The digital asset custody landscape has been sharply reminded of its inherent vulnerabilities following a sophisticated breach targeting Trust Wallet’s browser extension just before the holiday period. Initial assessments confirm that the exploit, which materialized via a compromised extension update, resulted in the draining of approximately $7 million worth of digital currencies from a staggering 2,596 individual cryptocurrency wallet addresses. This incident underscores a critical friction point in the decentralized finance (DeFi) ecosystem: the security reliance placed upon user-facing software interfaces, even those associated with major industry players.
Trust Wallet, a widely adopted non-custodial solution boasting an active user base exceeding 200 million, serves as a vital gateway for managing diverse crypto assets, including Bitcoin, Ethereum, Solana, and thousands of associated tokens. Its utility spans across dedicated iOS and Android mobile applications, complemented by the scrutinized browser extension. Established in 2017 and subsequently integrated into the Binance ecosystem the following year, Trust Wallet maintains an operational facade of independence as a decentralized application, a crucial distinction in security discourse, as it theoretically places asset control solely with the user.
The genesis of the crisis was traced to version 2.68.0 of the Chrome browser extension. Reports indicate that this specific build contained a malicious JavaScript payload designed for data exfiltration. Upon installation or update, this code silently harvested sensitive wallet credentials, leading directly to the subsequent asset withdrawals. Trust Wallet’s confirmation of the breach followed external inquiry, prompting an immediate security advisory urging users to transition to version 2.69, which was swiftly deployed to neutralize the ongoing threat vector.
The Anatomy of the Supply Chain Breach
Analysis provided by CEO Eowyn Chen pointed toward a highly targeted breach of the software distribution pipeline rather than a flaw within the core application logic itself. Chen articulated a compelling, albeit alarming, hypothesis: the attackers did not exploit a vulnerability in Trust Wallet’s internal testing or release framework but rather gained unauthorized access to the platform’s API credentials for the Chrome Web Store.

"The malicious extension v2.68 was NOT released through our internal manual process," Chen stated, suggesting a bypass of established security protocols. The working theory posits that a leaked or compromised Chrome Web Store API key was leveraged to submit the compromised version. Critically, this malicious package successfully navigated the standard review processes implemented by the extension marketplace, leading to its official release on December 24, 2025, at 12:32 UTC. This detail elevates the severity, implying a potential weakness in the third-party platform’s vetting procedures, or a highly sophisticated method of obfuscation employed by the threat actors.
In immediate remediation steps, Trust Wallet took decisive action to regain control over its distribution channels. The company unilaterally revoked all active release APIs, effectively instituting a two-week moratorium on any new extension versions pushed via automated means. Simultaneously, defensive measures targeted the attacker’s command-and-control infrastructure. The malicious domain used for data exfiltration was reported to the domain registrar, NiceNIC, resulting in its prompt suspension, thereby severing the primary channel for continued credential harvesting from users who had not yet updated.
The Second Wave: Exploiting Panic with Phishing
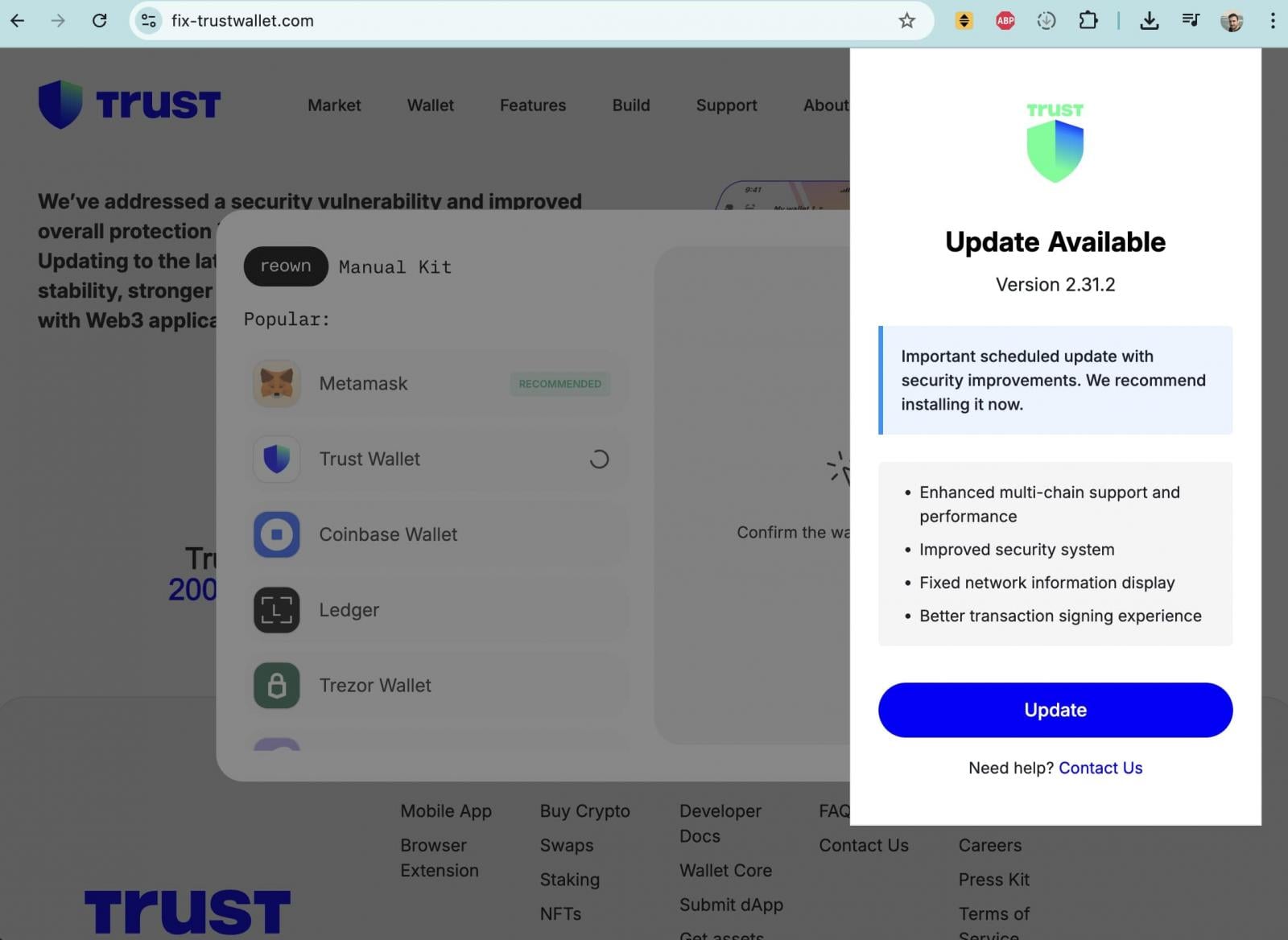
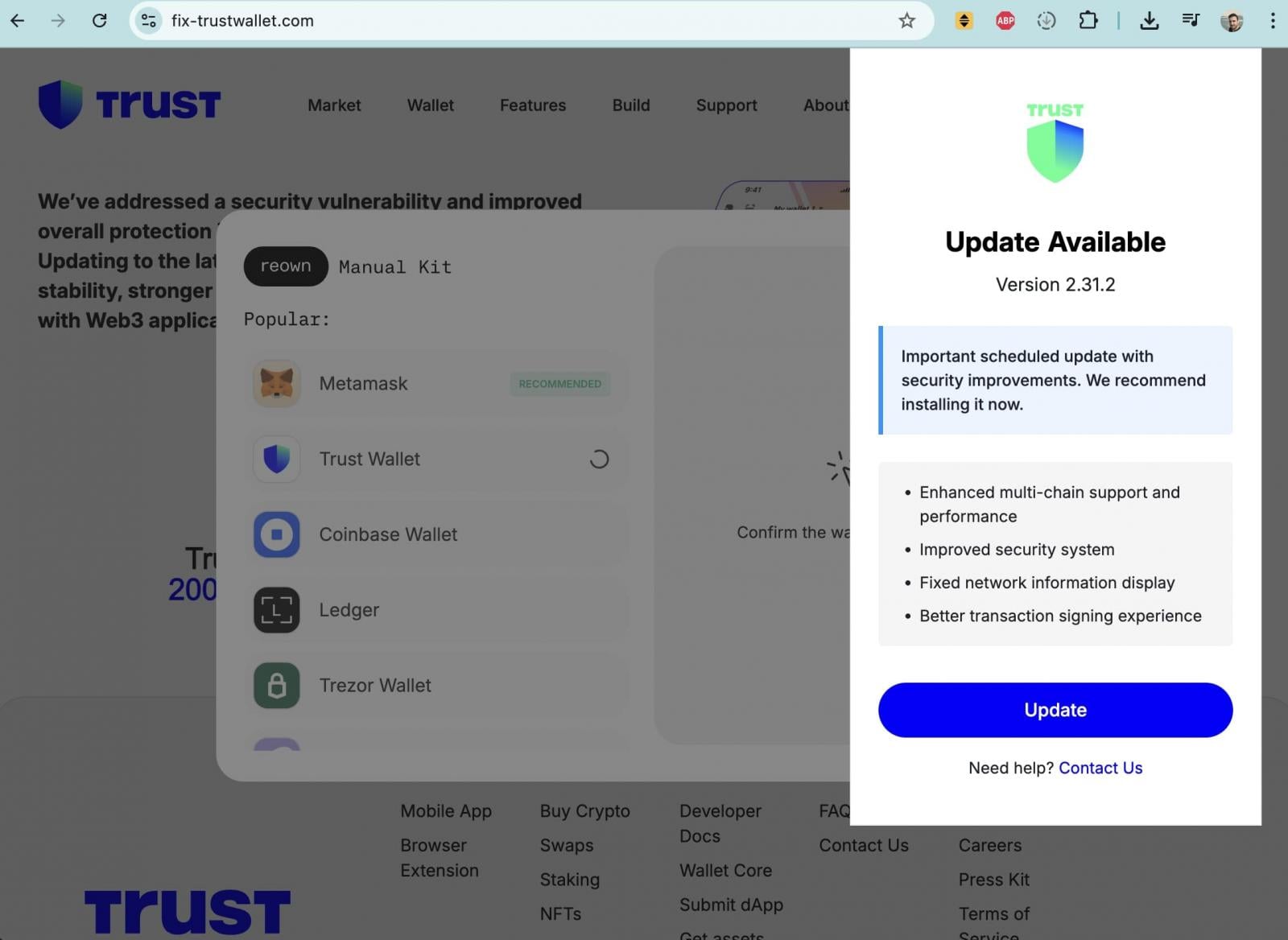
The security breach quickly catalyzed a secondary, highly opportunistic threat: a widespread phishing campaign capitalizing on user anxiety. Following the initial disclosure, threat actors initiated aggressive social engineering efforts, deploying Trust Wallet-branded websites and communications designed to look entirely legitimate. These deceptive sites solicited users to input their critical wallet recovery seed phrases under the guise of needing an "important scheduled update with security improvements."
This tactic is a classic example of exploiting the "fix-it" reflex in cybersecurity incidents. When users are aware of a breach but lack immediate clarity on mitigation, they become susceptible to urgent requests for information that promise a resolution. The existence of a documented malicious domain, fix-trustwallet[.]com, exemplified this predatory behavior, illustrating the attackers’ agility in pivoting from a software supply chain attack to a direct social engineering offensive.
Quantifying the Damage and Compensation Protocols
As the immediate technical threat was contained, Trust Wallet shifted focus to forensic accounting and victim restitution. The final tally confirmed that assets were stolen from 2,596 distinct wallet addresses, aggregating to the aforementioned $7 million loss. CEO Chen later provided an update detailing the complexities of the claims verification process.

The verification challenge was compounded by an influx of suspicious submissions. Chen noted that approximately 5,000 claims had been filed against the identified 2,596 affected addresses. This disparity strongly suggested a significant volume of fraudulent or duplicate claims attempting to exploit the reimbursement program. This reality necessitates a rigorous, multi-layered verification process to differentiate legitimate victims from malicious actors attempting to divert restitution funds.
To manage this, Trust Wallet established a dedicated portal for affected users to submit essential forensic data: contact information, the compromised wallet address, the address receiving the stolen funds (the hacker’s address), and the specific transaction hashes associated with the drain. Crucially, the company maintained a strict policy warning against the submission of any private keys, seed phrases, or passwords—the very data the initial exploit sought to steal. The compensation process, managed through the be-support.trustwallet.com portal, involves intensive cross-referencing of data points to establish irrefutable ownership. Trust Wallet issued a public apology, acknowledging the "frustrating and disruptive" nature of the incident while committing resources to expedite the verification and compensation timeline.
Industry Implications: Decentralization vs. Distribution Security
This event sends a potent signal across the broader cryptocurrency industry, particularly concerning the security architecture of non-custodial wallets that rely on browser extensions. While Trust Wallet is decentralized in custody—meaning assets are not held by Binance—its distribution mechanism, relying on centralized app stores (like the Chrome Web Store), introduces a single point of failure that mirrors traditional centralized software vulnerabilities.
Expert Analysis on Distribution Security: Security architects often point out that the "decentralized" nature of a wallet pertains to asset control, not software delivery. If the delivery mechanism (the extension marketplace) is compromised, the security benefit of self-custody is temporarily negated during the period the malicious software is active on the user’s endpoint. This incident highlights the critical need for stricter continuous auditing protocols, perhaps utilizing cryptographic proofs of integrity embedded directly within the software update mechanism, verifiable client-side, rather than solely relying on the platform store’s vetting layer.
The compromise of the API key suggests a failure in credential management at the development or distribution interface. For a project with such significant user volume, the practice of using API keys with broad publishing permissions warrants intense scrutiny. Industry best practices now strongly advocate for "least privilege" access for distribution tokens, employing multi-factor authentication (MFA) on all deployment pipelines, and implementing "break-glass" procedures that mandate manual, out-of-band verification for any significant update release.
Future Impact and Emerging Trends in Wallet Security
The fallout from this $7 million theft will likely accelerate several crucial trends in digital asset security:
- Hardware Integration Push: There will be an increased user migration toward hardware wallets (e.g., Ledger, Trezor) for storing significant balances, as these devices physically isolate private keys from internet-connected environments, rendering extension-based malware ineffective for immediate asset drainage. Non-custodial software wallets may see their primary utility shift towards smaller, transactional balances.
- Enhanced Wallet Integrity Checks: Wallet providers will likely implement more robust, proactive integrity checks at launch and during routine operations. This could involve checking cryptographic hashes against a known-good manifest stored on a separate, immutable ledger (like a specific blockchain), allowing the client application to flag potential tampering even if the extension store mistakenly approved a malicious build.
- Heightened Vigilance Against Post-Incident Scams: The rapid deployment of secondary phishing campaigns underscores that the period immediately following a major breach is the most dangerous for users. Security advisories must now explicitly detail the expected fraudulent activities, educating users not just on what to avoid (sharing seeds) but also on what to expect (impersonation, fake compensation forms). The use of platform-specific social media ads (like Telegram) to push these scams is a growing vector that requires dedicated countermeasures from the affected companies.
- Regulatory Scrutiny on Distribution: While decentralized wallets operate in a grey area concerning direct financial regulation, the reliance on centralized distribution points like the Chrome Web Store places them partially under the purview of those platform owners. Regulators and consumer protection agencies may begin to scrutinize the security standards required for crypto-related extensions published on these major software marketplaces.
The Trust Wallet incident serves as a sobering case study in the fragility of software supply chains within the crypto ecosystem. Even with decentralized custody, the point of software delivery remains a critical vulnerability, capable of undermining user trust and causing massive financial losses when exploited by determined threat actors. The swift commitment to reimbursement demonstrates corporate responsibility, but the technical lesson—that API key management is as critical as smart contract auditing—will resonate throughout the development community for the foreseeable future.