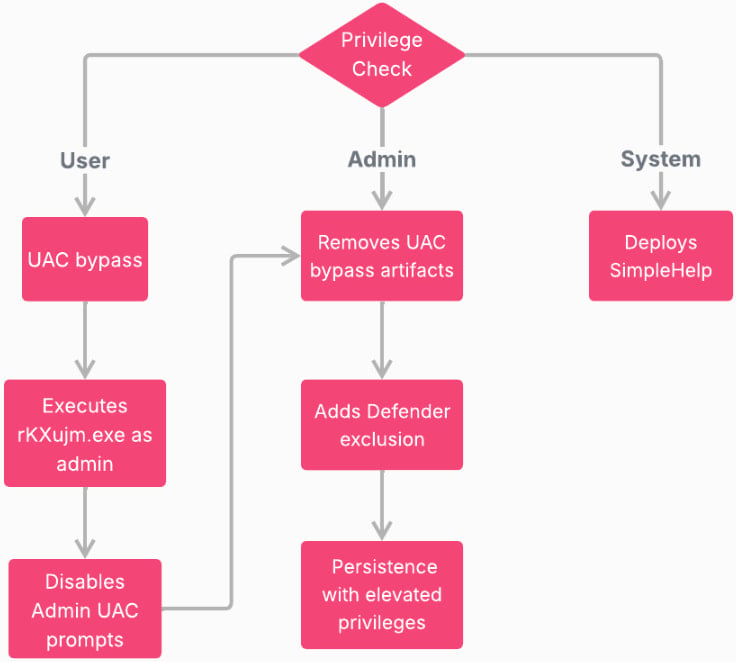
If the system is deemed a valid target, the malware generates a unique host identifier for subsequent C2 communications. The subsequent actions are then dictated by the privileges attained during the initial execution chain, which involved a dedicated UAC bypass component.
If the malware achieves elevated privileges (System or Administrator), it can execute more aggressive actions, potentially including deeper system persistence mechanisms or credential harvesting directly from memory. If only standard user privileges are attained, the malware focuses on establishing its basic C2 communication loop and waiting for further instructions, often focusing on reconnaissance or accessing files within the compromised user’s profile. This tiered approach ensures that even limited access yields potential intelligence.
Command and Control and Strategic Implications
Once the backdoor is operational, it establishes periodic communication with its designated C2 server. This communication involves sending rudimentary host metadata—fingerprinting the compromised machine—and then polling the server for further directives at randomized intervals. This randomization in polling frequency is an attempt to evade network traffic analysis based on fixed communication schedules.
If the C2 server responds with encapsulated PowerShell code, the backdoor dynamically converts this payload into a script block and executes it asynchronously using background jobs. This asynchronous execution ensures that the primary C2 communication thread remains responsive, allowing the actor to issue multiple commands rapidly without waiting for the preceding script to fully complete its execution, thereby maximizing operational efficiency during an active session.
The attribution to the Konni group is reinforced by correlating specific elements of this new campaign—including the structure of the initial launcher, filename conventions used in the lures, and overlaps in the overall execution chain architecture—with previously documented Konni activities.
Industry Implications: The AI Arms Race in Cyber Conflict
The integration of LLM-generated code into state-sponsored cyber operations signifies a critical inflection point. This development has profound implications across the cybersecurity industry:
1. Accelerated Development Cycle: Threat actors can now generate complex, functional malware modules in minutes rather than days or weeks. This dramatically lowers the barrier to entry for creating sophisticated tools and allows established groups like Konni to focus their human resources on high-level operational planning rather than low-level coding.
2. Enhanced Evasion and Polymorphism: LLMs excel at generating varied syntax for the same function. This capability allows attackers to create highly polymorphic malware that changes its structural signature with every new iteration, challenging signature-based detection systems and increasing the complexity of threat intelligence sharing.
3. The Blockchain Target Premium: By specifically targeting blockchain developers, Konni is capitalizing on the high-value nature of crypto assets and the often complex, bespoke security architectures prevalent in the Web3 space. Developers hold the keys to infrastructure, making them significantly more valuable targets than general corporate users.
4. Defensive Countermeasures: The defensive community must rapidly adapt. Reliance on traditional static analysis signatures will become increasingly ineffective against AI-generated, highly obfuscated code. The focus must shift toward behavioral analysis, monitoring for runtime anomalies, scrutinizing process lineage (especially PowerShell execution paths), and employing advanced sandbox technologies capable of fooling AI-aware malware. Furthermore, organizations developing DLT tools must assume their engineers are under constant, high-level surveillance.
The publication of Indicators of Compromise (IoCs) by researchers is a vital first step, but the industry must recognize this is not an isolated incident but a trend signaling the formal integration of generative AI into the arsenal of sophisticated espionage operations. Securing the development lifecycle against these intelligent, rapidly evolving threats is now paramount for maintaining the integrity of the digital economy.

