The persistent exploitation of a critical vulnerability within the widely deployed WinRAR archiving utility underscores a persistent weakness in the software supply chain, providing a reliable initial access vector for a broad spectrum of malicious actors. Identified under the designation CVE-2025-8088, this high-severity security defect represents a sophisticated path traversal vulnerability that cunningly utilizes the NTFS Alternate Data Stream (ADS) feature to bypass standard security controls and write arbitrary files to sensitive system locations. The continued active exploitation, noted by global threat intelligence groups, highlights the significant operational risk posed by unpatched legacy software, even when patches have been made available.
This particular vulnerability exploits a fundamental mechanism within Windows—Alternate Data Streams—which allows data to be appended to existing files without altering the primary file content, often remaining invisible to standard file enumeration tools. In the context of WinRAR archives, attackers have weaponized this feature to embed malicious payloads within the metadata or associated streams of seemingly innocuous files, such as decoy PDF documents or spreadsheets contained within a compressed archive. When a victim extracts or opens the compromised archive, the flaw permits WinRAR to traverse directory structures beyond the intended extraction path, enabling the placement of executable code or configuration files directly into critical directories, most notably the Windows Startup folder. Placement in this folder guarantees persistence; the malware automatically executes upon the next system reboot, establishing a foothold independent of user interaction after the initial compromise.
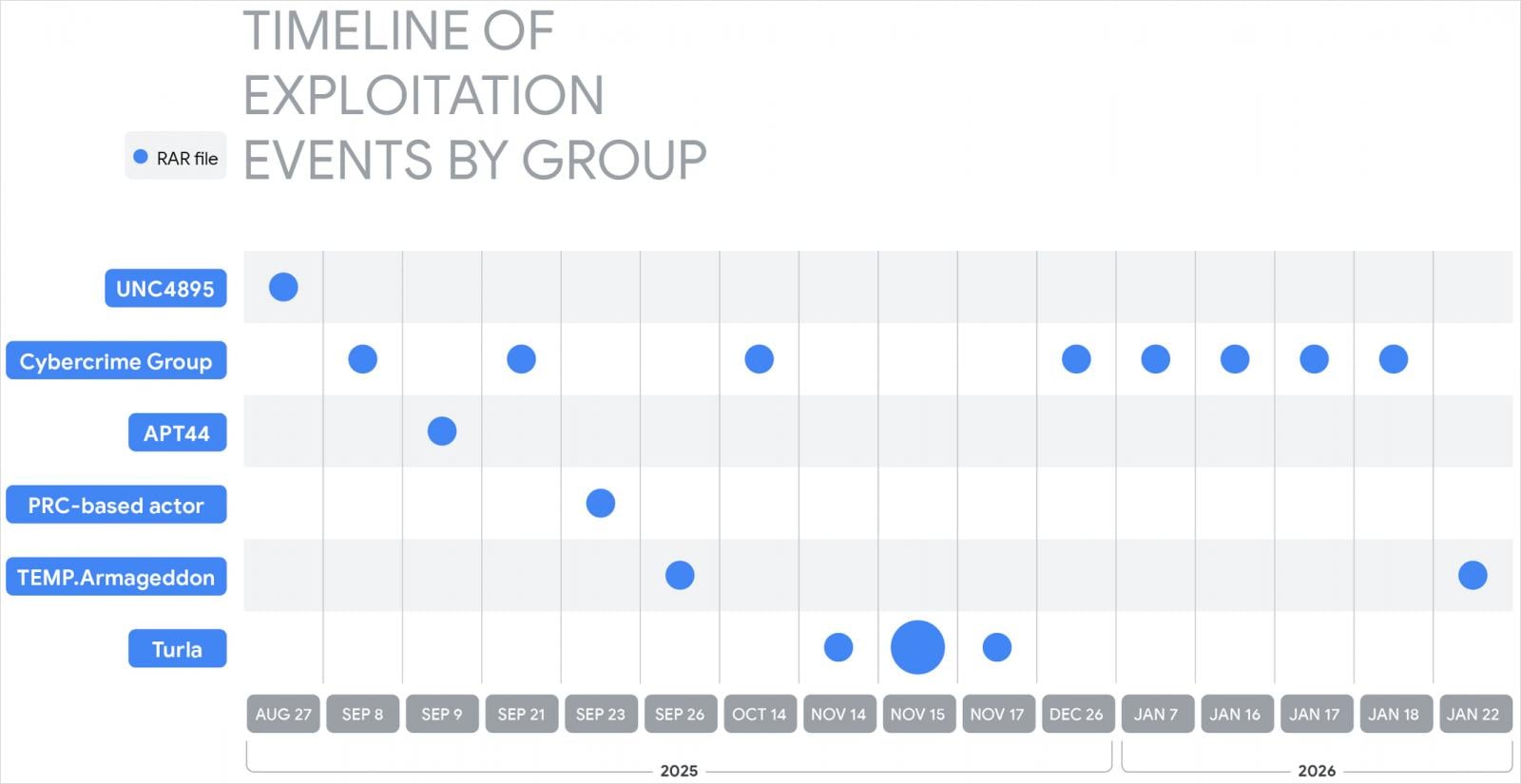
The timeline of exploitation reveals a rapid adoption of this zero-day capability. Initial observations of exploitation activity trace back to mid-July 2025. This early phase was notably linked to sophisticated, state-sponsored espionage groups, indicating the high value placed on this access method for intelligence gathering operations. Subsequently, the threat landscape broadened significantly, incorporating financially motivated cybercriminals who quickly integrated the exploit into their standard toolkit for deploying commodity malware. This dual-pronged assault—from nation-state actors seeking strategic advantage and lower-tier criminals seeking immediate financial gain—cements the CVE-2025-8088 flaw as a universal access enabler.
The initial public disclosure surrounding this vulnerability was brought to light by researchers at ESET in early August 2025. Their findings specifically implicated the Russia-aligned threat group known as RomCom, who were observed utilizing the flaw in targeted phishing campaigns, suggesting that exploit development and weaponization occurred rapidly following the vulnerability’s emergence or discovery. The subsequent validation and expanded analysis by the Google Threat Intelligence Group (GTIG) confirmed the widespread nature of the abuse, detailing the broad range of threat actors now leveraging the flaw.
The technical mechanics of the attack chain, as detailed by Google researchers, rely on misdirection. An archive delivered to a target contains both the visible, legitimate decoy file (e.g., a document) and concealed Alternate Data Streams housing the executable components. The path traversal mechanism, triggered during the extraction process by WinRAR’s handling of these specific stream definitions, redirects the payload to a location where it can execute persistently. The final executed file types observed are typical for initial access: LNK shortcuts, HTML Applications (HTA), batch scripts (.BAT), command files (.CMD), or various scripting languages designed for immediate execution upon system startup.

The state-sponsored entities identified by Google in connection with CVE-2025-8088 typically aim for long-term espionage objectives. Their payloads are often geared toward establishing resilient command-and-control (C2) channels, deploying sophisticated surveillance modules, or mapping internal network topologies for future lateral movement. For these actors, the reliability and stealth offered by the ADS-leveraging path traversal are paramount to maintaining an undetected presence within sensitive environments.
In contrast, the financially motivated threat actors exhibit a focus on immediate monetization. GTIG observed these groups using the WinRAR vulnerability to deploy a range of well-known, off-the-shelf malware. This includes Remote Access Trojans (RATs) like XWorm and AsyncRAT, tools that grant operators comprehensive remote control over compromised systems. Furthermore, there is evidence of deployment for information stealers designed to harvest credentials, financial data, and sensitive documents. Disturbingly, some campaigns targeted the installation of malicious browser extensions for Chrome, specifically engineered to intercept banking credentials or hijack web sessions, illustrating a direct monetization path.
A crucial element linking these disparate groups is the apparent commoditization of exploit acquisition. Google’s analysis strongly suggests that many of these actors did not develop the exploit themselves but rather procured it from specialized exploit brokers operating within the cybercriminal underground. The reporting highlights the activities of one such vendor, operating under the alias "zeroplayer," who publicly advertised the functional WinRAR exploit in July 2025. This vendor’s portfolio is telling; they were also marketing other high-value, zero-day exploits targeting major enterprise software, including sandbox escapes for Microsoft Office, Remote Code Execution (RCE) vulnerabilities in corporate VPN solutions, Windows local privilege escalation flaws, and bypass techniques for contemporary Endpoint Detection and Response (EDR) and antivirus solutions. Prices for these exploits ranged significantly, spanning from $80,000 to $300,000, reflecting their potency and reliability.
This market dynamic represents a significant maturation in the cyber threat ecosystem. The availability of potent, pre-packaged exploits reduces the barrier to entry for cybercrime organizations of varying sophistication levels. When a vulnerability like CVE-2025-8088 is effectively weaponized and then sold on the open market, it accelerates the ‘attack lifecycle.’ Instead of requiring months for threat actors to develop and test reliable exploitation chains, a ready-to-use module can be integrated into phishing kits within weeks, leading to mass exploitation against any organization running unpatched versions of the software.
Industry Implications and the Software Supply Chain Risk
The widespread, sustained abuse of this WinRAR vulnerability has profound implications for software vendors and enterprise security architects. First, it reaffirms the danger inherent in relying on globally distributed, yet infrequently updated, utility software. WinRAR, despite its age and ubiquity, remains a staple in countless corporate and personal environments for file management, making it an irresistible target for threat actors seeking broad reach.
Second, the reliance on ADS for payload delivery highlights a gap in defensive visibility. Traditional static analysis tools and even many runtime protection mechanisms are often configured to look for suspicious executable files appearing in expected directories. The abuse of ADS allows the malicious content to exist in an auxiliary data structure, only materializing as an executable file upon system instruction, often evading signature-based detection during the initial archive analysis phase.

For security teams, the exploitation of CVE-2025-8088 serves as a stark reminder that initial access often hinges on file handling vulnerabilities rather than complex network intrusions. This necessitates a shift in focus toward granular endpoint monitoring and process lineage tracking. Security solutions must be capable of identifying when archival software initiates file creation sequences in sensitive locations like the Startup folder or user profile directories, even when the source appears to be a benign data stream.
Furthermore, the involvement of exploit brokers signals a professionalization of the cybercriminal supply chain. Organizations like "zeroplayer" function as venture capitalists for cybercrime, funding the research and development of high-impact exploits and then democratizing access to them. This commercialization forces defenders into a constant, reactive game of catch-up, as the window between vulnerability disclosure (or discovery) and mass weaponization shrinks dramatically.
Expert Analysis on Persistence and Evasion
From an expert perspective, the choice of persistence mechanism—the Windows Startup folder—is strategically sound for these threat actors. While advanced EDR solutions are adept at monitoring registry keys associated with persistence (like Run keys), the Startup folder remains a relatively straightforward and reliable method that often requires less complex evasion techniques. If the dropped file is a standard LNK file pointing to a legitimate-looking executable disguised within a user profile folder, the chain of execution is difficult to attribute to malware solely based on the initial archive extraction event.
The success of this exploit relies on social engineering layered on top of a technical flaw. The user must be convinced to download and open the malicious archive. The decoy documents—PDFs, invoices, or sensitive-sounding memos—are essential bait. The technical flaw then does the heavy lifting, turning a user action intended for productivity into a system compromise. This layered approach—social engineering plus a reliable technical vulnerability—is the hallmark of highly effective intrusion campaigns.
Future Impact and Evolving Defense Strategies
The continued exploitation of CVE-2025-8088, months after its initial discovery and likely subsequent patching by WinRAR developers, indicates a failure in patch management across many organizations. This highlights a systemic issue where critical updates for non-operating system utilities are often delayed or missed entirely.
Looking ahead, this incident sets several trends:
-
Increased Scrutiny on Archival Utilities: Security researchers and vendors will likely dedicate more resources to auditing the file handling and extraction logic within popular tools like WinRAR, 7-Zip, and others. Expect more focus on buffer overflows, improper input validation, and directory traversal possibilities within these sandboxed environments.
-
Normalization of Exploit Trading: The documented pricing and diversification of exploits sold by brokers like "zeroplayer" suggest that advanced, zero-day capabilities will remain accessible to a wider array of threat groups, including ransomware affiliates and smaller fraud operations. This forces security postures to assume the constant possibility of zero-day compromise.
-
Defense-in-Depth for Initial Access: Security architectures must evolve beyond perimeter defenses. The focus must shift inward to runtime integrity and behavioral analysis. Techniques such as application control policies that restrict where executables can be dropped, coupled with advanced monitoring for anomalous process spawning following file decompression, will become standard requirements for mitigating these types of multi-stage attacks. Specifically, monitoring for scripts executing shortly after archive extraction, particularly those targeting user environment variables or system startup locations, is critical.
The WinRAR path traversal flaw serves as a potent case study in modern cyber threats: a single, deeply embedded software flaw, when paired with the ready availability of exploit technology, can become a universal tool for adversaries ranging from nation-states to opportunistic cybercriminals, demanding relentless vigilance in software hygiene and endpoint detection capabilities. The ongoing threat illustrates that foundational software components remain fertile ground for compromise, even as attention frequently shifts toward newer, more complex technologies.

