A highly sophisticated and targeted spear-phishing operation has been discovered that successfully compromised dozens of high-profile individuals across the Middle East, blending traditional credential theft with advanced, real-time surveillance capabilities. The victims include a cross-section of politically sensitive targets: senior government officials, academics specializing in national security, prominent journalists, business executives, and figures within the Iranian diaspora. The campaign’s discovery offers a rare, granular view into the methodology of actors operating at the nexus of state-sponsored espionage and organized cybercrime, highlighting a significant and ongoing threat to regional stability and digital freedom.
The incident came to light recently after a prominent U.K.-based Iranian human rights activist, Nariman Gharib, publicly disclosed receiving a highly suspicious link via a private WhatsApp message. Recognizing the inherent danger, the activist refrained from clicking the link but subsequently shared the malicious URL and provided technical insights to researchers. This initial act of vigilance paved the way for a deeper investigation into the campaign’s infrastructure, revealing the full extent of its invasive goals: the simultaneous theft of credentials for services like Gmail, the hijacking of secure messaging accounts, and unauthorized device surveillance.
Geopolitical Context and Timing
The timing of this digital offensive is critically important. It occurred concurrently with one of the most significant periods of anti-government unrest in recent Iranian history, marked by prolonged, widespread protests and subsequent violent state crackdowns. Crucially, the government responded to the internal dissent by imposing severe and sustained national internet blackouts, making external communications and information sharing exceptionally difficult for those within the country.
In such a volatile environment, intelligence gathering aimed at key diaspora figures, journalists covering the protests, and foreign policy experts becomes paramount for both state security agencies and adversarial intelligence services. This context immediately lends credence to the hypothesis that the campaign was driven by espionage, seeking to map communication networks, identify opposition leaders, and understand the flow of sensitive information related to the uprising. The operational environment of the Middle East, characterized by pervasive offensive cyber activity originating from multiple nation-states, ensured that external researchers were highly motivated to dissect this threat.
Unmasking the Attack Chain
Analysis of the phishing site’s source code, conducted in collaboration with leading digital security experts, confirmed the campaign was designed to be a multi-stage attack customized to the target’s platform and perceived value. The initial vector was a simple, yet highly effective, social engineering technique: a message sent via WhatsApp containing a link purporting to be an invitation to a virtual meeting or urgent communication.
The technical infrastructure relied on using a Dynamic DNS (DDNS) provider, specifically DuckDNS, to host the initial, deceptive link (e.g., a subdomain resembling whatsapp-meeting.duckdns.org). Dynamic DNS services are frequently abused by threat actors because they allow a simple, memorable URL to mask the frequently changing IP address of the actual malicious hosting server, thereby increasing resilience against takedowns and obscuring the true origin location. When contacted regarding the abuse, the DDNS provider owner reportedly requested a formal abuse report rather than immediately confirming the site’s removal, highlighting the reactive challenges faced by service providers in curbing rapid-fire phishing infrastructure deployment.
The true malicious landing page was hosted on domains like alex-fabow.online, which were registered just weeks prior to the active campaign period. Further investigation revealed a cluster of similarly named domains on the same dedicated server, suggesting a broader, pre-planned infrastructure aimed at impersonating generic meeting room platforms, such as meet-safe.online and whats-login.online.
Upon clicking the initial link, the victim was subjected to a branching attack path. For many targets, the page displayed a meticulously crafted replica of a Gmail sign-in portal, designed not only to capture primary credentials (username and password) but also to harvest the time-sensitive, second-factor authentication (2FA) codes sent via SMS or generated by an authenticator application.
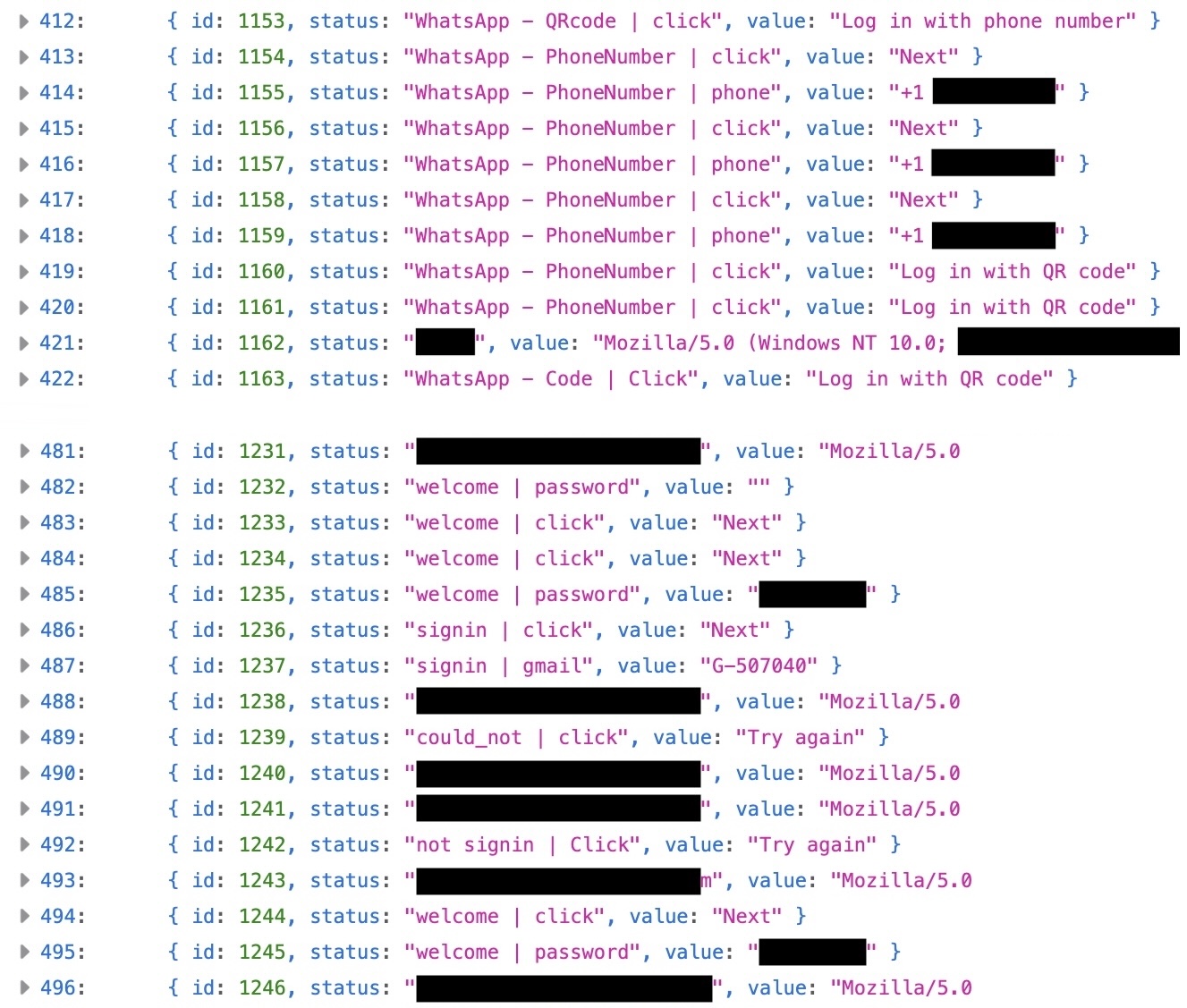
The Catastrophic OpSec Failure
In a significant operational security blunder that provided investigators with unprecedented visibility into the campaign’s success, the threat actors failed to secure their command-and-control (C2) server. Researchers were able to identify and access an exposed log file on the server simply by modifying the URL structure of the phishing page. This file, accessible without any password protection, contained a comprehensive, real-time record of all data submitted by victims during the attack flow.

This exposed dataset contained over 850 individual entries detailing interactions, including incorrect password attempts, successful credential entries, and, critically, the submission of 2FA codes, effectively functioning as a keylogger for the entire process. This forensic data allowed security professionals to reconstruct the exact steps taken by dozens of victims, confirming successful compromise. The logs also captured User Agent strings, demonstrating that the toolkit was cross-platform compatible, targeting users on Windows, macOS, iPhone, and Android devices.
The victim data retrieved from the exposed server was alarming in its diversity and geopolitical significance. Individuals successfully compromised included a senior Lebanese cabinet minister, the head of an Israeli drone manufacturing company, a national security academic based in the Middle East, and several individuals with ties to the U.S. and the Iranian diaspora. The targeting appears highly strategic, focusing on individuals whose communication and intellectual capital would be valuable to an intelligence service seeking regional insight. While the total number of verified, high-value compromises was fewer than 50, the depth of access gained—including 2FA codes—indicates that the campaign achieved substantial strategic success.
Surveillance Capabilities: Beyond Credentials
What differentiates this campaign from typical financial phishing is its deep integration of surveillance techniques. For victims targeted via WhatsApp, the attack flow included a sophisticated session hijacking component. The malicious landing page displayed a fake WhatsApp Web QR code, leveraging the platform’s legitimate device linking feature. The attackers lured targets into scanning this QR code, under the guise of joining a meeting, which immediately linked the victim’s primary WhatsApp account to a device controlled by the attackers. This granted them full access to chats, contact lists, and potentially media shared via the application, mirroring known techniques previously used against users of platforms like Signal.
Further examination of the phishing page code by security experts, including Runa Sandvik, revealed invasive browser API calls. When the page loaded, the embedded JavaScript would attempt to invoke the browser’s permission prompts for two highly sensitive capabilities:
- Geolocation Access (
navigator.geolocation): If the victim granted permission, the browser would immediately transmit the device’s precise GPS coordinates to the attacker’s server. The code was engineered to continue reporting location data every few seconds for the entire duration the page remained open, enabling continuous tracking. - Media Access (
navigator.getUserMedia): The code also sought permission to access the device’s camera and microphone. If approved, the script was capable of recording short bursts of audio and snapping photos every three to five seconds.
While no captured surveillance data (audio or images) was observed on the exposed server logs, the sheer inclusion of these invasive functions strongly suggests the actors were motivated by intelligence collection and espionage, rather than mere financial gain.
The Attribution Conundrum
Determining the true identity and motivation of the threat actor is complicated, exhibiting characteristics that blur the lines between state-backed activity and organized crime.
Arguments for State-Sponsored Espionage:
Leading experts, such as Gary Miller of Citizen Lab, noted that the operation bore "the hallmarks of an IRGC-linked spearphishing campaign." The evidence supporting this attribution includes:
- Targeting Profile: The high-value, politically sensitive targets (politicians, defense industry figures, activists) are typical of state intelligence priorities.
- Geopolitical Alignment: The campaign’s focus on the Iranian diaspora and regional adversaries (including Israeli and Lebanese figures) aligns with Iranian foreign and domestic intelligence objectives, especially during a period of internal dissent.
- Surveillance Focus: The capability to continuously track location, record audio, and capture images is almost exclusively required by espionage operations, not financially motivated cybercriminals.
- Sophistication: The multi-stage attack flow, including real-time 2FA bypass and cross-platform compatibility, suggests resources typical of a nation-state actor.
Arguments for Financially Motivated Cybercrime:
Conversely, analysis of the infrastructure pointed toward a more financially driven profile. Ian Campbell, a threat researcher, examined the domain registration data and found that the campaign’s core infrastructure had been established weeks or even months before the peak of the Iranian protests. The use of generic, high-risk domains and the operational sloppiness (the exposed server log) are not typical of elite, state-level advanced persistent threat (APT) groups, who usually maintain rigorous operational security.

Campbell characterized the domains as medium-to-high risk, linked to operations often associated with financial motives.
The Hybrid Model:
The prevailing expert consensus acknowledges the growing trend of hybrid operations. Nation-states, particularly those facing international sanctions, are known to contract or outsource cyber operations to criminal groups. This strategy provides plausible deniability, allowing the state to leverage existing criminal infrastructure and talent while insulating itself from direct attribution. The U.S. Treasury Department has previously sanctioned Iranian entities for acting as fronts for the Islamic Revolutionary Guard Corps (IRGC) to conduct targeted social engineering and phishing campaigns, lending credibility to the hypothesis that a government actor utilized a financially motivated proxy for this campaign.
Industry Implications and Future Defense
This incident underscores several crucial implications for the cybersecurity industry and vulnerable communities globally.
First, the successful use of the WhatsApp device linking feature for session hijacking demonstrates that even end-to-end encrypted messaging platforms remain vulnerable through social engineering that exploits legitimate user features. While platform providers like Meta have implemented stricter controls, users must treat any unsolicited QR code scanning request with extreme suspicion.
Second, the reliance on Dynamic DNS providers necessitates a stronger, more proactive stance from these services. While DDNS serves legitimate purposes, rapid identification and suspension of malicious subdomains are critical to shortening the lifespan of phishing campaigns, especially those targeting high-value individuals.
Finally, the surveillance components leveraging standard browser APIs—geolocation and media access—highlight the danger of granting permissions to unknown or suspicious websites. Browsers must continue to refine and strengthen permission models, providing clearer warnings to users when a site attempts to activate sensitive hardware like cameras and microphones.
For activists, journalists, and government personnel operating in politically sensitive regions, digital security training must evolve beyond simple password hygiene. Mitigation strategies must emphasize hardware-based two-factor authentication (such as physical security keys), which are impervious to SMS or time-based one-time password (TOTP) interception, and a zero-trust approach to unsolicited messages, regardless of the sender’s apparent identity. The success of this hybrid campaign confirms that threat actors will continue to innovate, leveraging geopolitical tensions to maximize the impact of targeted phishing with deeply invasive surveillance capabilities. The exposed logs provided a momentary window into this dark infrastructure; the expectation is that these campaigns will inevitably resurface, employing even greater levels of camouflage and sophistication.