A sophisticated, albeit low-profile, threat actor identified as Zestix is actively monetizing corporate breaches by advertising access to sensitive data pilfered from compromised self-hosted or managed file-sharing platforms, namely ShareFile, Nextcloud, and OwnCloud instances. This activity, detailed in recent analysis by the cybercrime intelligence firm Hudson Rock, illustrates a critical vulnerability point in modern enterprise infrastructure: the weak link between endpoint security and cloud access control. Zestix is functioning effectively as an Initial Access Broker (IAB), packaging and selling these digital entry points on various underground forums, signaling a mature, transactional approach to cybercrime targeting specific, high-value cloud deployments.
The infiltration vector detailed in the intelligence report points toward a pervasive threat already resident within corporate networks: information-stealing malware. Specifically, credential harvesting tools such as RedLine, Lumma, and Vidar are implicated in the initial compromise of employee workstations. These stealthy applications are adept at exfiltrating stored credentials, session cookies, personal identifiable information (PII), and sensitive financial data directly from web browsers, messaging applications, and cryptocurrency wallets. The typical distribution pathway for these infostealers often involves the murky realm of malvertising campaigns or socially engineered "ClickFix" attacks, designed to trick end-users into executing malicious payloads disguised as legitimate software updates or fixes.
The crucial nexus point for Zestix’s operation, however, is the subsequent exploitation of these stolen credentials. When valid login details—username and password—are acquired from an infected endpoint, the threat actor uses them to gain unauthorized entry into organizational cloud storage environments. This entire operation hinges on a fundamental security gap: the absence or failure of Multi-Factor Authentication (MFA) on these critical file-sharing services. Without this essential layer of defense, compromised credentials grant attackers the keys to the kingdom, allowing them to bypass perimeter defenses entirely and move directly to data exfiltration.

Hudson Rock’s investigation uncovered a deeply concerning pattern regarding credential hygiene. In numerous analyzed instances, the stolen credentials sold by Zestix had remained viable and active within criminal databases for years. This suggests a systemic failure within targeted organizations to enforce robust credential rotation policies or, critically, to invalidate active sessions promptly following a known or suspected security incident involving an endpoint. Such prolonged validity dramatically increases the dwell time available for threat actors to leverage their access for reconnaissance and large-scale data theft.
Sector-Wide Exposure and the Breadth of Stolen Assets
The scope of Zestix’s advertised illicit trade is alarmingly broad, spanning dozens of organizations across sectors vital to national and economic security. Industries identified as targets include aviation, defense contracting, healthcare, critical utilities (power and water), mass transit systems, telecommunications, legal services, real estate, and various governmental bodies. This diversification suggests Zestix is not focused on a single vertical but rather exploiting any organization utilizing these specific file-sharing platforms without adequate security layering.
The methodology employed by Zestix involves methodical parsing of the logs generated by the aforementioned infostealers. By specifically filtering logs for URLs associated with ShareFile, Nextcloud, and OwnCloud, the actor identifies compromised credentials tied directly to corporate cloud resources. They then attempt authentication on the target services. If MFA is absent, access is secured. Hudson Rock employed sophisticated correlation techniques, cross-referencing this illicit market data with open-source intelligence, metadata, and public images to pinpoint the probable points of entry, lending significant credence to their findings in at least 15 verified cases where infostealer data directly mapped to cloud service credentials.
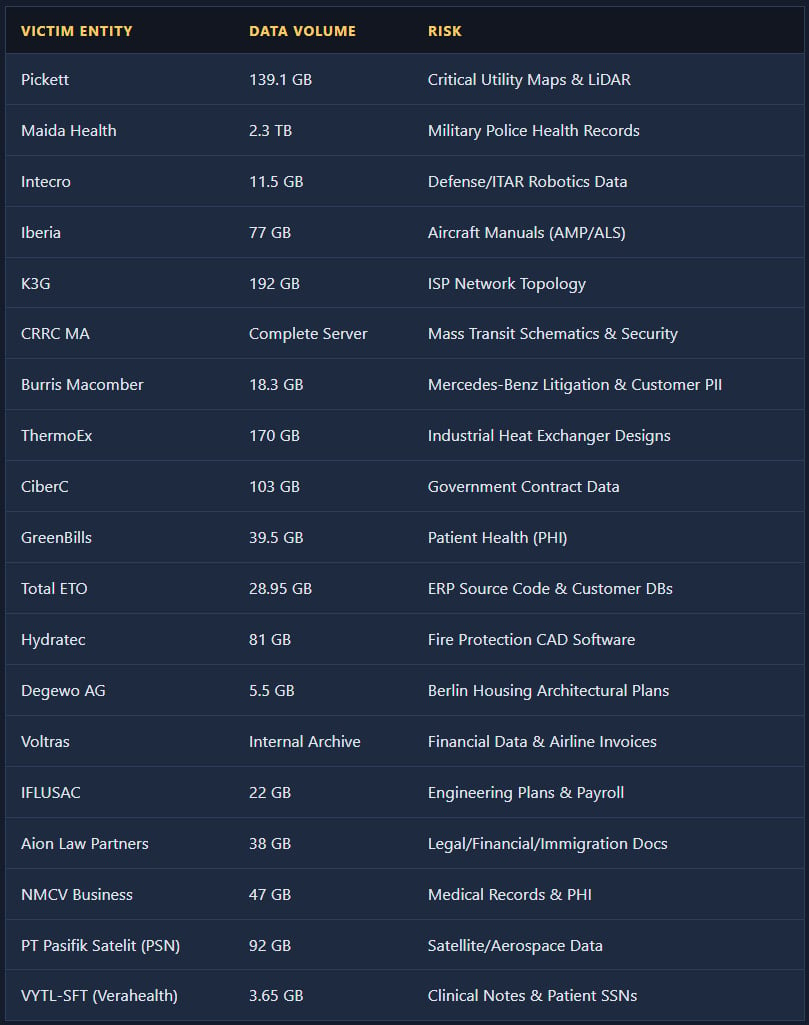
The nature of the data offered for sale underscores the severity of these breaches. Zestix is advertising data caches ranging from tens of gigabytes up to multiple terabytes, promising access to information that could cause catastrophic damage if exposed. The claimed contents include highly sensitive intellectual property (IP) and operational data: aircraft maintenance manuals and fleet specifics, proprietary defense and engineering schematics, extensive customer databases, protected health information (PHI), mass-transit infrastructure layouts, utility LiDAR mapping data, Internet Service Provider (ISP) network configurations, sensitive satellite project documentation, proprietary Enterprise Resource Planning (ERP) source code, government contracts, and confidential legal filings.

The implication of this data loss extends beyond mere financial penalties associated with data breaches. The exposure of defense and aerospace schematics, for instance, presents tangible industrial espionage risks, potentially compromising supply chains. Similarly, exposed government contracts raise direct national security concerns, as foreign adversaries could gain insight into government priorities, procurement strategies, and operational dependencies.
Furthermore, Hudson Rock has identified evidence of Zestix operating under an alternate alias, "Sentap," which is allegedly peddling access to an additional 30 victims. While the intelligence regarding this secondary set has not undergone the same rigorous, multi-vector validation process as the Zestix listings, it suggests a potentially wider network of compromised organizations or an effort to diversify sales channels and obscure the actor’s true reach.
The Systemic Failure: Endpoint Security as the Gateway
The core revelation from this intelligence is that the threat actor is capitalizing not on novel zero-day exploits against the cloud platforms themselves, but on the systemic failure to secure the user endpoint and enforce robust authentication protocols. The success of RedLine, Lumma, and Vidar is predicated on an environment where security awareness is low, and MFA adoption is inconsistent.
This phenomenon is not isolated to the specific victims Zestix is currently marketing. Hudson Rock’s broader threat intelligence sweep indicates that cloud exposure resulting from endpoint compromise is a widespread, systemic vulnerability affecting thousands of corporate systems globally. The firm reports identifying thousands of infected machines across major global entities, including known exposures at firms like Deloitte, KPMG, Samsung, Honeywell, and Walmart. While these specific organizations may not be directly linked to the current Zestix sales, their compromised endpoints represent a vast, readily available pool of credentials that could fuel future IAB operations.
Industry Implications and Expert Analysis
From an expert perspective, this pattern highlights the diminishing efficacy of relying solely on perimeter defenses or traditional network security tools when the endpoint itself is compromised. The modern enterprise security posture must shift to a "Zero Trust" architecture that inherently assumes breach.
For Cloud Providers (ShareFile, Nextcloud, OwnCloud): While the immediate responsibility for access control lies with the implementing organization, these providers face reputational risk. Their platforms, when configured by customers, must strongly default to or mandate MFA. If the default installation settings lack robust security baselines, they contribute indirectly to the attack surface. Proactive communication and security hardening advisories, especially regarding credential leakage risks, are paramount. Hudson Rock’s reported intent to notify the platform vendors is a necessary step to prompt platform-level warnings or security updates.
For Enterprise Security Leaders: The key takeaway is the critical need for aggressive MFA enforcement across all remote access points, especially for platforms hosting sensitive data, regardless of whether they are proprietary or open-source deployments. Furthermore, security operations centers (SOCs) must enhance detection capabilities for the early stages of this kill chain: recognizing the activity patterns of infostealers on endpoints and rapidly invalidating compromised credentials across all connected services immediately upon detection. The years-long persistence of some stolen credentials underscores a major gap in automated session revocation processes.
For the Cybercrime Economy: Zestix represents the maturation of the IAB model. Previously, hackers might sell network access or RDP credentials. Now, the commodity is highly specific, authenticated access to cloud resources. This is more valuable because it bypasses initial network traversal steps and lands the buyer directly at the data repository, significantly speeding up the monetization process. The diverse and high-value nature of the advertised data (IP, PHI, defense secrets) pushes the price point significantly higher than simple credit card dumps.
Future Trajectory and Mitigation Strategies
The future impact of this trend suggests that as organizations increasingly move critical data off-premise or into managed cloud environments, the credential exfiltration pipeline fueled by endpoint malware will remain a primary vector for sophisticated actors. The rise of remote and hybrid work environments has exponentially increased the number of potential endpoint compromises, making the "trusted" employee device the weakest link.
Mitigation must be multi-layered and aggressively enforced:
- Universal MFA Implementation: This is non-negotiable for all organizational cloud services, prioritizing phishing-resistant MFA methods (like FIDO2 security keys) over less secure SMS-based tokens, as even MFA tokens can sometimes be bypassed through session hijacking or social engineering if the initial credential theft is successful.
- Endpoint Detection and Response (EDR) Excellence: EDR solutions must be tuned not just to catch malware execution but to detect the behavior associated with credential harvesting—attempts to read browser memory, access specific configuration files, or connect to known command-and-control servers associated with RedLine or Lumma.
- Privileged Access Management (PAM) and Least Privilege: Access to file-sharing platforms should be time-bound and strictly limited to the minimum required scope. If an employee’s workstation is compromised, the blast radius should be contained by ensuring their cloud session expires quickly or requires re-authentication for accessing high-risk directories.
- Continuous Credential Auditing: Organizations must adopt tools that can scan for, flag, and automatically force resets on credentials known to be exposed in public breaches or, as in this case, observed being actively traded on underground markets.
The intelligence regarding thousands of infected machines at major corporations confirms that this is not a niche problem but a pervasive security hygiene failure. The Zestix operation serves as a stark, public demonstration of how readily available endpoint compromise tools can be weaponized against poorly secured, yet critical, corporate cloud infrastructure, turning mundane stolen passwords into high-stakes national security liabilities.

