The digital ecosystem experienced a notable, albeit localized, disruption as Logitech’s critical utility software for macOS, namely Options+ and G HUB, abruptly ceased functionality following the expiration of their embedded code-signing certificates. This failure cascaded across Apple hardware, instantly rendering sophisticated input devices—ranging from productivity-focused mice to high-performance gaming peripherals—incapable of utilizing their advanced, customized features. For a significant segment of the user base, this was not a minor inconvenience but a sudden regression to baseline functionality, stripping away meticulously configured ergonomic shortcuts, specialized macros, and precise peripheral behaviors.
Logitech Options+, the software suite designed to unlock the granular customization capabilities of their productivity hardware, and G HUB, the dedicated platform for tuning Logitech G series gaming gear, are central to the user experience for millions. These applications facilitate deep-level configuration, allowing users to tailor button assignments, define complex application-specific profiles, fine-tune DPI and sensor sensitivity, and manage intricate RGB lighting schemes. When the underlying trust mechanism—the digital certificate used by Apple’s operating system to verify the authenticity and integrity of the application—lapsed, macOS security protocols automatically blocked execution, preventing the applications from launching or causing them to enter endless loading loops.
Reports began surfacing across technical forums and social media platforms, painting a picture of widespread user confusion and mounting frustration. Users attempting to launch Options+ or G HUB found the applications either spinning indefinitely or failing to initialize entirely. This meant that customized scroll wheel behaviors, gesture controls on trackpads, and complex macros essential for professional workflows or competitive gaming suddenly reverted to factory defaults or became entirely inaccessible. The immediate impact was a tangible loss of productivity and a perceived degradation in the value proposition of the hardware itself.

The user response highlighted the deep dependency professionals and enthusiasts place on these software layers. Users reported time wasted attempting traditional troubleshooting steps—reinstalling the applications, navigating macOS Safe Mode, and manually deleting preference files in a desperate attempt to force a refresh of the application state. This level of troubleshooting often risks data loss, particularly when dealing with configuration profiles that are not consistently backed up externally. The sudden imposition of this issue underscored a fundamental vulnerability in relying on third-party vendor support for core operational continuity.
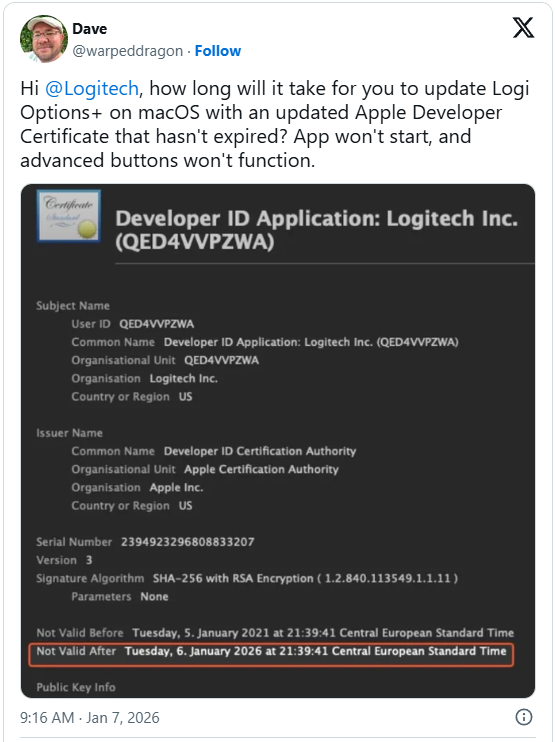
Logitech eventually acknowledged the widespread outage via its official support channels, confirming the root cause was indeed the expiration of the necessary digital certificate. In a statement published on their support portal, the company confirmed that "Logitech Options+ and G HUB are currently not working on macOS due to an expired certificate required for the apps to run." While this admission provided clarity, the initial lack of an immediate fix amplified user anxiety. The company indicated they were working on delivering a resolution, promising a new installer package. Crucially, they assured users that this update would deploy without requiring a version number bump and, more importantly, would preserve all existing user profiles and customization settings—a vital detail for users who would otherwise face hours of reconfiguration. However, the absence of a concrete timeline for the release of this emergency patch left the user base in limbo.
The Critical Role of Code Signing in Modern Operating Systems
To understand the severity of this incident, one must appreciate the function of code-signing certificates within the macOS security architecture. Modern operating systems, especially those designed by Apple, operate under a principle of least privilege and strict verification. Applications distributed outside the Mac App Store must be cryptographically signed by the developer using a trusted certificate issued by a recognized Certificate Authority (CA).
This signature serves two primary functions: Authentication and Integrity. Authentication verifies that the software genuinely originates from the claimed developer (Logitech, in this case). Integrity ensures that the code has not been tampered with or maliciously altered since it was signed. When macOS checks this certificate and finds it expired, the operating system interprets this as a failure in one of these two core security premises. It cannot definitively prove the software’s provenance or guarantee its current state, leading to the default action: blocking execution. This is an intentional design choice by Apple to safeguard users from potentially compromised or unauthorized software running on their systems.

For peripheral drivers and configuration utilities like Options+ and G HUB, which often require deep access to system-level input events and hardware interfaces (sometimes necessitating kernel extensions or low-level accessibility permissions), this security gate is particularly stringent. The expiration of the certificate effectively transformed powerful customization tools into untrusted binaries overnight.
Industry Implications: Supply Chain and Operational Risk
This incident serves as a potent case study highlighting latent risks within the software supply chain, particularly concerning maintenance and lifecycle management of digital assets. For a company the size of Logitech, the oversight of a single cryptographic key expiry represents a significant lapse in operational discipline.
From an industry perspective, this scenario raises several crucial points:
- Certificate Management as a Security Priority: In an era where security is paramount, certificate expiry is not merely an administrative oversight; it is a security incident. Organizations must implement robust, automated monitoring and rotation schedules for all critical signing certificates. The failure here suggests a breakdown in proactive certificate lifecycle management.
- Dependency on Proprietary Software: While hardware innovation continues, the functionality of modern peripherals is increasingly abstracted behind proprietary software layers. When these software layers fail due to external dependencies (like a CA certificate), the entire hardware ecosystem is paralyzed. This emphasizes the need for contingency plans, perhaps including basic, non-expiring drivers for core functionality.
- User Trust and Brand Perception: For Logitech, a company whose brand equity is built on reliability and quality, this event damages user trust. Users who invest in premium hardware expect consistent performance. When that performance is instantly revoked due to an internal administrative failure, it prompts users to question the vendor’s diligence across the entire product stack.
The temporary workarounds proposed by the community—such as manually rolling back the system clock to a time before the certificate expired—are inherently risky. Tampering with the system date can cause cascading issues with other time-sensitive services, secure connections (HTTPS), and scheduled tasks. Furthermore, attempting to run older, potentially unpatched versions of the software introduces a different vector for security vulnerabilities that the vendor might have already fixed in newer builds.
Expert Analysis: The Cost of Neglected Maintenance
Security engineers often point out that digital infrastructure requires continuous maintenance, not just initial deployment. The cost of implementing a resilient certificate management system—including automated alerts, escrow management for private keys, and defined renewal workflows—is dwarfed by the cost of downtime, customer support strain, and reputation damage incurred when such a certificate lapses.
In complex environments like macOS, where security policies are continuously tightened by Apple, third-party developers must stay meticulously current. A certificate expiry suggests a failure to adhere to best practices, possibly relying on manual checks rather than automated DevOps pipelines designed to manage these critical security components. The fact that the fix involved pushing a new installer without a version bump suggests the underlying code was largely sound, but the packaging metadata was critically flawed. This points to a process failure rather than a complex engineering bug.
Future Impact and Mitigation Strategies
The aftermath of this incident will likely influence how users interact with and deploy peripheral management software moving forward. For the immediate term, users are left balancing the inconvenience of default settings against the risk of applying unofficial fixes.
Looking ahead, the industry trend leans towards tighter integration with operating system security features, making these certificate-based failures more likely if maintenance slips. For peripheral manufacturers, this event necessitates a review of their cross-platform deployment strategies:
- Prioritizing Native macOS Integration: While G HUB and Options+ are powerful, exploring deeper integration with macOS native features, such as Accessibility settings or Keyboard Shortcuts management that bypass the need for constant, intrusive self-verification checks, could provide a more resilient baseline experience.
- Enhanced Communication Protocols: When failures occur, the response needs to be swift and multifaceted. Logitech’s eventual support page update was necessary, but pre-emptive notifications pushed through update channels or even system alerts (if permitted by the OS) could drastically reduce user panic and support load.
- Auditing Legacy Support: The continued reliance on certificate-based authentication for software that has existed for several years highlights the challenge of maintaining security standards across evolving operating system security paradigms. Regular, mandated audits of signing certificates for all persistent applications are becoming essential components of a mature software maintenance schedule.
Ultimately, the failure of Logitech’s macOS utilities due to an expired certificate underscores a persistent reality in the technology sector: the most sophisticated hardware is only as reliable as its least maintained piece of supporting software. As users continue to rely on these configuration layers to optimize their digital tools, vendors must elevate certificate lifecycle management from a routine administrative task to a mission-critical security function. The temporary disabling of customized input methods serves as a stark reminder that trust in the digital realm is granted through timely, verifiable credentials, and failure to renew those credentials carries immediate and tangible consequences for end-users. The extended period of uncertainty following the initial outage suggests that while the fix was simple in concept, the process of deploying it securely across a broad user base without data loss required careful, deliberate steps that could not be rushed.

