The global claims administration and risk management powerhouse, Sedgwick, has officially acknowledged a significant cybersecurity incident targeting its specialized arm, Sedgwick Government Solutions (SGS). This subsidiary plays a critical role in managing sensitive processes for numerous U.S. federal agencies, making the breach far more consequential than a typical corporate data compromise. The confirmation, though sparse on immediate technical details, has sent ripples through the federal contracting landscape, highlighting persistent vulnerabilities within the third-party ecosystem supporting core government functions.
Sedgwick, a behemoth in its field, boasts a global footprint supporting over 10,000 clients across 80 nations, including nearly 60% of the Fortune 500. Its primary operations—claims administration and comprehensive risk management—touch upon vast amounts of personal and corporate data. However, it is the focused operations of SGS that draw immediate governmental scrutiny. This division services more than two dozen critical federal agencies, handling essential, often high-stakes, administrative tasks.
The roster of clients served by SGS reads like a catalog of key American regulatory and security bodies. Among the confirmed users of SGS services are the Cybersecurity and Infrastructure Security Agency (CISA), the Department of Commerce, the United States Citizenship and Immigration Services (USCIS), the Department of Homeland Security (DHS), the U.S. Department of Labor, and Customs and Border Protection (CBP), alongside the U.S. Coast Guard. The implication of a breach within an entity supporting agencies responsible for national security, immigration processing, and critical infrastructure defense cannot be overstated.
In a statement confirming the intrusion, a Sedgwick spokesperson emphasized the isolation protocols in place. They confirmed that the incident was contained strictly to Sedgwick Government Solutions and stressed that the broader Sedgwick corporate network, encompassing its massive global claims data infrastructure, remained unaffected. This segmentation—a key tenet of modern enterprise security architecture—is vital for limiting the blast radius of any compromise. The spokesperson detailed that upon detection, the company immediately activated its established incident response framework, engaging external, specialized cybersecurity experts coordinated through outside legal counsel to conduct a thorough forensic investigation.
The specific point of entry appears to have been an "isolated file transfer system" utilized by SGS. This detail suggests the threat actors may have targeted a specific ingress/egress point designed for secure data exchange with government partners, potentially exploiting a weakness in how documents were moved between SGS and its federal clients. Crucially, the company has stated there is "no evidence of access to claims management servers," an important distinction given the sensitive nature of the data handled by the parent company. Furthermore, Sedgwick assured stakeholders that the operational continuity of SGS in serving its government clientele has not been impaired. Law enforcement agencies have been formally notified, commencing the official governmental inquiry alongside the internal technical review.

The TridentLocker Connection and Ransomware Tactics
While Sedgwick’s initial communication avoided naming the responsible party, subsequent developments strongly suggest the involvement of the TridentLocker ransomware operation. This attribution comes directly from the threat actors themselves, who have publicly claimed responsibility for the attack on SGS. Such claims often accompany demands for ransom and are frequently used to apply pressure on compromised organizations.
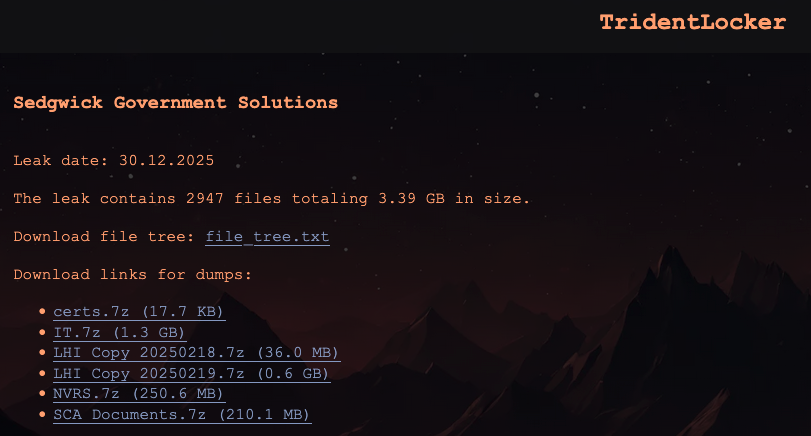
TridentLocker actors assert they exfiltrated approximately 3.39 gigabytes of documentation from the compromised subsidiary. In a standard double-extortion tactic increasingly prevalent in the ransomware landscape, the group has allegedly begun publishing samples of the stolen data on their dark web leak site hosted on the Tor network. This dual threat—data encryption combined with data exposure—is designed to maximize the financial and reputational damage, often forcing victims to pay even if backups allow for system restoration.
TridentLocker is a relatively newer player, having first appeared on the threat radar in November. Its victimology, though currently limited to about a dozen entities listed on its leak site, already includes significant international organizations. A notable prior victim is Bpost, the Belgian Post Group. Bpost confirmed a breach affecting its network around early December, though, similar to Sedgwick’s report, they maintained that their core postal operations remained functional despite the ransomware event. The pattern of targeting logistics and administrative service providers suggests TridentLocker may be prioritizing organizations that act as crucial, yet often less visibly hardened, intermediaries for larger entities or governments.
Expert Analysis: The Perils of Third-Party Risk
The breach at SGS serves as a stark, high-profile case study in the escalating risk associated with third-party vendor management, particularly within the government contracting space. For decades, large federal agencies have outsourced complex administrative functions—like benefits processing, claims adjudication, and records management—to specialized private sector firms to enhance efficiency and manage costs. This practice, however, concentrates sensitive data across a sprawling supply chain of contractors.
From a risk management perspective, SGS represents a "choke point." Compromising one well-connected contractor can provide access to data streams from multiple, disparate government entities. Security analysts often refer to this as "supply chain risk amplification." If the data housed by SGS includes personally identifiable information (PII) or protected health information (PHI) related to federal employees, veterans, or applicants for immigration benefits, the potential for widespread identity theft and bureaucratic disruption is severe.
The isolation strategy employed by Sedgwick—segmenting SGS from the main enterprise—is commendable but not foolproof. Attackers who gain a foothold within a segmented network often dedicate significant time to lateral movement, attempting to pivot from the initial point of compromise (the file transfer system) into other accessible, albeit logically separated, environments. The success of the TridentLocker group in exfiltrating 3.39 GB suggests a period of sustained presence within the target environment, long enough to identify, stage, and transfer data before detection.

The fact that the breach involved an isolated file transfer system is particularly telling. These systems are inherently high-value targets because they manage the flow of sensitive data out of secure environments or into controlled contractor systems. Weaknesses here—perhaps outdated authentication protocols, unpatched server software, or misconfigured access controls on the external interface—provide a direct pipeline for data exfiltration without necessarily requiring deep penetration into the core operational network.
Industry Implications and Regulatory Scrutiny
For the federal contracting community, this incident mandates an immediate reassessment of their security posture, particularly concerning adherence to mandates such as the Cybersecurity Maturity Model Certification (CMMC) requirements, even if SGS itself might not be directly subject to the strictest CMMC levels depending on the specific contracts held. The incident underscores that compliance checklists alone are insufficient; continuous, proactive defense against evolving ransomware techniques is essential.
Agencies like CISA, which itself is listed as an SGS client, will be under immense pressure to review their due diligence processes for vetting contractors. How effectively did CISA monitor the security posture of SGS? Did any existing compliance reports flag the potential vulnerability in the file transfer mechanism? This breach will likely fuel regulatory momentum toward stricter enforcement of security standards across the entire federal IT ecosystem, potentially leading to more stringent contractual language regarding incident reporting timelines, mandated third-party audits, and default penalties for successful intrusions originating from a vendor.
The reputational damage extends beyond Sedgwick’s immediate financial losses related to the investigation and potential regulatory fines. Trust is the currency of the claims administration business. When a contractor managing sensitive government casework suffers a major data exposure, it erodes public and governmental confidence in the outsourcing model itself. Agencies may become more hesitant to delegate critical functions, leading to potential inefficiencies as tasks are potentially brought back in-house or re-tendered under hyper-conservative security parameters.
Future Trajectories and Defensive Evolution
The TridentLocker attack on Sedgwick Government Solutions signals several enduring trends in the cyber threat landscape:
-
Targeting the Intermediary: Threat actors are increasingly focusing on mid-tier service providers like SGS. These firms possess highly valuable government data but may not command the same immediate defensive resources or public visibility as the primary government agencies themselves. They represent a softer, yet equally lucrative, target.
-
The Persistence of Double Extortion: The immediate publication of alleged data confirms that ransomware groups are fully committed to the data exfiltration component of their attacks. This necessitates a shift in organizational thinking from simple data recovery (which backups handle) to comprehensive data governance and breach response planning that anticipates public disclosure.
-
The Criticality of Network Segmentation Verification: Sedgwick’s assertion of network segmentation is the first line of defense. However, organizations must move beyond merely stating segmentation exists to actively and continuously proving it through rigorous penetration testing and red teaming exercises that specifically attempt cross-segment movement. An "isolated system" is only as strong as its access controls to the rest of the network.
For organizations handling sensitive government data, the path forward requires a significant investment in Zero Trust architecture principles, particularly around data transfer mechanisms. File transfer systems, often legacy components, must be modernized with stringent mutual authentication, micro-segmentation down to the process level, and continuous monitoring for anomalous data egress patterns. The incident at SGS serves as a definitive warning: in the interconnected world of federal contracting, a vulnerability in one contractor’s file server can become a national security concern. The comprehensive investigation now underway must not only identify how TridentLocker gained entry but also rigorously test whether the safeguards meant to protect the parent company were truly impenetrable against a determined, patient adversary operating within a supposedly segregated environment.

