The digital ecosystem surrounding WordPress, the world’s most dominant content management system (CMS), is constantly under siege by threat actors seeking vulnerabilities that offer a fast track to administrative control. A significant security incident has recently emerged concerning the Modular DS WordPress plugin, a powerful tool designed for centralized management across numerous WordPress installations. Security researchers have confirmed active exploitation of a critical vulnerability—officially cataloged as CVE-2026-23550—that allows unauthenticated remote attackers to escalate privileges directly to full administrator access on vulnerable sites. This situation underscores a perennial challenge in the open-source ecosystem: the tension between feature-rich centralization and maintaining a hardened security posture across thousands of dependent environments.
Modular DS, installed on over 40,000 websites, is designed to streamline operations for site owners, developers, and hosting providers. Its utility lies in enabling remote monitoring, centralized user management, software updates across a network of sites, server information retrieval, and maintenance execution—all from a single dashboard. This high degree of access and connectivity, while operationally efficient, inherently increases the potential blast radius should a flaw be discovered and exploited.
The timeline of the breach highlights the alarming speed at which sophisticated threats can move from discovery to active weaponization. Security firm Patchstack identified the initial signs of exploitation on January 13th, around 02:00 UTC. Following rapid confirmation of the vulnerability, researchers proactively engaged the vendor. Remarkably, the Modular DS development team responded with swift decisiveness, releasing a mitigating patch—version 2.5.2—just hours later. This rapid response cycle is commendable, but the initial window of compromise remains a significant concern for the installed base.
Deconstructing the Vulnerability: A Flaw in Trust Verification
The root cause of CVE-2026-23550 lies in a fundamental lapse within the plugin’s architecture concerning request validation, specifically when operating in "direct request" mode. In this mode, intended for trusted internal communication or specific administrative channels, the plugin exhibited a critical failure: it accepted incoming requests as inherently trustworthy without enforcing requisite cryptographic checks to verify the request’s origin. This lack of origin validation effectively opened several sensitive API endpoints to the public internet.
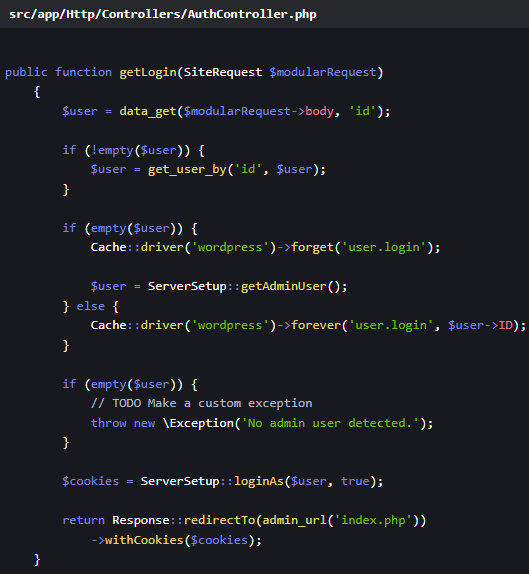
The most devastating consequence of this design oversight was the activation of an automatic administrative login fallback mechanism. According to the technical analysis provided by Patchstack, the application logic within the authentication controller (src/app/Http/Controllers/AuthController.php, specifically the getLogin method) was designed to attempt reading a User ID directly from the incoming request body ($modularRequest).

The critical flaw materialized when no specific User ID was supplied by the attacker. Instead of rejecting the request or falling back to a secure default, the code defaulted to fetching an existing administrator or super administrator account from the database and immediately logging in as that user. This represents a textbook case of insecure direct object reference (IDOR) leading directly to unauthorized authentication and maximum privilege escalation. As Patchstack summarized, because this path was accessible to unauthenticated users due to the flawed trust mechanism, it enabled an immediate, trivial privilege escalation.
The exposed logic is graphically illustrated by the fallback sequence: an attacker simply needs to send a request to the vulnerable endpoint, omit the desired user ID, and the plugin, in its misguided attempt to be helpful, grants them the highest level of site access. For administrators managing dozens or hundreds of sites through this centralized hub, the implications are catastrophic: a single compromised instance via this vulnerability potentially grants control over the entire managed network.
Industry Implications and the Centralization Risk
This incident serves as a stark warning regarding the security architecture of centralized management tools. While solutions like Modular DS offer substantial benefits in scalability and efficiency—reducing the manual overhead of patching, configuration, and monitoring across a large fleet of WordPress sites—they simultaneously create a single point of failure with an outsized impact.
For Managed Service Providers (MSPs) and large digital agencies that rely on such plugins to maintain service level agreements (SLAs) for numerous clients, the compromise of the management layer is an existential threat. A successful exploit doesn’t just mean one client site is breached; it means the keys to the entire kingdom, the central administrative credentials for all connected sites, are potentially exposed or leveraged. This elevates the severity far beyond a typical plugin vulnerability, moving it into the realm of supply chain risk management for the hosting provider itself.
The scale of the affected base—40,000 installations—ensures that threat actors, particularly those engaged in automated vulnerability scanning and mass exploitation campaigns, would immediately target this flaw. The fact that exploitation was confirmed within hours of the vulnerability’s disclosure underscores the reality of the "zero-day to N-day" lifecycle in the modern threat landscape; attackers are faster and more automated than ever before.
Expert Analysis: Architectural Failures in Trust Boundaries
From a deep technical security perspective, CVE-2026-23550 exposes a fundamental misunderstanding or misimplementation of security trust boundaries within the plugin’s framework. In modern application security, especially within APIs or remote management interfaces, trust must be explicitly established and continuously verified.

The "direct request" mode suggests a mechanism intended for internal communication, possibly bypassing standard WordPress authentication checks for efficiency. However, when such a mode interacts with external HTTP requests without a robust, cryptographically secure token, signature, or nonce verification, it effectively dissolves the application’s security perimeter. The lack of an origin check suggests the developers relied implicitly on network segmentation or configuration settings that were simply absent or bypassed in the public-facing context.
The fallback mechanism is particularly egregious from a security engineering standpoint. Security protocols must adhere to the principle of least privilege and "fail securely." When an expected input (a specific User ID) is missing, the system should fail closed—returning an error, denying access, or defaulting to the lowest possible privilege level—rather than defaulting to the highest possible privilege (admin login). This design choice indicates a priority given to functionality and user experience over security hardening, a common pitfall in rapidly developed or feature-heavy plugins.
The Remediation Landscape and Post-Exploitation Cleanup
The swift patch to version 2.5.2 addressed the core issue by dismantling the dangerous route matching logic. The fix implemented several crucial security enhancements:
- Removal of URL-based Route Matching: Moving away from easily manipulated URLs for routing sensitive functions eliminates a major avenue for path traversal or unauthorized endpoint access.
- Validated Filter Logic: The new logic is reportedly driven entirely by validated filter mechanisms, suggesting a stricter adherence to expected input parameters rather than relying on request structure.
- Default 404 Route: Implementing a catch-all route ensures that unrecognized or malformed requests are explicitly rejected, improving the overall robustness against fuzzing and probing.
- Safe Failure Mode: Crucially, the system now handles unrecognized requests safely, preventing the automatic fallback to administrative sessions.
While upgrading is paramount, the vendor’s supplementary advice is critical for any site that may have been compromised between January 13th and the time of patching. The advice to review server access logs for anomalous traffic targeting authentication endpoints is essential for incident response. More importantly, checking for the addition of rogue administrator accounts is necessary because an attacker who gains admin access can easily create a persistent backdoor user before logging out.
The final recommendation—regenerating all WordPress salts (authentication keys, security keys, and secret keys)—is a non-negotiable step for any potentially compromised WordPress installation. Salts are foundational to session security; if an attacker managed to steal session cookies or tokens before the patch, regenerating these keys invalidates all existing sessions and tokens, effectively locking out unauthorized actors who relied on stolen credentials.
Future Impact and Trends in Plugin Security
This incident is not isolated; it is symptomatic of broader trends shaping the WordPress security landscape. As the platform continues to host increasingly complex business operations, plugins are evolving into miniature SaaS applications embedded within the CMS structure. This complexity introduces more sophisticated attack surfaces, often involving custom authentication, external API calls, and internal service communication protocols—all of which require expert-level security scrutiny.
The future of WordPress security will increasingly rely on automated static and dynamic analysis tools capable of detecting insecure trust assumptions, such as those seen in Modular DS’s "direct request" mode. Developers must adopt security-by-design principles, treating every internal communication path as potentially exposed externally unless proven otherwise via rigorous cryptographic verification.
Furthermore, the reliance on centralized management tools necessitates enhanced auditing and logging features built directly into these plugins. Administrators need real-time alerts not just when a plugin update fails, but when internal endpoints exhibit unusual traffic patterns, especially those related to authentication processing without valid session tokens.
For the tens of thousands of organizations using Modular DS, this event must serve as a catalyst for immediate action: update to 2.5.2 or higher immediately, perform the recommended post-patch audit, and fundamentally reassess the security posture of any centralized management tool in use. The speed of the fix demonstrates vendor accountability, but the speed of the exploit demonstrates attacker proficiency. In the ongoing digital arms race, vigilance remains the most critical defense.

