The Gootloader malware operation, a persistent threat actor specializing in initial access brokerage for subsequent cybercriminal activities—including high-stakes ransomware deployments—has implemented a sophisticated evolution in its delivery mechanism. Security researchers have observed the threat actor employing highly unusual, segmented ZIP archives, often chaining together between 500 and 1,000 individual compressed files to conceal the final malicious payload, a JScript file. This technique represents a significant escalation in anti-analysis strategies, specifically targeting the automated static and dynamic analysis pipelines relied upon by modern security tools.
This novel packaging method deliberately engineers file corruption from the perspective of standard extraction utilities. While the concatenation of hundreds of ZIP segments creates a single, massive file structure, this structure is specifically crafted to be functional only under native operating system decompression routines. Crucially, analysis environments reliant on widely adopted third-party libraries, such as those underpinning 7-Zip or WinRAR, often fail catastrophically when attempting to parse the file header and directory structures. The resulting crash or unhandled exception prevents the automatic extraction and subsequent detonation of the embedded JScript payload, effectively blinding static scanning engines.
This shift in delivery methodology underscores the continuous "arms race" between threat actors and the cybersecurity industry. Gootloader, which has been intermittently active since 2020, demonstrated a tactical resurgence following a reported seven-month hiatus late last year. Initial reports detailing its return highlighted the use of malformed ZIP archives, often characterized by minor structural anomalies or simple filename mismatches designed to confuse basic unpacking scripts. The current iteration, however, demonstrates a quantum leap in complexity, moving from simple structural flaws to deliberately crafted, massive file corruption designed to overload or confuse parsing engines through sheer scale and engineered inconsistency.
Deconstructing the Obfuscation: Structural Anomalies as a Weapon
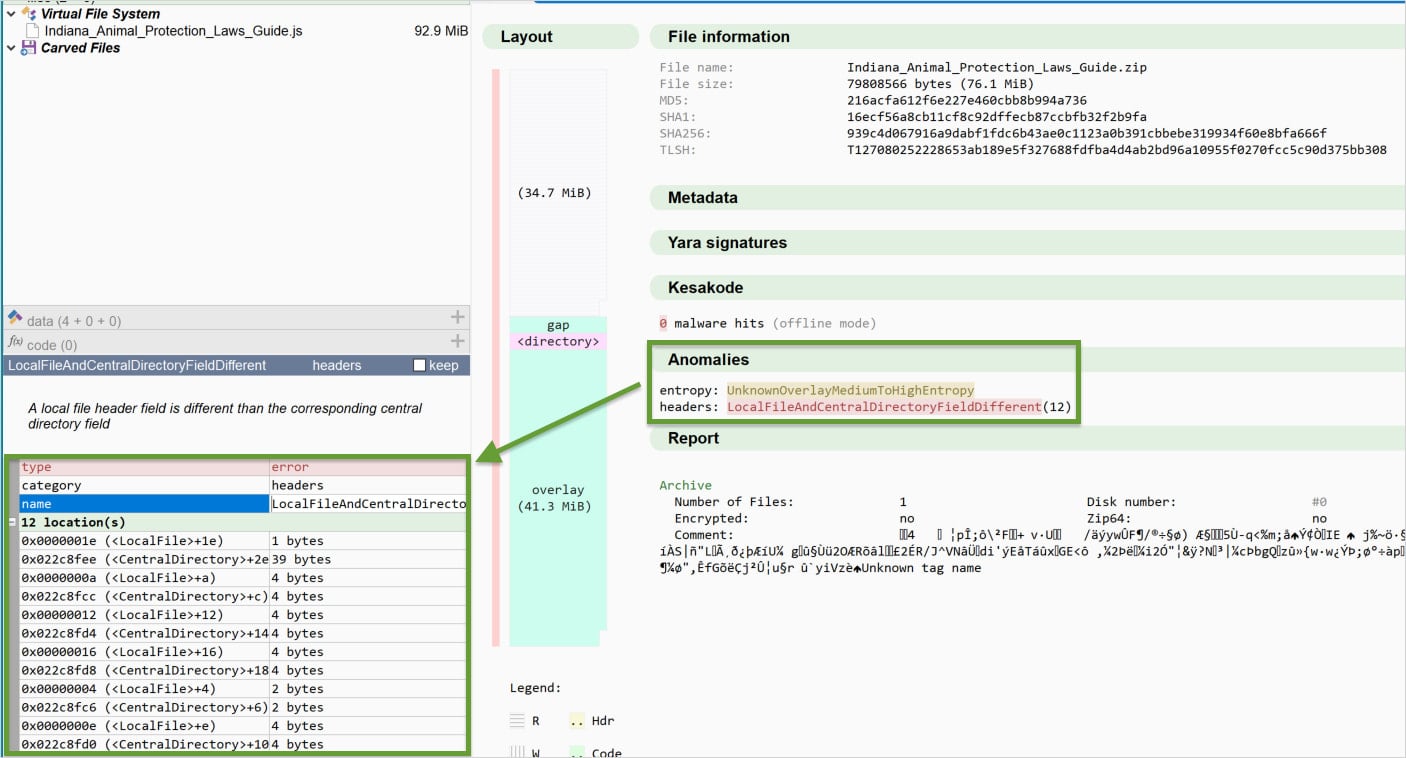
The core innovation lies in how the ZIP archives are constructed and concatenated. Threat actors are leveraging undocumented or non-standard interpretations of the ZIP file format specification. A standard ZIP file contains a Local File Header (LFH) for each file, followed by the actual compressed data, and finally, a Central Directory structure that provides an index of all files within the archive.

Gootloader operators are now aggressively manipulating these components across the concatenated chain. Researchers analyzing recent samples have identified extensive obfuscation mechanisms that go beyond simple structural breakage. Key among these is the deliberate introduction of inconsistencies between the metadata recorded in the LFHs and the overarching Central Directory structure. By populating these directories with hundreds, potentially thousands, of repeating or contradictory entries—but ensuring the Windows native extraction utility (which may prioritize certain header reads over others) can still piece together the correct sequence to reach the payload—the attackers achieve a dual objective. They evade tools that require strict adherence to the ZIP specification for reliable parsing, while maintaining functionality for the intended victim environment running default Windows utilities.
The payload itself remains consistent in its initial stages: an archived JScript file. Upon successful, native decompression, the script is designed to execute via the Windows Script Host (WScript) environment, typically launched from a temporary directory. This initial execution is a critical pivot point. To ensure resilience and recurring access, the malware immediately establishes persistence. This is achieved by injecting malicious shortcut (.LNK) files into the system’s Startup folder. These shortcuts are engineered to point directly to a second, often modified, JScript file.
The subsequent execution chain is highly characteristic of established initial access techniques. The initial payload launch triggers the execution of the second JScript via the command-line interpreter, CScript, often utilizing NTFS shortnames to obscure directory paths or filenames. This is rapidly followed by a technique common in modern malware delivery: PowerShell spawning an instance of PowerShell. This dual-layer invocation of PowerShell is frequently used to fetch and execute subsequent stages of the attack, often leading to the deployment of Cobalt Strike beacons or other sophisticated post-exploitation frameworks that facilitate the final ransomware payload delivery.
Industry Implications: The Limits of Automated Defense
The evolution of Gootloader’s delivery mechanism presents significant challenges across the security industry, particularly for organizations heavily reliant on automated threat analysis platforms.
Firstly, Sandbox Evasion is significantly enhanced. Traditional sandboxes often rely on emulated file system interactions or common archive parsing libraries to unpack and analyze suspicious attachments. When a file parser encounters a sequence of 1,000 concatenated ZIP headers, the resulting resource consumption and structural confusion often lead to timeout errors or analysis failures before the malicious script is ever revealed. This forces analysts to manually inspect the file, drastically slowing down response times for zero-day variants.

Secondly, Endpoint Detection and Response (EDR) Gaps are exposed. While EDR solutions monitor process execution, they may struggle to correlate the initial file download event with the subsequent successful, native extraction by Windows utilities, especially if the extraction process itself is not immediately flagged as suspicious behavior. The reliance on native Windows tools (WScript, CScript) rather than external executables further lowers the heuristic alert threshold for many EDR systems.
Thirdly, Threat Intelligence Utility is diminished unless specific signature matching is rapidly updated. Generic YARA rules targeting common ZIP structure might fail against these heavily customized archives. As security vendor Expel researchers demonstrated, effective detection currently requires highly specific YARA rules that look for the combination of expected ZIP header features, the presence of hundreds of repeating LFHs, and specific End-Of-Central-Directory (EOCD) record characteristics that betray the intentional corruption scheme. This demands continuous, high-fidelity threat intelligence sharing to keep pace.
Expert Analysis: The Intentional Trade-Off of Functionality
The technical decision to rely on native Windows utilities for decompression, while breaking third-party tools, reveals a calculated risk assessment by the threat actors. They are prioritizing the bypass of automated security controls over universal compatibility. In a typical enterprise environment, Windows remains the dominant operating system, and its built-in compression utility is designed to handle archives robustly, even those with minor errors, as part of maintaining backward compatibility and user experience.
The trade-off is clear: an attacker is willing to risk detection by an advanced security sandbox that might fail to unpack the file, provided the target endpoint—a standard, unhardened Windows machine—will successfully unpack and execute the script without friction. This strategy capitalizes on the security industry’s tendency to build analysis environments based on standardized, open-source libraries (like those used by 7-Zip) rather than replicating the specific, often proprietary, logic embedded within Microsoft’s native decompression binaries.
Furthermore, the persistence mechanism—leveraging LNK files in the Startup folder—is an antiquated but highly effective technique. Modern security tooling often focuses its heuristic scrutiny on WMI persistence, registry modifications, or scheduled tasks. Simple addition of a shortcut file to a well-known system folder, especially one pointing to a legitimate system process (WScript/CScript), often slips under the radar until the lateral movement phase begins. The use of NTFS shortnames further illustrates an understanding of how legacy file system metadata can be exploited for obfuscation, a technique often overlooked in modern, cloud-centric security monitoring.
Future Trajectory and Mitigation Strategy
The continuous innovation by Gootloader suggests that threat actors are investing heavily in making their initial access phase as opaque as possible. We can anticipate further refinement in these file-based evasion techniques. Future iterations may involve:
- Polymorphic Concatenation: Varying the number of ZIP segments (e.g., fluctuating between 300 and 1,500) or changing the internal structure of the segment chains to defeat static YARA rules based on counts or specific repeating patterns.
- Time-Based Triggers: Embedding logic within the compressed structure (if possible via metadata manipulation) that only allows successful decompression or execution after a specific delay or after checking for sandbox artifacts.
- Hybrid Archives: Incorporating other benign file types into the chain, making the overall container appear less like a purely malicious archive bundle and more like a corrupted, multi-part data dump.
For defenders, the response must be multi-layered and focus on preemptive hardening rather than reactive signature creation.
The most immediate and effective mitigation advised by researchers involves re-associating file handlers. By changing the default application for opening JScript (.js) files from the execution-oriented Windows Script Host (WScript.exe) to a benign text editor like Notepad, the entire execution chain is broken at the point of user interaction (e.g., if a user accidentally double-clicks the downloaded file). This moves the execution control from the malicious environment to a safe viewer.
Secondly, process control hardening is essential. Organizations should rigorously restrict the execution of scripting engines from non-standard locations. Specifically, blocking wscript.exe and cscript.exe from running content originating from user download directories (%TEMP%, %AppData%) unless explicitly sanctioned by application control policies, significantly reduces the blast radius should the initial file decompression succeed.
Finally, organizations must invest in behavioral analysis tools capable of monitoring the file system at a granular level—tracking the creation of LNK files in the Startup directory and monitoring the sequential spawning of powershell.exe from cscript.exe processes. This behavioral correlation, rather than reliance on file signature matching alone, offers the best defense against highly obfuscated, multi-stage initial access frameworks like the current iteration of Gootloader. The battle is shifting from what the file is, to what the file makes the system do.

