The burgeoning ecosystem surrounding AI-enhanced Integrated Development Environments (IDEs), particularly those built upon the open-source foundation of Microsoft’s Visual Studio Code (VSCode), is facing a critical, yet subtle, supply chain vulnerability. Solutions such as Cursor, Windsurf, Google Antigravity, and Trae, which integrate sophisticated artificial intelligence capabilities directly into the coding workflow, have inadvertently created an exploitable gap by retaining outdated extension recommendation logic inherited from their upstream source. This oversight allows threat actors to potentially hijack developer trust by registering namespaces for extensions that exist in the official Microsoft Visual Studio Marketplace but are absent from the alternative, open-source registry utilized by these forks: OpenVSX.
The architectural divergence necessitating this reliance on OpenVSX is rooted in licensing constraints. While these AI-centric IDEs leverage the robust VSCode core, they cannot seamlessly integrate with the proprietary Visual Studio Marketplace due to licensing agreements tied to Microsoft’s commercial distribution terms. Consequently, developers of these derivative environments have adopted OpenVSX as the default repository for extensions. However, the transition is incomplete. The core issue arises because the derivative IDEs often hardcode lists of "recommended" extensions within their configuration files. These internal pointers frequently point directly to the original Microsoft Marketplace identifiers, creating a critical mismatch when the IDE queries the local OpenVSX instance.
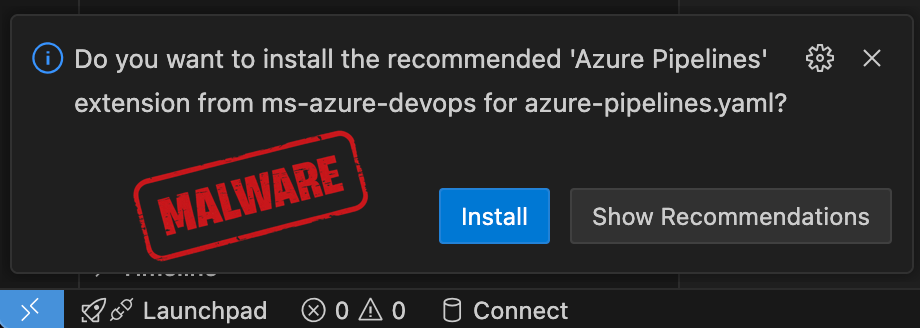
This hardcoded inheritance manifests in two primary modes, both designed to enhance developer productivity by proactively suggesting necessary tooling. The first is context-aware, file-based recommendation. For instance, if a developer opens a configuration file like azure-pipelines.yaml, the IDE is programmed to suggest the official Azure Pipelines extension. The second is system-aware, software-based suggestion. If the IDE detects the presence of software like PostgreSQL on the developer’s machine, it triggers a prompt to install a corresponding PostgreSQL extension. In a properly configured environment relying solely on OpenVSX, these recommendations would resolve to existing packages within that repository.
The vulnerability exploited here hinges on the "unclaimed namespace" phenomenon. When the IDE attempts to locate a recommended extension—say, publisher.extension-name—in the OpenVSX registry, it finds the namespace for that publisher does not exist. This situation presents an open invitation for malicious actors. By registering the previously unowned publisher namespace on OpenVSX, a threat actor gains the ability to publish an extension under that trusted name.

Security researchers from the supply-chain security firm Koi recently brought this sophisticated attack vector to light. Their analysis underscores the danger: developers inherently trust prompts originating from their primary development environment, especially when those prompts relate to widely used, established tools. A developer, seeing a recommendation for the "Azure Pipelines Extension" pop up within their trusted AI-IDE, is highly likely to click "Install" without cross-referencing the source registry. If the namespace has been successfully squatting, the installed extension will not be the legitimate tool, but rather a malware-laden package designed to compromise the developer’s environment, steal credentials, or inject malicious code into the ongoing software development lifecycle (SDLC). This essentially transforms a productivity feature into a high-leverage supply chain infiltration mechanism.
The ramifications of this discovery extend far beyond individual developer workstations; they challenge the security posture of entire organizations building on these popular AI coding assistants. If a compromised extension makes its way into enterprise source code repositories, the impact could be systemic, leading to the compromise of production environments or the exfiltration of proprietary intellectual property.
Following the disclosure of their findings in late November 2025, Koi researchers initiated contact with the affected vendors: Google, Windsurf, and Cursor. The response timeline highlights disparate levels of urgency within the ecosystem. Google demonstrated proactive remediation, swiftly removing 13 specific extension recommendations from its IDE configuration by December 26th. However, at the time of this analysis, Cursor and Windsurf had yet to issue public responses or implement patches, leaving their user bases potentially exposed to this namespace squatting attack vector.
Recognizing the immediate danger posed by the lack of vendor response, the Koi team took the decisive, albeit temporary, measure of performing "defensive squatting." They proactively claimed the namespaces for the most egregious offenders within the OpenVSX registry. This move was not intended to offer functionality, but rather to act as a critical block. By publishing non-functional placeholder extensions under the legitimate names, they effectively neutralized the ability of malicious actors to register and upload malware under those specific, highly desirable aliases. This crucial intervention buys time for the respective IDE vendors to properly resolve the underlying configuration issue—removing the pointers to the non-existent OpenVSX entries altogether or ensuring they point only to verified, official OpenVSX publishers.
Furthermore, the security researchers collaborated with the Eclipse Foundation, the steward of the OpenVSX marketplace. This partnership is vital for implementing systemic defenses. Coordination efforts focus on auditing all referenced namespaces within the ecosystem, rigorously verifying the provenance of extensions, removing any contributors who cannot be authenticated as official maintainers of the intended software, and deploying broader, registry-level safeguards against namespace squatting attempts moving forward.

It is important to note, based on current data, there is no evidence suggesting that threat actors had successfully weaponized this specific configuration vulnerability before the discovery and subsequent defensive action by the Koi team. However, the existence of the gap demonstrates a clear failure point in the derivative IDE development process: the incomplete synchronization between the upstream configuration blueprint (VSCode’s recommendations) and the downstream deployment environment (OpenVSX).
Industry Implications: Trust in the AI-Augmented Toolchain
This incident serves as a stark warning about the inherent security challenges introduced by forking established, widely-used software, especially when those forks integrate cutting-edge features like generative AI. The proliferation of VSCode-derived IDEs is a direct response to the demand for specialized, AI-native coding environments. These environments promise increased developer velocity by understanding code context, debugging suggestions, and generating boilerplate code based on deep analysis of the project structure. Yet, this velocity often comes at the expense of rigorous configuration auditing.
The core industry implication revolves around the concept of inherited trust. Developers trust Microsoft’s recommendations because they are vetted within the official ecosystem. When that trust mechanism is transferred wholesale to a third-party fork that uses a different marketplace backend (OpenVSX), the necessary vetting process is bypassed. For organizations relying on these AI IDEs for critical development work, this represents a significant blind spot in their Software Composition Analysis (SCA) tooling, which may not be configured to monitor third-party marketplace backends like OpenVSX with the same rigor applied to the primary Visual Studio Marketplace.
The response from the affected vendors will set a precedent for how the open-source community manages derivatives of major proprietary platforms. While Google’s swift action is commendable, the silence from Cursor and Windsurf raises concerns about resource allocation toward security hardening versus feature development in rapidly evolving AI tooling. For enterprises integrating these tools, dependency mapping must now explicitly include the configuration files of derivative IDEs to identify hardcoded marketplace references.
Expert-Level Analysis: The Mechanics of Namespace Hijacking
From a deep technical perspective, this vulnerability is an example of a classic dependency confusion attack, albeit one tailored specifically to marketplace metadata rather than package managers like npm or PyPI. The mechanism relies on the IDE’s internal logic preferring a locally sourced metadata pointer, even if that pointer resolves to an empty or unverified repository (OpenVSX in this case), over an external, potentially more reliable source if the local query fails or is misconfigured.
The dual recommendation system—file-based and software-based—amplifies the attack surface. File-based triggers are predictable, allowing an attacker to easily map which file types trigger which recommendations. Software-based triggers, while seemingly more complex, rely on the IDE performing local system enumeration (e.g., checking for installed binaries or environment variables). An attacker can simply ensure that the target system appears to have the required dependency installed, thereby triggering the malicious suggestion.
The "placeholder extension" defense employed by Koi is an elegant, if temporary, mitigation. It exploits the same trust mechanism: the IDE finds an extension under the claimed namespace and happily installs the dummy package, preventing a malicious payload from being deployed. However, this is a reactive measure. The long-term solution requires a fundamental shift in how these forks manage their extension discovery pipeline, potentially involving:
- Active Manifest Synchronization: Creating a continuous, verified sync mechanism between the official VSCode recommendation manifest and the OpenVSX manifest, flagging and removing entries that do not resolve correctly.
- Publisher Verification Layer: Implementing an explicit layer within the IDE that checks the publisher ID against a curated whitelist of verified publishers on OpenVSX, rather than blindly trusting the existence of the namespace.
- User Transparency: Enhancing the recommendation dialog to clearly state the source marketplace (e.g., "Recommended from OpenVSX") rather than implicitly suggesting the source is the same as the upstream default.
Future Impact and Trends: Securing the AI Development Environment
.jpg)
The trajectory of software development points toward even deeper integration of AI assistants directly into the IDE fabric. As IDEs become smarter, they will inevitably take on more automated configuration tasks, including dependency management and toolchain setup. This incident foreshadows future vulnerabilities where AI agents, acting on behalf of the developer, might automatically download and integrate components based on flawed or incomplete internal mappings.
We can anticipate a growing need for "Trust Anchors" within the developer toolchain. Just as certificate pinning is used for secure network communication, IDEs may need cryptographic verification layers for extension sources. The community surrounding OpenVSX and similar open-source marketplaces will need to mature their governance models rapidly to handle the influx of specialized, derivative clients demanding reliable, verifiable content.
Furthermore, this event underscores the critical importance of the Eclipse Foundation’s role in maintaining OpenVSX as a legitimate, secure alternative. If major players like Cursor and Windsurf continue to rely on it, the stability and security assurances provided by the foundation become paramount to enterprise adoption. A fragmented marketplace where trust is assumed rather than verified is an invitation for sustained adversarial activity. Developers and security teams must now treat any extension recommendation from a VSCode fork with the same initial skepticism applied to any unverified third-party binary, actively auditing the source registry before execution. The convenience of AI-driven tooling must never supersede fundamental security hygiene.

