The digital infrastructure landscape is grappling with the fallout from the disclosure of a severe authentication bypass vulnerability, tracked as CVE-2026-24061, which permits unauthenticated remote access to systems utilizing the GNU InetUtils telnetd server. Internet security monitoring entity Shadowserver has published sobering statistics indicating that close to 800,000 Internet-facing IP addresses are running services that exhibit Telnet fingerprints, presenting a staggering potential attack surface for malicious actors exploiting this zero-day flaw. This situation underscores a persistent, systemic weakness in managing legacy network services and embedded systems globally.
The vulnerability specifically targets older iterations of the GNU InetUtils suite, spanning versions 1.9.3, which dates back over a decade to its 2015 release, up to version 2.7. The critical security patch arrived swiftly from the open-source community, with version 2.8 being released on January 20th, marking the definitive resolution to the issue. However, the widespread deployment of vulnerable software across diverse, often unmanaged, environments means that remediation efforts will likely lag significantly behind the immediate threat.
The technical mechanics of the bypass are alarmingly simple, as detailed by Simon Josefsson, an open-source contributor who brought the flaw to light. The core issue lies in how the telnetd server processes environment variables passed from the client. The server invokes the system’s login utility, /usr/bin/login, which typically executes with root privileges, by passing the client-supplied USER environment variable as the final command-line argument. Josefsson explained that a malicious client can craft this environment variable to contain the precise string "-f root". When this crafted string is transmitted, often through manipulation of the Telnet protocol’s option negotiation sequence (specifically the IAC command), the login utility interprets the string as a command-line instruction to log in directly as the root user without requiring any form of password validation. This maneuver effectively vaporizes the established security perimeter, granting immediate, full administrative control over the affected device.
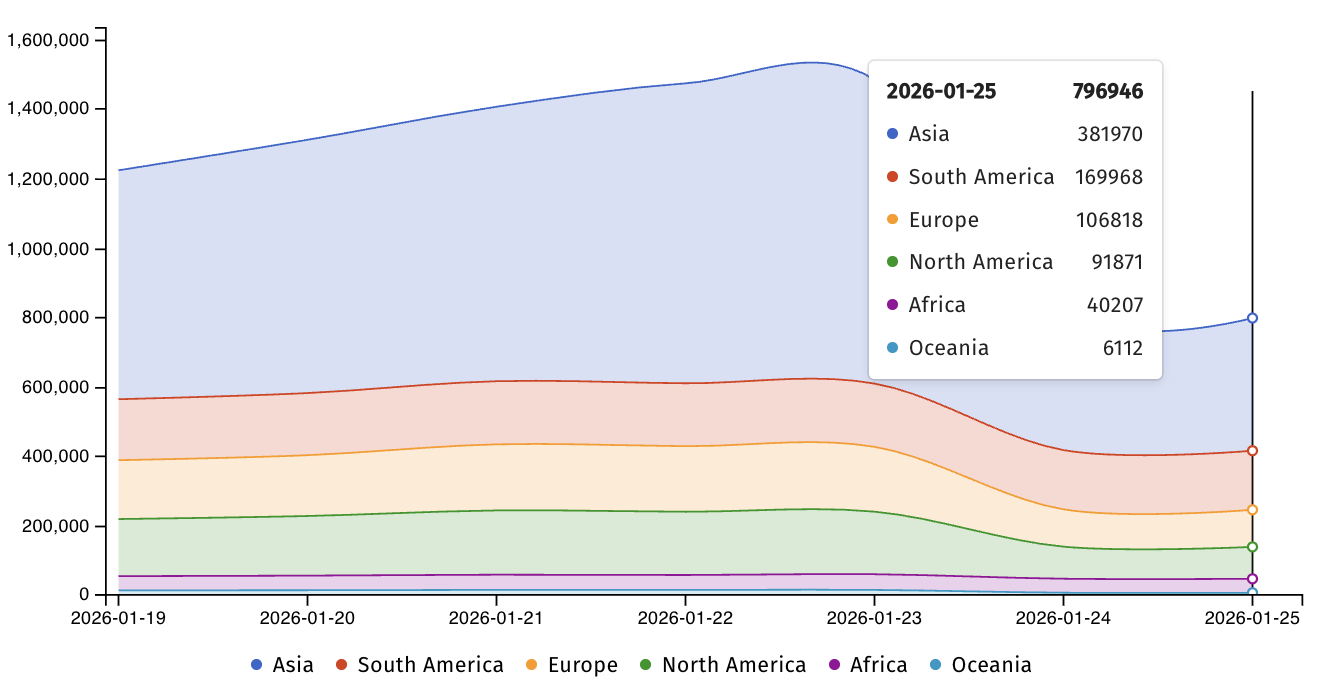
Shadowserver has provided a stark geographical breakdown of the exposed instances. Their scans reveal that out of the nearly 800,000 detected Telnet endpoints, the overwhelming majority reside in the Asia-Pacific region, accounting for over 380,000 addresses. South America follows with nearly 170,000 exposed systems, and Europe accounts for just over 100,000. Crucially, Shadowserver acknowledges a significant information gap: while they can identify exposed Telnet services, they currently lack telemetry to determine precisely how many of these devices are actually susceptible to the specific CVE-2026-24061 exploit, though the likelihood is high given the active exploitation.
Piotr Kijewski, CEO of the Shadowserver Foundation, emphasized the fundamental problem: "We are observing approximately 800,000 instances of Telnet exposed globally—a situation that, inherently, should not exist. Telnet should never be publicly accessible over the Internet, yet its presence persists, particularly on older Internet of Things (IoT) devices and deeply embedded systems." This statement captures the tension between modern security requirements and the inertia inherent in managing large fleets of specialized hardware.

The Pervasive Threat of Legacy Systems
The prevalence of vulnerable Telnet servers is deeply rooted in the architecture of GNU InetUtils. This collection of essential networking utilities—encompassing services like telnetd, ftpd, rshd, alongside diagnostic tools like ping and traceroute—is ubiquitous in many Linux distributions and proprietary firmware stacks. Because these utilities are often considered foundational and rarely require frequent updates unless a critical vulnerability arises, many devices running on these older toolsets have remained untouched for years, sometimes even exceeding a decade of operational life without patching.
This stagnation is most pronounced in the realm of industrial control systems (ICS) and IoT devices. These environments prioritize stability and long operational lifecycles over rapid patch deployment. A router, network switch, environmental sensor, or specialized industrial controller might be deployed with firmware containing a decade-old version of InetUtils, making it an ideal, long-term target for attackers aware of the protocol’s inherent security failings. Telnet’s inherent lack of encryption, combined with this new authentication bypass, creates a perfect storm for remote takeovers.
Immediate Exploitation in the Wild
The threat was not theoretical for long. Mere days following the official disclosure and patching of CVE-2026-24061, threat intelligence firm GreyNoise reported concrete evidence of active exploitation in the wild. Their telemetry indicated that malicious attempts began as early as January 21st, just one day after the patched version 2.8 was released.
The initial attack campaigns were limited but systematic. GreyNoise detected these exploits originating from 18 distinct IP addresses, resulting in approximately 60 observed Telnet sessions attempting to leverage the flaw. The attackers skillfully utilized the Telnet protocol’s "Interpret As Command" (IAC) option negotiation sequence. By injecting the specific USER=-f <user> payload during this handshake, they bypassed the standard login prompt entirely, aiming straight for shell access.
Analysis of the initial probes revealed a clear objective: targeting the root user. In a staggering 83.3% of observed attempts, the malicious payload specifically sought to elevate privileges to root, indicating an intent to gain full system compromise rather than merely executing low-level commands. While the vast majority of this activity appeared automated—evidenced by consistent terminal speed settings and predictable X11 DISPLAY values—GreyNoise noted sporadic instances suggesting "human-at-keyboard" interaction, implying that sophisticated actors or botnet operators were actively testing and validating initial access.
Following the successful (or attempted) authentication bypass, the attackers immediately shifted to post-exploitation reconnaissance and payload deployment. GreyNoise observed subsequent attempts to install Python-based malware. However, these secondary efforts often faltered, likely because the compromised devices—especially older IoT hardware—lacked the necessary Python interpreters, supporting libraries, or expected directory structures required for the malware staging process. While the initial root compromise was achieved, the deployment of secondary malware was frequently unsuccessful, suggesting the attackers were targeting a broad net of vulnerable systems, some of which were too minimal to support further infection.

Industry Implications and Expert Analysis
The revelation of CVE-2026-24061 serves as a stark reminder of the severe risks associated with maintaining legacy, unencrypted remote access protocols. For security architects and CISOs, this incident highlights several critical areas of failure:
1. Protocol Obsolescence: Telnet, alongside insecure versions of FTP and RSH, should be universally deprecated in favor of encrypted alternatives like SSH. The fact that an authentication bypass exists in a widely deployed server implementation eleven years after initial releases suggests insufficient vendor scrutiny and poor lifecycle management practices for foundational services.
2. IoT and Embedded Device Security Debt: The sheer volume of vulnerable devices points directly to the security debt accumulated in the IoT and operational technology (OT) sectors. These devices are often deployed and then forgotten, existing outside the typical enterprise patch management cycle. The reliance on outdated GNU utilities within these constrained environments means that an entire class of hardware remains vulnerable to simple, protocol-level attacks.
3. The Speed of Exploitation: The fact that active exploitation began only one day after the patch release demonstrates the speed at which the threat intelligence community and malicious actors operate. Zero-day vulnerabilities, especially those leading to root access, transition to "N-day" threats almost instantaneously, demanding near-immediate patching strategies.
From an expert perspective, the method of exploitation—manipulating environment variables passed to /usr/bin/login—is a classic software engineering oversight. It exploits the implicit trust placed in the internal execution flow rather than validating external input strictly. In modern secure coding standards, environment variables passed from external sources should never be directly used as command-line arguments to privileged execution environments without rigorous sanitization and boundary checks.
Mitigation Strategies and Future Trends
For system administrators confronting this immediate risk, the primary directive is swift remediation. The most secure path involves immediately upgrading to GNU InetUtils version 2.8 or later, which contains the necessary fix to prevent the malicious parsing of the USER environment variable.
However, recognizing the reality of legacy systems where immediate upgrading is impossible due to operational constraints or vendor abandonment, temporary mitigation steps are essential:
- Service Disablement: If Telnet functionality is not strictly required for operational continuity, the vulnerable
telnetdservice must be entirely disabled across all endpoints. - Network Segmentation and Firewalling: For systems that absolutely must retain Telnet access (a scenario highly discouraged), administrators must implement strict firewall rules. TCP port 23 should be blocked at the perimeter firewall and, ideally, restricted via internal segmentation firewalls to only allow connections from explicitly trusted administrative jump boxes or bastion hosts, never directly from the public internet.
Looking forward, this event will likely influence security priorities across several domains. We anticipate increased scrutiny from supply chain risk management frameworks concerning the versions of core utilities embedded in commercial hardware and software. Furthermore, security monitoring tools will likely tune their detection capabilities to look specifically for the Telnet IAC negotiation sequence anomalies used in this exploit, even as attackers pivot to other environmental variable abuse techniques in less patched systems.
The exposure of nearly 800,000 potential entry points highlights a fundamental truth in cybersecurity: convenience and legacy compatibility often come at the expense of security. Until the industry collectively retires insecure protocols like Telnet and enforces robust patch management for embedded devices, these "forgotten" systems will continue to serve as low-hanging fruit for threat actors seeking broad, unauthenticated access to the global network infrastructure. The financial and operational costs associated with cleaning up compromises stemming from such easily exploitable flaws far outweigh the investment required for proactive protocol migration and diligent asset inventory management.

