The persistent threat actor behind the GlassWorm malware campaign has resurfaced, initiating a fourth, more targeted wave that specifically targets the macOS developer ecosystem. This latest iteration leverages malicious extensions distributed through the OpenVSX registry, deploying trojanized cryptocurrency wallet applications to compromise sensitive user data and credentials. This development marks a significant pivot for the campaign, which previously concentrated its efforts on Windows environments, signaling a calculated adaptation to new high-value targets within the software development community.
The Vector: Compromising the Developer Workflow
Visual Studio Code (VS Code) has become an indispensable tool for modern software engineering, relying heavily on extensions to augment its functionality. These extensions, sourced from official repositories like the Microsoft Visual Studio Marketplace or vendor-neutral alternatives such as OpenVSX, introduce features ranging from language support and debugging tools to themes and productivity enhancements. It is precisely this trust inherent in the developer workflow that threat actors exploit. GlassWorm’s methodology centers on injecting malicious code into these extensions, weaponizing a tool developers willingly install to improve their efficiency.
The OpenVSX registry, designed as an open, community-driven repository, naturally attracts developers seeking alternatives to Microsoft’s curated marketplace, often for compatibility reasons or philosophical preference for open standards. This decentralization, while beneficial for software freedom, introduces a broader attack surface that GlassWorm is adept at navigating.

The initial discovery of GlassWorm in October revealed a sophisticated technique: embedding malware using "invisible" Unicode characters to evade rudimentary detection mechanisms within the extension metadata or code listings. Upon installation, the payload executed a broad spectrum of data exfiltration activities, targeting credentials for critical development platforms like GitHub and npm, alongside sensitive cryptocurrency wallet information stored in browser extensions. Furthermore, the malware established persistent remote access capabilities, utilizing VNC for direct control and leveraging SOCKS proxies to mask its network traffic through the victim’s compromised machine.
Despite immediate public disclosures and subsequent remediation efforts by platform maintainers, GlassWorm demonstrated resilience. It returned in early November, once again exploiting the OpenVSX platform, and reappeared in early December, this time targeting the official VS Code marketplace. This pattern of repeated re-emergence underscores the cat-and-mouse game inherent in platform security, where threat actors quickly iterate to bypass newly implemented security controls.
The macOS Evolution: New Obfuscation and Escalated Aims
The fourth wave, meticulously analyzed by researchers at Koi Security, reveals a calculated strategic shift. The malware is now laser-focused on macOS, necessitating fundamental changes to its execution and persistence mechanisms to align with Apple’s operating system architecture.
Previous iterations relied on Windows-specific tools like PowerShell for execution and Registry modifications for persistence. The macOS variant discards these in favor of native Apple tooling. The execution chain now employs AppleScript, a scripting language deeply integrated into the macOS environment, and leverages LaunchAgents—the standard macOS method for ensuring software runs persistently across system restarts—to maintain its foothold on the compromised machine.

Technically, the obfuscation method has also evolved. Moving away from the Unicode trickery of the first two waves and the compiled Rust binaries seen in the third, this latest payload employs an AES-256-CBC encrypted payload concealed within compiled JavaScript files embedded within the OpenVSX extensions. This strong encryption requires specific decryption keys held only by the command-and-control (C2) infrastructure, making static analysis significantly more challenging.
A crucial evasive measure observed is a mandatory 15-minute delay before the malicious logic initiates execution. This deliberate pause is a common tactic designed to bypass automated security sandbox environments and dynamic analysis tools that often terminate processes after a short timeout, thereby allowing the malware to appear benign during initial automated scrutiny.
Significantly, the C2 communication backbone remains remarkably consistent: the Solana blockchain. The use of a blockchain for C2 infrastructure is a hallmark of modern, sophisticated threat actors. It provides a decentralized, pseudonymous, and often censorship-resistant channel for receiving commands and exfiltrating small amounts of data, making attribution and network blocking substantially more difficult than traditional C domain-based C2s. Researchers have noted continued overlap in the underlying infrastructure supporting this C2 mechanism, suggesting the same threat group is orchestrating these successive attacks.
The Escalation: Targeting Hardware Wallet Integrity
While the scope of credential theft remains broad—including over 50 browser-based cryptocurrency extensions, developer credentials (GitHub, npm), and general browser data—the most alarming addition in this fourth wave is the direct targeting of hardware cryptocurrency wallets.
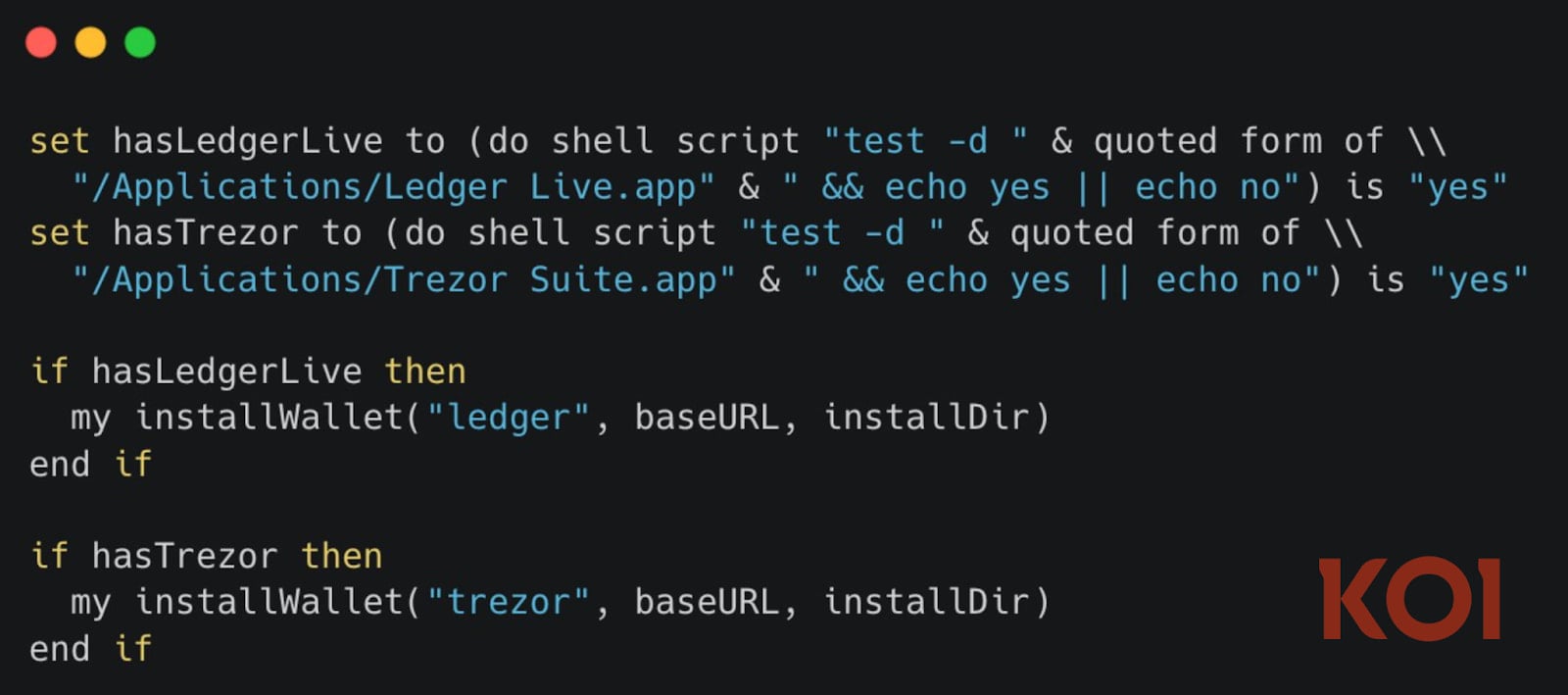
GlassWorm is now actively scanning the macOS host system for established hardware wallet management applications, specifically naming Ledger Live and Trezor Suite. The objective is not merely to steal seed phrases or passwords stored on the machine, but to actively replace the legitimate application executables with trojanized versions.
This "application replacement" technique represents a severe escalation in the attack’s severity. If successful, the attacker would gain the ability to intercept transactions authorized by the user via their physical hardware device, effectively rendering the security benefits of the hardware wallet moot. The compromised application would display the legitimate transaction details to the user while secretly broadcasting a modified, attacker-controlled transaction to the network.
However, Koi Security reports a current impediment to this critical function: the trojanized wallet replacements are currently returning empty files. This failure suggests a temporary infrastructure gap. As the researchers hypothesize, the capability itself is fully engineered and ready—the architecture for replacement is in place—but the necessary malicious payloads tailored for the macOS wallet executables might still be under development, or the infrastructure linking the compromised extension to the payload delivery system is undergoing migration. Crucially, all other primary malicious functions—credential theft, Keychain password harvesting (another significant macOS-specific target), data exfiltration, and persistence establishment—are reported as fully operational.
Industry Implications and the Supply Chain Risk
The GlassWorm campaign is a potent illustration of the increasing sophistication of software supply chain attacks, particularly targeting developer tools. Developers, operating under tight deadlines and often installing dozens of extensions weekly, are inherently exposed.

The implications for software security extend far beyond the individual developer:
- Erosion of Trust in Developer Ecosystems: The repeated successful infiltration of both official (VSCode) and vendor-neutral (OpenVSX) marketplaces erodes the fundamental trust developers place in these distribution channels. When the tools of creation are themselves compromised, the integrity of all downstream software products is potentially jeopardized.
- Focus on High-Value Assets: By pivoting specifically to macOS and focusing heavily on hardware crypto wallets, the attackers are demonstrating a clear understanding of their target demographic’s highest-value digital assets. Developers working in finance or cryptocurrency are prime targets for maximum financial impact.
- Platform Response Gaps: The ability of GlassWorm to return across multiple iterations, adapting its obfuscation (Unicode to Rust binaries to AES-encrypted JS) and execution methods (PowerShell/Registry to AppleScript/LaunchAgents), highlights that platform-level vetting processes, while improving, are still reactive rather than predictive against novel evasion techniques. OpenVSX, by its nature, may have inherently looser controls than Microsoft’s official channel, making it an easier entry point, yet the threat demonstrates cross-platform viability.
Mitigation and Future Threat Landscape Analysis
The immediate recommendation for any developer using VS Code or compatible editors is a comprehensive security audit. Immediate removal of any potentially compromised extensions is mandatory. Furthermore, due to the breadth of credential theft—GitHub, npm, and browser data—a complete reset of platform-specific secrets is necessary: changing GitHub passwords, revoking and regenerating all npm tokens, and scrutinizing local system configurations for signs of persistent malicious scripts or unauthorized LaunchAgents.
From an industry perspective, the future trajectory of threats like GlassWorm will likely emphasize deeper integration into development environments. We anticipate a trend toward:
- AI-Assisted Payload Generation: Utilizing generative AI to create polymorphic malware code that constantly shifts its structure to defeat signature-based detection, making the encryption and obfuscation seen in GlassWorm Wave 4 the baseline, not the exception.
- Zero-Trust Extension Vetting: Marketplaces will likely be forced to move toward mandatory code signing by verified entities or implement significantly more rigorous, automated static and dynamic analysis pipelines that specifically test for post-installation persistence mechanisms like LaunchAgents, rather than just initial code review.
- Hardware Wallet Interception: The ambition to compromise hardware wallet authorization is a critical marker. If this functionality becomes reliable, it will force a re-evaluation of "cold storage" security assumptions, particularly for users who bridge the gap between offline security and online convenience by using desktop management applications.
The fact that download counters, even when potentially inflated by threat actors (showing over 33,000 installs for some affected extensions), indicate significant reach underscores the urgency. GlassWorm is not merely opportunistic; it is persistent, adaptive, and actively escalating its technical capabilities to achieve high-value financial and intellectual property theft within the sensitive realm of software development. The adaptation to macOS confirms that no operating system within the professional development sphere is safe from these evolving, supply-chain-focused threats.

