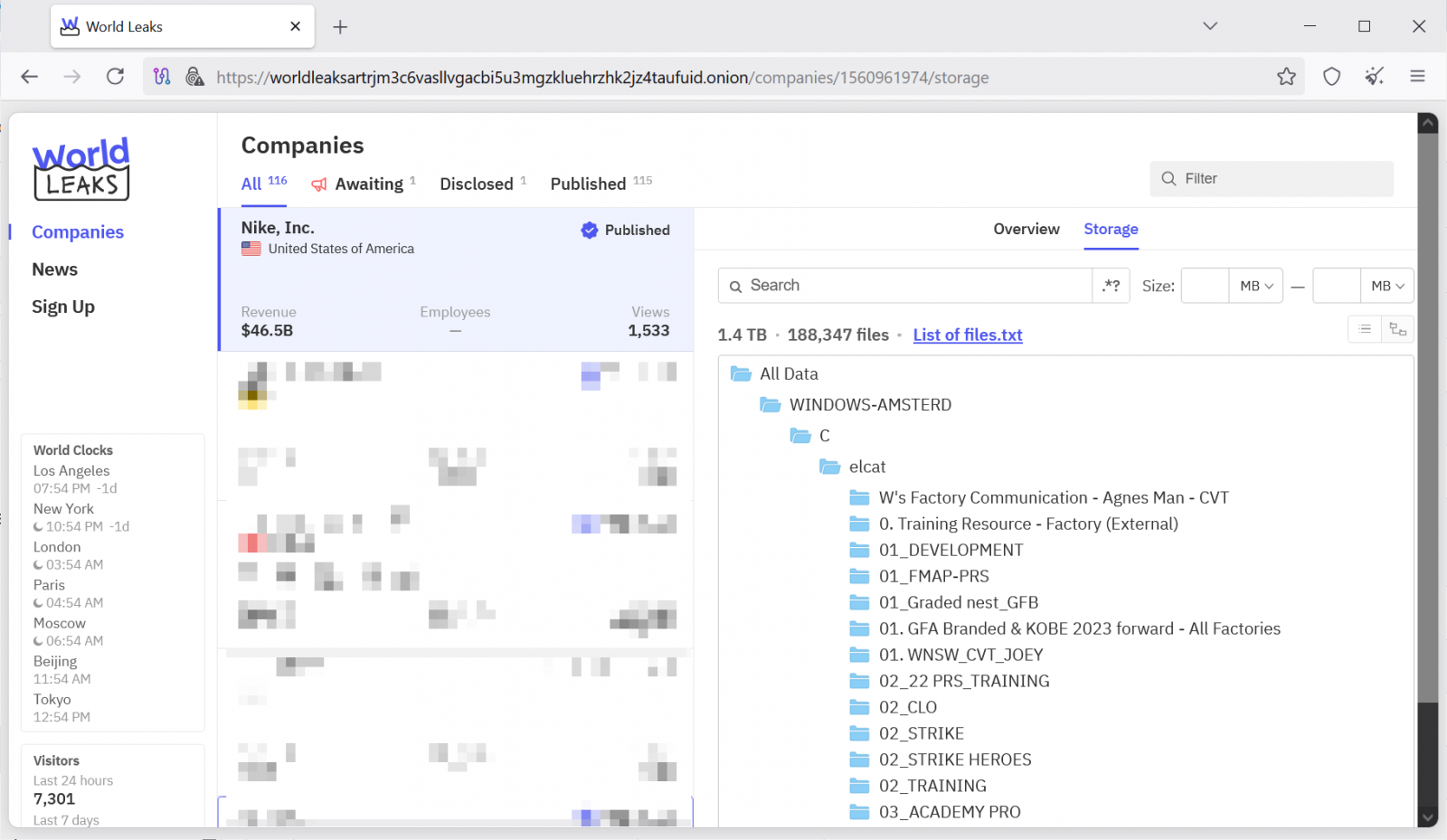
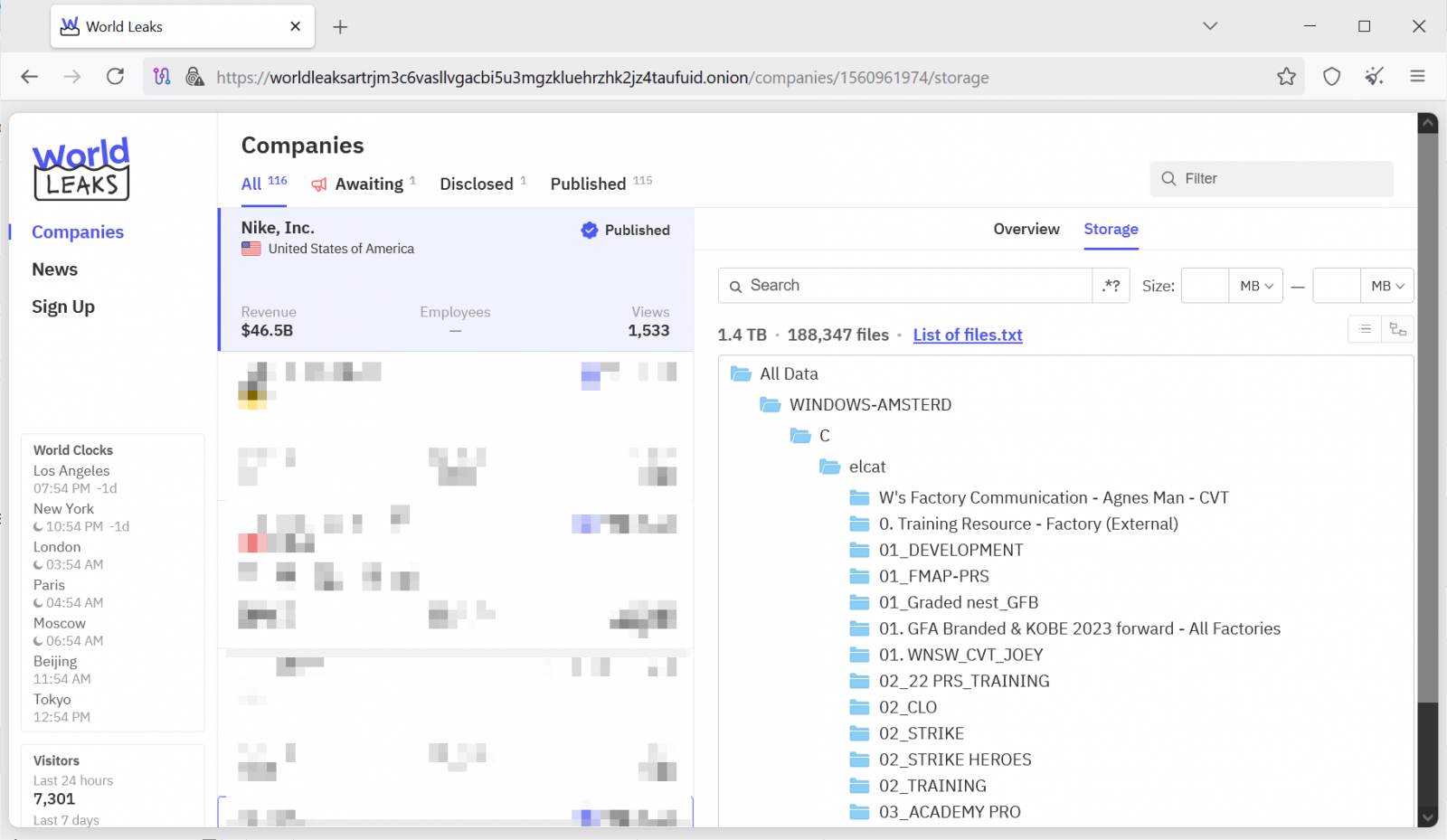
The athletic apparel behemoth Nike is currently navigating the fallout from what it has officially termed a "potential cyber security incident," following the highly publicized data dump orchestrated by the cybercriminal collective known as World Leaks. Reports indicate the threat actor posted approximately 1.4 terabytes (TB) of files allegedly exfiltrated from the corporation’s sensitive digital repositories. This event underscores the persistent and escalating threat landscape facing even the most security-conscious multinational organizations in the current digital economy.
In a measured response delivered via email communication, the company affirmed its commitment to safeguarding stakeholder information: "We always take consumer privacy and data security very seriously," the statement read. "We are investigating a potential cyber security incident and are actively assessing the situation." This standard corporate acknowledgment initiates a critical forensic phase, aimed at determining the scope of compromise, the vectors utilized by the attackers, and the precise nature of the exposed data.
The escalation occurred when the World Leaks extortion group prominently featured Nike on its dedicated dark web data-leak portal. The group claimed to have successfully pilfered close to 190,000 distinct files. Crucially, these purported stolen assets allegedly contain proprietary corporate intelligence pertinent to Nike’s intricate business operations, suggesting a deep-level intrusion into internal systems rather than just peripheral customer data exposure.
Intriguingly, subsequent monitoring revealed that the World Leaks entry pertaining to Nike was rapidly withdrawn from the public leak site shortly before detailed reporting on the incident gained widespread traction. This sudden removal suggests several immediate possibilities within the realm of incident response: either active, high-stakes negotiations are underway between Nike and the threat actors, potentially involving a ransom payment to secure the deletion of the data, or the threat actors were compelled to retract the listing due to immediate legal or technical pressures. Regardless of the reason, Nike has yet to issue any definitive confirmation validating the threat group’s assertions regarding the actual theft or exfiltration of data, and independent verification of the authenticity and sensitivity of the purportedly leaked files remains pending.
The Evolving Modus Operandi of Threat Actors
To fully appreciate the gravity of this situation for Nike, it is essential to contextualize the threat actor involved. World Leaks is not a newly emerged entity but is widely understood within cybersecurity circles to be the rebranded face of the Hunters International ransomware operation. This transition, which reportedly solidified in January 2025, marks a strategic pivot within the cybercrime ecosystem. Citing mounting risks associated with traditional file encryption ransomware campaigns—coupled with diminishing profitability and increased law enforcement scrutiny—Hunters International executed a full shift to a data theft and extortion-only model. This "double extortion" precursor (stealing data before encryption) has now evolved into a primary, singular revenue stream for groups like World Leaks.

Hunters International itself was a relatively recent phenomenon, surfacing in late 2023. Early analysis suggested potential lineage or code similarities with the infamous Hive ransomware group, hinting at a lineage of experienced operators simply adopting new branding following Hive’s supposed dismantling. This continuous rebranding and evolution are hallmarks of modern cybercriminal enterprises seeking operational security and to evade sanctions or takedowns.
The track record of World Leaks and its predecessor demonstrates a pattern of targeting high-profile entities across diverse sectors. The list of organizations previously claimed as victims by this operation is extensive and includes significant governmental, technological, and industrial entities. Noteworthy past targets reportedly include the U.S. Marshals Service, the Indian technology powerhouse Tata Technologies, the Japanese optics manufacturer Hoya, North American automotive retail giant AutoCanada, and the critical U.S. Navy contractor Austal USA. This history establishes World Leaks as a sophisticated actor capable of penetrating complex, high-security environments, thereby elevating the perceived risk level for Nike.
Furthermore, the operational reach of World Leaks affiliates extends to sophisticated supply chain vulnerabilities. In recent activity, affiliates were implicated in the breach of a Dell product demonstration platform. More technically concerning was their reported exploitation of legacy, end-of-life SonicWall SMA 100 devices, leveraging these unpatched entry points to deploy custom malware, specifically the OVERSTEP rootkit. This capability demonstrates not only data exfiltration prowess but also the ability to maintain deep, persistent access within compromised networks.
Industry Implications: The New Imperative for Data Governance
The potential compromise of 1.4 TB of corporate data at Nike sends ripples far beyond the immediate brand reputation crisis. For the global sportswear and retail sector, this incident highlights critical vulnerabilities in managing vast quantities of both proprietary business data and consumer Personally Identifiable Information (PII).
The sheer volume of data—1.4 TB—suggests the attackers accessed more than just marketing plans; they likely touched R&D, supply chain logistics, financial forecasting, and potentially employee records, given the nature of corporate system compromises. The theft of operational data can translate directly into competitive disadvantages, allowing rivals to anticipate product launches, understand margin structures, or exploit known supply chain bottlenecks.
This event reinforces a paradigm shift in enterprise risk management: Data is the primary asset, and its leakage is the primary threat vector. Unlike ransomware, where recovery is often a discrete event (paying or rebuilding), data leakage is permanent. Once corporate strategy or intellectual property is public, the damage is irreversible, regardless of whether a ransom is paid.

Expert Analysis: Supply Chain, Third-Party Risk, and Zero Trust Failures
From an expert perspective, an intrusion leading to the compromise of such a large dataset often points to systemic failures in one of three core security domains: supply chain vetting, remote access security, or the efficacy of a Zero Trust architecture.
Supply Chain Blind Spots: Given the history of World Leaks affiliates targeting vendors (like the Dell platform breach), it is plausible that the initial compromise vector was a third-party vendor or contractor with elevated, overly permissive access to Nike’s core systems. In the interconnected world of global manufacturing and logistics, a vulnerability in a small logistics partner can serve as the critical pivot point into a Fortune 500 environment. Modern security frameworks must mandate rigorous, continuous auditing of third-party access entitlements, moving beyond simple annual compliance checks.
Remote Access and Legacy Systems: The attack signature often associated with these groups—exploiting older or unpatched VPN appliances (like the SonicWall example)—suggests that unmanaged or insufficiently patched perimeter defenses might have been the ingress point. Even large enterprises struggle with Shadow IT and the proper retirement of legacy hardware or software that remains connected to the corporate backbone. If the attackers bypassed multi-factor authentication (MFA) via compromised credentials harvested elsewhere, it indicates a breakdown in credential hygiene or MFA enforcement.
Zero Trust Maturity: The modern security standard dictates a Zero Trust model, where no user or device is inherently trusted, even within the network perimeter. A breach of this magnitude suggests that once the initial foothold was established, the attacker was able to move laterally with relative ease to access core data stores. This implies that internal segmentation, micro-segmentation policies, and least-privilege access controls were either absent or insufficiently enforced across the internal network architecture. The presence of 1.4 TB of accessible data suggests that network topography allowed broad reach from the initial point of compromise.
Future Impact and Security Trends
The Nike incident will undoubtedly serve as a case study reinforcing several emerging trends in cybersecurity strategy for 2026 and beyond:
1. The Rise of Data-Centric Compliance: Regulatory bodies globally are shifting focus from just protecting systems to demonstrating granular control over data flow. Future compliance frameworks will likely demand organizations prove they can isolate, classify, and restrict access to data sets that, if leaked, would cause severe competitive harm (e.g., R&D, long-term financial models), treating this operational IP with the same gravity as consumer PII.
2. Prioritization of Data Loss Prevention (DLP) in Extortion Scenarios: As groups like World Leaks focus purely on data exfiltration, investments in advanced Data Loss Prevention (DLP) solutions—especially those incorporating AI to monitor anomalous data movement patterns—will become non-negotiable. The goal shifts from preventing the theft (which is increasingly difficult) to detecting the exfiltration attempt in real-time, allowing for prompt quarantine and response before the massive data volume is successfully transferred.
3. Hardening the Software Supply Chain: Expect an acceleration in the adoption of Software Bill of Materials (SBOMs) not just for product development but for internal infrastructure components. Organizations will demand greater transparency from their technology providers regarding the security posture of the software they deploy, viewing every piece of integrated technology as a potential backdoor.
4. The Inevitability of "Leak and Negotiate": The fact that the listing was pulled suggests that extortion remains a potent financial incentive, even if the attack vector is purely data leakage rather than encryption. Companies must develop robust pre-negotiation frameworks, balancing the reputational damage of paying a ransom against the catastrophic business impact of having proprietary plans—or worse, sensitive engineering diagrams or employee data—circulated indefinitely on the dark web.
Nike’s ongoing investigation is more than an internal audit; it is a stress test for global corporate resilience against a highly adaptive, post-ransomware threat actor. The outcome will dictate the necessary level of cybersecurity investment and architectural restructuring required across the entire high-value manufacturing and retail ecosystem to prevent similar massive-scale operational data exposures in the near future.