The cybersecurity landscape is currently grappling with a sophisticated surge in social engineering tactics, with the notorious extortion group ShinyHunters publicly claiming responsibility for a string of highly effective voice phishing (vishing) operations. These coordinated attacks are laser-focused on compromising Single Sign-On (SSO) infrastructure provided by major vendors, including Okta, Microsoft Entra, and Google Workspace. Successful infiltration of these central identity hubs grants threat actors the keys to a vast array of interconnected Software-as-a-Service (SaaS) platforms, setting the stage for massive corporate data exfiltration and subsequent extortion attempts.
The methodology employed by these threat actors represents a chilling evolution in phishing. Rather than relying solely on deceptive emails or static malicious links, the attackers engage directly with employees via telephone. They meticulously impersonate internal IT support staff, leveraging persuasive social engineering narratives to establish a sense of urgency and authority. The primary objective of these calls is to coerce the target employee into visiting a counterfeit login portal designed to mirror their organization’s legitimate SSO interface. Once on the fake site, the victim is tricked into willingly surrendering their primary credentials. Crucially, the attack vector extends past mere password theft; the attackers successfully guide the victim into also providing their Multi-Factor Authentication (MFA) codes or approving push notifications in real-time.
This complete credential takeover—credentials plus the temporary MFA token—instantly compromises the user’s SSO session. For modern enterprises, SSO services act as the digital front door to the entire cloud ecosystem. An Okta, Entra, or Google identity breach is not merely a single account compromise; it is akin to obtaining a master key ring. The compromised SSO dashboard reveals an inventory of all linked enterprise applications—ranging from mission-critical systems like Salesforce, Microsoft 365, and Google Workspace, to collaboration tools like Slack, development platforms like Atlassian, and financial systems such as SAP. Attackers systematically move across this landscape, harvesting sensitive data from every accessible service linked to that user profile, a process that often goes undetected until the extortion demands surface.
The Technical Sophistication of Real-Time Phishing Kits
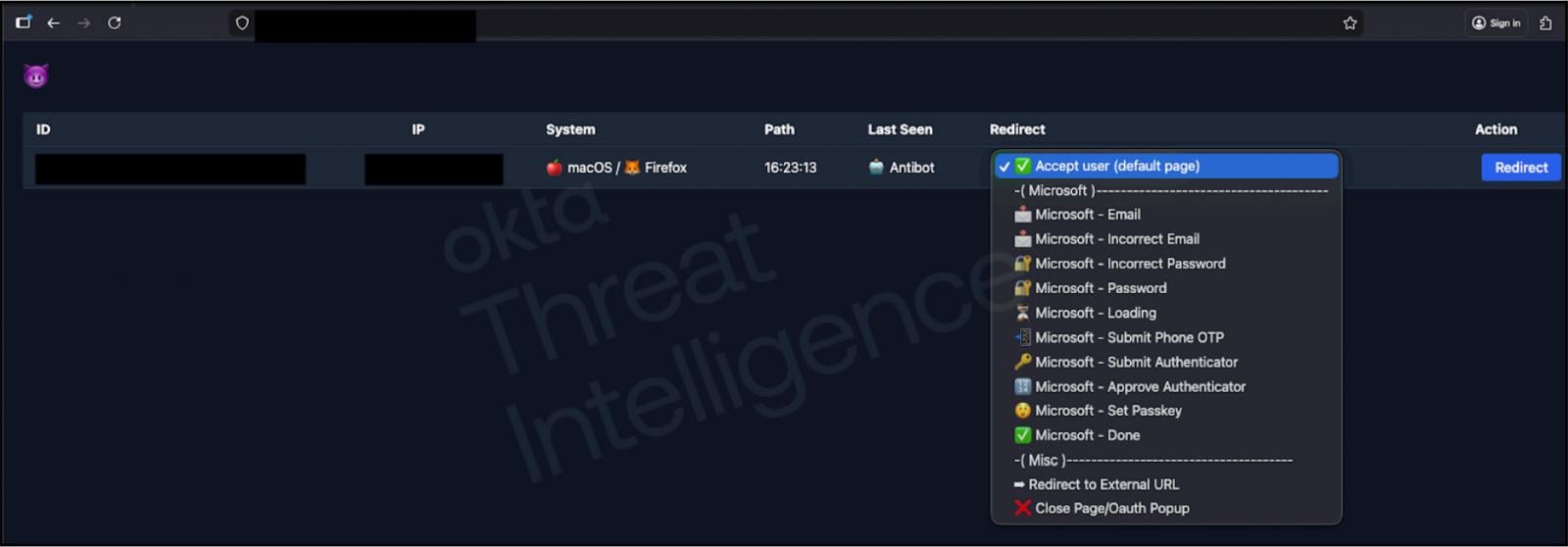
The efficacy of this campaign is underpinned by highly evolved phishing infrastructure. As previously documented by security researchers, these attacks rely on specialized phishing kits designed specifically to defeat interactive authentication methods. These kits are not rudimentary web templates; they incorporate dynamic control panels accessible to the threat actor conducting the vishing call.

During the conversation with the targeted employee, the attacker uses this remote control panel to manipulate the content displayed on the victim’s screen in real time. If the initial login attempt (using stolen credentials) triggers an MFA prompt—for example, a request to approve a push notification—the attacker’s control panel dynamically renders a convincing, fake dialog box on the victim’s browser. This dialog box instructs the employee on exactly how to approve the MFA request on their actual device, thus bypassing the security control in the moment it is deployed. This iterative, guided approach overcomes the friction that often causes traditional MFA-protected phishing attempts to fail.
Security vendors, notably Okta, have provided detailed technical insights into the capabilities of these kits, noting their ability to seamlessly integrate the attacker’s actions with the victim’s real-time authentication challenges. While Okta has provided crucial threat intelligence describing the mechanisms, the company has officially declined to comment specifically on the ongoing data theft incidents linked to these attacks.
ShinyHunters Confirms and Clarifies Campaign Scope
Following initial reports circulating within the security community, the ShinyHunters collective directly engaged with investigative journalists to confirm their involvement. While initially evasive, the group later issued a statement confirming responsibility for "some of the social engineering attacks."
In their communication, ShinyHunters clearly articulated their strategic focus, emphasizing that Salesforce environments remain their "primary interest and target," labeling other compromised systems as secondary gains or "benefactors." This focus aligns with their established history of targeting high-value corporate data repositories. The group acknowledged the general reporting regarding the phishing infrastructure and domain usage deployed in the campaign. However, they contested one specific piece of visual evidence—a screenshot of a command-and-control server shared by Okta—claiming that their operational infrastructure was custom-built ("in-house") rather than utilizing publicly referenced templates.
Crucially, ShinyHunters explicitly stated their targeting extended beyond Okta, confirming operations against Microsoft Entra and Google SSO environments, thereby escalating the perceived scope of the threat across the entire identity management ecosystem.

Microsoft indicated it had no immediate comment, while Google maintained that, based on their current telemetry, there was "no indication that Google itself or its products are affected by this campaign," suggesting that the abuse is centered on the identity management layer provided by third-party providers or Google’s external SSO integration points, rather than vulnerabilities within the core Google authentication service itself.
The Data Advantage: Leveraging Prior Breaches
A significant factor underpinning the success rate of these vishing campaigns is the quality of the intelligence used to select and target victims. ShinyHunters claimed they are systematically reusing data previously stolen in large-scale breaches, most notably the extensive data theft incidents involving Salesforce environments. This stolen repository contains essential intelligence for effective social engineering: employee names, precise job titles, and direct contact phone numbers.
Armed with this verified personal and professional data, the attackers can construct highly believable scripts, lending credibility to their impersonation of internal support staff. This pre-existing data acts as an accelerant, drastically reducing the time and effort required to socially engineer a successful MFA bypass compared to attackers relying on generalized phishing lists.
The group’s operational posture remains aggressive. In parallel with the vishing campaign, ShinyHunters recently reactivated its Tor-based data leak site, which now lists several new victims. These include SoundCloud, Betterment, and Crunchbase. While SoundCloud and Betterment had previously disclosed security incidents—SoundCloud confirming a breach in late 2025 and Betterment acknowledging its email platform was leveraged for crypto scams this month—Crunchbase is a newly confirmed victim, having reported today that documents were exfiltrated from its corporate network. Crunchbase confirmed containment, engagement with cybersecurity experts, and notification of federal law enforcement, stating that business operations remained unaffected.
Industry Implications: The Centrality of SSO and MFA Fatigue
The current situation serves as a stark warning regarding the inherent risk associated with consolidating digital access through SSO platforms. While SSO offers immense productivity benefits—reducing password fatigue and streamlining cloud access—it concentrates risk onto a single authentication vector.

Expert Analysis on Risk Concentration:
From a security architecture perspective, the attacks exploit a fundamental gap: the assumption that MFA is an impenetrable barrier. While MFA successfully thwarts automated credential stuffing and password spray attacks, real-time human interaction, known as MFA fatigue or MFA bombing (when used aggressively), remains a potent vulnerability. When an attacker can talk an employee through the final step of authentication, the entire MFA deployment effectively collapses.
This elevates the importance of modern authentication mechanisms. Security analysts are now emphasizing the need to move beyond simple SMS codes or easily coerced push notifications toward phishing-resistant MFA methods, such as FIDO2/WebAuthn hardware security keys (e.g., YubiKeys). These solutions require physical presence and interaction with a secure element, making them impervious to remote manipulation via vishing scripts.
Supply Chain and Third-Party Risk:
The targeting of SSO providers highlights a critical dependency within the modern enterprise technology stack. If the identity provider (IdP) is breached, the security posture of every downstream application—from HR platforms to source code repositories—is immediately jeopardized. This puts intense pressure on IdP vendors to maintain impeccable security standards, as their compromise cascades throughout their entire customer base. Furthermore, organizations must rigorously vet the security practices of their IdPs, treating them not just as service providers but as mission-critical security enablers.
Future Impact and Evolving Threat Landscape
The success of ShinyHunters in attributing and profiting from these vishing operations is likely to inspire other threat groups. We anticipate a rapid adoption curve for these advanced, interactive phishing kits across the broader cybercriminal ecosystem.
Automation vs. Human Element:
While much of cybersecurity focuses on automating defenses against automated attacks, this campaign demonstrates the enduring potency of targeted, high-touch social engineering when paired with bespoke tooling. Future defense strategies must integrate threat intelligence on these specific vishing methodologies, training security teams to identify and flag unusual authentication attempts originating from internal helpdesk numbers or unexpected sources.
The Data Ecosystem Feedback Loop:
The reliance on data stolen from prior breaches (like Salesforce) to fuel new, more effective attacks creates a dangerous feedback loop. Every successful data breach provides richer reconnaissance material for future extortion attempts. This necessitates a fundamental shift in how organizations manage data retention and breach response, recognizing that data leaked today might be weaponized against employees tomorrow via targeted social engineering.
Ultimately, the ShinyHunters campaign underscores a paradigm shift: the perimeter has dissolved, and the user’s moment of trust—the single moment of authentication—is now the most heavily contested ground in enterprise security. Organizations relying on standard, easily bypassed MFA methods face an escalating threat that requires immediate investment in phishing-resistant authentication technologies and intensive, role-specific security awareness training focused specifically on recognizing and thwarting real-time voice manipulation.

