The United States Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent directive compelling federal agencies to remediate critical security vulnerabilities present in installations of Gogs, a self-hosted Git service. This action follows confirmed exploitation in the wild, categorizing the flaw as a zero-day threat that poses an immediate risk to the integrity and confidentiality of government systems. The vulnerability, formally cataloged as CVE-2025-8110, is a particularly insidious form of Remote Code Execution (RCE) rooted in a fundamental failure of input sanitization within the application’s file handling mechanisms.
Gogs, written in the Go programming language, has carved out a niche as a lightweight, often containerized, alternative to larger enterprise code management solutions like GitLab or GitHub Enterprise. Its simplicity and low resource overhead have made it an attractive option for organizations, including various government departments, seeking localized control over source code repositories and collaboration workflows. However, this ubiquity, especially when deployed facing the public internet for remote access, transforms any critical flaw into a widespread threat vector.
The technical mechanism underpinning CVE-2025-8110 centers on a path traversal weakness residing within the application’s PutContents API endpoint. This API is designed to facilitate the writing or updating of file contents within a controlled repository structure. The critical failure lies in the software’s inability to properly validate user-supplied paths, allowing an authenticated attacker to manipulate the destination of file writes by leveraging symbolic links (symlinks) within a crafted repository. This technique effectively allows the attacker to break out of the intended repository sandbox and overwrite arbitrary files located outside the designated working directory.
Crucially, this vulnerability is not merely a standalone issue; it represents a bypass of security controls implemented to mitigate a preceding RCE vulnerability, CVE-2024-55947. This suggests a pattern of incomplete remediation or a fundamental architectural weakness that one patch failed to fully address. By exploiting CVE-2025-8110, an adversary can direct file-write operations toward configuration files critical to the system’s operation. The most impactful target identified is the Git configuration setting known as sshCommand. By overwriting this specific setting with commands crafted by the attacker, the system is effectively tricked into executing arbitrary code upon subsequent Git operations, culminating in a complete system compromise. This chain of exploitation transitions an authenticated user from a limited role to a full remote execution capability.
Discovery and Disclosure Timeline: A Race Against Exploitation
The identification of this severe vulnerability is credited to Wiz Research, who uncovered the issue during forensic analysis of a malware infection on one of their customer’s externally accessible Gogs servers back in July. Following standard responsible disclosure protocols, Wiz reported the findings to the Gogs maintainers on July 17th. The response timeline, however, reveals a significant delay in acknowledgment and patching, a common challenge in the ecosystem of open-source, volunteer-maintained software.

Gogs maintainers reportedly acknowledged the detailed report nearly three and a half months later, on October 30th. This gap provided a critical window for malicious actors who may have already been probing for such flaws. The official patches, which introduced necessary symlink-aware path validation across all file-write entry points—a direct countermeasure to the path traversal issue—were released only last week, according to Wiz’s disclosure summary.
The timeline of active exploitation is even more concerning. Wiz Research documented a first wave of attacks sometime before the patch release, and critically, observed a second wave targeting this vulnerability as an active zero-day exploit beginning on November 1st. This means that exploitation was actively occurring for weeks, potentially months, before patches were made available, and shortly after the initial discovery.
The Scope of Exposure and Federal Urgency
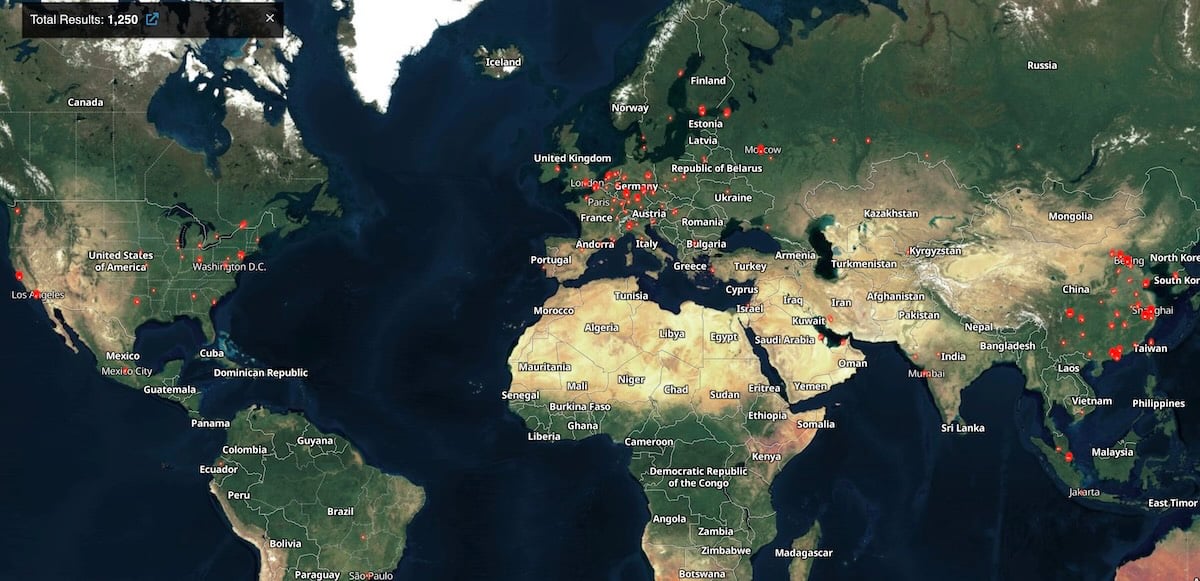
The breadth of the potential impact is alarming. Wiz researchers utilized Shodan to map the internet-facing footprint of Gogs instances, discovering over 1,400 servers accessible via HTTP headers indicating a Gogs login page. Of these, a staggering 1,250 instances reportedly remained exposed to the public internet at the time of the analysis, indicating a significant population of vulnerable targets worldwide. More worryingly, the investigation revealed that over 700 of these identified instances showed active signs consistent with compromise—evidence suggesting successful exploitation during the zero-day campaigns.
In response to the confirmed real-world exploitation and the documented exposure within the digital supply chain, CISA has officially integrated CVE-2025-8110 into its Known Exploited Vulnerabilities (KEV) Catalog. This inclusion is not a mere advisory; it triggers mandatory compliance actions for Federal Civilian Executive Branch (FCEB) agencies. FCEB agencies—which encompass crucial non-military departments like the Department of Energy, the Department of Justice, the Department of Homeland Security, and the Department of State—have been given a strict remediation deadline of three weeks, set for February 2, 2026.
CISA’s directive underscores the severity: "This type of vulnerability is a frequent attack vector for malicious cyber actors and poses significant risks to the federal enterprise." This language confirms that threat actors view such flaws as low-hanging fruit for initial network penetration or staging grounds for more complex operations. The guidance compels agencies to immediately apply vendor-supplied mitigations, adhere to existing Binding Operational Directive (BOD) 22-01 guidance if the service is cloud-based, or, as a final resort, immediately decommission the product if patching is not feasible.
Expert Analysis: The Context of Supply Chain Risks
This incident highlights several critical pressure points in modern IT security management, particularly within environments utilizing open-source components like Gogs.

1. The Authentication Hurdle Misconception: A key takeaway is the necessity of the "authenticated attacker" prerequisite. While this requirement might seem to limit the scope compared to unauthenticated RCEs, in environments managing source code, authentication is often trivially obtained or assumed for internal or semi-trusted external users. A compromised developer credential, a misconfigured internal API key, or even a successful phishing attempt against a low-level user grants the necessary access to weaponize this flaw. The barrier to entry for catastrophic impact is therefore lower than it appears.
2. The Interconnectedness of Vulnerabilities: The fact that CVE-2025-8110 acts as a bypass for a prior RCE (CVE-2024-55947) signals systemic flaws in the initial patch implementation or a failure to comprehensively sanitize input across all related functions. Security engineering teams must recognize that fixing one vulnerability often exposes the underlying architectural weakness that allowed the first exploit. Comprehensive root-cause analysis, rather than surgical patching, is essential for robust security.
3. The Burden on Maintainers: The multi-month delay between discovery and acknowledgment by Gogs maintainers underscores the inherent risks associated with relying on potentially under-resourced open-source projects for mission-critical infrastructure. While open-source fosters transparency, it does not guarantee rapid response times, especially when maintainers are volunteers balancing personal and professional obligations. This places an amplified burden on consuming organizations, like federal agencies, to maintain hyper-vigilance regarding the security posture of every third-party component they integrate.
Mitigation and Forensic Imperatives for Gogs Users
Beyond the mandatory federal patching timeline, all organizations running Gogs installations must adopt immediate, defense-in-depth measures to shrink the attack surface.
Immediate Surface Reduction: The most proactive step advised is to immediately disable the default setting allowing open registration. In nearly all enterprise or governmental contexts, source code management should never permit anonymous sign-ups. Furthermore, limiting network access via stringent controls, such as routing access exclusively through a Virtual Private Network (VPN) or enforcing strict IP allow lists at the firewall level, renders internet-facing exposure moot, even if the vulnerability remains unpatched.
Forensic Deep Dive: For system administrators concerned about prior compromise, the focus must shift to behavioral indicators rather than just version numbers. The exploitation technique provides clear forensic signatures:
- API Abuse: Scrutinize logs for abnormal or high-volume usage of the
PutContentsAPI, especially requests originating from newly authenticated or low-privilege accounts. - Artifact Inspection: Search file systems for repositories exhibiting suspicious characteristics. The attackers in the documented waves created repositories with randomized, eight-character names during their compromise attempts. Identifying these ephemeral, seemingly random repositories is a strong indicator of malicious activity.
- Configuration Tampering: Directly examine critical configuration files, specifically looking for modifications to SSH command settings that might redirect execution paths or install backdoors.
Future Trends: Hardening the Self-Hosted Perimeter
The Gogs RCE incident serves as a potent reminder that as organizations migrate to lightweight, cloud-native tools, the security perimeter shifts inward to the application layer itself. The trend toward containerization and microservices means that self-hosted tools, often deployed rapidly for convenience, are frequently deployed without the rigorous security hardening applied to mature SaaS offerings.
The reliance on path validation to prevent arbitrary file overwrites is an aging security paradigm. Modern application security demands rigorous, context-aware input validation, often involving abstract syntax tree (AST) analysis or deep symbolic execution when dealing with file system operations. The vulnerability in Gogs suggests a failure to adopt these contemporary safeguards against path manipulation, a class of bug that remains alarmingly prevalent across various software stacks written in languages that offer low-level file system access.
For the broader technology landscape, this event reinforces the critical role of proactive vulnerability disclosure programs and the necessity for rapid patching cycles, especially for software components that are frequently exposed to the public internet. CISA’s swift action signals an increased regulatory appetite to enforce rapid remediation when zero-day exploitation crosses the threshold into the federal network perimeter, setting a precedent that will likely cascade down to critical infrastructure sectors relying on similar open-source tooling. The focus going forward must be on automating the detection of these environmental misconfigurations and ensuring that the speed of deployment does not continually outpace the diligence of security verification.

