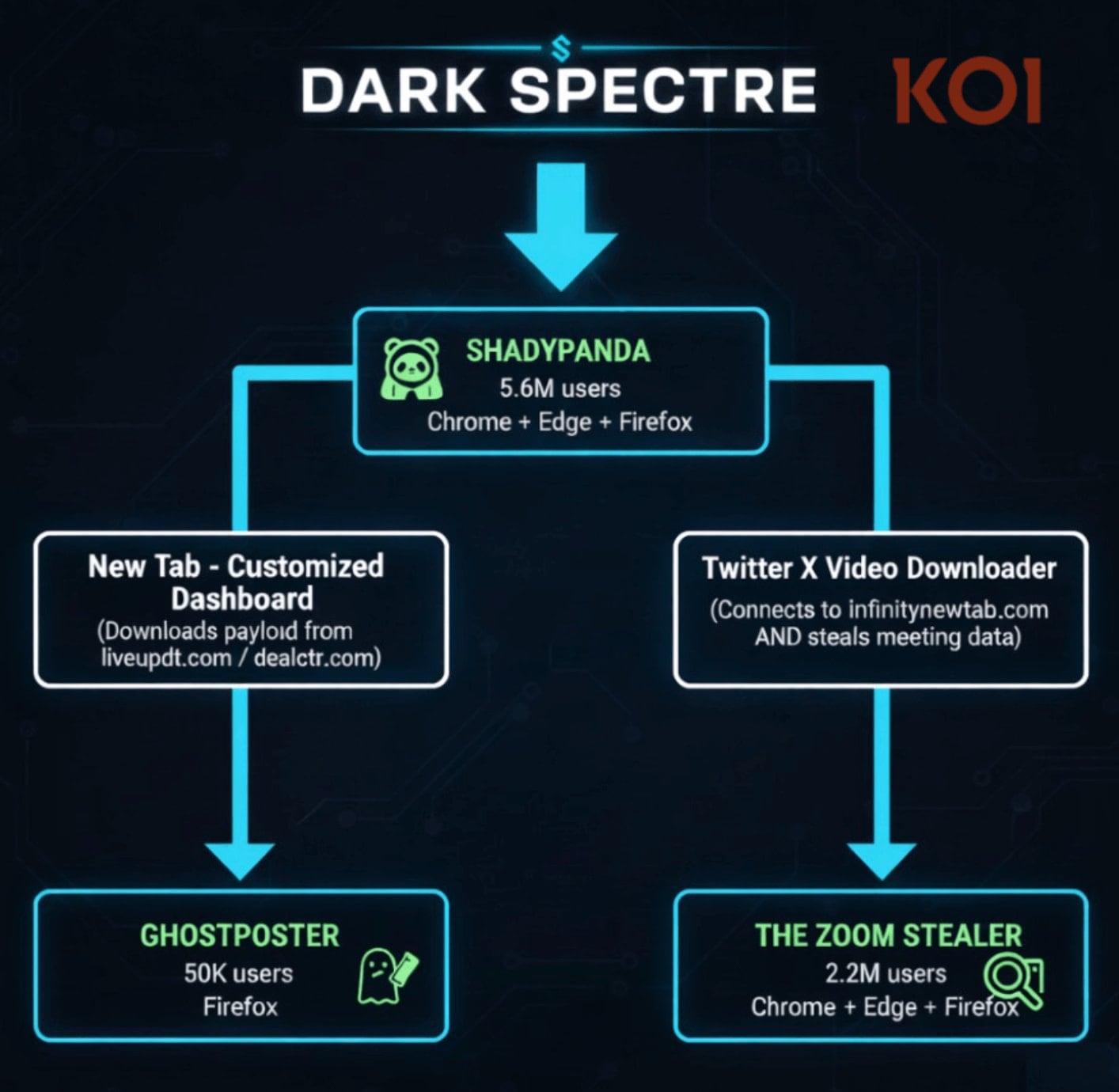
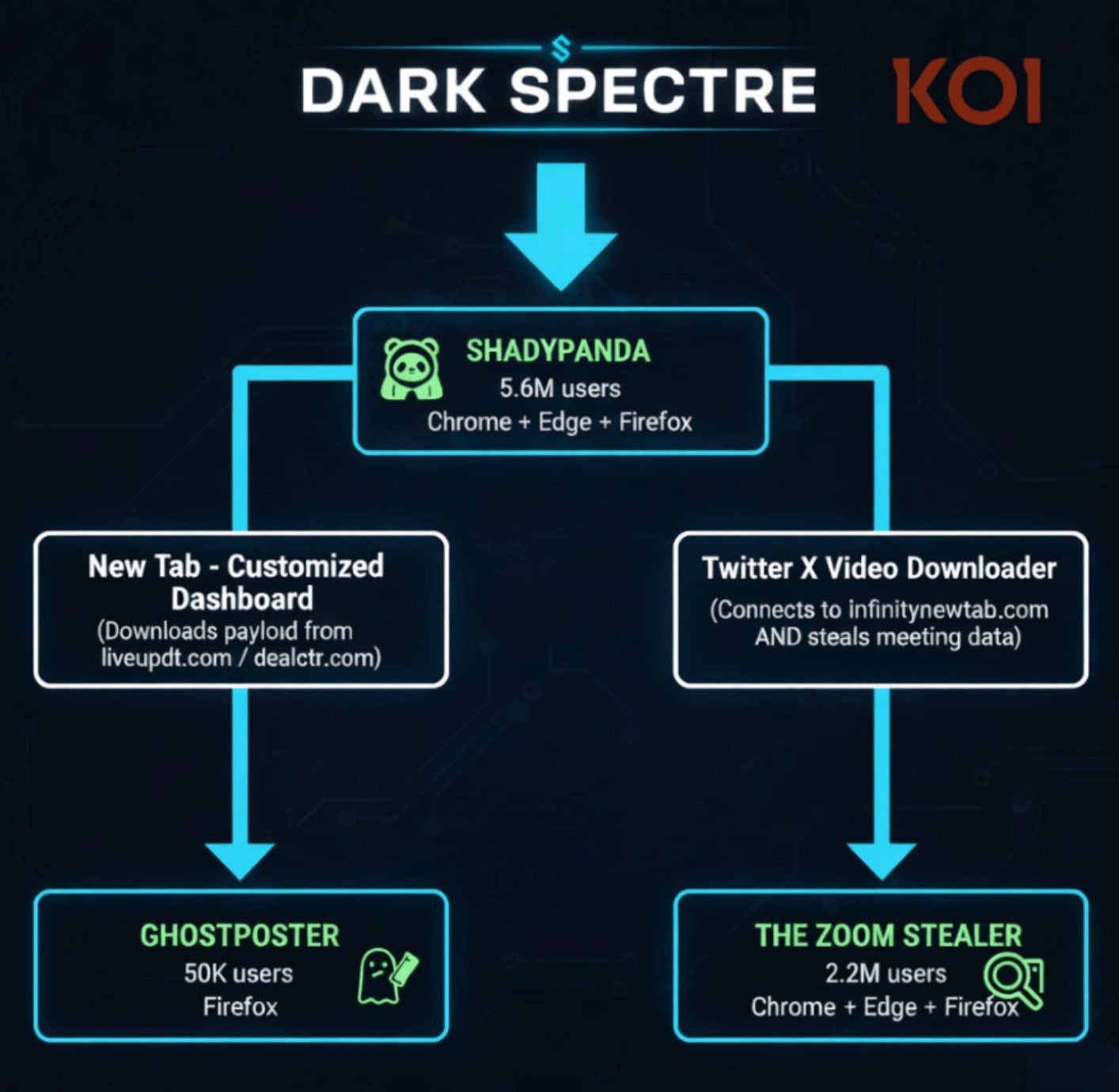
A pervasive and deeply entrenched digital espionage campaign, dubbed "Zoom Stealer" by cybersecurity investigators, has successfully compromised an estimated 2.2 million users across the Chrome, Firefox, and Microsoft Edge ecosystems. This sophisticated operation leverages at least 18 seemingly benign browser extensions to systematically harvest sensitive metadata related to online conferencing, including meeting URLs, unique identifiers, discussion topics, detailed descriptions, and, critically, any embedded access credentials.
This specific set of malicious extensions forms part of a much broader, multi-year threat matrix orchestrated by a single, highly persistent threat actor identified by researchers as DarkSpectre. Analysis indicates that DarkSpectre is responsible for three distinct browser extension campaigns that, over a span of seven years, have collectively impacted over 7.8 million end-users. The consistent infrastructure and operational characteristics strongly suggest that DarkSpectre is linked to previously documented threat activities originating from China, specifically drawing parallels with the "GhostPoster" campaign, which targeted Firefox users, and the "ShadyPanda" operation, known for deploying spyware payloads across Chrome and Edge installations.
The depth of this operation is further illuminated by the ongoing activities associated with the ShadyPanda lineage. Security firm Koi Security reports that ShadyPanda maintains an active presence through nine currently deployed extensions, augmented by an additional 85 "sleeper" extensions. These sleepers are designed to remain dormant, cultivating a significant user base before a coordinated, malicious update transforms their functionality overnight. This "dormancy" tactic is a hallmark of advanced supply chain compromise, maximizing the potential blast radius before detection.

Attribution Solidified: Infrastructure Reveals Origin
While prior indications pointed toward a China-based origin for these threat actors, the latest investigation provides significantly clearer attribution markers. The operational footprint of DarkSpectre is now firmly anchored by several key indicators. These include the reliance on Alibaba Cloud for hosting critical infrastructure, the presence of specific Internet Content Provider (ICP) registrations tied to Chinese entities, and the pervasive inclusion of Chinese-language strings and comments embedded within the malicious code artifacts. Furthermore, the observed activity patterns align precisely with the Chinese standard time zone, and the monetization strategies appear specifically tuned toward the dynamics of Chinese e-commerce platforms, painting a comprehensive picture of the adversary’s base of operations and strategic focus.
The Nature of the Harvest: Corporate Espionage Fuel
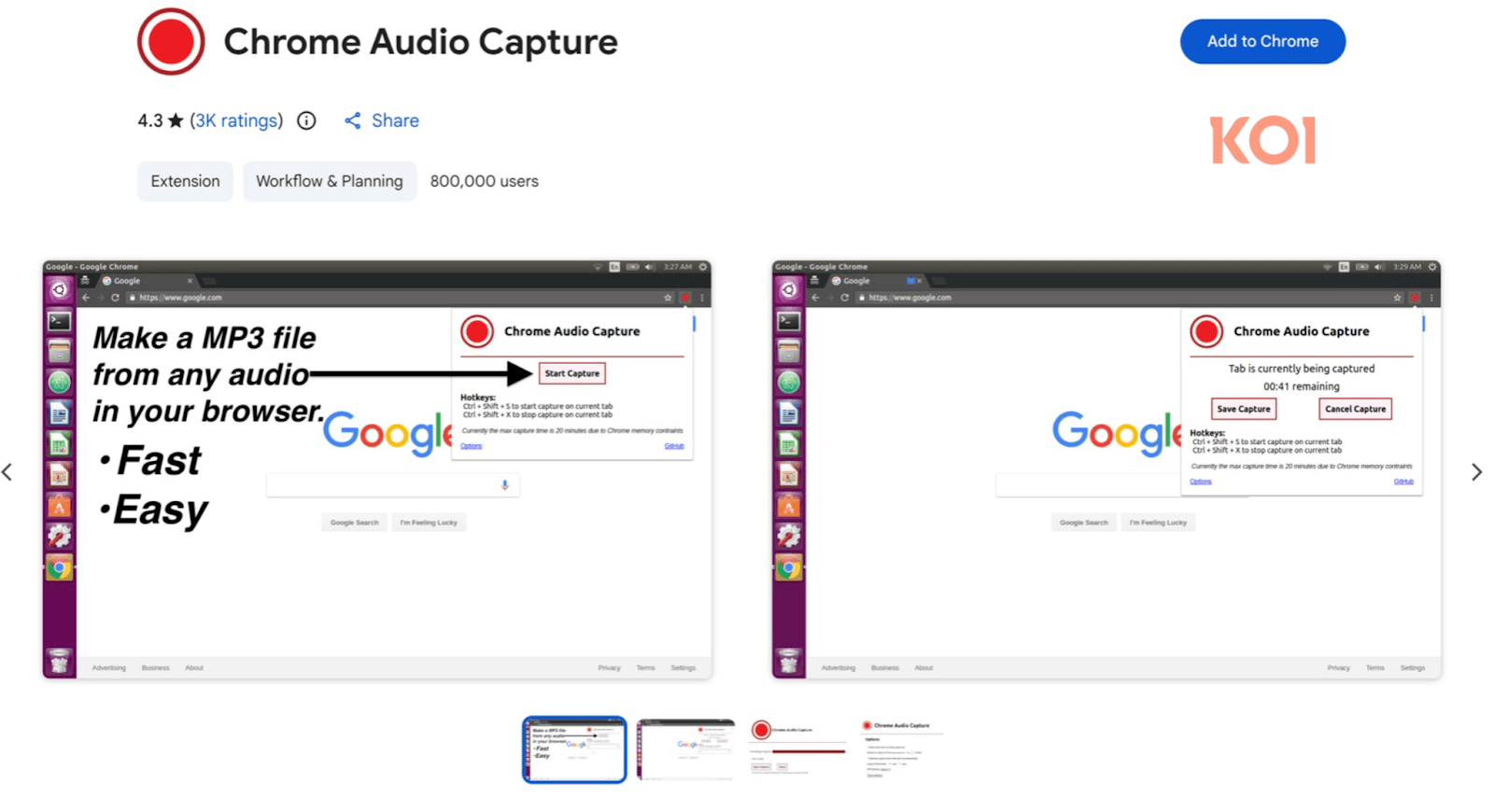
The 18 extensions involved in the Zoom Stealer phase exhibit a deceptive duality. While some extensions market themselves under utility-focused names—such as the widely installed "Chrome Audio Capture" (with approximately 800,000 installations) and "Twitter X Video Downloader"—they are functionally compromised. Crucially, Koi Security confirmed that these extensions perform their advertised functions perfectly, which aids in evading user suspicion. This functionality masks the covert data exfiltration process.
These extensions are engineered with broad access permissions, specifically targeting interactions with 28 distinct video-conferencing platforms, encompassing industry giants like Zoom, Microsoft Teams, Google Meet, and Cisco WebEx.
The specific data harvested during user sessions includes:

- Meeting URLs and Identifiers: Direct access points to ongoing or scheduled sessions.
- Session Titles and Descriptions: Contextual information about the meeting’s purpose and seniority of participants.
- Participant Lists: Names, roles, and organizational affiliations of attendees.
- Embedded Passwords/Tokens: Crucial authentication details sometimes transmitted unencrypted or visible within the Document Object Model (DOM) during session initiation.
- Registration Page Data: Information harvested when users interact with webinar sign-up forms, which often captures initial contact details for sales or marketing leads.
This highly sensitive stream of information is not collected in periodic batches; rather, it is exfiltrated in real-time via persistent WebSocket connections directly back to the threat actors’ command-and-control infrastructure. The triggering mechanism for this data theft is precise: it initiates when a victim navigates to a webinar registration page, joins an active meeting, or interacts with the interface of any of the targeted conferencing platforms.
Industry Implications: Beyond Simple Theft
The strategic value of the data collected by DarkSpectre cannot be overstated. This is not merely about stealing financial details; it represents a deep dive into corporate intellectual property and strategic planning. Koi Security’s analysis underscores that this harvested intelligence is perfectly suited for high-level corporate espionage and advanced sales intelligence gathering.
The potential downstream applications are manifold and severe:
- Social Engineering at Scale: By possessing participant lists, meeting contexts, and internal jargon, threat actors can craft highly convincing spear-phishing and social engineering attacks against specific individuals or entire departments. Knowing who attended a strategy session allows an attacker to impersonate a colleague or executive with unparalleled context.
- Competitive Sabotage: The acquisition of meeting links and schedules allows adversaries to either inject themselves into confidential sessions—acting as eavesdroppers—or, more maliciously, leak proprietary information or meeting details to direct competitors.
- Credential Harvesting for Lateral Movement: If embedded passwords or session tokens are captured, these can be immediately leveraged to gain unauthorized access to internal corporate networks, moving laterally from a compromised browser session into more secure enterprise environments.
As the Koi Security report succinctly notes, "By systematically collecting meeting links, participant lists, and corporate intelligence across 2.2 million users, DarkSpectre has created a database that could power large-scale impersonation operations—providing attackers with credentials to join confidential calls, participant lists to know who to impersonate, and context to make those impersonations convincing." This collection forms a foundational layer for advanced persistent threat (APT) activities disguised as legitimate user behavior.
Expert Analysis: The Browser as the Weakest Link
The sustained success of DarkSpectre highlights a critical vulnerability in modern enterprise security posture: the over-reliance on the browser as a trusted execution environment. In the early days of browser extensions, they were viewed primarily as productivity enhancements. Today, they function as mini-applications with extensive privileges over the browser’s DOM and network traffic.
Security architects often focus heavily on perimeter defenses and endpoint detection and response (EDR) solutions, yet frequently underestimate the risk posed by third-party browser add-ons. An extension, once granted permissions, effectively runs with the same privileges as the user within that browser context. This means any data visible to the user—including dynamically loaded credentials, ephemeral session tokens, or sensitive text within an active meeting interface—is visible to the extension’s underlying code.
The tactic of delaying malicious payload activation via "sleeper" extensions is a sophisticated evasion technique. Traditional signature-based anti-malware solutions, or even standard app store vetting processes, often fail to flag an extension during its initial, innocuous phase. The threat only materializes after the extension has achieved critical mass, making the subsequent removal effort significantly more challenging, as it requires addressing millions of already compromised installations.
Industry Response and Future Trends in Extension Security
The immediate challenge lies in mitigating the damage from the existing DarkSpectre footprint. While security vendors like Koi Security have responsibly reported the malicious extensions, the observed reality is that many remain accessible on major storefronts like the Chrome Web Store at the time of analysis. This indicates a critical bottleneck in the enforcement and rapid removal procedures utilized by platform owners.
For enterprises, this incident serves as a stark reminder to implement stringent browser management policies. Security teams must move beyond simple blacklisting and adopt deep inspection or sandboxing solutions for browser extensions. Key mitigation strategies include:
- Strict Whitelisting: Limiting the installation of extensions to a pre-approved, minimal set required for specific job functions.
- Regular Audits of Permissions: Periodically reviewing the permissions granted to all installed extensions, particularly those that have recently received updates, regardless of their perceived vendor reputation.
- User Education on Context: Training employees to recognize that even popular utility extensions can be compromised and should not be used when handling highly sensitive corporate data.
Looking ahead, the reliance on browser extensions for critical business functions—from CRM integration to specialized development tools—will only increase. This trend necessitates a fundamental shift in how platform providers, like Google and Mozilla, approach extension security. We can anticipate a move toward more rigorous, continuous runtime analysis rather than solely relying on static code review during submission. Furthermore, emerging technologies may force extensions into more confined, permission-limited sandboxes, preventing them from accessing sensitive data across disparate domains without explicit, granular user consent for every interaction. The DarkSpectre campaigns underscore that the supply chain of browser tooling is now a prime vector for state-sponsored or highly organized corporate espionage, demanding a security paradigm shift commensurate with the risk.