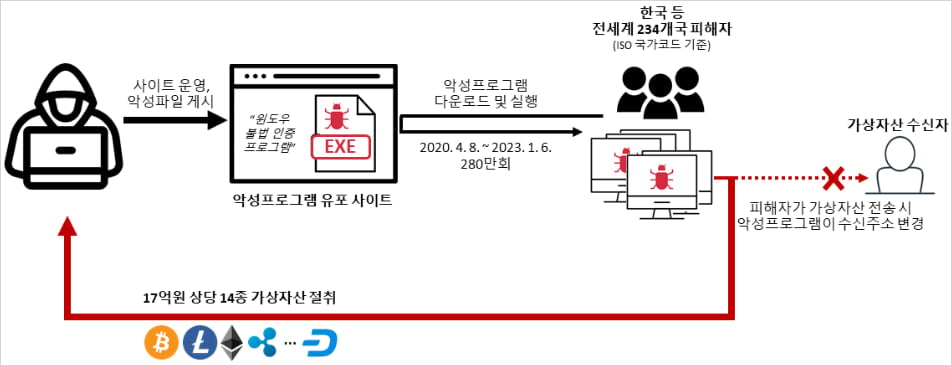
The intricate web of cybercrime spanning continents has tightened around a 29-year-old Lithuanian national, who now faces charges for orchestrating a sophisticated malware distribution scheme that leveraged the illicit appeal of software cracking tools. This individual is alleged to be the central figure responsible for infecting an estimated 2.8 million computer systems globally with highly damaging "clipper" malware, carefully camouflaged within downloads of KMSAuto—a notorious utility used for the unauthorized activation of Microsoft Windows and Office products. The culmination of a multi-year international investigation, facilitated through coordination by Interpol, resulted in the suspect’s extradition from Georgia to South Korea, marking a significant victory for transnational cybercrime enforcement.
The core mechanism of this malicious operation centered on exploiting a fundamental temptation: the desire to obtain expensive software licenses without payment. KMSAuto, and similar Key Management Service (KMS) emulators, have long been vectors for malware infection because users seeking pirated software are inherently less likely to employ robust security measures or question the provenance of the downloaded files. According to official reports released by the Korean National Police Agency (KNPA), the perpetrator injected a malicious executable into the KMSAuto package. Upon execution, this payload executed a highly targeted form of theft: continuous scanning of the system’s clipboard memory.
Clipper malware, by definition, monitors data copied to the clipboard—a temporary storage area often used for text, images, or, critically in this context, cryptocurrency wallet addresses. When the malware detected a string formatted like a valid crypto address, it would instantaneously swap the legitimate destination address with one secretly controlled by the attacker. This process, often executed within milliseconds, ensured that even meticulous users making a transfer would inadvertently redirect substantial sums of digital currency to the threat actor’s wallets.
The scale of the operation, spanning from April 2020 until January 2023, highlights the sustained nature of the campaign. Authorities estimate that the illicit software activator was distributed to nearly three million hosts worldwide. The financial impact was substantial, with the KNPA calculating that the attacker successfully diverted virtual assets amounting to approximately 1.7 billion South Korean Won (equivalent to roughly $1.2 million USD) across 8,400 separate fraudulent transactions. These illicit gains were funneled through 3,100 unique virtual asset addresses identified by investigators.
The Investigative Trail: From Cryptojacking Reports to International Apprehension
The genesis of this successful apprehension traces back to August 2020, when South Korean authorities received initial reports indicative of widespread cryptojacking activity. Victims reported discrepancies in cryptocurrency transfers, pointing toward the presence of clipper malware silently hijacking transactions. Unlike ransomware, which locks files, clipper malware is a silent parasite, making attribution and tracing significantly more complex. The investigation required deep forensic analysis to connect the seemingly disparate theft incidents back to a singular source distribution channel.

Investigators meticulously traced the infection path, confirming that the KMSAuto distribution platform served as the primary conduit. The attack was not limited in scope; forensic analysis revealed that the clipper specifically targeted transactions intended for at least six major cryptocurrency exchanges, indicating a broad awareness of the most active digital asset platforms. The technical sophistication lay not just in the clipboard hijacking, but in maintaining a low profile across millions of infected systems for nearly three years.
The breakthrough in identifying the perpetrator involved sophisticated tracing of the stolen funds. By mapping the flow of cryptocurrency from victim wallets to the attacker-controlled wallets, investigators were able to build a financial profile. This financial forensics trail eventually led to physical world intelligence regarding the suspect’s location and movements. A critical phase of the operation occurred in December 2024, when authorities executed a raid in Lithuania, the suspect’s last known base of operations. During this raid, law enforcement seized 22 pieces of critical evidence, including laptop computers and mobile communication devices, which provided the final digital links needed for prosecution.
The final act of the international pursuit concluded in April 2025. The suspect was apprehended while in transit between Lithuania and Georgia, indicating an attempt to flee jurisdiction following increased investigative pressure. This successful extradition to South Korea underscores the strengthening collaboration between international policing bodies in tackling cyber threats that transcend national borders.
Industry Implications: The Enduring Danger of "Freeware" Lures
This high-profile case serves as a stark reminder to both individual users and enterprise security teams about the pervasive danger associated with utilizing unauthorized software, particularly tools designed to circumvent digital rights management (DRM). The KMSAuto incident is a textbook example of how the allure of ‘free’ premium software is weaponized by cybercriminals.
From an industry perspective, the reliance on pirated activators exposes organizations to supply chain risks far beyond simple copyright infringement. When corporate endpoints or developer workstations utilize cracked software, the security perimeter is inherently breached. The threat actor in this case did not need sophisticated zero-day exploits or complex phishing campaigns against corporate infrastructure; they relied on user complacency regarding software legality.
This methodology is demonstrably repeatable. As law enforcement agencies dismantle one distribution network, others quickly emerge, often mimicking popular tools. Recently, security analysts have observed similar tactics employed using impersonations of Microsoft Activation Scripts (MAS), where malicious PowerShell scripts were delivered through fake activation domains, ultimately installing complex loaders like Cosmali. This pattern suggests that activators, due to their perceived utility in certain technical communities, will remain a preferred Trojan horse for malware deployment, including ransomware, cryptominers, and information stealers.

Expert Analysis: The Technical Anatomy of Clipper Malware and Digital Asset Theft
The technical architecture underpinning this successful long-term campaign warrants deeper examination. Clipper malware, while conceptually simple—monitor and replace—requires specific operational parameters to achieve large-scale success.
Firstly, the malware needed robust persistence and evasion capabilities. To remain undetected across 2.8 million installs for nearly three years, the executable likely employed techniques to bypass standard endpoint detection and response (EDR) systems, possibly through fileless execution or heavy obfuscation of the clipboard monitoring routine. The code likely included whitelists for common legitimate clipboard operations (like copying text for a web search) to avoid triggering alerts, focusing only on specific string patterns indicative of cryptocurrency wallet formats (e.g., Bitcoin, Ethereum, or newer token addresses).
Secondly, the targeting of multiple exchanges implies a sophisticated understanding of the digital asset ecosystem. Each cryptocurrency possesses a unique address structure. The malware needed dynamically updated detection heuristics or regular updates to recognize and replace addresses across various chains simultaneously. Targeting six exchanges suggests the attacker was maximizing the probability of intercepting high-value transfers across popular platforms.
Furthermore, the financial laundering process must have been complex. Moving $1.2 million through 8,400 transactions necessitates a high degree of operational security on the attacker’s side. The funds were likely cycled through mixers, privacy coins, or decentralized exchanges (DEXs) rapidly to obscure the trail before they could be cashed out via less regulated avenues. The ability of the KNPA to trace these movements sufficiently to pinpoint the suspect’s physical location underscores significant advancements in blockchain forensic analysis capabilities employed by state actors.
Future Impact and Defensive Strategies
The successful takedown of this operation offers valuable lessons for proactive cybersecurity posture development, moving beyond reactive threat response. The fundamental takeaway remains: the greatest vulnerability often lies at the intersection of user behavior and accessible temptation.
For enterprise security architects, this reinforces the critical need for stringent application control policies. Systems should be configured to execute only whitelisted applications, and unauthorized executables—especially those associated with DRM circumvention—should be blocked at the network or endpoint level. Furthermore, security teams must prioritize continuous monitoring of internal network traffic for anomalies related to cryptocurrency wallets if they operate in sectors dealing with digital assets.
On the user education front, the message must evolve beyond simple warnings about phishing. It needs to incorporate the tangible, high-value risks associated with pirated software. Users must understand that installing a tool like KMSAuto is equivalent to granting root-level access to an unknown third party with a direct financial motive.
Looking ahead, as blockchain technology becomes more integrated into mainstream finance, the sophistication of clipper malware is expected to increase. Future iterations might utilize more advanced context awareness, perhaps scanning emails or documents in addition to the clipboard, or employ polymorphic code that changes its signature constantly to evade signature-based detection tools. We may also see attackers move toward "transaction interception" malware that targets APIs or smart contract interactions directly, rather than relying solely on the end-user action of pasting an address.
The coordinated international effort that led to the arrest—from the initial technical reporting in South Korea, through forensic work spanning digital currency trails, culminating in raids in Lithuania and an arrest in transit to Georgia—sets a high benchmark for prosecuting cybercriminals who operate across jurisdictional boundaries. However, until the demand for illicitly obtained software wanes, the threat landscape will continue to be seeded with these seemingly innocuous, yet financially devastating, malware packages. The ongoing defense requires not just better technology, but a fundamental shift in user perception regarding the true cost of ‘free’ software. The investigation revealed the tools used, but the enduring challenge is mitigating the behavioral risks that make such campaigns viable on a scale of millions of systems.

