A sophisticated cyber-espionage campaign leveraging seemingly innocuous Google Chrome extensions has been unearthed, specifically designed to compromise the security posture of organizations reliant on leading enterprise Human Resources (HR) and Enterprise Resource Planning (ERP) platforms. Security researchers have identified a cluster of five malicious browser add-ons, collectively installed by over 2,300 users, that perform a triad of dangerous actions: stealing active session cookies, manipulating the Document Object Model (DOM) to obstruct security controls, and actively injecting session tokens for direct account takeover.
The discovery, meticulously documented by the cybersecurity firm Socket, highlights the persistent danger posed by third-party extensions operating within the highly privileged environment of a user’s browser. These extensions specifically targeted dominant industry solutions, including Workday, NetSuite, and SAP SuccessFactors—platforms that manage the most sensitive employee data, payroll information, and core business operations. The implications extend far beyond simple credential theft; this campaign represents a direct assault on the operational integrity and data confidentiality housed within these critical systems.
Socket’s analysis reveals a tightly coordinated operation despite the facade of disparate publishers. The researchers noted shared characteristics across the identified extensions, including identical targeting criteria for major enterprise platforms, matching lists of security tools they were programmed to detect, and remarkably similar API endpoint patterns and underlying code structures. This uniformity strongly suggests a centralized command structure orchestrating the deployment, even though the extensions were released under varying aliases. Four of the five malicious tools were attributed to a developer handle named ‘databycloud1104,’ while the fifth operated under the moniker ‘Software Access,’ utilizing slightly different branding to evade immediate detection.
The Anatomy of the Attack: Three Malicious Modalities
The core danger of this campaign lies in the multifaceted approach to exploitation. Unlike simpler phishing attempts, these extensions operate covertly within the user’s active session, bypassing many conventional perimeter defenses.
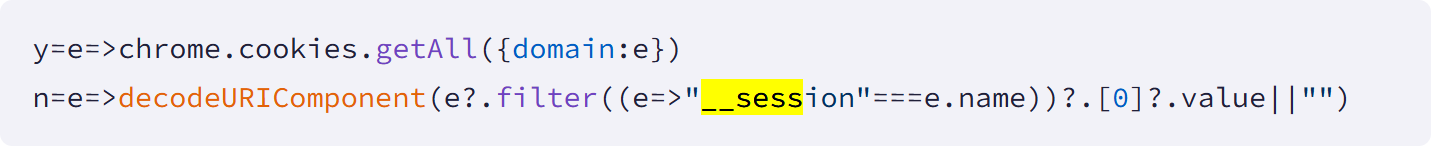
Firstly, the extensions executed persistent **cookie exfiltration**. Multiple add-ons were programmed to continuously search for and extract authentication cookies, specifically those named “__session,” associated with the targeted Workday, NetSuite, and SuccessFactors domains. These cookies represent the active, authenticated state of the user. Crucially, this extraction occurred with alarming frequency—every 60 seconds—and the harvested tokens were transmitted back to remote Command and Control (C2) servers. This continuous exfiltration ensured that attackers could potentially hijack a session even after the legitimate user had performed a routine re-login, as the compromised session cookie might remain valid for a short window.
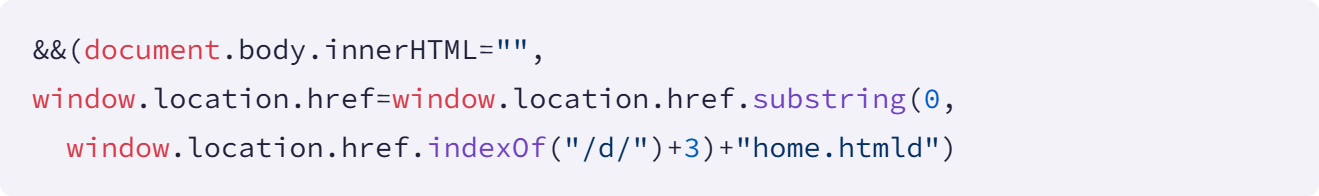
Secondly, and perhaps most insidious in its operational impact, was the technique of **DOM manipulation to block security administration pages**. Two of the more widely deployed extensions, ‘Data By Cloud 2’ (installed approximately 1,000 times) and ‘Tool Access 11,’ employed page title detection mechanisms. Upon loading sensitive administrative interfaces within Workday, these extensions would either entirely scrub the content of the page or actively redirect the administrator away from critical management views. Socket detailed the scope of this blockage: ‘Tool Access 11’ targeted 44 specific administrative pages covering core security functions like authentication policy configuration, security proxy settings, IP range management, and session control parameters. ‘Data By Cloud 2’ extended this obstruction to 56 pages, adding controls related to password management, account deactivation routines, Two-Factor Authentication (2FA) device oversight, and security audit log review.
The strategic implication of this page blocking is profound. If an organization detects an intrusion or suspicious activity within their HR or ERP system, the designated security personnel or administrators might find themselves functionally blind or unable to enact immediate mitigation steps, such as revoking sessions or isolating compromised accounts, thereby creating a critical window for data exfiltration or further system compromise.

The third and most severe vector, utilized by the ‘Software Access’ extension, involved **bidirectional cookie injection for direct session hijacking**. This capability elevates the threat from passive data theft to active system takeover. Not only could this extension steal active session tokens, but it could also receive pre-stolen or newly generated cookies from the attacker’s C2 infrastructure and inject them directly into the victim’s browser session. This technique circumvents the need for the attacker to know any credentials (username, password, or MFA code), granting them immediate, seamless access to the targeted enterprise account with the full privileges of the compromised user.
Marketing Deception: The Lure of Productivity
The success of this campaign relied heavily on social engineering, specifically targeting employees tasked with managing large, complex enterprise applications. The extensions were marketed aggressively on the Chrome Web Store not as surveillance tools, but as legitimate enhancements designed to streamline often cumbersome workflows within Workday, NetSuite, and SuccessFactors.
For example, ‘Data By Cloud 2’ presented itself as a productivity dashboard offering bulk management capabilities and expedited access for power users managing numerous enterprise accounts—a common necessity in large organizations. Meanwhile, ‘Tool Access 11’ adopted a deceptive security posture, claiming to *restrict* user interaction with “special tools” to prevent accidental compromise. This inverted marketing strategy—selling a security feature that was actually a backdoor—is a particularly cynical layer to the attack.
Crucially, none of the extensions transparently disclosed their actual capabilities in their listings or privacy policies. The requested browser permissions, while broad, appeared consistent with the claimed integration functionalities, further lulling unsuspecting users into granting the necessary access for the malicious code to execute.
Industry Implications and Expert Analysis
The deployment of these extensions against HR and ERP systems carries significant weight within the cybersecurity landscape. These platforms are the crown jewels of organizational data. Compromise of Workday, for instance, can lead to immediate financial fraud via payroll manipulation, exposure of executive compensation data, or widespread theft of personally identifiable information (PII) related to the entire employee base.
From an expert perspective, this campaign exemplifies the ongoing failure of the “zero-trust” model to adequately account for the endpoint environment of web applications. While network segmentation and strong identity controls are paramount, they often break down when the user’s own browser, acting as the final access gateway, is compromised by a trusted, yet malicious, application layer component.
The coordinated nature of the attack—sharing code signatures and C2 infrastructure—suggests a professional threat actor, potentially a well-resourced criminal syndicate or a state-sponsored entity focused on corporate espionage or large-scale financial disruption. The relatively small user count (2,300 installs) suggests a highly focused, targeted initial deployment, perhaps a proof-of-concept or a spear-phishing attempt aimed at high-value targets within specific organizations before a broader rollout.
The ability to hijack sessions without credentials is a significant development in browser-based attacks. Traditional security models rely on the integrity of the login flow (username/password/MFA). By compromising the active session token (the cookie), the attacker effectively steps into the shoes of the authenticated user, rendering MFA useless for that session duration. This tactic is notoriously difficult to detect post-factum unless advanced session monitoring or User and Entity Behavior Analytics (UEBA) tools are in place to flag anomalous actions following a session takeover.
The Future of Extension Security and Mitigation Strategies
The immediate aftermath requires swift action. Socket’s swift reporting to Google resulted in the removal of the identified extensions, a necessary but reactive step. For any organization that used these add-ons, immediate incident response protocols must be initiated. This includes mandatory password resets for all affected accounts on Workday, NetSuite, and SuccessFactors, and comprehensive forensic analysis by security teams to determine the extent of data exposure or manipulation.
Looking forward, this incident underscores several critical trends in enterprise security architecture:
- Enhanced Browser Security Posture: Organizations must move beyond simply blocking known malicious extensions. A Zero Trust approach must be extended to the browser itself, perhaps through hardened browser configurations, application whitelisting for extensions, or utilizing virtualized browser environments for accessing critical applications.
- Session Monitoring Maturity: Relying solely on perimeter authentication is insufficient. Robust UEBA tooling must monitor session behavior *after* authentication. Anomalies such as rapid data download spikes, configuration changes initiated at odd hours, or rapid traversal between sensitive security pages should trigger immediate alerts or session termination.
- Policy Transparency Enforcement: Google and other platform providers face increasing pressure to enforce stricter vetting for extensions requesting broad access permissions, especially those targeting high-value enterprise APIs. The deceptive marketing tactics seen here require behavioral analysis, not just static code review, during the vetting process.
- The Supply Chain of Trust: This highlights that the “software supply chain” risk now extends directly into the end-user application layer. IT and security leadership must mandate rigorous third-party risk assessments for any browser add-on used by employees accessing sensitive corporate resources, regardless of how benign the tool appears.
The campaign targeting HR and ERP platforms via Chrome extensions serves as a sharp reminder that the perimeter of the enterprise network is no longer defined by firewalls, but by the weakest link in the user’s software chain. As enterprise platforms become increasingly web-native and reliant on user-level context, the browser extension will remain a prime, low-cost, high-impact vector for sophisticated attackers seeking direct access to core business functions.