A highly critical security vulnerability, dormant within the GNU InetUtils telnetd server for over a decade, has recently been disclosed and is already facing active exploitation attempts in the wild. Cataloged under CVE-2026-24061, this flaw represents a stark reminder of the inherent risks associated with relying on legacy, unmaintained network protocols, particularly in environments where patching cycles are notoriously slow. Reported publicly on January 20th, the vulnerability’s technical nature makes it alarmingly simple to weaponize, with proof-of-concept exploit code circulating rapidly among security researchers and malicious actors alike.
The Anatomy of a Decade-Long Oversight
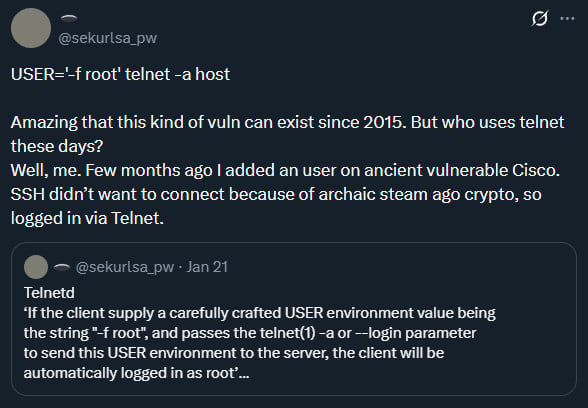
The core of CVE-2026-24061 lies in how the telnetd component of the widely used GNU InetUtils suite handles environmental variables during the execution of the local login process. Simon Josefsson, an open-source contributor and security professional, detailed the mechanism of failure. The vulnerability stems from the direct, unsanitized passage of the user-controlled USER environment variable to the /usr/bin/login utility when spawning a new session.
In standard operation, the telnetd service accepts incoming connections. When a user attempts to log in, the system executes /usr/bin/login to handle authentication. Crucially, the flawed implementation allows an attacker to inject command-line arguments disguised as part of the USER variable. By crafting a specific payload—specifically setting USER to -f root—and initiating a connection using the non-interactive, unauthenticated telnet -a command (which attempts to log in using the remote user’s identity, often ignored or bypassed in misconfigurations), the attacker completely bypasses the standard authentication checks. The result is immediate, unauthenticated elevation to root privileges on the compromised host.
This systemic oversight has been embedded in the codebase since version 1.9.3, released in 2015, affecting all subsequent versions up to and including 2.7. The GNU Project swiftly addressed the issue, releasing version 2.8 which incorporates the necessary sanitization to neutralize the threat. However, the sheer longevity of the vulnerability highlights a pervasive issue in software supply chain management: dependencies, even those seemingly benign or rarely updated, can harbor deep, critical flaws.
Industry Implications: The Shadow of Operational Technology
The implications of an easily exploitable root compromise via a decade-old bug are far-reaching, but they cast a particularly dark shadow over Operational Technology (OT) and Industrial Control Systems (ICS) environments. GNU InetUtils, which bundles foundational network services like telnetd, ftpd, rshd, ping, and traceroute, is ubiquitous in the Linux and Unix ecosystem.
While modern IT infrastructure has largely migrated from the inherently insecure Telnet protocol to Secure Shell (SSH) for remote administration, Telnet remains stubbornly present in specialized sectors. Its simplicity, minimal overhead, and compatibility with ancient hardware make it a persistent feature in industrial settings—think legacy Programmable Logic Controllers (PLCs), Human-Machine Interfaces (HMIs), surveillance cameras, and various IoT sensors deployed on factory floors or critical infrastructure networks.
As Cristian Cornea of Zerotak noted in discussions regarding OT security, the replacement of these systems is rarely straightforward. "Critical systems in OT/ICS environments are not designed for rapid iteration or seamless upgrades," Cornea explained. "Any maintenance or patching operation often necessitates a full system reboot, which translates directly into production downtime. In environments where uptime is measured in years, administrators are inherently hesitant to touch stable, albeit insecure, legacy components." This reluctance creates a massive, vulnerable attack surface that attackers are now actively probing.

Even when administrators attempt to modernize, they frequently run into dead ends. As documented by various technical users, older networking gear, particularly from vendors like Cisco, often reaches an "End of Life" status where vendor support ceases, and firmware updates are non-existent. These devices are then kept operational via makeshift network segmentation, often relying on the fact that the insecure service (Telnet) is not directly exposed to the public internet.
Active Exploitation and Threat Monitoring
Despite the common assumption that Telnet is largely absent from internet-facing infrastructure, the reality observed by threat intelligence firms suggests otherwise, at least on targeted networks. Researchers are now observing a "find-and-exploit" campaign targeting CVE-2026-24061.
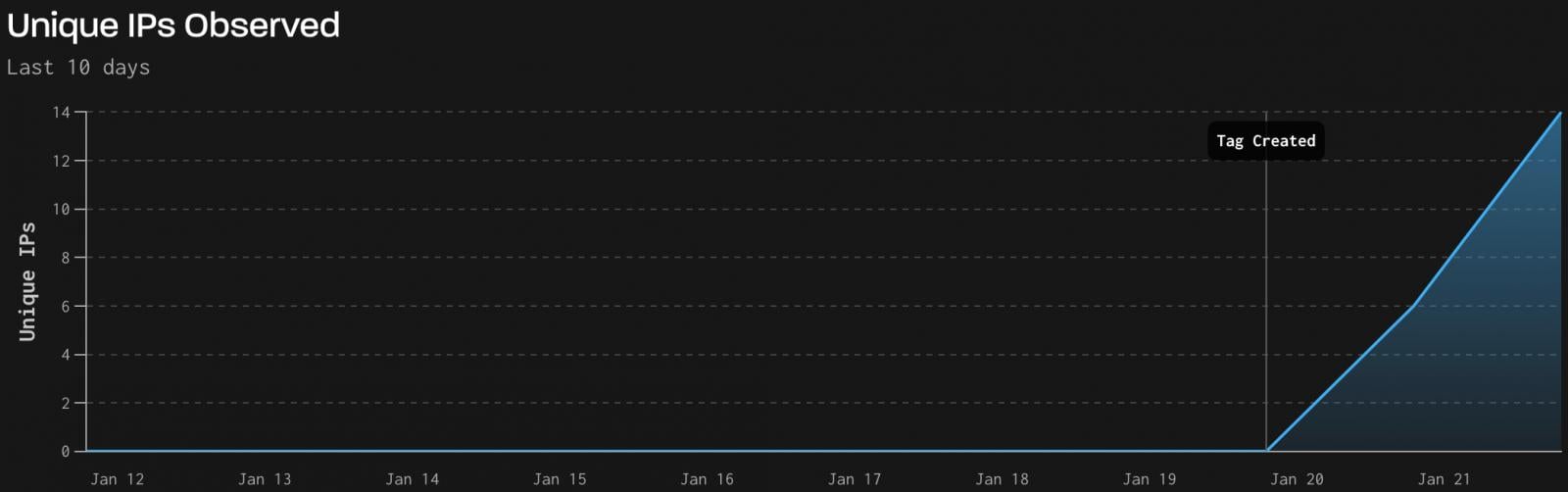
The threat monitoring firm GreyNoise has provided concrete data confirming active, real-world exploitation attempts against vulnerable endpoints discovered between January 21st and 22nd. The telemetry collected paints a picture of coordinated, automated scanning and exploitation:
- Scale of Activity: The exploitation attempts originated from 18 distinct attacker IP addresses, manifesting across 60 separate Telnet sessions.
- Malicious Intent: All observed traffic was categorized as 100% malicious, involving 1,525 packets totaling approximately 101.6 KB, confirming reconnaissance and active attempts to leverage the authentication bypass.
- Target Preference: In a striking 83.3% of cases, the attackers explicitly attempted to gain access as the
rootuser, confirming the primary goal is immediate, full system compromise rather than low-privilege access.
The attack vector utilized the Telnet "Interpret as Command" (IAC) option negotiation sequences to covertly inject the malicious USER=-f <user> string into the connection handshake, a highly specific technique indicative of actors who have thoroughly analyzed the vulnerability report.
Following the initial successful (or attempted) authentication bypass, the observed automated activity shifted into post-exploitation routines. These routines included automated reconnaissance scans to map the compromised system and initial persistence attempts, notably the staging of SSH keys for backdoor access and the attempted deployment of Python-based malware payloads. Significantly, GreyNoise observed that these post-exploitation efforts frequently failed due to missing necessary binaries or directories on the targeted systems—a common occurrence on stripped-down embedded or OT devices. While failure is encouraging, it does not negate the initial breach; it only suggests the attackers may be refining their tooling for future, more successful attempts.
Expert Analysis: The Nature of Trivial Exploits
The "trivial" nature of CVE-2026-24061 is what elevates its risk profile beyond complex, hard-to-replicate zero-days. A vulnerability that can be reliably triggered with a few command-line arguments is accessible to script kiddies and large-scale botnets alike. This accessibility drastically shortens the window between disclosure and mass exploitation.
From a software engineering perspective, this failure underscores the critical importance of input validation, particularly when interfacing with operating system command execution pathways (like spawning login). Any environment variable, especially one derived from network input, must be treated as potentially malicious, requiring rigorous sanitization (e.g., stripping leading hyphens or parsing arguments before execution) rather than being passed through directly.
The fact that this flaw persisted across 11 years of GNU InetUtils releases points to a broader challenge in open-source maintenance: the "bus factor" and the reliance on volunteer efforts for security auditing of mature, stable codebases. When a library is perceived as stable and legacy, security reviews often cease, allowing subtle but critical flaws like this environment variable mishandling to persist undetected until an external researcher discovers them.
Future Impact and Mitigation Imperatives
While some industry observers might minimize the threat by noting that few systems run Telnet exposed directly to the public internet, this perspective dangerously ignores the internal network landscape. An attacker who gains a foothold via a different initial vector—such as a phishing email or a vulnerable web application—will scan internal networks for legacy protocols. A vulnerable telnetd instance on an internal subnet connected to a critical manufacturing floor or utility network represents a direct bridge to high-value assets.
The industry response must be immediate and comprehensive:
- Prioritized Patching/Upgrading: System administrators using GNU InetUtils must immediately upgrade to version 2.8 or later. This should be treated with the same urgency as patching any known remote code execution vulnerability.
- Service Disablement: For systems that cannot be immediately patched—the common scenario in OT—the telnetd service must be administratively disabled. If the service is not required for any operational purpose, removing the binary entirely is the most robust countermeasure.
- Network Segmentation and Firewalling: TCP port 23 must be aggressively blocked at the perimeter of all sensitive network zones. Furthermore, internal network segmentation should be reviewed to ensure that devices with legacy services are isolated from general user access points. Only authorized management hosts, preferably utilizing secure protocols like SSH, should be permitted to communicate with these older systems.
- Inventory Management: This incident should trigger a renewed focus on asset inventory, particularly identifying all instances of Telnet services running across the enterprise and industrial footprint. Without a complete inventory, remediation efforts will inevitably miss critical targets.
The exploitation observed by GreyNoise confirms that automated tools are already mapping the landscape. While current post-exploitation success rates appear low due to missing tooling, attackers will inevitably iterate and adapt their malware to target the specific, often constrained, environments where Telnet still lingers. The window for proactive defense is closing rapidly, making immediate hardening of these decade-old exposures a cybersecurity imperative.