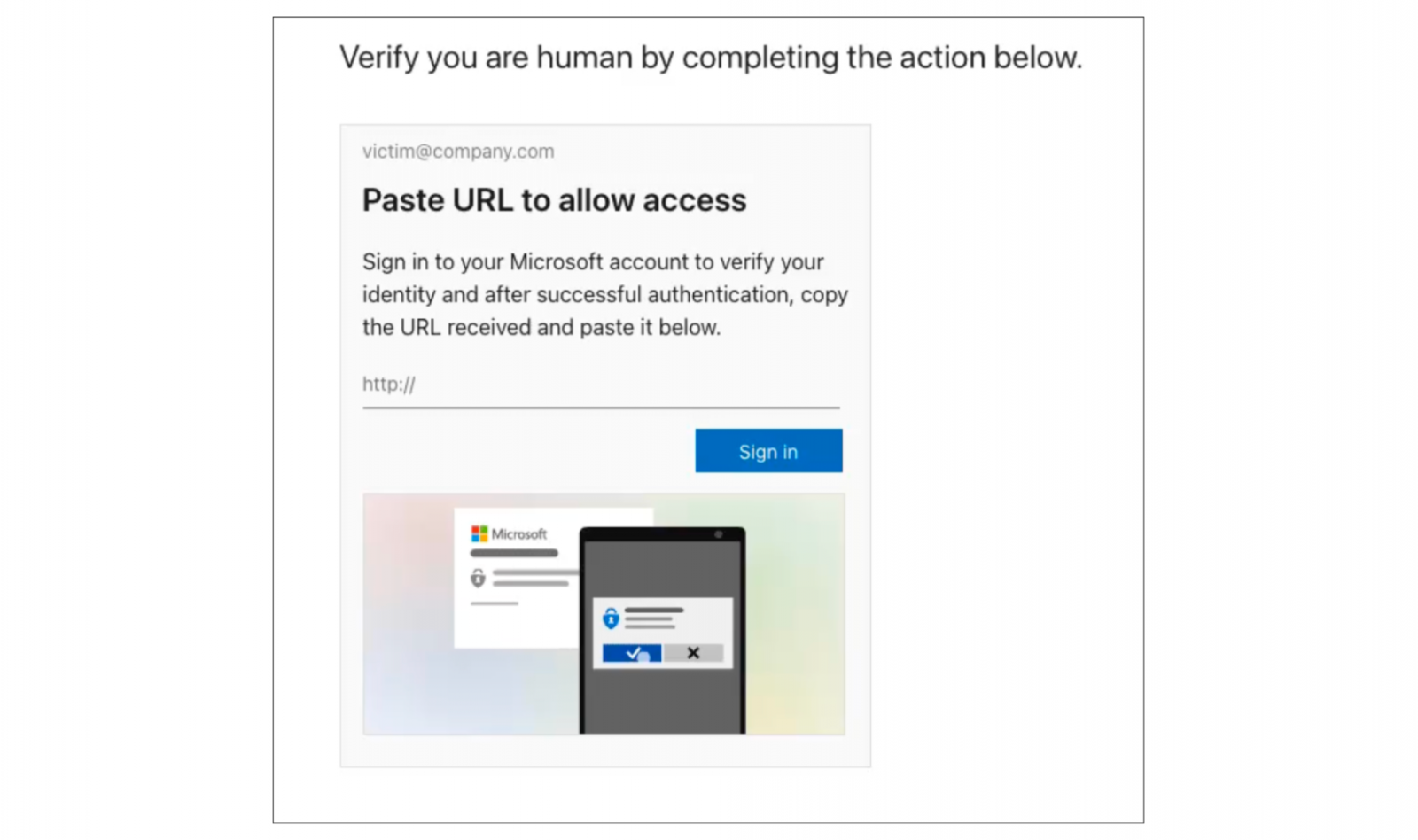
The cybersecurity landscape is perpetually reshaped by novel attack methodologies that exploit fundamental trust mechanisms in modern digital infrastructure. In December, security researchers at Push Security identified and successfully mitigated a sophisticated, previously unseen threat vector they designated as "ConsentFix." This technique represents a significant evolution in identity compromise, synergizing the user manipulation inherent in ClickFix-style social engineering with the granular access acquisition capabilities of OAuth consent phishing, specifically targeting Microsoft ecosystems. The campaign observed was extensive, deploying malicious payloads across a wide array of compromised web properties, indicating a broad, coordinated effort detected across numerous client environments.
The rapid dissemination and analysis of ConsentFix within the security community underscore its immediate relevance. Within days of its initial disclosure, independent researchers, including John Hammond, had already developed and demonstrated enhanced proof-of-concept versions, illustrating the technique’s inherent adaptability. Concurrently, analysis from major entities such as Microsoft and specialized security firms like Glueck Kanja provided crucial technical deep dives and mitigation strategies. This collective response highlights a critical juncture where the industry must rapidly adapt to attacks that bypass traditional authentication layers. This debrief aims to synthesize these community insights, provide an expert analysis of the technique’s inherent dangers, detail the observed campaign structure, and project its future implications for enterprise security architecture.
The Mechanics of Identity Bypass: ConsentFix 101
At its core, ConsentFix is engineered to subvert the standard OAuth 2.0 authorization flow. The objective is not to steal a static password or a one-time MFA code, but to trick a user into handing over a temporary, highly valuable OAuth authorization code directly to an adversary via a custom phishing interface. The attacker then leverages this code on their own machine to finalize the authorization handshake with the legitimate identity provider (e.g., Microsoft Entra ID), effectively gaining access to the targeted application or service under the victim’s identity.
The profound danger of this approach lies in its evasion of established identity-layer defenses. Passwords, even those protected by strong Multi-Factor Authentication (MFA), become irrelevant because the attack bypasses the initial authentication step entirely. Furthermore, phishing-resistant methods like FIDO2 security keys or passkeys, which are designed to prevent credential theft, offer no protection against ConsentFix, as the user is not entering secrets but rather participating in a flawed, coerced authorization exchange.
While OAuth abuse is not new—techniques such as standard consent phishing (tricking users into granting broad permissions to a malicious application) and device code phishing (leveraging the device_code flow) have been known for some time—ConsentFix introduces a critical procedural difference. Older consent phishing models typically focused on registering a persistent, fraudulent application within the tenant, which is increasingly difficult in modern cloud environments like Azure due to stricter default configurations governing user consent for application registration. Device code phishing, famously implicated in high-profile breaches like the 2025 Salesforce incidents, still requires the victim to input a short code into an attacker-controlled application interface. ConsentFix streamlines this by automating the capture of the authorization code itself, derived from a legitimate Microsoft redirection step.

The Novelty of the Threat: Why ConsentFix Escalates Risk
The danger inherent in ConsentFix stems from its deviation in target application selection and its manipulation of the local host redirection mechanism. Traditionally, consent phishing targets the initial registration of a third-party application. ConsentFix, however, specifically targets authorization flows for first-party Microsoft applications or command-line tools that rely on this specific localhost callback mechanism for local authentication—most notably, the Azure Command Line Interface (Azure CLI).
When an attacker targets the Azure CLI flow, they are not merely requesting access to email or calendar data; they are seeking access to the foundational management plane of the victim’s cloud environment. The implications are severe:
- Bypassing Standard OAuth Controls: Because the attack leverages the inherent functionality of established Microsoft applications (like Azure CLI) rather than registering a novel malicious application, many standard security controls designed to flag suspicious application registrations fail to trigger.
- Logging Deficiencies: Organizations often lack comprehensive, real-time logging specifically monitoring the exchange of authorization codes derived from localhost callbacks, leaving a critical detection gap. If the activity is not logged, it cannot be audited or analyzed retrospectively.
- Conditional Access Complications: A particularly insidious aspect is the exploitation of Conditional Access (CA) policy exclusions. Certain applications or requested scopes within Microsoft’s ecosystem may have pre-existing CA bypasses or configurations that permit access under specific, often benign-seeming, circumstances. ConsentFix exploits these established pathways to complete the handshake without triggering standard MFA challenges or location-based restrictions.
The attacker’s goal is to manually complete the authorization flow that normally occurs silently when a user runs az login or a similar command locally. By intercepting the authorization code generated via the http://localhost:<port> redirect, the attacker obtains the necessary artifact to exchange for session tokens (access or refresh tokens) for the targeted Azure CLI application on their own infrastructure. This grants them programmatic, persistent access to manage the victim’s cloud resources.
Campaign Execution and Attribution Insights
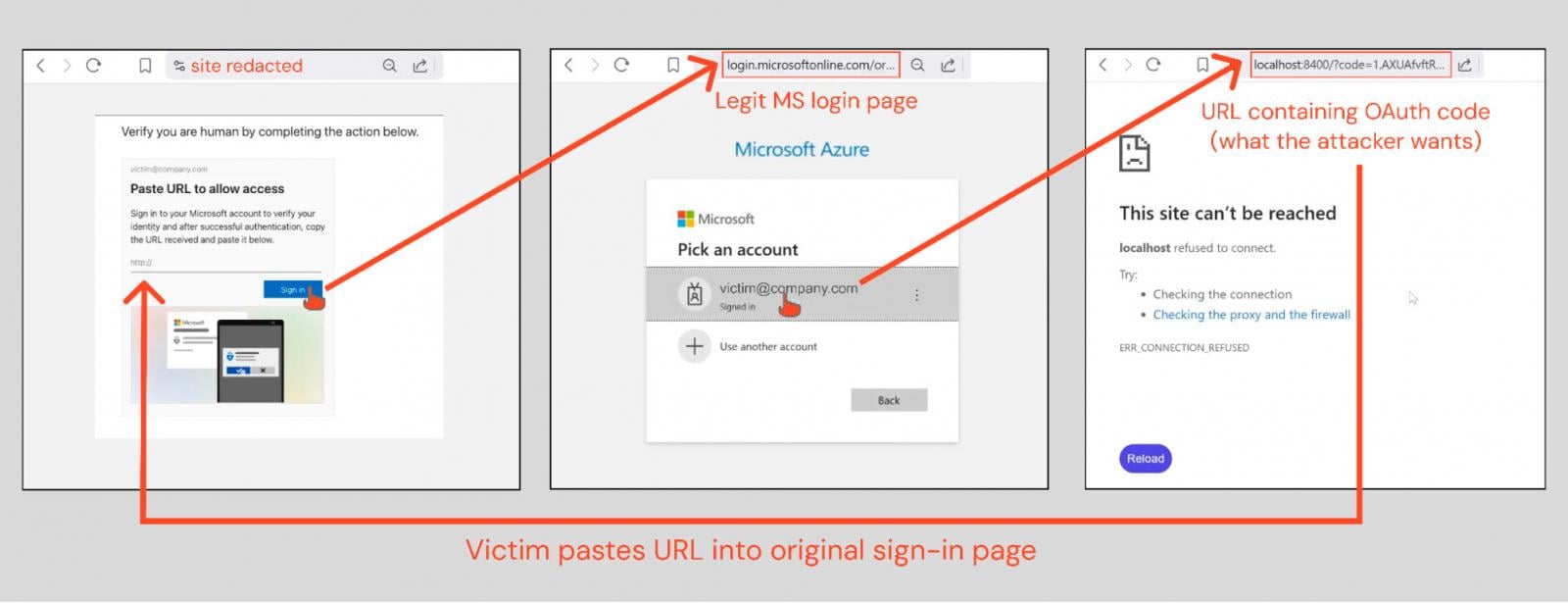
The initial ConsentFix campaign observed by Push Security was characterized by its use of compromised websites to host the malicious phishing lure. The user journey was deceptively simple, blending social engineering with technical steps:
- The Lure: The victim lands on a compromised site presenting a plausible scenario—often framed as a mandatory "human verification" step or a required "session refresh."
- The Redirect: The user clicks a link (often labeled "Sign In"), which initiates the legitimate Microsoft authentication portal. If the user is already authenticated in their browser session, this step is frictionless, pre-populating their credentials.
- The Code Generation: Upon successful (though coerced) selection of their account, the browser is redirected to a
localhostURL, which contains the critical OAuth authorization code embedded in the URI parameters. - The Capture: The user is then socially engineered to copy this entire
localhostURL and paste it into the original attacker-controlled phishing page. - Token Acquisition: The attacker receives the authorization code and immediately exchanges it server-side for long-lived access and refresh tokens associated with the targeted application (e.g., Azure CLI).
Subsequent tracking and collaboration with peer researchers suggest a potentially high-level threat actor behind the most recent large-scale deployment. Evidence points toward linkages with the Russian state-affiliated Advanced Persistent Threat group APT29. This attribution is supported by the attack’s sophisticated stealth tactics, which surpass the typical detection evasion seen in commodity criminal phishing operations. The methodology appears to be a highly refined evolution of previous manual social engineering efforts, such as those documented by Volexity, where victims were previously instructed to email the localhost response back to the attacker—a process ConsentFix automates and streamlines significantly.
Community Validation and Rapid Iteration
The security community’s swift engagement with ConsentFix provided invaluable, rapid validation and enhancement of the technique. This iterative development cycle illustrates the dual-edged sword of publicly known vulnerabilities: while disclosure aids defense, it simultaneously accelerates offensive refinement.
John Hammond’s immediate demonstration showcased a "V2.0" iteration that significantly improved the user experience for the victim. Hammond’s implementation used a pop-up browser window to generate the authorization code URL, which could then be seamlessly drag-and-dropped onto the phishing page. This increased smoothness drastically lowers the cognitive friction required for a victim to complete the malicious action, suggesting that future criminal variants will adopt similar low-friction interfaces.
Furthermore, researchers like Fabian Bader and Dirk-jan Mollema from Glueck Kanja cataloged an expanded list of vulnerable first-party applications. Their research identified a total of 11 applications susceptible to ConsentFix that also possess documented Conditional Access exclusions. This list effectively maps out the broader attack surface beyond just Azure CLI, indicating that the scope of potential compromise across an organization’s SaaS footprint is wider than initially assumed. These exclusions, often put in place for legacy integration or specific administrative functions, become direct vectors for identity takeover when paired with a ConsentFix payload.
Industry Implications and Future Trajectories
The emergence of ConsentFix signals a definitive shift in the threat landscape: attacks are moving further away from credential harvesting and toward direct token acquisition via protocol manipulation. For security architects, this means reliance on traditional perimeter defenses or even standard endpoint security solutions (like EDRs that do not possess deep browser telemetry) is becoming insufficient.
The speed of adaptation seen in the security community—both in identifying the flaw and in rapidly improving the attack—guarantees that ConsentFix, or highly similar protocols, will soon be standard issue in the toolkits of sophisticated criminal syndicates and nation-state actors alike. We anticipate imminent zero-day variants that may target different OAuth flows or leverage newer application registration types to maintain stealth.
The critical industry takeaway is the necessity of monitoring the browser context as a primary security surface, analogous to how EDR monitors the endpoint operating system. Attacks occurring entirely within the browser sandbox—like AiTM phishing, session hijacking, and ConsentFix—demand behavioral analysis of user interactions and page execution, not merely checking IP addresses or known malicious URLs (Indicators of Compromise, or IoCs).
Updated Mitigation Strategies for Security Teams
Addressing ConsentFix requires a multi-layered approach that acknowledges its browser-native nature and its exploitation of default configurations:
1. Enhancing Microsoft Logging and Monitoring:
Organizations heavily invested in Microsoft security stacks must move beyond baseline logging for OAuth events. Specific attention should be paid to:
- Audit Sign-in Logs: Scrutinize logs for successful authentication events that are immediately followed by high-privilege application grants, especially when associated with applications that might typically require local client interaction (like CLI tools).
- Conditional Access Insights: Regularly review CA policies, specifically identifying any application or scope-level exclusions. If an application like Azure CLI has an exclusion, ensure that access to that application is gated by other, non-bypassable controls, such as requiring compliant devices or specific network locations for management tasks.
- Application Consent Monitoring: While ConsentFix exploits flows that may bypass registration controls, monitoring for the granting of specific, high-risk API permissions (like Graph API
Directory.ReadWrite.All) remains crucial, even if the mechanism is non-standard.
2. Browser Telemetry and Behavioral Detection:
The most effective defense against zero-day browser attacks is behavioral monitoring. Security solutions must analyze the entire lifecycle of a web session: the loading of the page, the execution of scripts, and the sequence of user inputs. For ConsentFix specifically, detection logic should look for sequences involving:
- Initiation of a legitimate OAuth flow (Microsoft login screen).
- Redirection to a
localhostURI containing an authorization code parameter. - Subsequent submission of that code/URL back to the initial, external, non-Microsoft domain.
This end-to-end process monitoring allows for the blocking of the transaction in real-time, regardless of whether the specific phishing site is known.
3. Proactive Hardening:
Beyond reactive defense, organizations must proactively assess their identity attack surface:
- Reviewing Application Permissions: Conduct quarterly audits of all registered applications and the permissions they hold, strictly enforcing the principle of least privilege.
- MFA Enforcement Gaps: Use identity governance tools to map out all SSO coverage gaps and MFA exemptions, as ConsentFix thrives where standard authentication layers are weak or absent.
The community has already contributed valuable tools, including specialized Elastic detection rules designed to profile ConsentFix activity, providing immediate actionable intelligence for detection engineering teams.
Conclusion: The New Frontier of Identity Protection
ConsentFix is a potent reminder that securing modern identity is not just about fortifying credentials; it is about securing the protocols that use those credentials. By cleverly weaving together social engineering with the functional requirements of local command-line authentication, attackers have created a powerful bypass for widely deployed security measures. The rapid community response—leading to technical improvements and broader scope identification—demonstrates the resilience of the security ecosystem, but it also serves as a stark warning: these novel techniques are being iterated upon at machine speed. Organizations must pivot their defenses to focus on granular, behavioral detection within the browser context to successfully neutralize threats that, by design, seek to operate invisibly to legacy tooling.