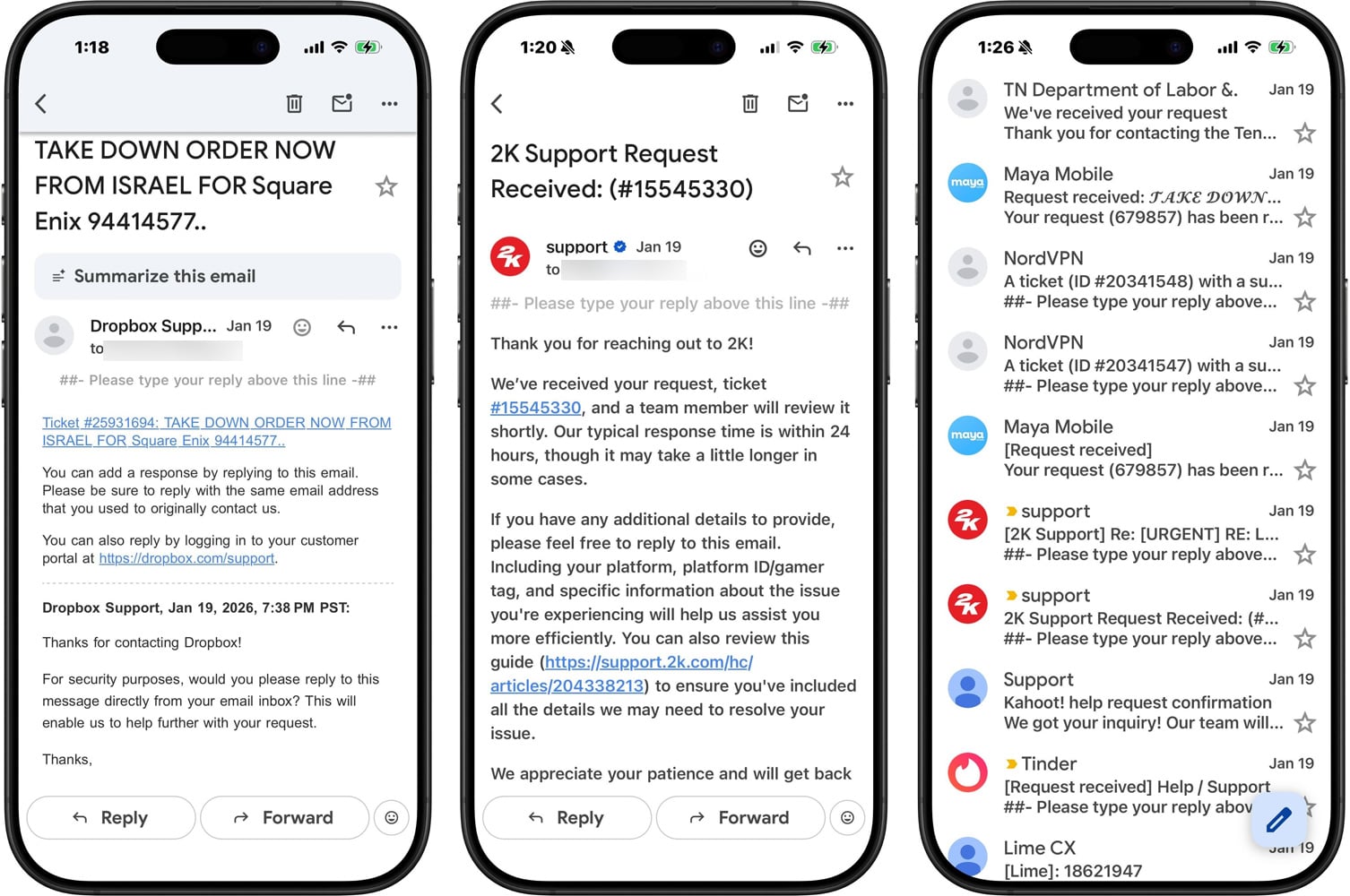
The digital ecosystem is currently grappling with the fallout of a widespread digital nuisance campaign, characterized by an overwhelming flood of unsolicited electronic messages targeting users globally. This significant communication disruption, which commenced around January 18th, leverages vulnerabilities within numerous organizations’ implementations of the Zendesk customer service ticketing platform. Reports surfaced rapidly across professional and public social media channels detailing the receipt of hundreds, and in some cases thousands, of emails bearing bizarre, erratic, or even superficially alarming subject lines. This incident serves as a stark reminder of the interconnected risks inherent in relying on third-party software infrastructure for critical business functions.
The core mechanism driving this saturation attack hinges on a feature, or rather, a configuration weakness, within the Zendesk ecosystem. Attackers have discovered and exploited the ability for unauthenticated, non-verified users to initiate a support ticket submission. Upon submission of a fabricated ticket—often utilizing vast lists of target email addresses—the Zendesk instance automatically generates a standard confirmation email, dispatched directly to the specified recipient address. This automated response acts as the delivery vehicle for the spam payload. By iterating this process across compromised or poorly configured instances, threat actors effectively weaponize the trusted communication channels of legitimate enterprises into a high-volume spam relay.
While the immediate threat does not appear to be rooted in traditional malware distribution or overt phishing attempts designed for credential harvesting, the sheer scale and chaotic nature of the communications are profoundly disruptive. Recipients are faced with an inbox avalanche, forcing them to manually triage legitimate communications from the noise. Furthermore, the content itself is often intentionally jarring—ranging from mock law enforcement notices and corporate takedown threats to nonsensical appeals like "Help Me!" or spurious offers for digital goods such as Discord Nitro. A notable characteristic of this campaign is the heavy utilization of Unicode characters to render text in bold, stylized, or multi-lingual formats, further enhancing their disruptive visual impact and potentially confusing automated content filters.
A cross-section of high-profile organizations, spanning technology, gaming, finance, and even governmental bodies, have been identified as unwitting sources of this digital deluge. The list of affected entities is extensive and includes major names such as Discord, Tinder, Riot Games, Dropbox, CD Projekt (via their 2k.com domain), NordVPN, Kahoot, and Headspace, alongside state-level agencies like the Tennessee Department of Labor and Revenue. The implication here is significant: the integrity of customer-facing communication is being undermined, not by a direct breach of the company’s primary systems, but by the compromised trust of their support infrastructure layer.

Industry Implications: The Erosion of Trust in Automated Communications
The fallout from this type of infrastructure abuse extends beyond mere annoyance; it strikes at the heart of digital trust. When automated emails originate from a domain known to be legitimate—like a company’s official support channel—they inherently possess a higher degree of perceived authenticity than typical unsolicited mail. This allows the spam to bypass conventional Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM) checks designed to flag external spoofing.
For the affected companies, the immediate consequence is customer confusion and potential reputational damage. Recipients, bombarded by emails seemingly from a trusted service, may experience anxiety or waste valuable time investigating the source. The fact that prominent firms like Dropbox and 2K felt compelled to issue public clarifications underscores the severity of the situation. These organizations were forced to divert support resources to manage the consequences of their own communication systems being exploited, transforming a security incident into a public relations challenge.
This incident highlights a critical, often overlooked vector in modern cybersecurity: supply chain risk embedded in SaaS dependency. Companies outsource customer relationship management (CRM) and helpdesk functionality to platforms like Zendesk, prioritizing scalability and feature richness over granular security configuration. While Zendesk provides robust security measures, the default settings, intended to foster ease of use for customer feedback (allowing unverified submissions), create an exploitable attack surface. This situation forces a difficult calculation for businesses: balancing frictionless customer engagement against hardening the perimeter against automated abuse.
Expert Analysis: The Mechanics of Relay Spam and Configuration Drift
Security experts categorize this activity as "relay spam," a technique distinct from traditional email bombing or Denial of Service (DoS) attacks. Relay spam exploits the inherent trust relationship between a legitimate mail server and the receiving client. The email isn’t technically spoofed; it is genuinely sent by the Zendesk servers on behalf of the client company.
The vulnerability rests squarely on the configuration posture of the individual Zendesk tenants. Zendesk’s platform, by design, facilitates rapid onboarding of support queries. As outlined by the vendor, the ability for "anyone to submit a support ticket, provide feedback, and report bugs without having to sign up for a dedicated support account" is a feature intended to lower the barrier for user interaction. However, without stringent rate limiting, CAPTCHA challenges, or, critically, restricting ticket submission to known, verified users, this flexibility becomes a liability.

Attackers systematically test the configuration of thousands of Zendesk instances. When an instance is found where a submission of an arbitrary email address in the contact field results in an automated confirmation email being relayed, that instance is added to the spamming matrix. The volume suggests the use of automated scripts capable of performing rapid-fire submissions against known or discovered Zendesk endpoints. The bizarre, multi-lingual Unicode content is likely an attempt to evade rudimentary text-based content filters, maximizing the noise-to-signal ratio for the recipients.
From a defensive standpoint, the failure here is primarily one of security hygiene and configuration management at the enterprise level, rather than a zero-day exploit against the Zendesk core platform itself. Zendesk’s prior December advisory regarding "relay spam" confirms that the vector was known and documented, placing the onus on adopting preventative measures such as enforcing user verification for ticket submission.
Future Impact and Evolving Security Trends
This massive spam wave serves as a pivotal case study illustrating the increasing sophistication of low-effort, high-impact disruption campaigns. It signals a trend where attackers prioritize leveraging legitimate infrastructure pathways over direct system penetration.
1. The Rise of Infrastructure Abuse Campaigns: We are likely to see an increase in attacks that treat established SaaS platforms—not just email relays, but collaboration tools, documentation repositories, and cloud storage services—as conduits for mass messaging or low-grade disruption. The focus shifts from gaining root access to gaining administrative access to communication features.
2. Re-evaluation of Default Configurations: Security teams must move away from accepting default configurations in business-critical SaaS applications. Features designed for maximum accessibility (like unverified public submissions) must be scrutinized against potential misuse, leading to a necessary pivot towards "secure-by-default" policies, even if it introduces minor friction for legitimate users.

3. Vendor Response and Platform Hardening: Following such a high-profile incident, Zendesk is compelled to accelerate the deployment of platform-level mitigations. Their announced introduction of enhanced monitoring and limits to detect unusual activity is crucial. However, the industry trend suggests that platform providers may need to shift the default setting to require verification for ticket creation, reversing the current user-experience bias. This could involve mandatory, lightweight authentication or advanced bot detection integrated directly into the ticket submission API endpoints.
4. The Need for Email Header Forensics Education: For end-users and security teams alike, this incident reinforces the need to deeply understand email headers. While the "From" address appears legitimate, a detailed analysis of the actual sending IP range and originating server (the Zendesk relay) would reveal the true source of the spam, helping organizations distinguish between a genuine support interaction and an infrastructure abuse event.
In conclusion, the global email inundation stemming from compromised Zendesk instances is a textbook example of leveraging feature permissiveness for malicious ends. It underscores a fundamental tension in modern cloud operations: the trade-off between seamless connectivity and hardened security. As businesses continue to integrate vast third-party service stacks, the responsibility for securing the resulting communication pathways becomes a shared, yet complex, challenge demanding proactive configuration auditing and a vendor ecosystem committed to secure-by-default operational postures. The incident demands that IT governance frameworks incorporate rigorous checks on every external-facing API endpoint, ensuring that accessibility does not equate to vulnerability.