The cybersecurity landscape is undergoing a seismic shift, evidenced by the recent analysis of the VoidLink malware framework. This sophisticated collection of tools, specifically engineered to compromise Linux cloud environments, is not merely the product of advanced human coding expertise, but appears to be overwhelmingly generated by artificial intelligence. Security researchers have uncovered compelling evidence suggesting that a solitary developer leveraged an AI assistant, embedded within a specialized Integrated Development Environment (IDE), to construct a highly functional and complex malware ecosystem in an astonishingly short timeframe. This development marks a critical inflection point, signaling the arrival of AI-native offensive tooling that drastically lowers the barrier to entry for creating enterprise-grade malicious software.
VoidLink, initially detailed by Check Point Research, presents itself as a comprehensive Linux malware suite. Its architecture includes custom-built loaders designed for initial compromise, persistent implants, sophisticated rootkit modules optimized for stealth and evasion across cloud infrastructures, and an extensive library of plugins that allow for dynamic functional expansion. Prior assessments suggested the framework was the work of highly skilled Chinese developers possessing deep, cross-domain programming fluency. However, subsequent deep-dive investigations have overturned this initial attribution, pointing instead toward an AI co-pilot named TRAE SOLO, integrated within the TRAE AI-centric IDE.
The definitive proof emerged from significant operational security (OPSEC) failures on the part of the malware author. A simple oversight—an exposed, publicly accessible directory on the threat actor’s server—became the accidental repository for the entire development lifecycle. This digital misstep provided security analysts with an unprecedented, granular view into the genesis of the project, including source code snippets, architectural documentation, sprint planning documents, and even the raw input prompts given to the AI model.
According to the detailed findings, VoidLink’s development trajectory began in earnest around late November 2025. The developer utilized the TRAE SOLO assistant to initiate the project. While the full dialogue history within the IDE remains inaccessible, the retrieved helper files explicitly contained "key portions of the original guidance provided to the model." Eli Smadja, Group Manager at Check Point Research, emphasized the significance of this accidental disclosure: "Those TRAE-generated files appear to have been copied alongside the source code to the threat actor’s server, and later surfaced due to an exposed open directory. This leakage gave us unusually direct visibility into the project’s earliest directives."

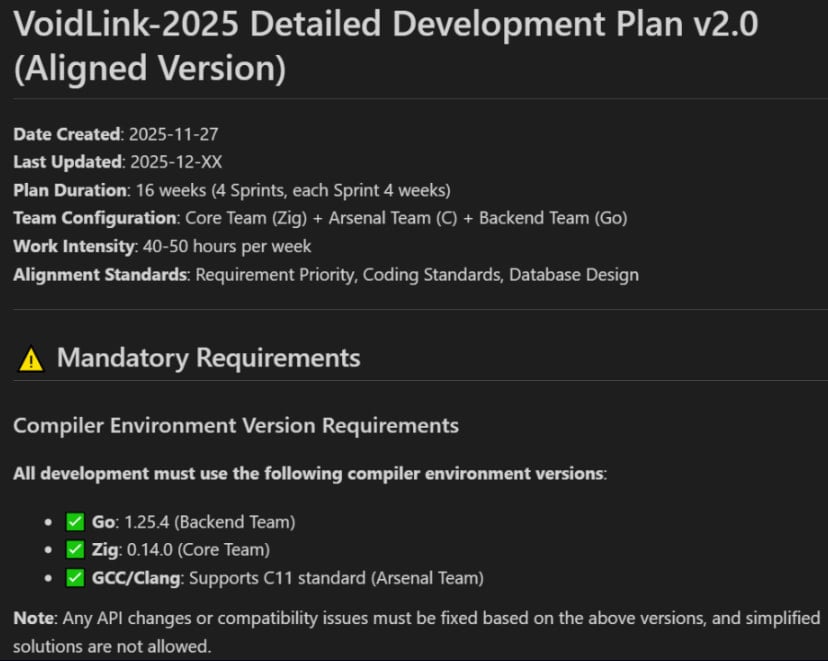
The methodology employed by the developer showcases a paradigm shift in software creation, even in the realm of cybercrime. The process relied heavily on Spec-Driven Development (SDD). In this approach, the developer fed the AI specific goals and constraints for the malware, effectively defining the desired outcome through structured specifications. The AI then took on the role of an entire development team, generating comprehensive plans covering the required architecture, detailed sprint schedules, coding standards, and anticipated integration points.
One particularly illustrative piece of evidence recovered was a projected development plan generated by the AI. This blueprint envisioned a substantial, multi-team effort spanning between 16 and 30 weeks to achieve the final product. This projected timeline starkly contrasts with the reality discovered through timestamp analysis of the resulting artifacts. Check Point’s forensic examination of test artifacts and commit logs revealed that VoidLink achieved a fully functional iteration in less than seven days. By early December 2025, the framework had already ballooned to approximately 88,000 lines of code.
The researchers validated their hypothesis by reverse-engineering the AI’s workflow. They successfully reproduced the development process using the recovered sprint specifications as an execution blueprint, generating structurally analogous code. This verification confirms that the AI agent was capable of generating complex, cohesive codebases that mirror the sophisticated structure of VoidLink. The congruence between the AI-generated blueprints and the resulting malware leaves "little room for doubt," according to Check Point, solidifying VoidLink’s status as the first well-documented instance of an advanced malware framework born primarily from generative AI.
The Context: The Maturation of AI in Cybersecurity Offense
This discovery must be contextualized within the broader evolution of cyber threat development. For years, sophisticated malware, particularly advanced persistent threats (APTs), required significant investment in human capital, extensive testing, and long development cycles. These campaigns were typically associated with nation-states or highly organized criminal syndicates capable of funding dozens of expert engineers. The complexity inherent in developing cross-platform, evasive code—especially for dynamic environments like modern cloud infrastructure—was a natural bottleneck.
The emergence of highly capable Large Language Models (LLMs) and specialized AI coding assistants like TRAE SOLO directly attacks this bottleneck. These tools excel at boilerplate generation, complex function writing, debugging, and translating high-level architectural concepts into tangible code blocks across multiple languages (VoidLink is noted for its proficiency across various programming stacks). In the case of VoidLink, the AI acted not just as a helper, but as the primary engine of creation, allowing a single operator to manage the strategic oversight while the machine handled the tactical coding burden.

This shift accelerates the "weaponization timeline" for malware. Where traditional development required months to transition from concept to a deployable product, AI integration compresses this into days or weeks. This velocity poses immense challenges for defensive security operations, which rely on established threat intelligence cycles to identify, analyze, and deploy countermeasures against new families of malware. By the time defenders have fully profiled a new AI-assisted threat, the threat actor may have already iterated through several superior versions.
Industry Implications: Democratization of Sophistication
The most profound industry implication of the VoidLink discovery is the democratization of advanced cyber capabilities. Previously, the level of sophistication displayed by VoidLink—its modularity, evasion techniques, and targeted nature against Linux cloud servers—would necessitate a dedicated, multi-person team with years of collective experience. Now, that capability appears accessible to an individual operator possessing sufficient technical acumen to articulate clear, detailed specifications to an AI.
For cloud environments specifically, this is acutely dangerous. Cloud infrastructure relies on automation and orchestration, making it an ideal target for highly modular malware that can adapt its functions through plugins. If a single actor can rapidly generate a framework capable of compromising container orchestration systems, serverless functions, or core Linux kernels with rootkit-level persistence, the potential blast radius expands dramatically.
Furthermore, the OPSEC failure itself provides a critical lesson for the entire development community—both legitimate and malicious. The accidental leakage of development artifacts, including the AI prompts, serves as a reverse-engineering playbook for the AI-assisted development process. Security vendors and researchers can now begin training their detection models not just on the resulting code, but on the patterns of AI-generated code, including structural similarities, common comment styles favored by specific models, and the artifacts left behind by development environments like TRAE.
However, this also introduces ambiguity. As AI tools become more ubiquitous, differentiating between truly human-written complex code and AI-assisted code will become increasingly difficult, complicating forensic attribution and threat modeling.
Expert-Level Analysis: Spec-Driven Development and AI Fidelity
The reliance on Spec-Driven Development (SDD) is noteworthy. SDD, when used correctly, ensures that the final product adheres precisely to the defined requirements. When an AI model handles the translation from high-level specification (the "spec") to low-level implementation (the code), the result is often highly consistent and structurally sound, provided the initial specification was robust.
In VoidLink’s case, the AI was tasked with creating components necessary for modern cloud infiltration: loaders for initial execution persistence, rootkit modules for hiding activity from kernel-level inspection tools, and a plugin architecture for extensibility. These are not trivial tasks; they require deep knowledge of memory management, operating system internals, and hypervisor interaction in cloud contexts. The fact that the AI produced code robust enough to reach functional status in under a week suggests that the underlying LLM has been extensively trained on high-quality, complex, offensive codebases.
The presence of developer guidance files alongside the source code is arguably more valuable than the code itself for analysis. These files reveal the intent and the assumptions the developer fed the model. For instance, if the guidance included specific directives on evading known EDR/XDR solutions prevalent in major cloud providers, security architects gain immediate insight into the threat actor’s current evasion priorities.
The speed metric—functional in a week versus a projected 16-30 weeks—highlights the AI’s role as an unprecedented efficiency multiplier. The human role effectively transitions from coder to architect and quality assurance manager. The developer sets the high-level goals, validates the AI’s generated architectural plans, and then approves the execution of the code generation sprints. This paradigm drastically increases the throughput of sophisticated offensive engineering.
Future Impact and Trends: Escalation and Countermeasures
The implications for future cyber conflict are stark. We are moving toward an era where the scarcity of offensive capability shifts from coding skill to access to cutting-edge AI tools and the ability to craft superior specifications.
.jpg)
1. Proliferation of High-Quality Threats: We anticipate a rapid increase in the volume and quality of malware targeting specific niches, such as proprietary APIs, zero-day exploitation chains, or highly customized cloud configurations, because the cost and time to develop such bespoke tools have plummeted.
2. The Rise of "AI vs. AI" Defense: Defensive security firms must accelerate their own adoption of generative AI, not just for threat detection (which they already do), but for automated vulnerability discovery and defensive patch generation. If attackers use AI to write malware in days, defenders must use AI to write detection signatures and exploit mitigations in hours.
3. Focus on Prompt Engineering Security: Security teams will need to implement rigorous internal controls and auditing around how employees interact with AI coding assistants, especially when developing security tools or internal infrastructure code. The "TRAE SOLO" incident demonstrates that the input prompts and the resulting development artifacts can become significant security liabilities if exposed. Guardrails must be established to prevent sensitive intellectual property or development plans from being inadvertently shared with the AI environment or being saved to insecure locations susceptible to accidental exposure.
4. Evasion Tactics Evolution: Future malware frameworks will likely incorporate anti-AI detection mechanisms, actively trying to obfuscate their structure to appear more "human" or deliberately injecting subtle, non-functional errors to confuse automated analysis tools trained on the patterns observed in VoidLink.
VoidLink is more than just a new piece of malware; it is a proof-of-concept for the next generation of cyber warfare. It confirms that the era where complex offensive tooling required large, well-funded teams is ending. The new paradigm favors the technically proficient individual leveraging autonomous development agents, demanding an immediate and fundamental reassessment of defensive postures across the global digital infrastructure. The speed and sophistication achieved by VoidLink serve as an early, unmistakable warning signal that the threat landscape is about to accelerate dramatically.

