The global automotive technology landscape faced a significant security reckoning this week as the Pwn2Own Automotive 2026 competition commenced in Tokyo, Japan, coinciding with the Automotive World conference. The opening day alone saw security researchers demonstrate a staggering 37 previously unknown (zero-day) vulnerabilities across critical vehicle components, culminating in a substantial payout of $516,500 for the initial successful exploits. This intense scrutiny underscores the escalating risk profile associated with the interconnected, software-defined vehicles dominating modern transportation infrastructure.
The most high-profile success of the day involved the infiltration of a Tesla vehicle’s Infotainment System. The Synacktiv Team achieved root permissions on this system via a USB-based attack vector. Their exploit chain was a sophisticated combination of an information leak vulnerability married to an out-of-bounds write flaw. This level of access grants an attacker deep control over the user-facing, and often network-connected, core of the vehicle’s digital experience. Furthermore, the same team secured an additional $20,000 by successfully chaining three distinct vulnerabilities to achieve root-level code execution on an aftermarket Sony XAV-9500ES digital media receiver, illustrating that vulnerabilities extend beyond OEM-specific hardware into the broader aftermarket ecosystem that consumers often integrate.
The severity of the findings stems from the context of the competition itself. Pwn2Own Automotive, orchestrated by Trend Micro’s Zero Day Initiative (ZDI), deliberately targets fully patched systems—meaning these vulnerabilities were present even on the latest, purportedly secure software builds available to consumers. The event, running from January 21st to 23rd, focuses laser-like attention on In-Vehicle Infotainment (IVI) systems, Electric Vehicle (EV) charging infrastructure, and foundational operating systems such as Automotive Grade Linux (AGL).
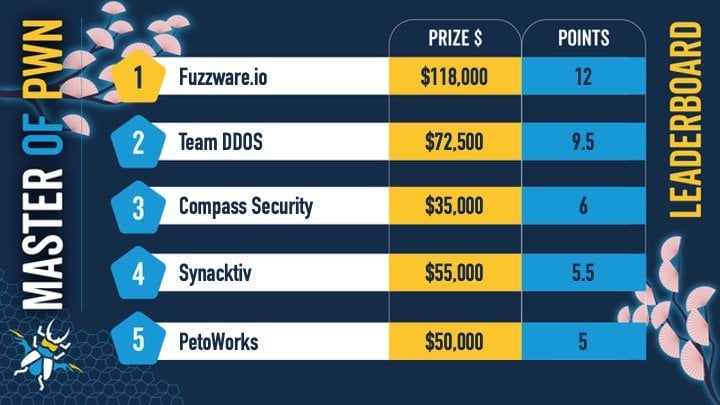
Beyond the high-profile Tesla breach, the charging ecosystem proved a fertile ground for exploitation. Teams Fuzzware.io demonstrated significant prowess by netting $118,000 through successful hacks targeting three distinct pieces of infrastructure: an Alpitronic HYC50 Charging Station, an Autel charger, and a Kenwood DNR1007XR navigation receiver. This highlights a critical, often overlooked, security perimeter: the charging network, which acts as a crucial nexus point between the vehicle and external networks.

PetoWorks contributed $50,000 to the day’s total earnings by successfully chaining three zero-day bugs to establish root privileges on a Phoenix Contact CHARX SEC-3150 charging controller. Gaining root access on charging hardware carries severe implications, potentially allowing malicious actors to manipulate charging speeds, disrupt grid interactions, or even introduce malware into the communication protocols used between vehicles and charging stations.
Team DDOS also made a substantial impact, banking $72,500 by compromising three different EV charging stations: the ChargePoint Home Flex, the Autel MaxiCharger, and the Grizzl-E Smart 40A vehicle charging station. The sheer diversity of compromised charging hardware suggests systemic security deficits across manufacturers and product tiers, from residential units to public fast chargers.
The intensity is set to continue into the subsequent days of the competition. The leaderboard for Day 2 shows aggressive targeting, indicating researcher confidence in finding further exploitable flaws. For instance, the Grizzl-E Smart 40A is slated for attack by four separate teams, each vying for a $50,000 prize per successful root attempt. Similarly, the Autel MaxiCharger faces three separate attempts, and two teams are lined up to tackle the ChargePoint Home Flex, with each success yielding $50,000. Team Fuzzware.io is also slated to attempt a $70,000 challenge against the Phoenix Contact CHARX SEC-3150 vehicle charger.
Industry Implications: The Software-Defined Vehicle Security Crisis
The results from Day 1 of Pwn2Own Automotive 2026 are more than just a measure of researcher skill; they are a stark diagnostic of the automotive industry’s current security posture. The transition to Software-Defined Vehicles (SDVs) has introduced unprecedented complexity. Modern vehicles are essentially rolling data centers, relying on dozens of Electronic Control Units (ECUs) communicating over high-speed networks like CAN bus and Ethernet, often layered with complex, Linux-based operating systems.
The successful compromise of the Tesla Infotainment System, specifically targeting the USB interface, demonstrates that the initial points of user interaction remain alarmingly vulnerable. While root access on an IVI system might not immediately translate to control over safety-critical functions like braking or steering (which are typically segmented onto isolated domains), it provides a powerful beachhead. From the IVI, an attacker can potentially pivot to other vehicle networks, intercept sensitive user data, or use the system to facilitate over-the-air (OTA) updates with malicious code if proper segmentation and validation mechanisms fail.

The repeated targeting of EV charging hardware points to a systemic failure in securing the auxiliary infrastructure that supports the EV revolution. As EVs become ubiquitous, the charging network transforms into critical national infrastructure. Vulnerabilities here allow for supply chain disruption, energy grid manipulation, or large-scale data exfiltration from fleets of connected vehicles. The fact that multiple, established charging brands were successfully targeted reinforces the need for rigorous, standardized security protocols across the entire EV charging supply chain, not just within the vehicle itself.
Expert Analysis: Chaining Vulnerabilities and the Cost of Complexity
From a cybersecurity perspective, the success of chaining vulnerabilities—as seen with Synacktiv’s exploit—is the hallmark of sophisticated attack methodologies. A single bug might be patched, but when an information leak is combined with an out-of-bounds write, the path to system compromise becomes exponentially easier for an attacker. This technique exploits the inherent complexity and poor boundary checks in large, integrated software stacks.
Automotive software development often relies on integrating third-party components, legacy code, and diverse operating systems (like AGL or proprietary Linux variants). Each integration point, each library dependency, represents a potential gap. The researchers are effectively demonstrating that current security validation processes—both internal QA and external penetration testing—are failing to detect these complex, multi-stage exploit paths before products hit the market.
The financial incentives driving this research are also significant. The substantial cash awards—totaling over half a million dollars on Day 1—signal to the security community that manufacturers are willing to pay premium prices for validated, high-impact vulnerabilities. This continuous flow of funding ensures that top-tier talent remains focused on automotive targets.
Future Impact and Evolving Trends
The immediate impact of Pwn2Own Automotive 2026 is the 90-day window granted to vendors. During this period, manufacturers must race to develop, test, and deploy patches for the 37 newly discovered flaws before Trend Micro’s ZDI releases the details publicly. A rapid response is crucial to prevent these zero-days from falling into the hands of malicious actors who lack the ethical constraints of the contest participants.
Looking ahead, several trends will define the next phase of automotive security challenges:
-
AI Integration and Attack Surface Expansion: As manufacturers integrate advanced driver-assistance systems (ADAS) and future autonomous capabilities relying heavily on machine learning models, the attack surface will expand to include the integrity of the AI models themselves. Exploiting model drift, data poisoning, or manipulating sensor fusion layers presents a new, potentially catastrophic, category of automotive vulnerability that future Pwn2Own events will likely explore.
-
OTA Security Resilience: The reliance on OTA updates for patching, while necessary, creates a single point of failure. If an attacker compromises the OTA infrastructure—as demonstrated by previous Pwn2Owns targeting related systems—they gain the capability to deploy malicious firmware globally across an entire fleet instantaneously. Future contests will likely focus on deep-dive compromises of secure boot chains and update signing mechanisms.
-
Standardization Pressure: The consistent exposure of vulnerabilities across different manufacturers (Tesla, Autel, Phoenix Contact) will inevitably increase regulatory pressure for standardized security benchmarks across the entire automotive supply chain, moving beyond voluntary disclosure and bug bounty programs toward mandatory, auditable security standards for all connected components, from the main vehicle computer down to the home charger.
The results from the first day of Pwn2Own Automotive 2026 serve as a critical, high-stakes stress test. While the researchers are rewarded for finding flaws, the industry is left with the urgent, expensive mandate of hardening systems that are no longer merely mechanical devices, but complex, interconnected digital platforms responsible for human lives and critical energy infrastructure. The cumulative cash awards paid out over the three days of this competition will ultimately reflect the true cost of securing the next generation of transportation.

