The digital ecosystem supporting Managed Service Providers (MSPs) was recently rattled by a significant internal data exposure incident involving Pax8, a prominent global cloud commerce marketplace. The company, which has rapidly scaled to become a major distributor in the channel, confirmed that an operational error resulted in the dissemination of sensitive business intelligence pertaining to a substantial number of its partners. This incident underscores the inherent fragility of third-party data management, particularly within complex, multi-tenant cloud environments where information flows across numerous organizational boundaries.
Pax8, a company boasting over 1,700 employees and servicing more than 47,000 partners across 18 countries, has enjoyed explosive growth, recently crossing the $2 billion annual revenue threshold, with Europe being a key engine for this expansion. It is precisely this rapid scaling and reliance on streamlined distribution channels that makes such an error so impactful.
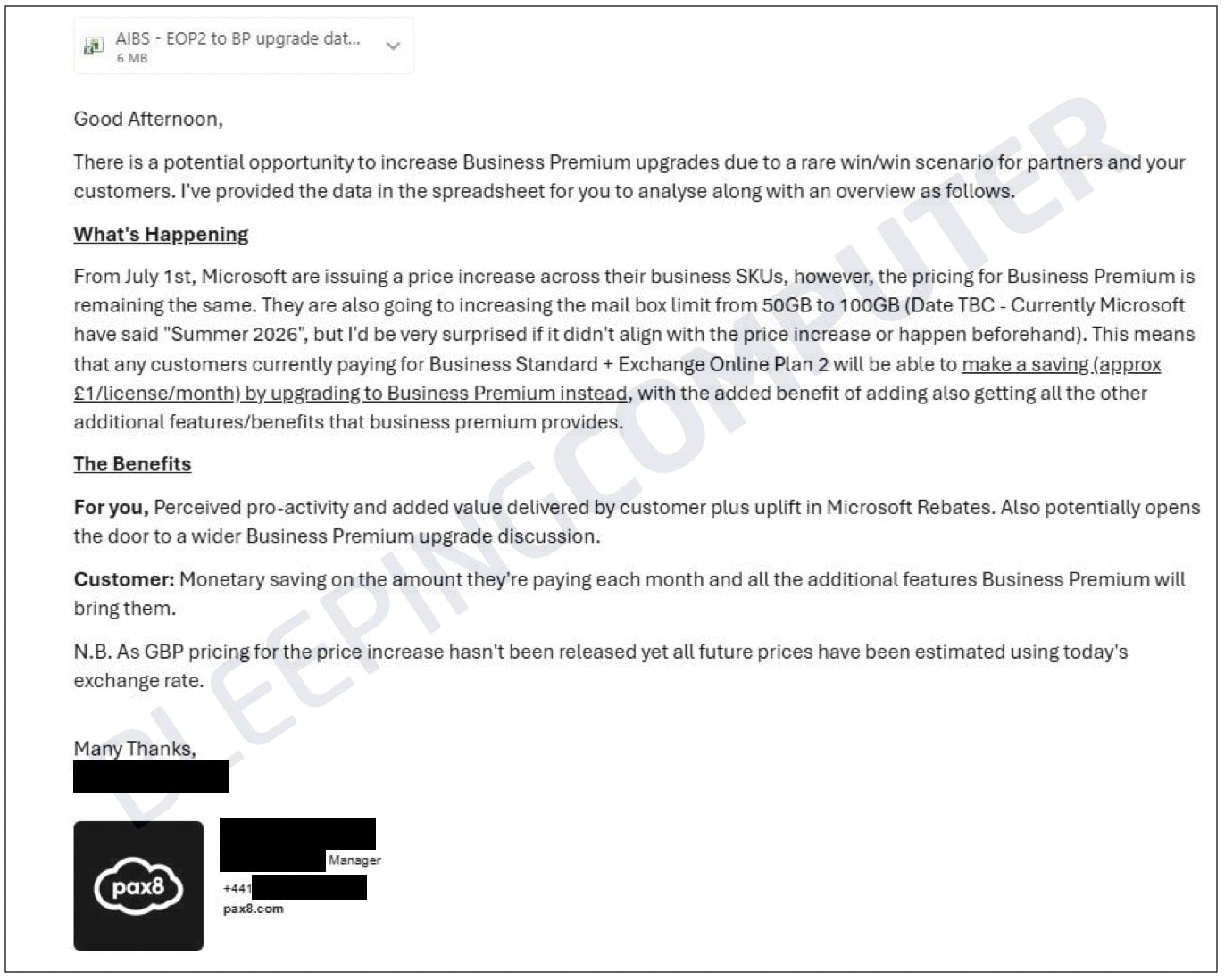
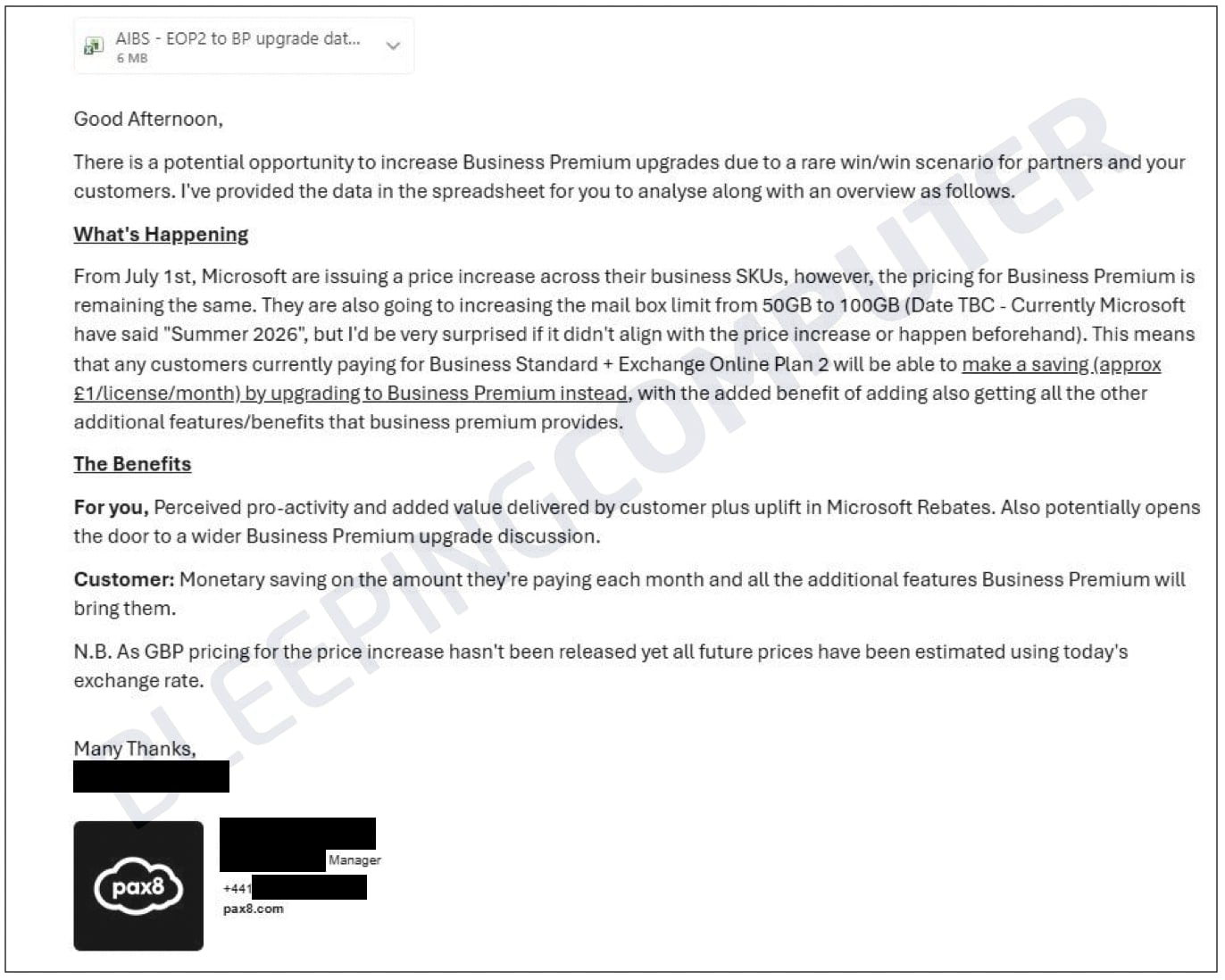
The breach originated from an email sent on January 13th, titled "Potential Business Premium Upgrade Tactic to Save Money," dispatched by a strategic account manager based in the EMEA region. This communication, intended for a highly specific audience, contained a comma-separated values (CSV) attachment that held proprietary operational details. While the email reached fewer than 40 recipients in the UK, the underlying data within the spreadsheet affected an estimated 1,800 partners, predominantly located in the UK, with a single outlier identified in Canada.
The nature of the exposed data elevates this from a minor administrative slip to a serious competitive intelligence event. According to confirmations from recipient MSPs, the attached CSV was a rich repository of actionable business metrics. It cataloged customer organization names, specific Microsoft Stock Keeping Units (SKUs) being utilized, the corresponding license counts, and critically, the renewal timelines under Microsoft’s New Commerce Experience (NCE) framework. Artifacts reviewed from multiple sources indicated the dataset was extensive, comprising over 56,000 distinct entries, detailing the intricate licensing footprint of numerous organizations.

This information is the lifeblood of MSP operations. It maps out client environments, highlights opportunities for upselling or cross-selling, and pinpoints contract vulnerabilities ripe for competitive exploitation. For an MSP, the visibility into a competitor’s or partner’s pricing structures and upcoming renewal windows is invaluable, providing an asymmetric advantage in client retention and acquisition strategies.
Pax8’s Remediation Efforts and Disclosure Limitations
Immediately following the transmission error, the sender initiated recovery protocols, attempting to recall the message. This was followed by a secondary communication explicitly acknowledging the mistake and instructing recipients to destroy the original email and its attachment immediately.
In their follow-up disclosure, Pax8 sought to mitigate the perceived risk by asserting that the file "did not contain personally identifiable information." Instead, the company characterized the contents as "limited internal business information reflective of your Pax8 pricing and some Microsoft program management." While this sidesteps direct PII concerns, the classification of "limited business information" is subjective in this context. Data revealing the exact configuration, scale, and contractual cadence of a client’s Microsoft estate, known only to the managing MSP and the distributor, constitutes highly sensitive commercial intelligence. Pax8 assured recipients that the incident resulted in "no impact to Marketplace availability or security controls."
The immediate actions taken by Pax8—contacting recipients, demanding deletion confirmation, conducting one-on-one follow-ups, and launching an internal review—demonstrate an adherence to standard incident response procedures for accidental disclosure. However, the genie, once out of the bottle, is difficult to contain in the digital realm.
The Competitive Intelligence Fallout: Beyond Accidental Sharing
The implications of this exposure extend far beyond the immediate circle of the 40 recipients. The data, once seen, can be copied, stored, and disseminated outside the control of Pax8’s recall request. The reports emerging from industry sources—that threat actors are actively soliciting affected MSPs to purchase copies of the exposed dataset—confirm the high market value of this intelligence.

For Competitors: Rival MSPs gain an unprecedented blueprint of their competitors’ client bases. They can analyze which organizations rely on Pax8, the size of their cloud deployments (e.g., E3 vs. E5 licenses, security add-ons), and when their contracts are up for renewal. This allows for hyper-targeted marketing campaigns, often leveraging precise knowledge of current vendor relationships and potential cost savings derived from switching providers—a direct form of client poaching enabled by insider data.
For Malicious Actors: The dataset serves as a premium targeting list for cybercriminals. Knowing the exact Microsoft SKUs in use allows for tailored spear-phishing attacks that mimic legitimate Microsoft communications regarding licensing changes or compliance updates. Furthermore, knowing the MSP managing the tenant provides a vector for Business Email Compromise (BEC) attacks, where attackers impersonate the MSP to trick client employees into performing unauthorized actions. Timing attacks around NCE renewal dates—a known period of administrative flux and vulnerability—increases the potential for extortion or successful social engineering.
Industry Implications: Trust in the Distribution Layer
This incident places a harsh spotlight on the security posture and internal controls of major cloud distributors like Pax8. These platforms act as central nervous systems for thousands of smaller service providers, aggregating operational data that is fundamentally non-public.
The core implication here is a crisis of trust in the "blind trust" model often employed in the channel. MSPs entrust distributors with detailed views into their business relationships to facilitate smooth provisioning and billing. When this aggregation layer suffers a leakage, it suggests systemic vulnerabilities in data segregation, access control, or, as in this case, basic procedural discipline (sending an attachment to the wrong recipient group).
For the wider channel, this event serves as a potent reminder that security diligence cannot stop at the customer endpoint; it must rigorously encompass all third-party vendors, particularly those handling aggregated business logic and commercial data. The fact that the data included NCE renewal dates is particularly sensitive, as the transition to NCE has been a complex compliance and cost management challenge for many organizations globally.
Expert Analysis: Data Segregation and Contextual Integrity
From a security architecture perspective, this incident highlights the failure of proper data segregation and contextual awareness within the distribution workflow. A standard procedure for an account manager should involve stringent checks ensuring that internal documents containing aggregated partner/customer data are restricted to internal teams or, if shared externally, only to the specific intended recipient—not broadcast to a wide partner list, even if that list is small.
The fields within the CSV—customer names, SKU counts, and renewal dates—represent Contextual Business Data (CBD). CBD, while not directly PII like a physical address or Social Security number, often carries higher commercial risk than PII because it dictates market strategy and financial forecasting for the affected MSPs. Regulations like GDPR, while primarily focused on PII, increasingly treat commercially sensitive information shared under confidentiality agreements with similar weight regarding required due diligence and breach notification standards.
The rapid succession of the accidental email, the recall attempt, and the follow-up notification suggests Pax8 recognized the severity swiftly. However, the fact that threat actors are already monetizing the data indicates that deletion requests are insufficient protection against a data set that has already escaped the immediate control of the sender. The challenge now lies in demonstrating to the 1,800 affected partners that the damage is contained, despite the intelligence being demonstrably available on the black market.
Future Trends: Centralization vs. Decentralization Risks
This event fuels a growing debate in the MSP sector regarding the benefits of centralized cloud marketplaces versus the risks associated with reliance on single points of failure. Marketplaces like Pax8 offer unparalleled efficiency, ease of management, and consolidated billing, which drive down operational overhead for thousands of smaller entities. However, this efficiency comes at the cost of data centralization.
As the industry continues to consolidate around major distributors, the potential impact of a single data incident multiplies. We are likely to see increased scrutiny from large enterprise partners and regulatory bodies on how distributors manage this aggregated, high-value data. Future vendor contracts may mandate more rigorous, independently verifiable data segregation protocols, perhaps requiring distributors to utilize zero-trust architectures for their internal data portals, ensuring that even an authorized employee can only access data strictly necessary for their immediate, defined task—a concept known as least privilege applied granularly across commercial data views.

Furthermore, this leak may accelerate the adoption of data loss prevention (DLP) tools specifically tailored for the channel ecosystem. These tools would need to be sophisticated enough to understand the context of licensing spreadsheets and subscription renewal data, blocking transmission based on content rather than just predefined sensitive keywords.
The incident serves as a stark illustration that in the high-stakes world of cloud distribution, human error remains the most potent vulnerability, capable of undermining the competitive standing of hundreds of organizations in a single, mistaken click. For Pax8, the imperative now is not just technical remediation, but a comprehensive rebuilding of partner confidence by demonstrating an unassailable commitment to commercial data protection.