The ongoing cat-and-mouse game between cyber threat actors and defensive security firms has taken a fascinating turn, centering on the cybersecurity intelligence provider Resecurity. The financially motivated hacking collective known as ShinyHunters has publicly asserted a significant data breach, claiming to have successfully exfiltrated sensitive internal assets from Resecurity’s network. These alleged spoils reportedly include proprietary threat intelligence reports, internal employee communications, comprehensive client registries, and private personnel data. In a bold move typical of modern digital brigandage, the group disseminated visual proof—screenshots ostensibly captured from Resecurity’s internal collaboration platforms—via a prominent messaging channel on Telegram.
The threat actors, who have recently styled themselves under the umbrella moniker "Scattered Lapsus$ Hunters," citing perceived operational overlap between themselves, the infamous Lapsus$ group, and Scattered Spider, framed the supposed infiltration as a retaliatory measure. They accused Resecurity personnel of engaging in deceptive social engineering tactics. Specifically, ShinyHunters alleged that Resecurity employees posed as prospective buyers during a supposed sale of a compromised Vietnamese financial system database, attempting to procure free data samples and extract operational intelligence on the hackers themselves.
However, Resecurity has vehemently refuted these claims of a successful production environment compromise. The firm counters that the data displayed by ShinyHunters originates exclusively from a sophisticated, purpose-built digital deception mechanism—a honeypot—meticulously engineered to lure, trap, and analyze adversaries targeting their infrastructure. This scenario underscores a critical evolution in cyber defense strategies: moving from purely reactive containment to proactive, intelligence-gathering entrapment.
The Architecture of Deception: Contextualizing the Honeypot Strategy
To fully appreciate the implications of this confrontation, one must understand the technical and strategic backdrop of cyber deception technology. A honeypot, in its essence, is a decoy system designed to mimic a high-value target, intentionally left vulnerable or accessible to draw in malicious actors away from genuine production assets. The primary objective shifts from preventing access (which is never guaranteed) to observing and recording the attacker’s methodology, tools, and ultimate objectives.

Resecurity detailed their response following the initial detection of adversarial probing. According to their timeline, their Digital Forensics and Incident Response (DFIR) team identified early indicators of reconnaissance activity on November 21, 2025, targeting publicly facing assets. The analysts quickly logged multiple Internet Protocol (IP) addresses associated with the probes, noting connections routing through known privacy services like Mullvad VPN, alongside geographically dispersed residential proxies, including several traced back to Egypt. This early identification allowed the firm to pivot rapidly into a controlled engagement posture.
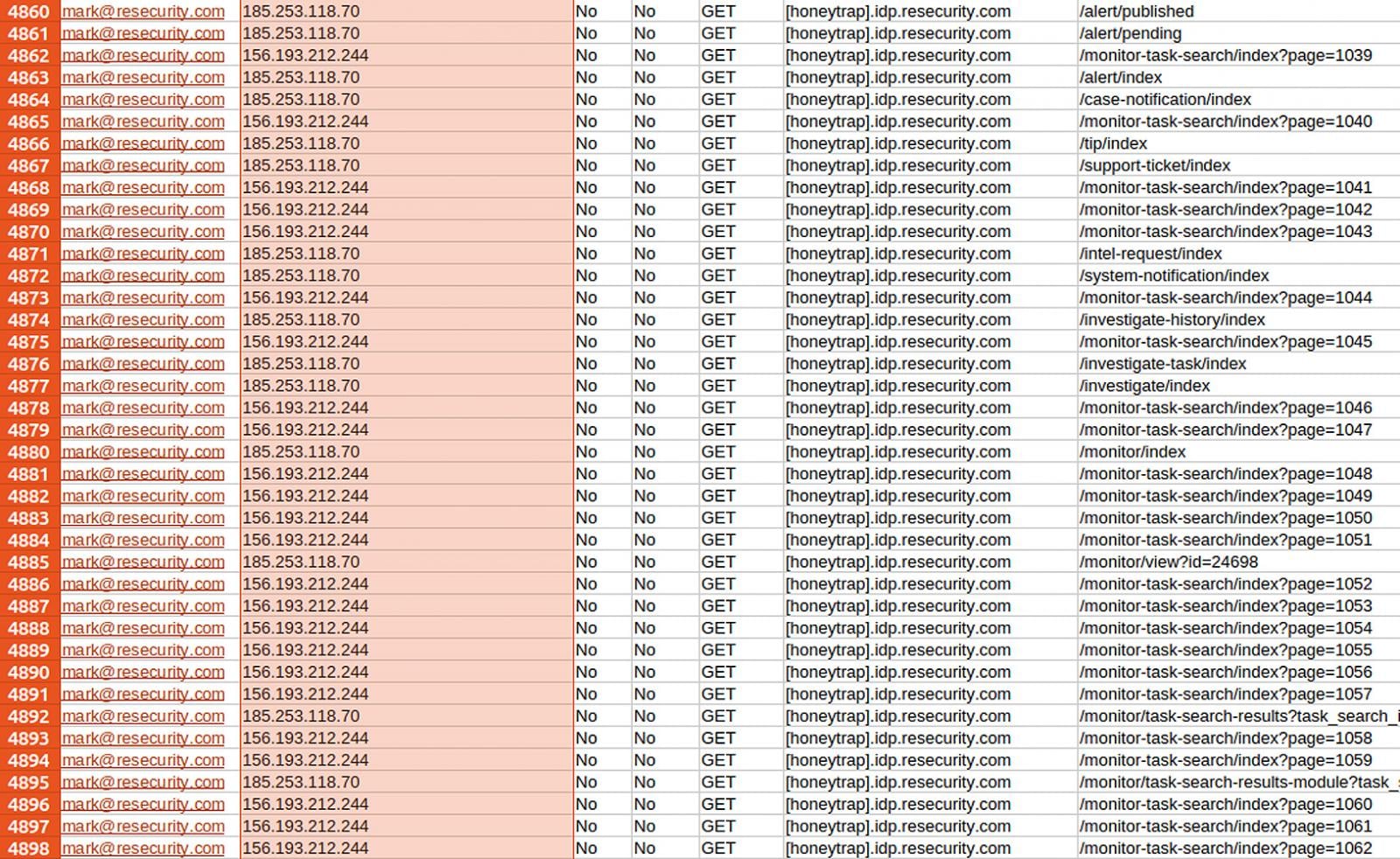
Instead of immediately blocking the identified entry points, Resecurity intentionally deployed a meticulously crafted "honeypot" account within an isolated segment of their network. This environment was populated with synthetic datasets—data that looked authentic but held no real-world value or sensitivity. The company leveraged its expertise to create highly realistic lures, including over 28,000 fabricated consumer records and more than 190,000 simulated payment transaction records, patterned precisely after the official API output formats of major payment processors like Stripe. This level of detail is crucial; sophisticated attackers perform rigorous validation checks, and superficial decoys are quickly abandoned.
Attacker Engagement and Intelligence Harvesting
The attacker, believing they had found a genuine weakness, began escalating their activities, particularly focusing on automated data exfiltration attempts throughout December. Resecurity’s monitoring revealed a sustained barrage of over 188,000 data requests between December 12th and December 24th, all executed through a complex chain of residential proxies.
This extended engagement provided Resecurity with an invaluable, real-time telemetry stream on the attacker’s Tactics, Techniques, and Procedures (TTPs). By observing how ShinyHunters navigated the simulated environment, which commands they executed, and how they attempted to package the stolen data, Resecurity gained actionable intelligence that can be directly integrated into threat detection models for their legitimate clients.
A significant breakthrough in the operation, according to Resecurity, occurred when the threat actor experienced operational security (OPSEC) failures. During these lapses, confirmed IP addresses were momentarily exposed when proxy connections failed. This intelligence was immediately cataloged and, critically, shared with international law enforcement partners. The firm further refined its trap by introducing additional synthetic datasets after observing the initial exfiltration patterns. This served a dual purpose: it kept the attacker engaged for longer while simultaneously triggering further OPSEC errors as the actor adapted to the "new" data landscape. These subsequent failures helped Resecurity narrow the physical and virtual infrastructure supporting the automated attack campaign, leading to the identification of specific servers used to manage the residential proxy network.

The intelligence gathered culminated in a formal request. Resecurity confirmed that, based on the network forensics and timestamps derived from the honeypot activity, a foreign law enforcement agency, acting as a partner to Resecurity, issued a subpoena targeting the identified threat actor infrastructure.
The Narrative War: Hype vs. Reality
The incident highlights a common dynamic in the cybersecurity landscape: the immediate, often sensationalized, claims made by threat actors versus the measured, often delayed, technical explanations provided by defenders. ShinyHunters’ immediate publication of screenshots—showing alleged internal Mattermost chats concerning malicious content on Pastebin—was designed for maximum impact and to cast doubt on Resecurity’s credibility. Their subsequent dismissal of Resecurity’s explanation as mere "damage control" is a predictable counter-maneuver intended to discredit the honeypot narrative before it can fully take hold.
However, the technical depth provided by Resecurity—detailing the precise date of initial detection (November 21, 2025), the specific volume of synthetic data deployed (28,000 records), and the subsequent collaboration with law enforcement—lends significant weight to their assertion. For security professionals, the key differentiator is the nature of the data involved. If ShinyHunters had successfully exfiltrated proprietary source code, unencrypted customer credentials, or genuine threat intelligence dossiers, the defensive posture would have been severely compromised. The fact that the disclosed data appears to be fabricated, following a clear timeline of monitored engagement, strongly supports the honeypot defense.
Industry Implications: The Value of Active Deception
This event serves as a potent case study illustrating the growing maturity and necessity of active defense measures, particularly deception technology. In an era where perimeter defenses are increasingly porous due to cloud sprawl and remote work, traditional "keep them out" strategies are insufficient. Modern security doctrine increasingly incorporates "detect and respond," and increasingly, "lure and learn."
For the cybersecurity intelligence sector, being the target of a high-profile threat group like ShinyHunters—even if contained—carries inherent reputational risk. Competitors and potential clients naturally scrutinize such incidents. Resecurity’s swift and detailed technical rebuttal, backed by forensic evidence of synthetic data deployment and intelligence sharing with judicial bodies, is a calculated move to reframe the narrative from victim to successful intelligence operator. They are signaling to the market that they possess the capability not just to defend themselves but to actively turn an attack into an intelligence windfall, effectively weaponizing the adversary’s efforts.
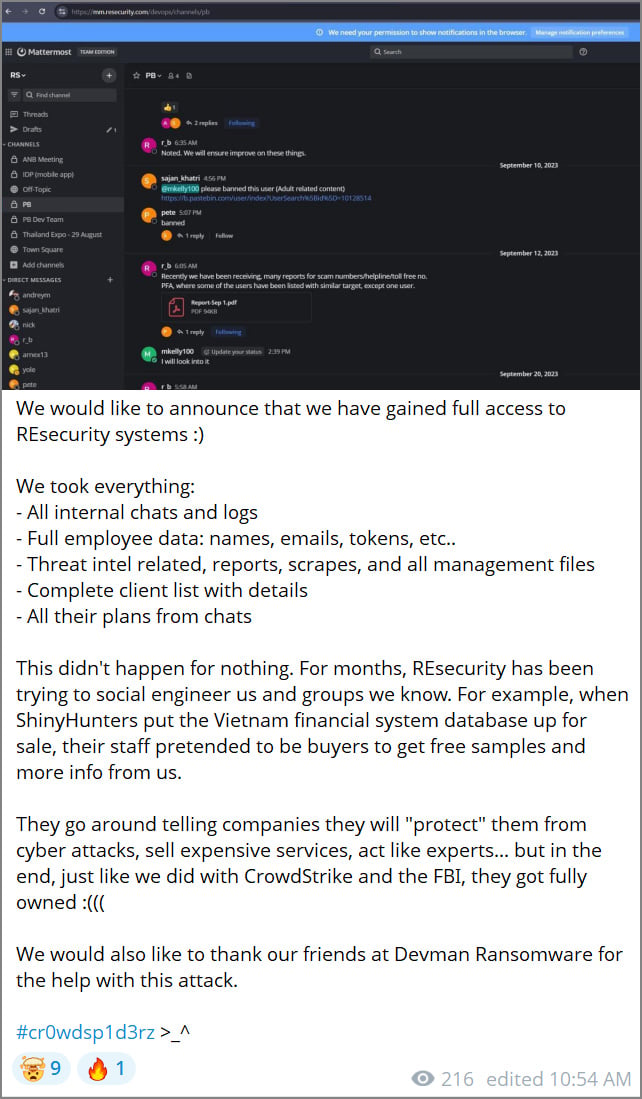
The sophistication of the honeypot deployment itself—mirroring real-world API formats and maintaining persistent monitoring across weeks of activity—sets a high bar for defensive engineering. It demonstrates that security firms are moving beyond simple network traps to creating highly interactive, data-rich environments that sustain the attacker’s interest long enough to yield meaningful intelligence regarding their infrastructure and command-and-control mechanisms.
Future Trends: The Escalation of Deception Warfare
The future of cyber defense will likely see a significant acceleration in the adoption of layered deception platforms. As threat actors become more adept at evading signature-based detection and standard behavioral analysis, the incentive to dedicate resources to baiting them increases. We can anticipate several trends emerging from incidents like this:
-
Hyper-Realistic Decoys: The quality of synthetic data will become paramount. Security vendors will invest heavily in generative AI models to create synthetic datasets—client manifests, code snippets, and internal memos—that are indistinguishable from reality, ensuring attackers commit maximum resources to the trap.
-
Automated Takedown Coordination: The seamless transition from honeypot observation to law enforcement action, as described by Resecurity, points toward formalized, pre-arranged intelligence-sharing protocols. Expect tighter integration between private sector DFIR teams and global law enforcement to expedite the attribution and disruption of threat actor infrastructure identified within these controlled environments.
-
The Attribution Challenge: While Resecurity claims success in identifying the threat actor’s infrastructure, the use of extensive residential proxy networks remains a formidable hurdle for definitive, public attribution. The ongoing "war of words" between ShinyHunters and Resecurity will likely continue, with the hackers attempting to leak more ambiguous proof to muddy the waters, while Resecurity relies on privileged, non-public intelligence shared with authorities.
Ultimately, this episode is less about a successful breach and more about a successful counter-intelligence operation. It underscores a shift in the cybersecurity arms race, where the most valuable commodity is no longer just preventing access, but controlling the attacker’s journey once they gain it, transforming a potential liability into a strategic intelligence asset. The community now awaits whether ShinyHunters can produce definitive evidence of genuine compromise, or if their boasted "full access" will remain confined to the digital playground Resecurity built for them.