
The intricate machinery of modern enterprise operation hinges entirely upon robust Identity and Access Management (IAM) frameworks. From the routine task of accessing corporate email to the high-stakes provisioning of cloud infrastructure or proprietary Customer Relationship Management (CRM) systems, IAM serves as the foundational security perimeter for digital engagement. However, as organizations experience exponential growth in scale, velocity, and environmental complexity—spanning multi-cloud deployments and hybrid work models—the established security controls often buckle under the strain.
One of the most significant bottlenecks, creating a direct conflict between operational agility and stringent security posture, is the management of time-bound, temporary elevated privileges—commonly known as Just-In-Time (JIT) access. Business units operate under the imperative of immediate productivity, demanding near-instantaneous access to specialized tools to resolve urgent incidents or progress critical projects. Conversely, security governance mandates, often driven by regulatory compliance (such as SOC 2, HIPAA, or GDPR) and internal audit requirements, necessitate rigorous oversight, explicit approval chains, and immutable audit trails, all while enforcing the Principle of Least Privilege (PoLP).
The traditional method of handling JIT requests—a cascade of emails, direct messages, and manual ticket manipulation—is inherently flawed. It introduces unacceptable latency and systemic vulnerability. This analysis delves into a sophisticated, pre-engineered automation solution, exemplified by the Tines “Grant Temporary Application Access” workflow, which is specifically architected to resolve this persistent tension by introducing intelligent orchestration into the access lifecycle.
The Escalating Risk Profile of Unmanaged Access Sprawl
As articulated by industry practitioners such as Stephen McKenna, IT Operations Technician at Tines, the fundamental axiom remains: “Scaling access inherently scales risk.” Every significant organizational event—a new hire onboarding (“joiner”), an internal transfer (“mover”), or an employee departure (“leaver”)—initiates a series of access changes that must be meticulously managed. The JIT scenario compounds this complexity because it involves granting *temporary* exceptions to standard access policies.
In heterogeneous environments where legacy systems coexist with modern SaaS platforms, these provisioning changes are frequently fragmented across disparate management consoles. While some modern applications integrate smoothly through Single Sign-On (SSO) providers like Okta or Azure AD, others necessitate manual intervention, script execution, or direct console manipulation for role assignment. This patchwork results in operational silos and security blind spots.
Consider the typical scenario requiring JIT access: a software developer needs elevated, time-limited permissions to debug a critical issue within a production Kubernetes cluster, or an external consultant requires specific administrative rights to a financial reporting database for a two-day audit. Without automated enforcement, the manual process inevitably involves:

- A request submission (often via an insecure channel).
- Manual verification of the requestor’s identity and necessity.
- The IT or Security team locating the correct administrative interface (e.g., AWS console, Jira group management, Okta admin panel).
- Manually adding the user to the required role or group.
- Setting a mental or calendar reminder to manually reverse the permission.
The inevitable outcome of this manual dependency is privilege creep and entitlement latency. Accounts granted for a specific debugging session might persist for weeks, leaving dormant, high-privilege pathways exposed. This lingering access represents a significant, unmitigated attack surface that auditors actively seek to identify.
Industry Implications: The Regulatory Imperative
The failure to enforce timely revocation of temporary access is not merely an IT efficiency problem; it is a compliance liability. Regulatory frameworks are increasingly focused not just on *who* has access, but *when* they have it. For instance, the concept of “break-glass” or emergency access procedures must be documented, controlled, and, crucially, automatically reset. A system that relies on human memory to revoke permissions fails the standard for demonstrable control maturity. Organizations facing stringent compliance regimes must transition from reactive remediation to proactive, policy-driven enforcement, making orchestration a necessity rather than a luxury.
The Paradigm Shift: Automated, Time-Bound Provisioning via Orchestration
The strategic implementation of an automation platform like Tines transforms the JIT access request from a manual administrative chore into a deterministic, auditable, and self-correcting process. The pre-built “Grant Temporary Application Access” workflow is a blueprint for achieving this balance, integrating disparate tools into a cohesive security choreography. It manages the entire access lifecycle—request, approval, provisioning, expiry, and revocation—with high fidelity.
The core strength of this approach lies in its ability to treat access as an ephemeral resource, defined by strict temporal boundaries. By leveraging existing investments in identity providers (like Okta), ticketing systems (like Jira Software), and communication platforms (like Slack or Microsoft Teams), the workflow builds a secure control plane:
1. Initiating Access via Self-Service Portal
The process begins not with an email, but with a controlled interface: a Tines Page. This serves as a standardized, user-friendly web form, accessible only to authorized personnel. The requestor explicitly defines the required parameters: the target application (e.g., “Staging Environment Access,” “Production Database Read-Write”), the precise duration of need (e.g., “45 minutes,” “End of Business Day”), and the mandatory business justification. This structured input eliminates ambiguity and immediately feeds clean data into the subsequent automation steps.
2. Enforcing Governance Through Contextual Approval
Upon submission, the workflow intelligently routes the request. Utilizing pre-configured logic, it maps the requested application to the correct approval authority—be it the direct manager, the application owner, or a dedicated security team. A rich, interactive notification is dispatched via the organization’s primary communication channel (e.g., Slack). Critically, this notification embeds actionable buttons (“Approve” or “Deny”). The approver can review the details and render a decision directly from the notification, minimizing context switching and accelerating response times. This instant feedback loop maintains business velocity.
3. Instantaneous, Auditable Provisioning
If the request is authorized, the automation engine executes the provisioning step without human intervention. It triggers a direct API interaction with the identity management system (e.g., Okta). The user is programmatically added to the specific security group tied to the requested permission level. This API-driven action ensures immediate enforcement of the privilege. Concurrently, to satisfy auditability requirements, the workflow ensures the decision and the request details are logged, often by creating or updating a corresponding ticket in Jira Software, establishing an unbroken chain of custody for the temporary privilege.
4. The Critical Wait State and Time-Bound Enforcement
This is the security linchpin. Once access is granted, the workflow enters a monitored “wait” state, precisely calibrated to the duration specified in the initial request. This is not a simple calendar reminder; it is an active, stateful hold within the automation engine. During this period, the user operates with the elevated permissions necessary for their task.
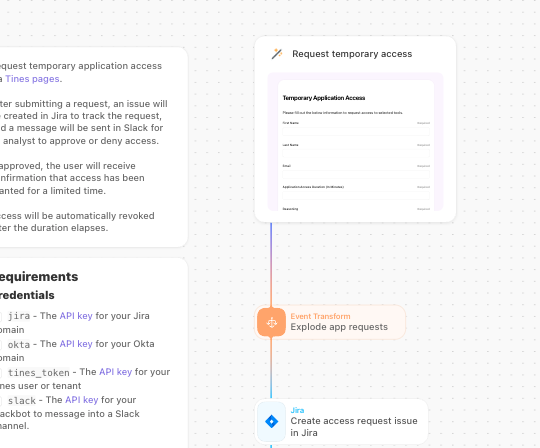
5. Automated, Unwavering Revocation
When the defined time expires, the workflow automatically transitions out of the wait state and executes the mandated cleanup sequence. It communicates back to the identity provider via API to remove the user from the access group, thereby instantly and unilaterally revoking the privilege. This eliminates the risk associated with forgotten manual steps. Post-revocation, the system finalizes the audit trail by closing the associated Jira ticket and notifying the user via Slack that their temporary session has concluded, providing transparency and closure.
Expert Analysis: Benefits Beyond Speed
The integration of such a structured workflow yields tangible benefits across security, operations, and compliance domains, moving beyond simple ticket reduction:
- Drastic Reduction in Attack Surface: By strictly enforcing time limits, the mean time that excessive privileges exist (MTTEP) approaches zero. This dramatically shrinks the window of opportunity for insider threats or external attackers exploiting dormant credentials.
- Enhanced Compliance and Auditability: Every JIT access request generates an immutable, machine-logged record detailing who requested it, who approved it, when it was granted, and precisely when it was revoked. This level of granularity satisfies even the most rigorous compliance scrutiny, shifting the burden of proof from manual documentation to automated system records.
- Operational Efficiency and IT Focus: IT and Security teams are freed from the repetitive, low-value task of access granting and revocation. This allows highly skilled personnel to focus on strategic security architecture, threat hunting, and proactive risk mitigation rather than reactive ticket closure.
Configuring the Ecosystem: Implementing the Template
The accessibility of pre-built automation significantly lowers the barrier to entry for implementing advanced JIT controls. Organizations can leverage the existing Tines Library to deploy this capability rapidly.
Phase 1: Ingestion of the Story
The “Grant temporary application access” template is sourced directly from the Tines Library. Importing this “Story” brings the foundational logic—the sequential steps, decision points, and integration hooks—directly into the organization’s Tines tenant. This avoids the complex and error-prone process of building stateful workflows from scratch.
Phase 2: Establishing Secure Credentials
The workflow’s utility is dependent on its ability to securely interact with external APIs. This requires configuring secure “Credentials” within the Tines environment. This typically involves setting up API keys or OAuth connections for:
- **Identity Provider (e.g., Okta):** Necessary for programmatic user/group manipulation.
- **Ticketing System (e.g., Jira Software):** Required for incident logging and audit trail maintenance.
- **Communication Platform (e.g., Slack/Teams):** Used for interactive approval routing.
These credentials are encrypted and managed internally by the platform, ensuring that sensitive API tokens are never exposed in logs or workflow definitions.

Phase 3: Customizing the User Interface (The Tines Page)
The front-end interface must reflect the organization’s actual access topology. By editing the initial “Page” element in the workflow canvas, administrators can tailor the request form. This involves populating dropdown menus with the exact security groups or roles available across the environment (e.g., mapping a selection like “Finance Reporting Access” to the correct Okta group ID). This customization ensures the user requests exactly what they need, no more, no less.
Phase 4: Policy Layer Integration
Flexibility is paramount in security automation. Administrators can augment the template logic using drag-and-drop canvas elements. For instance, a security policy might dictate that any request exceeding two hours automatically triggers an escalation to a Security Operations Center (SOC) analyst for manual review, or that access to highly sensitive environments (like core payment processing systems) requires two distinct managerial approvals. These conditional logic gates are inserted directly into the flow path, enforcing nuanced policy without requiring code changes.
Phase 5: Validation and Deployment
Rigorous testing is essential. A test request must be executed to verify that the approval notification is correctly routed, the API calls successfully modify the identity provider state, and, most critically, that the revocation timer functions precisely as expected. Once verified, the Tines Page is published and disseminated to the relevant teams, making secure, rapid JIT access an operational reality.
Future Trajectories in Access Control
The trend toward ephemeral, orchestrated access is accelerating, driven by the convergence of Zero Trust architecture principles and the increasing sophistication of threat actors. We are moving toward a future where permanent, standing access to critical systems will become an anomaly, reserved only for core infrastructure service accounts.
Future iterations of these workflows will likely incorporate advanced telemetry. Imagine a scenario where the workflow automatically shortens the approved JIT duration if the user exhibits unusual behavior *while* holding the elevated access—for example, attempting to query an excessive volume of records or accessing resources outside the designated scope. Machine learning models integrated into the orchestration layer could dynamically adjust the access window based on real-time risk scoring. This evolution transforms JIT from a static, time-based grant into a dynamically managed, behaviorally aware permission session, representing the next frontier in proactive security governance.

