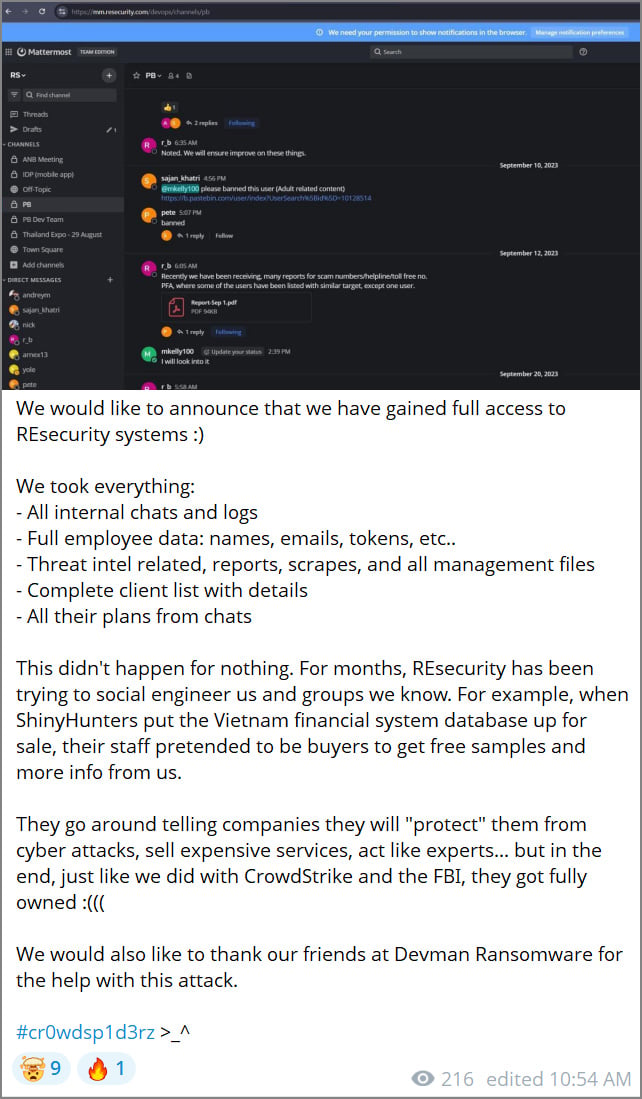
The digital security landscape is perpetually defined by an arms race between defenders and threat actors. This dynamic recently played out in a high-stakes confrontation involving the cybersecurity intelligence firm Resecurity and a group claiming affiliation with prominent ransomware and cybercrime syndicates. Threat actors operating under the banner of the "Scattered Lapsus$ Hunters" (SLH) publicly boasted of achieving a significant breach against Resecurity, claiming exfiltration of sensitive internal documents, proprietary threat intelligence reports, and comprehensive client data. The group disseminated purported evidence of their success via the Telegram messaging platform, including screenshots allegedly showing internal communications logs.
However, Resecurity has vehemently countered these claims, asserting that the entire engagement was a meticulously constructed cyber deception operation. According to the firm, the compromised systems were not part of their operational production environment but rather a highly specialized, isolated honeypot, specifically engineered to lure, monitor, and gather actionable intelligence on the specific adversaries involved. This incident underscores a critical evolution in defensive cybersecurity strategies: the proactive weaponization of deception technology to turn an apparent attack into an intelligence windfall.
The initial assertion from the SLH group, which attempts to draw lineage from notorious entities like Lapsus$ and Scattered Spider, framed the alleged infiltration as an act of digital retribution. They alleged that Resecurity personnel had engaged in social engineering tactics, masquerading as prospective buyers during an attempted illicit sale of a database purportedly belonging to a Vietnamese financial institution. The attackers claimed this pretense was an attempt by Resecurity to extract operational details about the threat group, prompting the retaliatory data theft.

Further complicating the narrative was an initial association with the ShinyHunters group. However, a subsequent clarification indicated that a spokesperson for ShinyHunters disavowed involvement in this specific action, despite historical ties to the SLH moniker. This internal fracturing or strategic distancing among threat collectives highlights the fluid and often opaque nature of underground cyber alliances.
The Architecture of Deception: Understanding the Honeypot Strategy
Resecurity’s response pivots entirely on the deployment of advanced deception technology. A honeypot, in cybersecurity parlance, is not merely a decoy server; it is a sophisticated, monitored resource intentionally exposed to attract malicious actors. Its primary function is to waste the attacker’s time, reveal their methodologies, and collect forensic data without placing genuine organizational assets at risk.
Resecurity’s Digital Forensics and Incident Response (DFIR) team initiated counter-intelligence measures after initially detecting probing activity against their publicly accessible systems on November 21st. The firm meticulously tracked reconnaissance indicators, logging multiple associated IP addresses, some originating from known VPN services like Mullvad and others geographically linked to Egypt. This early detection allowed the defenders sufficient lead time to construct the trap.
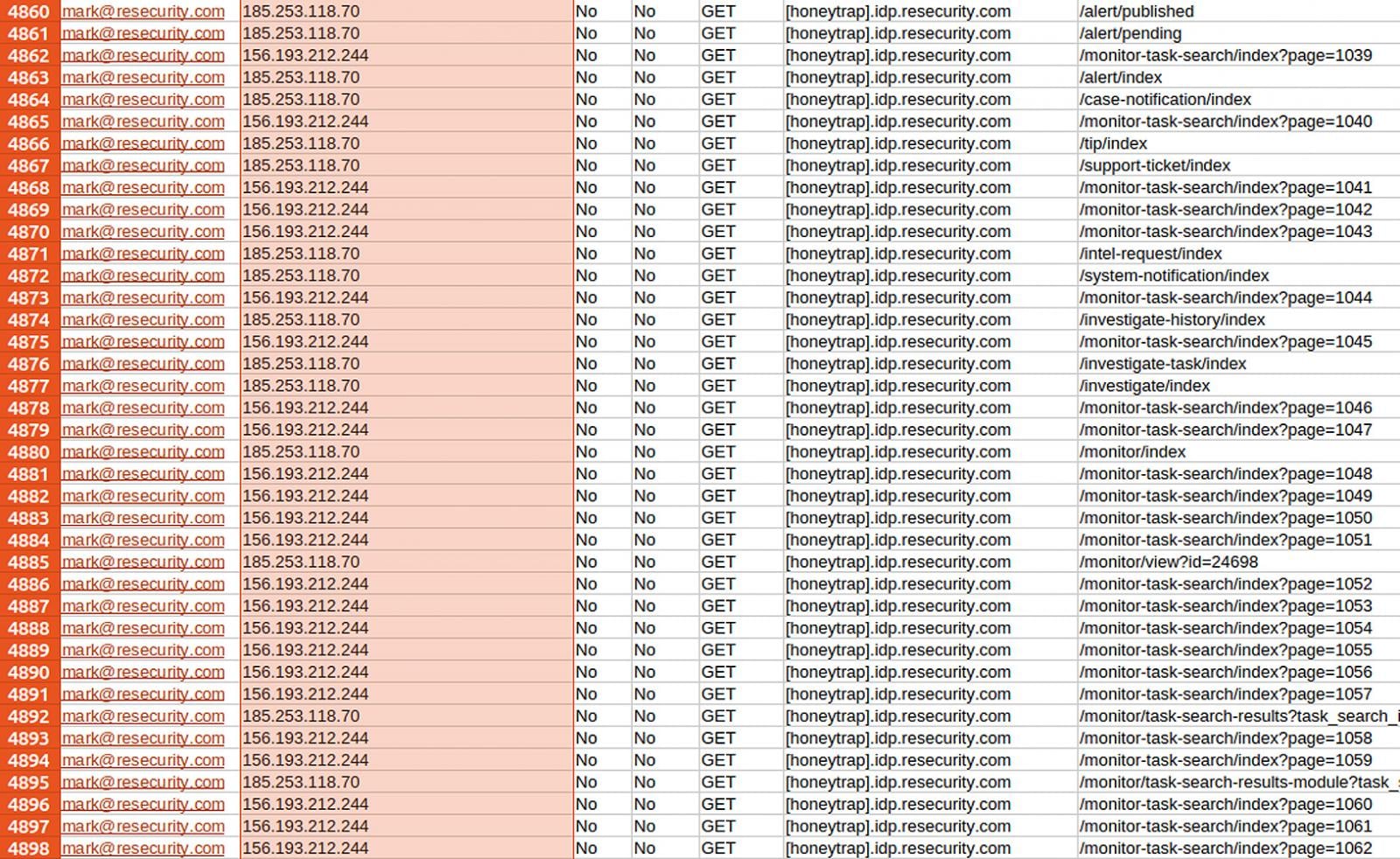
The critical step involved deploying a specialized honeypot account within a strictly isolated environment. This environment was populated with synthetic datasets designed to possess a high degree of verisimilitude to real-world operational data. Resecurity detailed that this synthetic trove included over 28,000 fabricated consumer records and more than 190,000 simulated payment transaction records, deliberately structured using the format of the Stripe official API to enhance perceived authenticity.

From mid-December through Christmas Eve, the monitoring team observed aggressive data exfiltration attempts by the threat actor. The researchers logged over 188,000 requests as the attacker attempted to automate the extraction of this fabricated intelligence, relying heavily on large pools of residential proxy IP addresses—a common tactic used to obscure origin. Throughout this intensive activity, Resecurity captured invaluable telemetry detailing the threat actor’s Tactics, Techniques, and Procedures (TTPs), infrastructure utilization, and operational security (OPSEC) posture.
Operational Security Failures and Intelligence Yield
The true success of the honeypot, according to Resecurity, lay in the subsequent OPSEC failures exhibited by the threat actor under the pressure of automated exfiltration. The firm states that the attacker inadvertently exposed confirmed, non-proxied IP addresses on several occasions due to proxy connection instability. This crucial intelligence—the actor’s real digital fingerprint—was immediately relayed to partner law enforcement agencies.
Furthermore, Resecurity leveraged the attacker’s continued engagement by introducing additional layers of synthetic data. This escalation tested the boundaries of the attacker’s persistence and methodology, leading to further operational slips that helped researchers narrow down the command-and-control (C2) infrastructure, including identifying servers utilized to manage the residential proxy botnet. The culmination of this intelligence gathering led to a subpoena request initiated by a foreign law enforcement partner, based on the forensic evidence collected.
The threat actors, however, remain unbowed, interpreting Resecurity’s disclosure as a weak attempt at damage control. Their latest public communication challenged the firm’s narrative, promising further evidence soon. This response confirms that while the data stolen was worthless, the tactical engagement itself continues to fuel a psychological battle in the information space.
Industry Implications: The Maturation of Deception Technology
This incident transcends a simple security spat; it offers a tangible case study on the increasing sophistication and efficacy of proactive cyber deception. For years, honeypots were often viewed as static, low-interaction lures. Modern deployments, as exemplified by Resecurity, represent high-interaction, dynamic environments that mimic production systems with alarming accuracy.
The industry implication here is profound. When a threat actor claims a major win against a security vendor and the vendor reveals the entire environment was a controlled simulation, it forces a re-evaluation of threat intelligence credibility. It suggests that security firms are moving beyond purely reactive defense to actively shaping the threat landscape in their favor.
Expert Analysis: Security architects specializing in threat intelligence note that the value derived from this honeypot far outweighs the initial cost of deployment. Instead of relying solely on Indicators of Compromise (IOCs) derived from past attacks, Resecurity has gained Indicators of Attack (IOAs) specific to the methods currently favored by this particular threat group. This intelligence is highly personalized and directly applicable to hardening their actual client environments against these precise TTPs. Furthermore, the successful attribution efforts, facilitated by the attacker’s OPSEC mistakes under surveillance, demonstrate the convergence of technical forensics and international legal recourse, a necessary development in combating sophisticated transnational cybercrime.
The use of synthetic data, modeled after real-world standards like the Stripe API, is particularly noteworthy. It moves beyond simple dummy files to create an environment that satisfies the technical requirements of an automated exfiltration tool, thereby ensuring the attacker spends maximum time interacting with the decoy system, believing they are achieving a meaningful objective.
Future Impact: Adversarial Engagement as a Service
The future impact of such deployments points toward the standardization of "Adversarial Engagement as a Service" or active deception platforms. Organizations will increasingly invest in comprehensive deception layers not just to detect intrusion, but to actively profile threat actors targeting their sector.
- Deep Profiling Over Surface Detection: The focus shifts from merely stopping the attack to deeply understanding the attacker’s toolset, command structure, and financial motivations. This intelligence informs predictive defense models better than generalized threat feeds.
- Legal and Attribution Pathways: As demonstrated, successful honeypots that lead to verifiable IP addresses provide a stronger evidentiary foundation for international law enforcement actions, potentially leading to disruption rather than mere remediation.
- The Deception Arms Race: Threat actors will inevitably adapt. We can anticipate increased sophistication in attacker reconnaissance designed to "fingerprint" decoys—checking for unusual monitoring artifacts or synthetic data irregularities. This necessitates continuous evolution in deception engineering to maintain the illusion.
The narrative war following such an event is also a significant trend. The SLH group’s immediate reaction—dismissing the honeypot revelation as "damage control"—is a classic information operation tactic intended to salvage credibility within their peer ecosystem. For Resecurity, the challenge lies in presenting the collected intelligence transparently enough to validate their counter-narrative without exposing the proprietary mechanics of their deception architecture to future attackers.
In conclusion, the confrontation with the Scattered Lapsus$ Hunters serves as a powerful illustration of the maturation of defensive security postures. By accepting the initial intrusion into a controlled environment, Resecurity transformed an alleged data breach into a highly valuable intelligence operation, reaffirming that in the modern cyber domain, the ability to control the narrative of engagement is often as critical as the ability to block initial access. The data stolen was valueless; the information gleaned about the adversary’s TTPs is priceless.