The cybersecurity landscape has recently been punctuated by the discovery of a sophisticated new threat actor tool, dubbed PDFSider, which was successfully deployed within the network infrastructure of a major Fortune 100 corporation operating in the highly regulated finance sector. This incident underscores a worrying trend where advanced persistent threat (APT) methodologies are being adopted and weaponized by financially motivated ransomware syndicates, blurring the lines between cyber-espionage and criminal extortion. The detection of PDFSider during a critical incident response engagement, flagged by security firm Resecurity, reveals a meticulously crafted backdoor designed for sustained, covert access, exhibiting operational characteristics deeply rooted in state-sponsored threat actor tradecraft.
The initial vector of compromise against the financial giant involved classic, yet highly effective, social engineering tactics. Threat actors managed to establish initial remote access by impersonating IT support personnel. This human-centric attack successfully coerced employees into downloading and executing legitimate remote access software—specifically, Microsoft’s Quick Assist tool. While Quick Assist is a benign utility intended for legitimate troubleshooting, its deployment in this context served as the crucial pivot point, establishing a trusted pathway for the subsequent deployment of the PDFSider payload. This reliance on social engineering highlights that even the most technically advanced defensive postures remain vulnerable to exploitation at the human layer, especially when combined with sophisticated malware delivery.
PDFSider is not an isolated incident; researchers confirm its linkage to recent operations involving the Qilin ransomware strain. More alarmingly, threat intelligence suggests that this specific backdoor is rapidly gaining traction, being "actively used" by a growing consortium of ransomware operators looking to secure footholds before launching final-stage payloads. This proliferation suggests the backdoor is either being sold on underground forums or shared among established criminal collectives, standardizing a high-efficacy infiltration mechanism across various campaigns.

The Art of Deception: DLL Sideloading Mastery
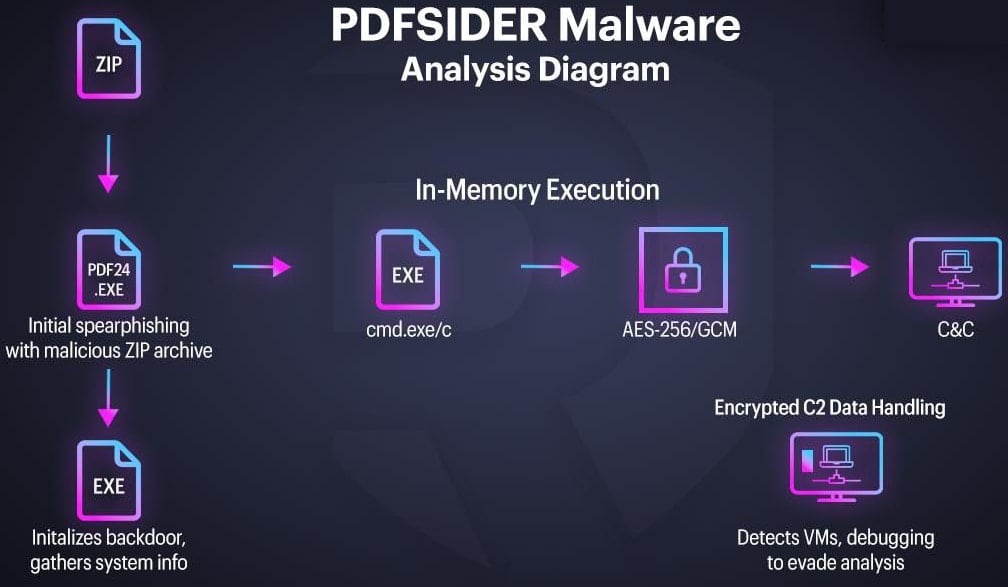
The technical brilliance of the PDFSider attack lies in its delivery mechanism, which expertly leverages the concept of DLL (Dynamic Link Library) sideloading to evade standard security monitoring. The infection package, typically distributed via spearphishing emails, contains a ZIP archive. Inside this archive resides a legitimate, digitally signed executable file associated with the PDF24 Creator tool, produced by Miron Geek Software GmbH. This use of a genuine, signed binary is a classic technique designed to appear trustworthy to endpoint detection and response (EDR) systems, which often flag unsigned executables or anomalous process chains.
However, embedded within this seemingly innocuous package is a maliciously crafted Dynamic Link Library file, specifically masquerading as cryptbase.dll. This DLL is the core component of the backdoor. When the legitimate PDF24 executable runs, it possesses a dependency on certain DLLs to function correctly. Due to inherent design flaws or vulnerabilities within the PDF24 software itself—a vulnerability analysts note is becoming distressingly common across widely used commercial software—the application loads the attacker’s malicious cryptbase.dll instead of the expected system file, or loads it in a way that grants the malicious code precedence. This process, DLL sideloading, grants the attacker’s code execution rights commensurate with the privileges of the legitimate, signed executable that invoked it, effectively bypassing immediate security scrutiny.
As Resecurity noted, the key vulnerability lies in the interplay between the legitimate signature and the exploitability of the hosting application. Cybercriminals are becoming increasingly adept at weaponizing minor flaws in trusted software dependencies to cloak their malware. Furthermore, researchers speculate that the advent of generative AI tools is accelerating the discovery and weaponization of such software vulnerabilities, making it easier for threat actors to quickly identify and package exploitation chains that were previously the domain of highly skilled, dedicated vulnerability researchers.
In some observed attack variations, the threat actors refined their spearphishing approach by using highly tailored decoy documents, sometimes even falsely attributing the authorship to a known entity, such as a Chinese government body, to increase the likelihood of the target opening the file. Once executed, the malicious DLL assumes control, running with the host process privileges.

Operational Stealth and Command Execution
PDFSider is engineered for extreme stealth. A critical feature of its operation is its memory-resident nature. Upon successful loading via DLL sideloading, the malware executes directly into the system’s Random Access Memory (RAM), leaving behind minimal persistent artifacts on the disk. This "fileless" characteristic significantly complicates forensic analysis and eradication efforts, as traditional file-scanning antivirus solutions often miss in-memory threats.
Command and control (C2) communications are orchestrated using anonymous pipes, a low-level Windows mechanism, to launch arbitrary commands through the Command Prompt (CMD). This abstraction allows the malware to perform system reconnaissance and execute further stages of the attack chain without generating easily traceable process execution logs associated with direct scripting engines or known malware beacons.
Upon initial compromise, the infected Windows host is assigned a unique identifier. The malware then meticulously gathers system information—details critical for tailoring subsequent attacks or confirming the value of the target environment. This exfiltrated telemetry is then transmitted back to the attacker’s Command and Control infrastructure, often hosted on compromised Virtual Private Servers (VPS), utilizing DNS tunneling over port 53. DNS exfiltration is a favored technique for sophisticated actors because port 53 traffic is rarely subjected to the deep packet inspection applied to standard HTTP or TCP connections, allowing data to leak out relatively unnoticed.
Advanced Cryptography and Evasion Techniques
What elevates PDFSider beyond typical commodity malware is its robust implementation of encryption for C2 communications. The malware leverages the Botan 3.0.0 cryptographic library, employing AES-256-GCM (Galois/Counter Mode) for data encryption. This is a high-standard symmetric encryption algorithm known for both its speed and its strong security guarantees.
Crucially, the implementation includes Authenticated Encryption with Associated Data (AEAD) in GCM mode. This ensures not only the confidentiality (encryption) of the data exchanged but also its integrity and authenticity. As Resecurity analysts point out, this level of cryptographic rigor is strongly indicative of malware designed for targeted, long-term operations where maintaining the secrecy and integrity of communication with the operator is paramount—a hallmark of APT activity. The decryption of incoming data occurs exclusively within volatile memory, further minimizing the forensic footprint on the compromised machine.
To ensure its longevity and evade automated analysis, PDFSider is equipped with several anti-analysis measures. These include checks on the available RAM size and the presence of common debugging tools or sandboxing environments. If the malware detects that it is being analyzed in a controlled laboratory setting—a sandbox—it is programmed to terminate execution immediately, presenting a benign profile to automated security scanners.
Industry Implications: The Blurring Lines of Cybercrime
The deployment of PDFSider within a Fortune 100 financial entity sends a powerful signal across the industry. Firstly, it confirms the maturation of ransomware groups, which are increasingly investing in bespoke, APT-grade tooling rather than relying solely on off-the-shelf exploit kits. The convergence of financially motivated ransomware with espionage-level tradecraft suggests a strategic shift: the goal is no longer just rapid financial gain via encryption, but potentially deep intelligence gathering, supply chain disruption, or long-term espionage, with ransomware serving as a potent smokescreen or a secondary monetization route.
For the financial sector, which handles some of the world’s most sensitive data and operates under intense regulatory scrutiny, this threat profile demands a fundamental reassessment of perimeter defenses. Traditional reliance on signature-based detection or even standard behavioral analysis is proving insufficient against malware that resides primarily in memory and employs legitimate software for initial execution.
Future Impact and Defensive Posture
The long-term impact of PDFSider and similar threats hinges on defensive adaptation. Organizations must move aggressively beyond traditional endpoint protection toward advanced threat hunting centered on process behavior and memory forensics. Specifically, security teams need to:
- Harden Third-Party Software Deployment: Implement strict controls over software execution environments, especially for tools that manage remote access (like Quick Assist) or handle file processing (like PDF readers). Policies should enforce the use of application whitelisting where feasible.
- Monitor for DLL Side-Loading Anomalies: Invest in advanced EDR capabilities that specialize in detecting when a signed executable loads an unsigned or suspicious DLL from an unexpected location, or when a legitimate application loads a dependency that communicates externally using sophisticated encryption.
- Enhance DNS Traffic Analysis: Given the use of DNS tunneling for exfiltration, network monitoring solutions must be capable of analyzing the entropy and frequency of DNS queries originating from endpoints to detect anomalous data leakage.
- Elevate Social Engineering Defenses: Continuous, realistic training for employees on recognizing impersonation tactics related to IT support or vendor requests remains a non-negotiable baseline defense against the initial access phase of attacks like this.
Resecurity’s assessment that PDFSider leans toward "espionage tradecraft" rather than purely financially driven malware suggests a future where sophisticated persistent access is the primary objective, allowing threat actors to observe, map, and potentially manipulate high-value targets over extended periods before deploying a disruptive final action. This transition necessitates a security architecture built not just to block known threats, but to detect the subtle, long-term presence of advanced persistent compromise. The PDFSider case serves as a stark reminder that the arms race in cybersecurity is increasingly being fought on the battleground of operational stealth and cryptographic sophistication.

